IDOL Keyview Filter SDK 11.5 .NET Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
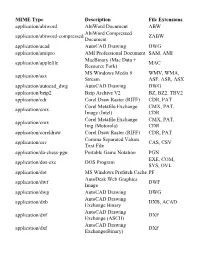
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Nucleic Acids Research
Nucleic Acids Research Executive editors R.T.Walker, Birmingham, UK B.E.Griffin, London, UK P.Pearson, Baltimore, MD, USA R.J.Roberts, Cold Spring Harbor, R.B.Hallick, Tucson, AZ, USA J.M.Rosen, Houston, TX, USA NY, USA J.E.Hearst, Berkeley, CA, USA I.C .Eperon, Leicester, UK N.C.Martin, Louisville, KY, USA M.J.Gait, Cambridge, UK W.R.McClure, Pittsburgh, PA, USA Editorial board M.Beato, Marburg, FRG W.T.Garrard, Dallas, 7X, USA S.E.V.Phillips, Leeds, UK A.J.Berk, Los Angeles, CA, USA F.Giannelli, London, UK R.H.Reeder, Seattle, WA, USA A.P.Bird, Edinburgh, UK P.J.Hagerman, Denver, CO, USA C.W.Schmid, Davis, CA, USA J.L.Bos, Utrecht, The Netherlands C.Helene, Paris, France Y.Shimura, Kyoto, Japan H.Buc, Paris, France A.J.Jeffreys, Leicester, UK R.Simpson, Bethesda, MD, USA K.Calame, New York, NY, USA C.J.Leaver, Oxford, UK D.Soll, New Haven, CT, USA N.Chua, New York, NY, USA H.Lehrach, London, UK B. Sollner-Webb, Baltimore, MD, USA D.A.Clayton, Stanford, CA, USA D.M.J.Lilley, Dundee, UK S.Spadari, Pavia, Italy A.Das, Farmington, CT, USA T.Lindahl, London, UK R.H.Symons, Adelaide, Australia M.L. DePamphilis, Nutley, NJ, USA S.M.Linn, Berkeley, CA, USA H.F.Tabak, Amsterdam, The M.P.Deutscher, Farmington, CT, USA J.T.Lis, Ithaca, NY, USA Netherlands J.E.Donelson, Iowa City, IA, USA R.McMacken, Baltimore, MD, USA S.Tilghman, Princeton, NJ, USA F.Eckstein, Gottingen, FRG D.A.Melton, Cambridge, MA, USA I.Tinoco, Jr, Berkeley, CA, USA J.D.Engel, Evanston, IL, USA J.R.Nevins, Durham, NC, USA Y.Wang, Shanghai, China P.T.Englund, Baltimore, MD, -

IBM PC Club IBM PC Club
San Jose PC CI ub Newsletter Document Number SJPCN03 May 4, 1982 Edited by Bonnie Lamb F98/142 San Jose 8 + 276-3653 VM(SJEVMl/LAMB) IBM PC Club IBM PC Club CONTENTS IBM SAN JOSE PC NEWSLETTER 1 Errata 1 April Meeting . 2 Special Interest Groups (SIG) 3 Survey Results ....... 3 San Jose PC Club Profile 5 Tips and Techniques 6 Programming notes 8 Electrohome 1302 Color Monitor with the PC 11 VOLKSWRITER Comparison to EASYWRITER 12 PC Puzzler 14 I nstall Notes 16 PC Club Program Library Directory 17 PC Add-Ons .... 19 SORT Comparisons 20 Help Wanted/Help Offered 21 Classified 22 PC Newsletter Articles 23 ii SJPCN03 05/04/82 IBM PC Club IBM SAN JOSE PC NEWSLETTER This month's newsletter has some survey results, sort performance information, a crossword puzzle (don't peek at the answers), and other good stuff. Time is short, we should have gone to press yesterday, so I'll close with next month's activity schedule: DATE DAY TIME LOCATION EVENT May 11 Tue. 5 p.m. STL Cafeteria PC Club Meeting May 12 Wed. 7:30p.m. DYSAN Santa Clara SVCC May 18 Tue. 5 p.m. STL K210 Phototypsetting SIG May 25 Tue. 5 p.m. STL K210 Visiclub (SIG) Meeting June 1 Tue. 5 p.m. STL K210 Advisory Meeting ERRATA The Silicon Valley Computer Club (SVCC) has found a bug in the BIOS modification that was printed in SJPCNOI to allow double-sided floppies. Details of symptoms and a possible fix are in the works. Look in next month's newsletter for this in formation. -

DECEMBER 1984 Editorial
SECRET UJUJUVC!JUJUJlb f5l5CBl!JWVU~ !D~~WCB~ Cf l!l U1 v ffil! f] Ill~(! ffi g 00 (!{il C!J l! '7 00 {iJ U1 ~ [1{iJ w~ NOV-DEC 1984 EO 1. 4. (c) P .L. 86- 36 . TRENDS IN HF COMMUNICATIONS (U) •••••••••••• • ••• J.._ ___---..._.1. \\:>............ 1 • SWITCHBOARD: • PAST, PRESENT AND FUTURE (U) •• ~ ............. I • • \ I .......... 5 \ OUT OF MY DEPTH (U) .......................•............•...; .. i .. \ ... ·........ 7 . • • • • • • • • • • • • • • • • • • • • • • ! I ...\ .......... s 1 EXPLORING A DOS DISKETTE (U)................... I ...... :; , ........ 12 HUMAN FACTORS (U) •••••••••••••••••••••••••••••• I l ........ 22 CAN YOU TOP THIS? (U) ........................... E. Leigh Sawyer ... , \~ ••••••• 24 PERSONAL COMPUTING IN A GROUP (U).............. • •••••• 25 FACTION LINE (U) ••• , •••••••••••••••••••••••• • ••• Cal Q. Lator •••••••••••••• • 35 NSA-CROSTIC NO. 59 (U) •••.•••••••••••••••••••••• D.H.W.;.,, ••••••••••••••••• 36 'flllS BOC\'.JMBNT <JONTl.INS <JOBl'JWORB MATl'JRIAh Ghi'tSSIFIEB BY tfSA/SSSM lH 2 SECRET BEGI:a\-SSIFY 0N. 0r igiriet iug Agency's Betezminatior:t Reqaized Declassified and Approved for Release by NSA on 'I 0- '16-2012 pursuant to E 0 . 13526, MOR Case # 54 77B OCID: 4009933 Published by Pl, Techniques and Standards EO 1. 4. ( c) P~L. 86-36 VOL. XI, No. 11-12 NOVEMBER-DECEMBER 1984 Editorial PUBLISHER BOARD OF EDITORS Edi.tor ...•••......_I _______ ... 1(963-3045s .) Product ion .•....•. I .(963-3369s) . : : : :· Collection .••••••..•••• i------.jc963-396ls) Computer Security •: ' •••••• 1 ,(859-6044) Cryptolinguist ics. l 963-1 f03s) Data Systems .•...•.•• ·l ., 963-4,953s) Information Science " • ..... I lc963-.5111s> Puzzles .......... David H. Williams'f(9637'Il03s) Special Research • ..•. Vera R. Filby;! C968'-7119s) Traffic Analysis •. Robert J. Hanyo!<f! (968-3888s) For subscript ions .. , send name and organizat~on to: I w14I i P.L. -

Computing :: Operatingsystems :: DOS Beyond 640K 2Nd
DOS® Beyond 640K 2nd Edition DOS® Beyond 640K 2nd Edition James S. Forney Windcrest®/McGraw-Hill SECOND EDITION FIRST PRINTING © 1992 by James S. Forney. First Edition © 1989 by James S. Forney. Published by Windcrest Books, an imprint of TAB Books. TAB Books is a division of McGraw-Hill, Inc. The name "Windcrest" is a registered trademark of TAB Books. Printed in the United States of America. All rights reserved. The publisher takes no responsibility for the use of any of the materials or methods described in this book, nor for the products thereof. Library of Congress Cataloging-in-Publication Data Forney, James. DOS beyond 640K / by James S. Forney. - 2nd ed. p. cm. Rev. ed. of: MS-DOS beyond 640K. Includes index. ISBN 0-8306-9717-9 ISBN 0-8306-3744-3 (pbk.) 1. Operating systems (Computers) 2. MS-DOS (Computer file) 3. PC -DOS (Computer file) 4. Random access memory. I. Forney, James. MS-DOS beyond 640K. II. Title. QA76.76.063F644 1991 0058.4'3--dc20 91-24629 CIP TAB Books offers software for sale. For information and a catalog, please contact TAB Software Department, Blue Ridge Summit, PA 17294-0850. Acquisitions Editor: Stephen Moore Production: Katherine G. Brown Book Design: Jaclyn J. Boone Cover: Sandra Blair Design, Harrisburg, PA WTl To Sheila Contents Preface Xlll Acknowledgments xv Introduction xvii Chapter 1. The unexpanded system 1 Physical limits of the system 2 The physical machine 5 Life beyond 640K 7 The operating system 10 Evolution: a two-way street 12 What else is in there? 13 Out of hiding 13 Chapter 2. -

Microsoft Exchange 2007 Journaling Guide
Microsoft Exchange 2007 Journaling Guide Digital Archives Updated on 12/9/2010 Document Information Microsoft Exchange 2007 Journaling Guide Published August, 2008 Iron Mountain Support Information U.S. 1.800.888.2774 [email protected] Copyright © 2008 Iron Mountain Incorporated. All Rights Reserved. Trademarks Iron Mountain and the design of the mountain are registered trademarks of Iron Mountain Incorporated. All other trademarks and registered trademarks are the property of their respective owners. Entities under license agreement: Please consult the Iron Mountain & Affiliates Copyright Notices by Country. Confidentiality CONFIDENTIAL AND PROPRIETARY INFORMATION OF IRON MOUNTAIN. The information set forth herein represents the confidential and proprietary information of Iron Mountain. Such information shall only be used for the express purpose authorized by Iron Mountain and shall not be published, communicated, disclosed or divulged to any person, firm, corporation or legal entity, directly or indirectly, or to any third person without the prior written consent of Iron Mountain. Disclaimer While Iron Mountain has made every effort to ensure the accuracy and completeness of this document, it assumes no responsibility for the consequences to users of any errors that may be contained herein. The information in this document is subject to change without notice and should not be considered a commitment by Iron Mountain. Iron Mountain Incorporated 745 Atlantic Avenue Boston, MA 02111 +1.800.934.0956 www.ironmountain.com/digital -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -
![Archive and Compressed [Edit]](https://docslib.b-cdn.net/cover/8796/archive-and-compressed-edit-1288796.webp)
Archive and Compressed [Edit]
Archive and compressed [edit] Main article: List of archive formats • .?Q? – files compressed by the SQ program • 7z – 7-Zip compressed file • AAC – Advanced Audio Coding • ace – ACE compressed file • ALZ – ALZip compressed file • APK – Applications installable on Android • AT3 – Sony's UMD Data compression • .bke – BackupEarth.com Data compression • ARC • ARJ – ARJ compressed file • BA – Scifer Archive (.ba), Scifer External Archive Type • big – Special file compression format used by Electronic Arts for compressing the data for many of EA's games • BIK (.bik) – Bink Video file. A video compression system developed by RAD Game Tools • BKF (.bkf) – Microsoft backup created by NTBACKUP.EXE • bzip2 – (.bz2) • bld - Skyscraper Simulator Building • c4 – JEDMICS image files, a DOD system • cab – Microsoft Cabinet • cals – JEDMICS image files, a DOD system • cpt/sea – Compact Pro (Macintosh) • DAA – Closed-format, Windows-only compressed disk image • deb – Debian Linux install package • DMG – an Apple compressed/encrypted format • DDZ – a file which can only be used by the "daydreamer engine" created by "fever-dreamer", a program similar to RAGS, it's mainly used to make somewhat short games. • DPE – Package of AVE documents made with Aquafadas digital publishing tools. • EEA – An encrypted CAB, ostensibly for protecting email attachments • .egg – Alzip Egg Edition compressed file • EGT (.egt) – EGT Universal Document also used to create compressed cabinet files replaces .ecab • ECAB (.ECAB, .ezip) – EGT Compressed Folder used in advanced systems to compress entire system folders, replaced by EGT Universal Document • ESS (.ess) – EGT SmartSense File, detects files compressed using the EGT compression system. • GHO (.gho, .ghs) – Norton Ghost • gzip (.gz) – Compressed file • IPG (.ipg) – Format in which Apple Inc. -

Using Netpresenz
NetPresenz 4.1 from netpresenz.com NB: Please click the "I Paid" checkbox in NetPresenz Setup - FTP Setup dialog. Contents What NetPresenz Does Features Using NetPresenz Setup FTP Setup WWW and Gopher Setup FTP Setup Details Scripting NetPresenz Setup Using NetPresenz Referring to your Server Using NetPresenz from a Un*x FTP Client Remote Volume Mounting Miscellaneous FTP Commands WWW Server Side Includes CGIs Java Missing files Gopher Security Considerations Avoid the Wrath of your Network Admin Limitations Remote Site Access Restrictions Acknowledgements How It Works What NetPresenz Does NetPresenz is a Macintosh implementation of the WWW, Gopher and FTP server protocols. It should be compatible with most FTP clients, and all WWW and Gopher clients. Basically it allows your Mac to act as an FTP server so you (and others) can access your files from anywhere around the world. Obviously there are some serious security considerations you should look into before using this software (see the Security Considerations section). NetPresenz requires System 7, MacTCP 1.1, and File Sharing enabled. It honours the Users & Groups privileges and passwords, and supports multiple logins, anonymous FTP (user name “anonymous” or “ftp”), as well as MacBinary and BinHex transfers, and the “MACB” FTP command. You can run NetPresenz as a foreground application (displaying the log), or as a background only application (use NetPresenz Setup to toggle between the two). Features Support WWW, Gopher and FTP connections. Full CGI support. Multiple simultaneous users. Honours System 7 Users & Groups (in fact depends on them!). Server Side Includes (SSI), counters and include files, file modification date and so forth. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

Name Synopsis Description Options Examples See Also
T1UNMAC(1) General Commands Manual T1UNMAC(1) NAME t1unmac − translate a Mac PostScript Type 1 font into PFAorPFB format SYNOPSIS t1unmac [−a|−b][−r][input [output]] DESCRIPTION t1unmac extracts POST resources from a Macintosh PostScript font file and creates a PFA (hexadecimal) or PFB (binary) font file. The file input should be in MacBinary I or II, AppleSingle, AppleDouble, or BinHexformat, or it can be a rawresource fork. If the file is a raw resource fork, you need to give the ‘−−raw’ option; otherwise t1unmac should automatically figure out what kind of file you have.Ifthe file output is not specified output goes to the standard output. OPTIONS −−pfa, −a Output in PFA(ASCII) format. −−pfb, −b Output in PFB (binary) format. This is the default. −−raw, −r Indicates that the input is a rawresource fork. −−macbinary Indicates that the input is in MacBinary I or II format. −−applesingle Indicates that the input is in AppleSingle format. −−appledouble Indicates that the input is in AppleDouble format. −−binhex Indicates that the input is in BinHex4.0 format. −−block−length=num, −l num PFB only: Set the maximum output block length to num. The default length is as large as memory allows. −−line−length=num, −l num PFAonly: Set the maximum length of encrypted lines in the output to num. (These are the lines consisting wholly of hexadecimal digits.) The default is 64. EXAMPLES On Mac OS X, you can use t1unmac to translate a font into PFAorPFB format as follows: % t1unmac −−rawFONTFILENAME/..namedfork/rsrc > OUTPUT SEE ALSO t1mac(1), t1ascii(1), t1binary(1), t1asm(1), t1disasm(1) AUTHORS Lee Hetherington ([email protected]) Eddie Kohler ([email protected]) Ported to Microsoft C/C++ Compiler and MS-DOS operating system by Kai-Uwe Herbing ([email protected]). -

Personal Computing
Personal Computing Thomas J. Bergin ©Computer History Museum American University Recap: Context • By 1977, there was a fairly robust but fragmented hobbyist-oriented microcomputer industry: – Micro Instrumentation Telemetry Systems (MITS) – Processor Technology – Cromemco – MicroStuf – Kentucky Fried Computers • Two things were needed for the personal computer revolution: 1) a way to store and retrieve data, and 2) a programming language in which to write applications. Homebrew Computer Club • March 5, 1975: the Amateur Computer Users Group (Lee Felsenstein, Bob Marsh, Steve Dompier, BobAlbrecht and 27 others) met in Gordon French’s garage, Menlo Park, CA • 3rd meeting drew several hundred people and was moved to the Coleman mansion • Stanford Linear Accelerator Center’s auditorium – Steve Wozniak shows off his single board computer – Steve Jobs attends meetings Homebrew-ed • 21 companies formed: – Apcose Apple – Cromemco Morrow – North Star Osborne • West Coast Computer Faire • Byte magazine, September 1975 • Byte Shop Both: images.google.com And then there was Traf-O-Data • October 28, 1955: William H. Gates III born – father: attorney mother: schoolteacher • Lakeside School: Lakeside Programming Group – Mothers Club: access to time-shared system at GE – Students hired by local firm to debug software – First computer program: Tic-Tac-Toe (age 13) – Traf-O-Data to sell traffic mgt. software (age 16) • 1973, Bill Gates enrolls at Harvard in pre-law. • Paul Allen is in his second year. January 1975, Popular Electronics: Altair • Allen shows