IDOL Connector Framework Server 12.0 Administration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
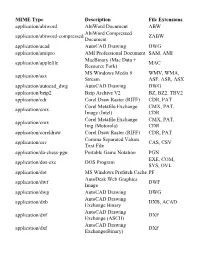
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

DXF Reference
AutoCAD 2012 DXF Reference February 2011 © 2011 Autodesk, Inc. All Rights Reserved. Except as otherwise permitted by Autodesk, Inc., this publication, or parts thereof, may not be reproduced in any form, by any method, for any purpose. Certain materials included in this publication are reprinted with the permission of the copyright holder. Trademarks The following are registered trademarks or trademarks of Autodesk, Inc., and/or its subsidiaries and/or affiliates in the USA and other countries: 3DEC (design/logo), 3December, 3December.com, 3ds Max, Algor, Alias, Alias (swirl design/logo), AliasStudio, Alias|Wavefront (design/logo), ATC, AUGI, AutoCAD, AutoCAD Learning Assistance, AutoCAD LT, AutoCAD Simulator, AutoCAD SQL Extension, AutoCAD SQL Interface, Autodesk, Autodesk Intent, Autodesk Inventor, Autodesk MapGuide, Autodesk Streamline, AutoLISP, AutoSnap, AutoSketch, AutoTrack, Backburner, Backdraft, Beast, Built with ObjectARX (logo), Burn, Buzzsaw, CAiCE, Civil 3D, Cleaner, Cleaner Central, ClearScale, Colour Warper, Combustion, Communication Specification, Constructware, Content Explorer, Dancing Baby (image), DesignCenter, Design Doctor, Designer's Toolkit, DesignKids, DesignProf, DesignServer, DesignStudio, Design Web Format, Discreet, DWF, DWG, DWG (logo), DWG Extreme, DWG TrueConvert, DWG TrueView, DXF, Ecotect, Exposure, Extending the Design Team, Face Robot, FBX, Fempro, Fire, Flame, Flare, Flint, FMDesktop, Freewheel, GDX Driver, Green Building Studio, Heads-up Design, Heidi, HumanIK, IDEA Server, i-drop, Illuminate Labs -

The Machine That Builds Itself: How the Strengths of Lisp Family
Khomtchouk et al. OPINION NOTE The Machine that Builds Itself: How the Strengths of Lisp Family Languages Facilitate Building Complex and Flexible Bioinformatic Models Bohdan B. Khomtchouk1*, Edmund Weitz2 and Claes Wahlestedt1 *Correspondence: [email protected] Abstract 1Center for Therapeutic Innovation and Department of We address the need for expanding the presence of the Lisp family of Psychiatry and Behavioral programming languages in bioinformatics and computational biology research. Sciences, University of Miami Languages of this family, like Common Lisp, Scheme, or Clojure, facilitate the Miller School of Medicine, 1120 NW 14th ST, Miami, FL, USA creation of powerful and flexible software models that are required for complex 33136 and rapidly evolving domains like biology. We will point out several important key Full list of author information is features that distinguish languages of the Lisp family from other programming available at the end of the article languages and we will explain how these features can aid researchers in becoming more productive and creating better code. We will also show how these features make these languages ideal tools for artificial intelligence and machine learning applications. We will specifically stress the advantages of domain-specific languages (DSL): languages which are specialized to a particular area and thus not only facilitate easier research problem formulation, but also aid in the establishment of standards and best programming practices as applied to the specific research field at hand. DSLs are particularly easy to build in Common Lisp, the most comprehensive Lisp dialect, which is commonly referred to as the “programmable programming language.” We are convinced that Lisp grants programmers unprecedented power to build increasingly sophisticated artificial intelligence systems that may ultimately transform machine learning and AI research in bioinformatics and computational biology. -

Meeting Planner Documentation
MEETING PLANNER Installation, Configuration, and User Guides Last Updated: April 24, 2018 EMS Software | emssoftware.com/help | 800.440.3994 | © 2018 EMS Software, LLC. All Rights Reserved. Table of Contents CHAPTER 1: Introduction to Meeting Planner 1 Contact Customer Support 1 CHAPTER 2: Network Architecture Diagram 2 2 CHAPTER 3: Hardware & Software Requirements 3 Hardware Requirements 3 1-5,000 active users 3 5,000-30,000 active users 4 30,000+ active users 5 Software Prerequisites 6 End-User Machines 6 Application Server 8 Exchange Server 10 Service Accounts 10 Database Server 11 CHAPTER 4: Hardware & Software Requirements Checklist 13 End user machines 13 Application Server 13 Web Server (Roles) 13 Message Queuing Services 14 Internet Information Services 14 Microsoft .NET Framework 14 Service Accounts 14 Database Server 14 SQL Server 14 CHAPTER 5: Server 2012 Prerequisite Setup 15 Application Server Prerequisite Setup 15 Web Server (Role) 15 Message Queuing Services 19 Internet Information Services (IIS) 19 Microsoft .NET Framework 21 Supporting Microsoft References: 22 Database Server Prerequisite Setup 22 SQL Server 22 CHAPTER 6: Server 2008 R2 Prerequisite Setup 25 Application Server Prerequisite Setup 25 Web Server (Roles) 25 Message Queuing Services 26 Internet Information Services (IIS) 27 Microsoft .NET Framework 28 Supporting Microsoft References: 29 Database Server Prerequisite Setup 29 SQL Server 29 CHAPTER 7: Application Server Installation 31 CHAPTER 8: Database Server Configuration 35 Identify Database 35 Restore Database -

An Evaluation of Go and Clojure
An evaluation of Go and Clojure A thesis submitted in partial satisfaction of the requirements for the degree Bachelors of Science in Computer Science Fall 2010 Robert Stimpfling Department of Computer Science University of Colorado, Boulder Advisor: Kenneth M. Anderson, PhD Department of Computer Science University of Colorado, Boulder 1. Introduction Concurrent programming languages are not new, but they have been getting a lot of attention more recently due to their potential with multiple processors. Processors have gone from growing exponentially in terms of speed, to growing in terms of quantity. This means processes that are completely serial in execution will soon be seeing a plateau in performance gains since they can only rely on one processor. A popular approach to using these extra processors is to make programs multi-threaded. The threads can execute in parallel and use shared memory to speed up execution times. These multithreaded processes can significantly speed up performance, as long as the number of dependencies remains low. Amdahl‘s law states that these performance gains can only be relative to the amount of processing that can be parallelized [1]. However, the performance gains are significant enough to be looked into. These gains not only come from the processing being divvied up into sections that run in parallel, but from the inherent gains from sharing memory and data structures. Passing new threads a copy of a data structure can be demanding on the processor because it requires the processor to delve into memory and make an exact copy in a new location in memory. Indeed some studies have shown that the problem with optimizing concurrent threads is not in utilizing the processors optimally, but in the need for technical improvements in memory performance [2]. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Agent-Based Architectures and Algorithms for Energy Management in Smart Gribs : Application to Smart Power Generation and Residential Demand Response Robin Roche
Agent-Based Architectures and Algorithms for Energy Management in Smart Gribs : Application to Smart Power Generation and Residential Demand Response Robin Roche To cite this version: Robin Roche. Agent-Based Architectures and Algorithms for Energy Management in Smart Gribs : Application to Smart Power Generation and Residential Demand Response. Other. Université de Technologie de Belfort-Montbeliard, 2012. English. NNT : 2012BELF0191. tel-00864268 HAL Id: tel-00864268 https://tel.archives-ouvertes.fr/tel-00864268 Submitted on 20 Sep 2013 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Université de Technologie de Belfort–Montbéliard Institut de Recherche sur les Transports, l’Énergie et la Société Laboratoire Systèmes et Transports École Doctorale Sciences pour l’Ingénieur et Microtechniques Algorithmes et Architectures Multi-Agents pour la Gestion de l’Énergie dans les Réseaux Électriques Intelligents Application aux Centrales à Turbines à Gaz et à l’Effacement Diffus Résidentiel Thèse no191 présentée et soutenue publiquement en vue de l’obtention du titre de Docteur en Génie Électrique par Robin Roche le 7 décembre 2012 Membres du jury : M. Mohamed Benbouzid IUT de Brest, LBMS Président M. Nouredine Hadjsaid INP Grenoble, G2Elab Rapporteur M. -

Hy Documentation Release 0.12.1+64.G5eb9283
hy Documentation Release 0.12.1+64.g5eb9283 Paul Tagliamonte Apr 14, 2017 Contents 1 Documentation Index 3 1.1 Quickstart................................................4 1.2 Tutorial..................................................5 1.2.1 Basic intro to Lisp for Pythonistas...............................5 1.2.2 Hy is a Lisp-flavored Python..................................7 1.2.3 Macros............................................. 12 1.2.4 Hy <-> Python interop..................................... 13 1.2.5 Protips!............................................. 14 1.3 Hy Style Guide.............................................. 14 1.3.1 Prelude............................................. 15 1.3.2 Layout & Indentation...................................... 15 1.3.3 Coding Style.......................................... 16 1.3.4 Conclusion........................................... 17 1.3.5 Thanks............................................. 17 1.4 Documentation Index.......................................... 18 1.4.1 Command Line Interface.................................... 18 1.4.2 Hy <-> Python interop..................................... 19 1.4.3 Hy (the language)........................................ 21 1.4.4 Hy Core............................................. 47 1.4.5 Reader Macros......................................... 65 1.4.6 Internal Hy Documentation................................... 66 1.5 Extra Modules Index........................................... 72 1.5.1 Anaphoric Macros....................................... 72 1.5.2 -

Scalable Speculative Parallelization on Commodity Clusters
Scalable Speculative Parallelization on Commodity Clusters Hanjun Kim Arun Raman Feng Liu Jae W. Leey David I. August Departments of Electrical Engineering and Computer Science y Parakinetics Inc. Princeton University Princeton, USA Princeton, USA [email protected] {hanjunk, rarun, fengliu, august}@princeton.edu Abstract by the cluster is difficult. For these reasons, such programs have been deemed unsuitable for execution on clusters. While clusters of commodity servers and switches are the most popular form of large-scale parallel computers, many programs are Recent research has demonstrated that a combination of not easily parallelized for execution upon them. In particular, high pipeline parallelism (DSWP), thread-level speculation (TLS), inter-node communication cost and lack of globally shared memory and speculative pipeline parallelism (Spec-DSWP) can un- appear to make clusters suitable only for server applications with lock significant amounts of parallelism in general-purpose abundant task-level parallelism and scientific applications with regu- programs on shared memory systems [6, 24, 27, 29, 30, 32, lar and independent units of work. Clever use of pipeline parallelism (DSWP), thread-level speculation (TLS), and speculative pipeline 36, 37]. Pipeline parallelization techniques such as DSWP parallelism (Spec-DSWP) can mitigate the costs of inter-thread partition a loop in such a way that the critical path is executed communication on shared memory multicore machines. This paper in a thread-local fashion, with off-critical path data flowing presents Distributed Software Multi-threaded Transactional memory unidirectionally through the pipeline. The combination of these (DSMTX), a runtime system which makes these techniques applicable two factors makes the program execution highly insensitive to non-shared memory clusters, allowing them to efficiently address inter-node communication costs. -

Easybuild Documentation Release 20210706.0 Ghent University
EasyBuild Documentation Release 20210907.0 Ghent University Tue, 07 Sep 2021 08:55:25 Contents 1 What is EasyBuild? 3 2 Concepts and terminology 5 2.1 EasyBuild framework..........................................5 2.2 Easyblocks................................................6 2.3 Toolchains................................................7 2.3.1 system toolchain.......................................7 2.3.2 dummy toolchain (DEPRECATED) ..............................7 2.3.3 Common toolchains.......................................7 2.4 Easyconfig files..............................................7 2.5 Extensions................................................8 3 Typical workflow example: building and installing WRF9 3.1 Searching for available easyconfigs files.................................9 3.2 Getting an overview of planned installations.............................. 10 3.3 Installing a software stack........................................ 11 4 Getting started 13 4.1 Installing EasyBuild........................................... 13 4.1.1 Requirements.......................................... 14 4.1.2 Using pip to Install EasyBuild................................. 14 4.1.3 Installing EasyBuild with EasyBuild.............................. 17 4.1.4 Dependencies.......................................... 19 4.1.5 Sources............................................. 21 4.1.6 In case of installation issues. .................................. 22 4.2 Configuring EasyBuild.......................................... 22 4.2.1 Supported configuration -

MS Exchange 2016
MS Exchange 2016 Deployment Guide UPDATED: 23 March 2021 MS Exchange 2016 Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved MS Exchange 2016 Table of Contents 1 Introduction 5 1.1 About This Manual 5 1.2 Related Firmware Version 5 1.3 Prerequisites 5 2 Exchange 2016 Overview 7 2.1 Understanding Server Load Balancing 7 2.2 Enable Subnet Originating Requests Globally 8 2.3 100-Continue Handling 9 2.4 Additional L7 Header 9 3 Virtual Service Templates 11 4 Configuring Virtual Services for Exchange 2016 12 4.1 HTTPS Offloaded and Reencrypt without ESP 12 4.1.1 Add SSL/TLS Certificate 12 4.2 HTTPS Offloaded and Reencrypt with ESP 14 4.2.1 Add SSL/TLS Certificate 15 4.2.2 Configure ESP 16 4.3 IMAP and IMAPS Virtual Service 18 4.4 IMAPS Offloaded and IMAP with STARTTLS Virtual Service 19 4.5 POP and POPS Virtual Service 20 4.6 POPS Offloaded and POP with STARTTLS Virtual Service 20 4.7 SMTP and SMTPS Virtual Service 21 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved MS Exchange 2016 4.8 SMTPS Offloaded and SMTP with STARTTLS Virtual Service 22 4.9 -

An Industrial Strength Theorem Prover for a Logic Based on Common Lisp
An Industrial Strength Theorem Prover for a Logic Based on Common Lisp y z Matt Kaufmannand J Strother Moore Personal use of this material is permitted. particular style of formal veri®cation that has shown consid- However, permission to reprint/republish this erable promise in recent years is the use of general-purpose material for advertising or promotional pur- automated reasoning systems to model systems and prove poses or for creating new collective works for properties of them. Every such reasoning system requires resale or redistribution to servers or lists, or considerable assistance from the user, which makes it im- to reuse any copyrighted component of this portant that the system provide convenient ways for the user work in other works must be obtained from the to interact with it. IEEE.1 One state-of-the-art general-purpose automated reason- ing system is ACL2: ªA Computational Logic for Applica- AbstractÐACL2 is a re-implemented extended version tive Common Lisp.º A number of automated reasoning of Boyer and Moore's Nqthm and Kaufmann's Pc-Nqthm, systems now exist, as we discuss below (Subsection 1.1). In intended for large scale veri®cation projects. This paper this paper we describe ACL2's offerings to the user for con- deals primarily with how we scaled up Nqthm's logic to an venientªindustrial-strengthºuse. WebegininSection2with ªindustrial strengthº programming language Ð namely, a a history of theACL2 project. Next, Section 3 describes the large applicative subset of Common Lisp Ð while preserv- logic supportedby ACL2, which has been designed for con- ing the use of total functions within the logic.