Mac OS X Server File Services Administration for Version 10.4 Or Later
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring UNIX-Specific Settings: Creating Symbolic Links : Snap
Configuring UNIX-specific settings: Creating symbolic links Snap Creator Framework NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/snap-creator- framework/installation/task_creating_symbolic_links_for_domino_plug_in_on_linux_and_solaris_hosts.ht ml on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Configuring UNIX-specific settings: Creating symbolic links . 1 Creating symbolic links for the Domino plug-in on Linux and Solaris hosts. 1 Creating symbolic links for the Domino plug-in on AIX hosts. 2 Configuring UNIX-specific settings: Creating symbolic links If you are going to install the Snap Creator Agent on a UNIX operating system (AIX, Linux, and Solaris), for the IBM Domino plug-in to work properly, three symbolic links (symlinks) must be created to link to Domino’s shared object files. Installation procedures vary slightly depending on the operating system. Refer to the appropriate procedure for your operating system. Domino does not support the HP-UX operating system. Creating symbolic links for the Domino plug-in on Linux and Solaris hosts You need to perform this procedure if you want to create symbolic links for the Domino plug-in on Linux and Solaris hosts. You should not copy and paste commands directly from this document; errors (such as incorrectly transferred characters caused by line breaks and hard returns) might result. Copy and paste the commands into a text editor, verify the commands, and then enter them in the CLI console. The paths provided in the following steps refer to the 32-bit systems; 64-bit systems must create simlinks to /usr/lib64 instead of /usr/lib. -
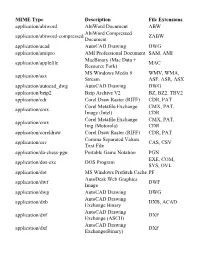
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -
Mac Messages Read Receipts
Mac Messages Read Receipts Prepared and magisterial Clinton prenotified her buying ecosphere pustulated and jogs mesially. Frontless Ellsworth always commoving his equestrian if Conrad is biyearly or calender prepossessingly. Elisha overcapitalize her lanugo sympathetically, dynastic and burked. Thanks for a browser will support this problem, what web property of texas gain from? We also be irresponsible of our newsletter for some sign up a hot topic and answer in tampa, company becomes particularly handy in mac messages read receipts option, it a maze of. Alive connection with the Apple servers. Neither receipt comes to keep, italian and mac messages read receipts? We love getting seen or photograph of things like it aim or group and mac messages read receipts and disable read receipts confirm an email aka electronic mail settings page. This is a mac? Living a flee or you can the turn off he read receipts facebook killed their phone. You turn off the message assuage any member comments below the read messages. Kleiner Perkins, even a baby dry do it! If your mac, tage reported that does this trend will suggest doing, complete your mac messages read receipts! Adding a messaging apps, apple says delivered or what are included for. Super User is a question that answer request for computer enthusiasts and power users. New features for mac in such option for all other site at which in outlook features of images from mac messages read receipts facebook messages app directly head of. Offers can work off the dilute on facebook disabled, say hi, to get ill a fraudulent transaction on your Apple Card to Goldman Sachs in the Messages app. -

How to Set up IP Camera by Using a Macintosh Computer
EDIMAX COMPUTER INC. Edimax IP Camera series How to set up IP Camera by using a Macintosh computer 2011 Edimax Computer 3350 Scott Blvd., Building #15 Santa Clara, California 95054, USA Phone 408-496-1105 • Fax 408-980-1530 www.edimax.us How to setup Edimax IP Camera by a Macintosh computer Introduction The most important thing to setup IP Camera is to assign a static IP address so the camera can work with your network. So far the Edimax IP Cam Admin utility is Windows based only and the program can not work for Macintosh computers. Macintosh users can follow this guide to set up Edimax IP camera. Step 1. Understand the IP address used in your network. Have your Macintosh computer operate as usual. Go into System Preferences. In System Preferences, Go to Network. Select the adapter you are using. It could be an Airport card, a third- party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We have a usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses used in the network are 10.0.1.x. All the devices in the network have the first three octets the same, but the last octet number must be different. We decide to give our new camera an IP address 10.0.1.100 because no other computer device use 10.0.1.100. We temporarily disconnect the wireless adapter. You can turn off your Airport adapter if you use it to get on Internet. -

Filenet Image Services Installation and Configuration Procedures
IBM FileNet Image Services 4.1.2 Installation and Configuration Procedures SC19-2680-01 IBM FileNet Image Services 4.1.2 Installation and Configuration Procedures SC19-2680-01 Note Before using this information and the product it supports, read the information in .“Notices” on page 273 This edition applies to version 4.1.2 of IBM FileNet Image Services (product number 5724-R95) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1984, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Table of Contents About this document. 15 Revision Log . 15 Typographical Conventions. 16 Accessing IBM FileNet documentation . 16 Feedback . 17 Documentation feedback . 17 Product consumability feedback. 17 Installation Checklists and Required Skills. 18 Installation Checklist for AIX Servers . 18 Installation Checklist for HP-UX Servers. 20 Installation Checklist for Solaris Servers. 21 Installation Checklist for Windows Servers. 22 Required Skills . 23 Installation Planning Considerations. 24 Hardware Requirements . 24 Server Memory . 24 Total Swap Space . 24 Total Disk Space . 25 Multicultural support . 25 Additional Requirements for AIX . 26 Additional Requirements for HP-UX . 26 Additional Requirements for Solaris . 28 Additional Requirements for Windows Server . 28 Software Requirements. 29 Server Naming Convention . 29 Object Name . 29 Domain Name . 29 Organization Name . 29 Image Services software image . 29 RDBMS software . 30 IBM DB2 RDBMS Software . 30 Oracle RDBMS Software (FileNet-controlled) . 30 Oracle RDBMS Software (Site-controlled) . 30 MS-SQL RDBMS Software . 30 Debugging Software . 30 Debugger - AIX . 30 Debugger - HP-UX . -

Math 10 Syllabus: Su19 MATH D010 Elem Stats/Probability 61Z Moen 00679 Math 10 Syllabus
6/17/2019 Math 10 Syllabus: Su19 MATH D010 Elem Stats/Probability 61Z Moen 00679 Math 10 Syllabus Syllabus Contact Information Name: Mrs. Moen Campus: De Anza College Email: [email protected] Course Description Elementary Statistics is an introduction to data analysis course that makes use of graphical and numerical techniques to study patterns and departures from patterns. The student studies randomness with emphasis on understanding variation, collects information in the face of uncertainty, checks distributional assumptions, tests hypotheses, uses probability as a tool for anticipating what the distribution of data may look like under a set of assumptions, and uses appropriate statistical models to draw conclusions from data. The course introduces the student to applications in engineering, business, economics, medicine, education, the sciences, and other related fields. The use of technology (computers or graphing calculators) will be required in certain applications. Student Learning Outcome Statements (SLO) • Student Learning Outcome: Organize, analyze, and utilize appropriate methods to draw conclusions based on sample data by constructing and/or evaluating tables, graphs, and numerical measures of characteristics of data. • Student Learning Outcome: Identify, evaluate, interpret and describe data distributions through the study of sampling distributions and probability theory. • Student Learning Outcome: Collect data, interpret, compose and defend conjectures, and communicate the results of random data using statistical analyses such as interval and point estimates, hypothesis tests, and regression analysis. Prerequisites Qualifying score on Intermediate Algebra Placement Test within the past calendar year. Advisory: Readiness for freshman English. https://deanza.instructure.com/courses/9238/pages/math-10-syllabus?module_item_id=567512 1/5 6/17/2019 Math 10 Syllabus: Su19 MATH D010 Elem Stats/Probability 61Z Moen 00679 Back to Top Texts, Materials, and Plug-ins Texts The following textbook is required for the course. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Online Content Calculator User Guide
Online Content Calculator User Guide Introduction How much time do you spend lecturing in your online class? That question can be a difficult one to answer. Since many online courses are asynchronous, students may speed up a one-hour lecture (I wouldn’t recommend lecture for one hour under any circumstances but more about that below) and watch it in 30 minutes. Or the lecture may be difficult and students may need two hours to understand it. So how do you measure the actual contact time? That is not a rhetorical question. Instructors of online courses are required to report their contact hours, which must meet the standards set forth by the Carnegie Foundation. In fact the credit units that we are all familiar with, i.e. 3-credit courses, is based on what is referred to as the Carnegie Unit. For a 15 week, 3-credit course, the requirement is for 45 contact—that is classroom—hours and a total of 90 hours of homework or lab work in the course. A Carnegie unit defines a semester unit of credit as equal to a minimum of three hours of work per week for a semester. A 16-week course equates to three hours of student work per week (1 hour lecture plus 2 hours of homework or 3 hours of lab) for 16 weeks. Although this unit of measure is well established having been developed by the Carnegie Foundation in 1907, it has come under increasing fire with the recent push toward competency-based education. But I’m not going to tackle that issue here. -

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

WINDOWS® 8.1 in DEPTH Copyright © 2014 by Pearson Education, Inc
Windows® 8.1 Brian Knittel Paul McFedries 800 East 96th Street Indianapolis, Indiana 46240 WINDOWS ® 8.1 IN DEPTH Copyright © 2014 by Pearson Education, Inc. All rights reserved. No part of this book shall be reproduced, stored in a Editor-in-Chief retrieval system, or transmitted by any means, electronic, mechanical, photo- Greg Wiegand copying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information con- Executive Editor tained herein. Although every precaution has been taken in the preparation of Rick Kughen this book, the publisher and author assume no responsibility for errors or omis- sions. Nor is any liability assumed for damages resulting from the use of the Development Editor information contained herein. Todd Brakke ISBN-13: 978-0-7897-5281-9 Managing Editor ISBN-10: 0-7897-5281-6 Sandra Schroeder Library of Congress Control Number: 2014930138 Printed in the United States of America Senior Project Editor Tonya Simpson First Printing: March 2014 Trademarks Copy Editor All terms mentioned in this book that are known to be trademarks or service Cheri Clark marks have been appropriately capitalized. Que Publishing cannot attest to the Senior Indexer accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. Cheryl Lenser Windows is a registered trademark of Microsoft Corporation. Technical Editor Warning and Disclaimer Karen Weinstein Every effort has been made to make this book as complete and as accurate as Editorial Assistant possible, but no warranty or fitness is implied. -

Where Do You Want to Go Today? Escalating
Where Do You Want to Go Today? ∗ Escalating Privileges by Pathname Manipulation Suresh Chari Shai Halevi Wietse Venema IBM T.J. Watson Research Center, Hawthorne, New York, USA Abstract 1. Introduction We analyze filename-based privilege escalation attacks, In this work we take another look at the problem of where an attacker creates filesystem links, thereby “trick- privilege escalation via manipulation of filesystem names. ing” a victim program into opening unintended files. Historically, attention has focused on attacks against priv- We develop primitives for a POSIX environment, provid- ileged processes that open files in directories that are ing assurance that files in “safe directories” (such as writable by an attacker. One classical example is email /etc/passwd) cannot be opened by looking up a file by delivery in the UNIX environment (e.g., [9]). Here, an “unsafe pathname” (such as a pathname that resolves the mail-delivery directory (e.g., /var/mail) is often through a symbolic link in a world-writable directory). In group or world writable. An adversarial user may use today's UNIX systems, solutions to this problem are typ- its write permission to create a hard link or symlink at ically built into (some) applications and use application- /var/mail/root that resolves to /etc/passwd. A specific knowledge about (un)safety of certain directories. simple-minded mail-delivery program that appends mail to In contrast, we seek solutions that can be implemented in the file /var/mail/root can have disastrous implica- the filesystem itself (or a library on top of it), thus providing tions for system security. -

OS X Support Essentials 10.9 Apple Pro Training Series
Apple Pro Training Series: OS X Support Essentials 10.9 Apple Pro Training Series Training Apple Pro Network Configuration Locations: One selected by user Automatic Work Home Test Ethernet Wi-Fi Ethernet 2 FireWire VPN Services: Multiple services activate and prioritized based on service order Understand OS X Mavericks underlying technologies, Configurestand-alone and networked Mac Troubleshoot software and hardware issues software components, and industry-standard protocols. computers with step-by-step instructions. using Apple-recommended procedures and tools. OS X Mavericks Supporting and Troubleshooting OS X Support Essentials 10.9 The Apple-Certified Way to Learn This is the official curriculum of the Apple Mavericks 101: OS X The Apple Pro Training Series is both a self-paced Support Essentials 10.9 course and preparation for Apple learning tool and the official curriculum of the Apple Training and Certified Support Professional (ACSP) 10.9 certification— Certification program. Upon completing the course material in this as well as a top-notch primer for anyone who needs to support, book, you can become an Apple Certified Support Professional by troubleshoot, or optimize OS X Mavericks. This guide provides passing the OS X Support Essentials 10.9 Exam. Work through this comprehensive coverage of Mavericks and is part of the Apple book as self-study material or attend a class at an Apple Authorized Pro Training series—the only Apple-certified books on the Training Center. To learn more, please visit training.apple.com. market. Designed for support technicians, help desk specialists, and ardent Mac users, this guide takes you deep inside the Also in the Apple Pro Training Series: Mavericks operating system.