Your Performance Task Summary Explanation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

NTFS • Windows Reinstallation – Bypass ACL • Administrators Privilege – Bypass Ownership
Windows Encrypting File System Motivation • Laptops are very integrated in enterprises… • Stolen/lost computers loaded with confidential/business data • Data Privacy Issues • Offline Access – Bypass NTFS • Windows reinstallation – Bypass ACL • Administrators privilege – Bypass Ownership www.winitor.com 01 March 2010 Windows Encrypting File System Mechanism • Principle • A random - unique - symmetric key encrypts the data • An asymmetric key encrypts the symmetric key used to encrypt the data • Combination of two algorithms • Use their strengths • Minimize their weaknesses • Results • Increased performance • Increased security Asymetric Symetric Data www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Confortable • Applying encryption is just a matter of assigning a file attribute www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Transparent • Integrated into the operating system • Transparent to (valid) users/applications Application Win32 Crypto Engine NTFS EFS &.[ßl}d.,*.c§4 $5%2=h#<.. www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Flexible • Supported at different scopes • File, Directory, Drive (Vista?) • Files can be shared between any number of users • Files can be stored anywhere • local, remote, WebDav • Files can be offline • Secure • Encryption and Decryption occur in kernel mode • Keys are never paged • Usage of standardized cryptography services www.winitor.com 01 March 2010 Windows Encrypting File System Availibility • At the GUI, the availibility -

Turning on Bitlocker Drive Encryption on Windows Computers Before You
Turning on BitLocker drive encryption on Windows computers Before you start a couple of VERY important notes... a) Make sure you have backups before you start just in case anything goes wrong (as it’s much harder, usually impossible, to recover data from an encrypted drive - as you would hope and expect). b) Make sure you keep a safe copy of the encryption key And please provide a copy for the IT Office to store for use in the event of a problem or, if you choose to let Microsoft keep it, make sure you know your login details for Microsoft. If you forget the passwords and can not recover a copy of your key you will loose all your files (which is another reason to keep backups). If you reset BitLocker and a new encryption key is set - please remember to provide a copy to the IT Office Windows 7, 8 and 10 have BitLocker Built in, this can be used to encrypt the hard drive. It just needs to be activated following the steps shown below. 1) Enable BitLocker for a Drive The easiest way to enable BitLocker for a drive is to right-click the drive in a File Explorer window, and then choose the “Turn on BitLocker” command. If you don’t see this option on your context menu. Then click on the windows icon and where it says “Type here to search” type in “encryption” and click on “Manage BitLocker” from the list of options that appears. It’s just that simple. The wizard that pops up walks you through selecting several options, which we’ve broken down into the sections that follow. -

Protecting Miscrosoft® Hyper-V Environments
Protecting Miscrosoft® Hyper-V Environments Who should read this paper Technical White Papers are designed to introduce Veritas partners and end users to key technologies and technical concepts that are associated with the Veritas™ Backup and Recovery product family. The information within a Technical White Paper will assist partners and end users as they design and implement data protection solutions based on Veritas Backup and Recovery products. Technical White Papers are authored and maintained by the Veritas Backup and Recovery Technical Services group. Veritas Backup Exec™ 15 Technical White Paper Protecting Hyper-V Environments Contents Introduction.......................................................................................3 Business Value....................................................................................3 Underlying Backup Principles.........................................................................7 Virtualized Application Protection .....................................................................10 Virtual Machine Recovery Options ....................................................................12 Improved Usability for Virtual Environments.............................................................15 Example Hyper-V Configurations .....................................................................16 Performance Recommendations .....................................................................17 Notes and Best Practices ...........................................................................18 -

Microsoft Windows FIPS 140 Validation Security Policy Document
Secure Kernel Code Integrity Security Policy Document Microsoft Windows FIPS 140 Validation Microsoft Windows 10 (Creators Update, Fall Creators Update, April 2018 Update) Microsoft Windows Server (versions 1703, 1709, and 1803) Non-Proprietary Security Policy Document Version Number 1.4 Updated On April 4, 2019 © 2018 Microsoft. All Rights Reserved Page 1 of 24 This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision). Secure Kernel Code Integrity Security Policy Document The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Minimum Hardware and Operating System
Hardware and OS Specifications File Stream Document Management Software – System Requirements for v4.5 NB: please read through carefully, as it contains 4 separate specifications for a Workstation PC, a Web PC, a Server and a Web Server. Further notes are at the foot of this document. If you are in any doubt as to which specification is applicable, please contact our Document Management Technical Support team – we will be pleased to help. www.filestreamsystems.co.uk T Support +44 (0) 118 989 3771 E Support [email protected] For an in-depth list of all our features and specifications, please visit: http://www.filestreamsystems.co.uk/document-management-specification.htm Workstation PC Processor (CPU) ⁴ Supported AMD/Intel x86 (32bit) or x64 (64bit) Compatible Minimum Intel Pentium IV single core 1.0 GHz Recommended Intel Core 2 Duo E8400 3.0 GHz or better Operating System ⁴ Supported Windows 8, Windows 8 Pro, Windows 8 Enterprise (32bit, 64bit) Windows 10 (32bit, 64bit) Memory (RAM) ⁵ Minimum 2.0 GB Recommended 4.0 GB Storage Space (Disk) Minimum 50 GB Recommended 100 GB Disk Format NTFS Format Recommended Graphics Card Minimum 128 MB DirectX 9 Compatible Recommended 128 MB DirectX 9 Compatible Display Minimum 1024 x 768 16bit colour Recommended 1280 x 1024 32bit colour Widescreen Format Yes (minimum vertical resolution 800) Dual Monitor Yes Font Settings Only 96 DPI font settings are supported Explorer Internet Minimum Microsoft Internet Explorer 11 Network (LAN) Minimum 100 MB Ethernet (not required on standalone PC) Recommended -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Windows 7 Bitlocker™ Drive Encryption Security Policy for FIPS 140-2 Validation
Windows 7 BitLocker™ Security Policy Page 1 of 16 Windows 7 BitLocker™ Drive Encryption Security Policy For FIPS 140-2 Validation For Windows 7 Document version 1.0 08/31/2011 1. Table of Contents 1. TABLE OF CONTENTS ......................................................................................................................... 1 2. INTRODUCTION .................................................................................................................................. 2 2.1 List of Cryptographic Modules ........................................................................................................................... 2 2.2 Brief Module Description ................................................................................................................................... 3 2.3 Validated Platforms ........................................................................................................................................... 4 3. INTEGRITY CHAIN OF TRUST .......................................................................................................... 4 4. CRYPTOGRAPHIC BOUNDARIES ..................................................................................................... 5 4.1 Overall Cryptographic Boundary........................................................................................................................ 5 4.2 BitLocker™ Components Included in the Boundary .......................................................................................... 5 4.3 Other Windows -

Samsung Galaxy J3 V J327V User Manual
User guide. User guide. User usuario. Guía del Guía GH68-47432D Printed in USA Galaxy J7_COLL-78600-UG-PO-CVR-6x4-V3-F-R2R.indd All Pages 2/2/17 11:00 AM SMARTPHONE User Manual Please read this manual before operating your device and keep it for future reference. Table of Contents Special Features . 1 Navigation . 28 Side Speaker . 2 Entering Text . 30 Getting Started . 3 Multi Window . 33 Set Up Your Device . 4. Emergency Mode . 35 Assemble Your Device . .5 Apps . 37 Start Using Your Device . 10 Using Apps . 38 Set Up Your Device . 11 Applications Settings . 41 Learn About Your Device . .15 Calculator . 45 Front View . 16 Calendar . 46 Back View . .18 Camera and Video . 49 Home Screen . .19 Clock . 54 VZW_J727V_EN_UM_TN_QB1_031717_FINAL Contacts . 57 Connections . 104 Email . 64 Wi‑Fi . 105 Gallery . .67 Bluetooth . 108 Google Apps . 71 Data Usage . 111 Message+ . .74 Airplane Mode . 113 Messages . .77 Mobile Hotspot . .114 My Files . 82 Tethering . 117 Phone . 84 Mobile Networks . 117 S Health . 94 Location . 118 Samsung Gear . 96 Advanced Calling . .119 Samsung Notes . 97 Nearby Device Scanning . .121 Verizon Apps . 99 Phone Visibility . .121 Settings . 101 Printing . .121 How to Use Settings . 102 Virtual Private Networks (VPN) . .121 Change Carrier . 123 Table of Contents iii Data Plan . 123 Smart Alert . 133 Sounds and Vibration . 124 Display . 134 Sound Mode . 125 Screen Brightness . 135 Easy Mute . 125 Screen Zoom and Font . 135 Vibrations . 125 Home Screen . 136 Volume . 126. Easy Mode . 136 Ringtone . .127 Icon Frames . .137 Notification Sounds . 128 Status Bar . .137 Do Not Disturb . 128 Screen Timeout . -

The Complete Guide to Windows 10 Privacy Settings Written by Gavin Phillips
! Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! The Complete Guide to Windows 10 Privacy Settings Written by Gavin Phillips Published October 2016. Read the original article here: http://www.makeuseof.com/tag/complete-guide-windows-10- privacy-settings/ This ebook is the intellectual property of MakeUseOf. It must only be published in its original form. Using parts or republishing altered parts of this ebook is prohibited without permission from MakeUseOf.com. Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! Table of contents General 4 Advertising ID 4 SmartScreen Filter 5 Send Info About Writing 5 Access My Language 5 Let Other Devices Open Apps 5 Let Other Devices Open Apps Using Bluetooth 6 Change Privacy Options Roundup 6 Location 7 Location 7 General Location 7 Default Location 7 Location History 8 Geofencing 8 Location Options Roundup 8 Camera 9 Microphone 10 Notifications 11 Speech, Inking, & Typing 13 Account Info 14 Contacts 15 Calendar 16 Call History 17 Email 18 Messaging 19 Radios 20 Other Devices 21 Sync With Devices 21 Use Trusted Devices 21 Feedback & Diagnostics 22 Feedback Frequency 22 Diagnostic and Usage Data 23 Background Apps 25 Is Windows 10 Still a Privacy Nightmare? 26 Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! The Windows 10 Anniversary Update brought forth an almost staggering number of changes. The update arrived in the first week of August, 2016, and its worldwide roll-out is expected to complete this month. This is a good time to explore the changes to all the Windows 10 privacy settings we’re still learning to live with. What follows is a page-by-page guide of Windows 10 Anniversary Update (referred to as AU forthwith) privacy settings, so you know exactly what to toggle, when to toggle it, and why you’d want to toggle it. -

Partition - Partitioning a Hard Drive
Partition - Partitioning a hard drive What is a partition? The partitioning of a hard drive occurs after the drive has been physically formatted but before it is logically formatted. It involves creating areas on the disk where data will not be mixed. It can be used, for example, to install differentoperating systems that do not use the same file system. There will therefore be at least as many partitions as there are operating systems using different file systems. If you are using just one operating system, a single partition the full size of the disk is sufficient, unless you want create several partitions so as to have, for example, several drives on which data are kept separate. There are three types of partitions: primary partitions, extended partitions andlogical drives. A disk may contain up to four primary partitions (only one of which can be active), or three primary partitions and one extended partition. In the extended partition, the user can create logical drives (i.e. "simulate" several smaller-sized hard drives). Let's look at an example where the disk contains one primary partition and one extended partition made up of three logical drives (later we will look at multiple primary partitions): For DOS systems (DOS, Windows 9x), only the primary partition is bootable, and is therefore the only one on which the operating system can be started. Partitioning is the process of writing the sectors that will make up the partition table (which contains information on the partition: size in sectors, position with respect to the primary partition, types of partitions present, operating systems installed,...). -
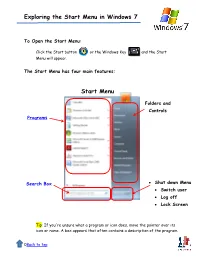
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e.