Predictable and Runtime-Adaptable Network-On-Chip for Mixed-Critical Real-Time Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
System Manual Pdm360smart Monitor CR1070 CR1071 Codesys® V2.3 Target V05 English
System Manual PDM360smart monitor CR1070 CR1071 CoDeSys® V2.3 Target V05 English 7390674_01_UK 2012-05-16 2012-05-16 7390674_01_UK ifm System Manual ecomatmobile PDM360smart (CR1070, CR1071) Target V05 2012-05-16 Contents Contents 1 About this manual 7 1.1 What do the symbols and formats mean? ......................................................................7 1.2 How is this manual structured?.......................................................................................8 2 Safety instructions 9 2.1 Important!........................................................................................................................9 2.2 What previous knowledge is required?.........................................................................10 3 System description 11 3.1 Information concerning the device................................................................................11 3.2 Information concerning the software.............................................................................11 3.3 PLC configuration .........................................................................................................12 4 Configurations 13 4.1 Set device parameters (setup)......................................................................................13 4.1.1 Start set-up ..............................................................................................................14 4.1.2 Show the current device settings.............................................................................15 4.1.3 Change -

Iot LSP Standard Framework Concepts 2015
AIOTI ALLIANCE FOR INTERNET OF THINGS INNOVATION IoT LSP Standard Framework Concepts Release 2.0 AIOTI WG03 – loT Standardisation 2015 AIOTI ALLIANCE FOR INTERNET OF THINGS INNOVATION Executive Summary This deliverable introduces IoT Standards Developing Organisation (SDO), Alliance and Open Source Software (OSS) landscapes to be used as input for the recommendations for Large Scale Pilots (LSPs) standard framework and gap analysis. The LSPs can play an important role in investigating and solving specific challenges for the IoT industry and promoting innovation that is related to specific activities such as 1) the applied standards framework, 2) deployments, 3) technological and business model validation and 4) acceptability. The main objective of this deliverable is to briefly present the global dynamics and landscapes of IoT SDO, Alliance and OSS initiatives, which can be used: 1) to leverage on existing IoT standardization, industry promotion and implementation of standards and protocols, 2) as input for LSP standards framework and gap analysis and 3) to provide a guideline for the proponents of future project proposals associated with future IoT related calls financed by the EC on the positioning of these initiatives within these landscapes. AIOTI – Restricted 2 AIOTI ALLIANCE FOR INTERNET OF THINGS INNOVATION Table of Contents 1. GOAL AND MOTIVATION............................................................................................................................. 4 2. IOT SDO AND ALLIANCE INITIATIVES LANDSCAPE.......................................................................... -

Catalog of GA Control Systems
GA automation technology product catalog Contact information GEBHARDT Automation GmbH Thüngenfeld 3 D- 58256 Ennepetal Germany Tel.: +49 2333 7908 - 0 available during working hours, Mo to Fr, from 800 to 1700 (5 pm) central european time (CET, GMT+1). FAX: +49 2333 7908 - 24 Web: www.gebhardt-automation.de Support [email protected] Information [email protected] Date: 10/2012 GA catalog_Rev 02.01_2012-10-09 en.doc page 2 of 40 Contents GA BlueLine Systems ............................................................................................................4 Redundancy, fault tolerance and voting...............................................................................................5 Machinery Monitoring Systems............................................................................................................6 Monitoring Capabilities.........................................................................................................................7 GA TMR/10-S.......................................................................................................................................8 GA TMR SMART-S ..............................................................................................................................9 GA DUPLEX/7-S ................................................................................................................................10 GA DUPLEX SMART-S .....................................................................................................................11 -

Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Evaluation of open source operating systems for safety-critical applications Master’s thesis in Embedded Electronic System Design Petter Sainio Berntsson Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY UNIVERSITY OF GOTHENBURG Gothenburg, Sweden 2017 MASTER’S THESIS 2017 Evaluation of open source operating systems for Safety-critical applications Petter Sainio Berntsson Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg Gothenburg, Sweden 2017 Evaluation of open source operating systems for safety-critical applications Petter Sainio Berntsson © Petter Sainio Berntsson, 2017 Examiner: Per Larsson-Edefors Chalmers University of Technology Department of Computer Science and Engineering Academic supervisor: Jan Jonsson Chalmers University of Technology Department of Computer Science and Engineering Industrial supervisors: Lars Strandén RISE Research Institutes of Sweden Dependable Systems Fredrik Warg RISE Research Institutes of Sweden Dependable Systems Master’s Thesis 2017 Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg SE-412 96 Gothenburg Telephone +46(0) 31 772 1000 Abstract Today many embedded applications will have to handle multitasking with real-time time constraints and the solution for handling multitasking is to use a real-time operating system for scheduling and managing the real-time tasks. There are many different open source real-time operating systems available and the use of open source software for safety-critical applications is considered highly interesting by industries such as medical, aerospace and automotive as it enables a shorter time to market and lower development costs. If one would like to use open source software in a safety-critical context one would have to provide evidence that the software being used fulfills the requirement put forth by the industry specific standard for functional safety, such as the ISO 26262 standard for the automotive industry. -

SAFE TORQUE OFF a Guide to the Application of the Control Techniques Safe Torque Off Safety Function and Its Compliance with IEC 61800-5-2 SAFE TORQUE OFF
SAFE TORQUE OFF A guide to the application of the Control Techniques Safe Torque Off safety function and its compliance with IEC 61800-5-2 SAFE TORQUE OFF 1. Purpose of this guide This application guide gives general explanations, advice and guidance for the use of the Safe Torque Off (STO) feature which is provided in many of Control Techniques’ variable speed drive products. It supplements the specific product information given in the product Technical Guides. In the event of any discrepancy the product Technical Guide takes precedence. Most of the information is general in nature and applies to all models. Some model- specific information is given in Annex 1. Important warnings The design of safety-related systems requires specialist knowledge. To ensure that a complete control system is safe it is necessary for the whole system to be designed according to recognised safety principles. The use of individual sub-systems such as drives with Safe Torque Off functions, which are intended for safety- related applications, does not in itself ensure that the complete system is safe. The information given in this publication gives guidance on the application of Control Techniques Safe Torque Off, and also some general background material on the design of safety-related systems for machinery control. This publication is not intended to form a complete guide to the subject. Some more detailed references are given at the end of the guide. The information provided is believed to be correct and to reflect accepted practice at the time of writing. It is the responsibility of the designer of the end product or application to ensure that it is safe and in compliance with the relevant regulations. -

Components DISTRIBUTOR
The REGION’S LARGEST Essential Components DISTRIBUTOR www.cbtcompany.com Why essential components? Get the right components, at the right price, right when you need them. CBT offers you quality Allen-Bradley® essential components with 110 years of time-tested quality and durability. This catalog is your initial guide to selecting the best components to meet your specific appli- cation requirements. With Allen-Bradley®’s product portfolio, you will find the highest quality components at a fair price, an intuitive product selection, and fast delivery. Additionally, you will receive components that perform to your specifications, accompanied by the professional knowledge and support of CBT’s industry special- ists, you will receive components that perform to your specifications and make up the complete system you need. Smart devices include: Variable Frequency Servo Motor Condition Drives Drives Starters Monitoring Smart devices make data-driven productivity improvements using smart devices At its most basic level, The Connected Enterprise is about enabling the equipment, machinery, and devices in a manufacturing plant to provide real-time information that can help optimize plant operations. Rockwell Automation smart devices help you: • Increase productivity • Produce higher-quality products at lower costs • Support regulatory compliance • Identify and address worker-safety issues • Optimize supply chains Smart devices are the foundation of integrated control and information, providing seamless connectivity and the raw data for your Connected -

Standards Publications
IRISH STANDARDS PUBLISHED BASED ON CEN/CENELEC STANDARDS 1. I.S. 178:1973 Date published 28 SEPTEMBER 2005 Extruded Rigid PVC Corrugated Sheeting 2. I.S. EN 60835-1-2:1993 Date published 1 JUNE 2005 Methods of measurement for equipment used in digital microwave radio transmission systems -- Part 1: Measurements common to terrestrial radio-relay systems and satellite earth stations -- Section 2: Basic characteristics (IEC 60835-1-2:1992 (EQV)) 3. I.S. EN 160000:1993/A1:1996 Date published 1 JUNE 2005 Generic Specification: Modular electronic units 4. I.S. EN 61595-1:1999 Date published 1 JUNE 2005 Multichannel digital audio tape recorder (DATR), reel-to-reel system, for professional use -- Part 1: Format A (IEC 61595-1:1997 (EQV)) 5. I.S. EN 1990:2002+NA:2010 Date published 24 MARCH 2005 Eurocode - Basis of structural design (including Irish National Annex) 6. I.S. EN ISO 14122-4:2004 Date published 23 FEBRUARY 2005 Safety of machinery - Permanent means of access to machinery - Part 4: Fixed ladders (ISO 14122-4:2004) 7. I.S. EN 13877-1:2004 Date published 23 SEPTEMBER 2005 Concrete pavements - Part 1: Materials 8. I.S. EN 13877-2:2004 Date published 23 SEPTEMBER 2005 Concrete pavements - Part 2: Functional requirements for concrete pavements 9. I.S. EN 12843:2004 Date published 4 MARCH 2005 Precast concrete products - Masts and poles 10. I.S. EN 13225:2005 Date published 4 MARCH 2005 Precast concrete products - Linear structural elements 11. I.S. EN 13693:2004 Date published 4 MARCH 2005 Precast concrete products - Special roof elements 12. -

Safety Guide for the Americas
Safety Guide for the Americas Six steps to a safe machine Contents Six steps to a safe machine Six steps to a safe machine Contents Six steps to a safe machine Laws, directives, standards, liability g §-1 • Regulatory requirements g §-1 • European directives g §-4 • Obligations of the machine manufacturer g §-5 • Standards g §-9 § • International/European standards g §-11 • Nationally recognized testing labs g §-14 • Test bodies, insurance providers, and authorities g §-15 Risk assessment g 1-1 • The risk assessment process g 1-1 • Functions of the machine g 1-3 • Identification of tasks and hazards g 1-4 1 • Risk estimation and risk evaluation g 1-5 • Documentation g 1-6 Safe design g 2-3 • Mechanical design g 2-3 • Operating and maintenance concept g 2-4 • Electrical installation g 2-5 • Enclosure ratings g 2-8 • Lock-out/tag-out g 2-10 2 • Stop functions g 2-11 g • Electromagnetic compatibility (EMC) 2-12 2-1 • Fluid technology g 2-14 g g • Use in potentially explosive atmospheres 2-15 c Design of the safety function g 3-1 Technical protective measures • Development of the safety concept g 3-13 g • Selection of the protective devices g 3-18 a Definition of the safety functions 3-2 g b Determination of the required g 3-9 • Positioning and dimensioning of 3-44 safety level protective devices • Integration of protective devices into g 3-65 3 the control system Implementation of the safety functions • Product overview for safeguarding g 3-76 d Verification of the safety function g 3-79 e Validation of all safety functions g 3-95 Risk reduction -

Safety Bock I/O Module TBPN-L1-FDIO1-2IOL
Your Global Automation Partner TBPN-L1-FDIO1-2IOL Safety Block I/O Module Safety manual - Translation 2 Hans Turck GmbH & Co. KG | T +49 208 4952-0 | F +49 208 4952-264 | [email protected] | www.turck.com Table of Content 1 About this document 5 2 Scope 5 3 Safety Integrity Level/Performance Level/Category 5 4 Product description 6 4.1 Intended use 6 4.1.1 Foreseeable misuse 6 4.2 Device overview 6 4.3 Type plate 7 4.4 Switches and connectors 7 4.5 Block diagram 7 5 Safety function 8 5.1 Safe status 8 5.2 Fatal Error 8 6 Safety planning 8 6.1 Prerequisites 8 6.2 Reaction time 8 6.3 Safety characteristic data 9 7 Operating instructions 9 7.1 General 9 7.2 Before operation 10 7.2.1 Mounting 10 7.2.2 Connection 11 7.2.3 Address assignment 12 7.2.4 Configuring 12 7.3 Operation 13 7.3.1 Indication elements 13 7.3.2 Output error behavior 14 7.3.3 Decommissioning 14 8 Appendix: Wiring diagram 14 8.1 Ethernet 14 8.2 Power supply 14 8.3 Safety inputs 14 8.4 Safety in-/outputs 15 8.5 DXP 15 8.6 IO-Link 15 9 Appendix: Connection examples 16 9.1 Inputs 16 9.2 Outputs 16 V2.0 | 2018/01 3 10 Appendix: Designations and abbreviations 17 11 Appendix: Function tests 17 12 Appendix: Document history 17 13 Appendix: Technical data 18 14 Appendix: Declaration of Conformity 20 4 Hans Turck GmbH & Co. -
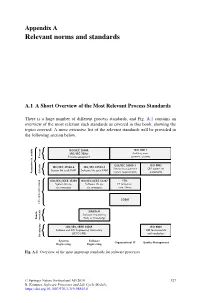
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems
IEC 61508 Overview Report A Summary of the IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems exida Sellersville, PA 18960, USA +1-215-453-1720 © exida IEC 61508 Overview Report, Version 2.0, January 2, 2006 Page 1 of 29 1 Overall Document Summary IEC 61508 is an international standard for the “functional safety” of electrical, electronic, and programmable electronic equipment. This standard started in the mid 1980s when the International Electrotechnical Committee Advisory Committee of Safety (IEC ACOS) set up a task force to consider standardization issues raised by the use of programmable electronic systems (PES). At that time, many regulatory bodies forbade the use of any software-based equipment in safety critical applications. Work began within IEC SC65A/Working Group 10 on a standard for PES used in safety-related systems. This group merged with Working Group 9 where a standard on software safety was in progress. The combined group treated safety as a system issue. The total IEC 61508 standard is divided into seven parts. Part 1: General requirements (required for compliance); Part 2: Requirements for electrical/electronic/programmable electronic safety-related systems (required for compliance); Part 3: Software requirements (required for compliance); Part 4: Definitions and abbreviations (supporting information) Part 5: Examples of methods for the determination of safety integrity levels (supporting information) Part 6: Guidelines on the application of parts 2 and 3 (supporting information) Part 7: Overview of techniques and measures (supporting information). Parts 1, 3, 4, and 5 were approved in 1998. Parts 2, 6, and 7 were approved in February 2000. -

D1.5 Impact on Standards and Open Initiatives - First Analysis
Ref. Ares(2020)1266005 - 28/02/2020 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Document Information Contract Number 825473 Project Website https://elastic-project.eu/ Contractual Deadline M15, Feb 2020 Dissemination Level CO Nature R Author(s) Thales R&T Contributor(s) BSC, ISEP, SIX, THALIT Reviewer(s) SIX, BSC Keywords Railway Safety Standards, Open Initiatives, Impact Notices: The ELASTIC project has received funding from the European Union’s Horizon 2020 research and innovation programme under the grant agreement Nº 825473. © 2019 ELASTIC. A Software Architecture for Extreme-ScaLe Big-Data AnalyticS in Fog CompuTing ECosystems. All rights reserved. D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Change Log Version Author Description of Change V0.1 TRT Initial Draft Contribution on the analysis of OpenFog V0.2 BSC Initiative V0.2 TRT Contribution 61508 std, Railway std V0.3 SIX DMTF V0.4 ISEP FIWARE V0.5 BSC OpenFog V0.6 THALIT Contribution 61508 std, Railway std V0.7 TRT Final version, including revision V0.8 SIX Internal review V1.0 BSC Final adjustments. Version released to EC. 2 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Table of contents Change Log ...................................................................................... 2 1. Executive Summary ....................................................................... 5 2. Introduction ............................................................................... 6 2.1 Purpose