13 Embedded Communication Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1) What Is the Name of an Ethernet Cable That Contains Two
1) What is the name of an Ethernet cable that contains two electrical conductors ? A coaxial cable 2) What are the names of the two common conditions that degrade the signals on c opper-based cables? Crosstal and attenuation 3) Which topology requires the use of terminators? Bus 4) Which of the following topologies is implemented only logically, not physical ly? Ring 5) How many wire pairs are actually used on a typical UTP Ethernet network? Two 6) What is the name of the process of building a frame around network layer info rmation? Data encapsulation 7) Which of the connectors on a network interface adapter transmits data in para llel? The System bus connector 8) Which two of the following hardware resources do network interface adapters a lways require? I/O port address and IRQ 9) What is the name of the process by which a network interface adapter determin es when it should transmit its data over the network? Media Access Control 10) Which bus type is preferred for a NIC that will be connected to a Fast Ether net network? PCI 11) A passive hub does not do which of the following? Transmit management information using SNMP 12) To connect two Ethernet hubs together, you must do which of the following? Connect the uplink port in one hub to a standard port on the other 13) Which term describes a port in a Token Ring MAU that is not part of the ring ? Intelligent 14) A hub that functions as a repeater inhibits the effect of____________? Attenuation 15) You can use which of the following to connect two Ethernet computers togethe r using UTP -

Introducing Zigbee Theory and Practice Into Information and Computer Technology Disciplines
AC 2007-1072: INTRODUCING ZIGBEE THEORY AND PRACTICE INTO INFORMATION AND COMPUTER TECHNOLOGY DISCIPLINES Crystal Bateman, Brigham Young University Crystal Bateman is an Undergraduate Student at BYU studying Information Technology. Her academic interests include ubiquitous technologies and usability. She is currently finishing an honors thesis on using mobile ZigBee motes in a home environment, and enjoying life with her husband and two daughters Janell Armstrong, Brigham Young University Janell Armstrong is a Graduate Student in Information Technology at BYU. Her interests are in ZigBee and public key infrastructure. She has three years experience as a Teacher's Assistant. Student memberships include IEEE, IEEE-CS, ACM, SWE, ASEE. C. Richard Helps, Brigham Young University Richard Helps is the Program Chair of the Information Technology program at BYU and has been a faculty member in the School of Technology since 1986. His primary scholarly interests are in embedded and real-time computing and in technology education. He also has interests in human-computer interfacing. He has been involved in ABET accreditation for about 8 years and is a Commissioner of CAC-ABET and a CAC accreditation team chair. He spent ten years in industry designing industrial automation systems and in telecommunications. Professional memberships include IEEE, IEEE-CS, ACM, SIGITE, ASEE. Page 12.982.1 Page © American Society for Engineering Education, 2007 Introducing ZigBee Theory and Practice into Information and Computer Technology Disciplines Abstract As pervasive computing turns from the desktop model to the ubiquitous computing ideal, the development challenges become more complex than simply connecting a peripheral to a PC. A pervasive computing system has potentially hundreds of interconnected devices within a small area. -

An Analysis of IEEE 802.16 and Wimax Multicast Delivery
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Calhoun, Institutional Archive of the Naval Postgraduate School Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2007-09 An analysis of IEEE 802.16 and WiMAX multicast delivery Staub, Patrick A. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/3203 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS AN ANALYSIS OF IEEE 802.16 AND WIMAX MULTICAST DELIVERY by Patrick A. Staub September, 2007 Thesis Advisor: Bert Lundy Second Reader: George Dinolt Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington DC 20503. 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED September 2007 Master’s Thesis 4. TITLE AND SUBTITLE An Analysis of IEEE 802.16 and WiMAX 5. FUNDING NUMBERS Multicast Delivery 6. AUTHOR(S) Patrick A. Staub 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -

System Performance of Wireless Sensor Network Using Lora…
Computers, Materials & Continua Tech Science Press DOI:10.32604/cmc.2021.016922 Article System Performance of Wireless Sensor Network Using LoRa–Zigbee Hybrid Communication Van-Truong Truong1, Anand Nayyar2,* and Showkat Ahmad Lone3 1Faculty of Electrical and Electronic Engineering, Duy Tan University, Da Nang, 550000, Vietnam; Institute of Research and Development, Duy Tan University, Da Nang, 550000, Vietnam 2Graduate School, Duy Tan University, Da Nang 550000, Vietnam; Faculty of Information Technology, Duy Tan University, Da Nang, Vietnam 3Department of Basic Science, College of Science and Theoretical Studies, Saudi Electronic University, Jeddah Campus, KSA *Corresponding Author: Anand Nayyar. Email: [email protected] Received: 15 January 2021; Accepted: 17 February 2021 Abstract: Wireless sensor network (WSN) is considered as the fastest growing technology pattern in recent years because of its applicability in var- ied domains. Many sensor nodes with different sensing functionalities are deployed in the monitoring area to collect suitable data and transmit it to the gateway. Ensuring communications in heterogeneous WSNs, is a critical issue that needs to be studied. In this research paper, we study the system performance of a heterogeneous WSN using LoRa–Zigbee hybrid communi- cation. Specifically, two Zigbee sensor clusters and two LoRa sensor clusters are used and combined with two Zigbee-to-LoRa converters to communicate in a network managed by a LoRa gateway. The overall system integrates many different sensors in terms of types, communication protocols, and accuracy, which can be used in many applications in realistic environments such as on land, under water, or in the air. In addition to this, a synchronous man- agement software on ThingSpeak Web server and Blynk app is designed. -

Survey of Important Issues in UAV Communications Networks
1 Survey of Important Issues in UAV Communication Networks Lav Gupta*, Senior Member IEEE, Raj Jain, Fellow, IEEE, and Gabor Vaszkun technology that can be harnessed for military, public and civil Abstract—Unmanned Aerial Vehicles (UAVs) have enormous applications. Military use of UAVs is more than 25 years old potential in the public and civil domains. These are particularly primarily consisting of border surveillance, reconnaissance and useful in applications where human lives would otherwise be strike. Public use is by the public agencies such as police, endangered. Multi-UAV systems can collaboratively complete missions more efficiently and economically as compared to single public safety and transportation management. UAVs can UAV systems. However, there are many issues to be resolved provide timely disaster warnings and assist in speeding up before effective use of UAVs can be made to provide stable and rescue and recovery operations when the public communication reliable context-specific networks. Much of the work carried out in network gets crippled. They can carry medical supplies to areas the areas of Mobile Ad Hoc Networks (MANETs), and Vehicular rendered inaccessible. In situations like poisonous gas Ad Hoc Networks (VANETs) does not address the unique infiltration, wildfires and wild animal tracking UAVs could be characteristics of the UAV networks. UAV networks may vary from slow dynamic to dynamic; have intermittent links and fluid used to quickly envelope a large area without risking the safety topology. While it is believed that ad hoc mesh network would be of the personnel involved. most suitable for UAV networks yet the architecture of multi-UAV UAVs come networks has been an understudied area. -

Nomadic Communications
Nomadic Communications Renato Lo Cigno ANS Group – [email protected] Francesco Gringoli [email protected] http://disi.unitn.it/locigno/index.php/teaching-duties/nomadic-communications Copyright Quest’opera è protetta dalla licenza: Creative Commons Attribuzione-Non commerciale-Non opere derivate 2.5 Italia License Per i dettagli, consultare http://creativecommons.org/licenses/by-nc-nd/2.5/it/ What do you find on the web site • Exam Rules • Exam Details ... should be on ESSE3, but ... • Generic (useful) information • Teaching Material: normally posted at least the day before the lesson • Additional Material and links • Laboratories groups, rules, description and hints • News, Bulletin, How to find and meet me and Francesco, etc. • ... The web site is work in progress (well as of today working badly, but improving) and updated frequently(that’s at least my intention) Please don’t blame ME if you did’t read the last news J Program • Why “Nomadic” – Mobile vs. nomadic – Cellular vs. HotSpot – Local wireless communications • Some rehearsal – Access Control Protocols – Protocols and architectures – Services and primitives – IEEE 802 project – Nomadic communications positioning Program • WLAN – 802.11 Standard – 802.11 MAC – 802.11b/g/a/h/n/ac PHY – QoS and Differentiation enhancement: 802.11e – Mesh networks: 802.11s & other protocols – Other extensions: 802.11f/p/ad/ad/... Program • Ad-Hoc Networks – Stand-Alone WLANs – Routing and multi-hop in Ad-Hoc networks • Vehicular Networks Problems and scenarios – Specific issues -

Comparison of Network Topologies for Optical Fiber Communication
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 10, December- 2012 Comparison Of Network Topologies For Optical Fiber Communication Mr. Bhupesh Bhatia Ms. Ashima Bhatnagar Bhatia Department of Electronics and Communication, Department of Computer Science, Guru Prem Sukh Memorial College of Engineering, Tecnia Institute of Advanced Studies, Delhi Delhi Ms. Rashmi Ishrawat Department of Computer Science, Tecnia Institute of Advanced Studies, Delhi Abstract advent of the Information age. Optical In this paper, the various network topologies technologies can cost effectively meet have been compared. The signal is analyzed as it corporate bandwidth needs today and passes through each node in each of the network tomorrow. Internet connections offering topology. There is no appreciable signal degradation in the ring network. Also there is bandwidth on demand, to fiber on the increase in Quality factor i.e. signal keeps on LAN. Fiber to the home can provide true improving as it passes through the successiveIJERT IJERTbroadband connectivity for nodes. For the bus topology, the quality of signal telecommuters as well as converged goes on decreasing with increase in the number multimedia offerings for consumers [2]. of nodes and the power penalty goes on increasing. For the star topology, it is observed These different communication networks that received power values of each node at a can be configured in a number of same distance from the hub are same and the topologies. These include a bus, with or performance is same. For the tree topology, it is without a backbone, a star network, a observed that the performance is almost identical ring network, which can be redundant to the performance of ring topology, as signal quality is improved as it passes through the and/ or self-healing, or some successive nodes of the hierarchy. -

The Spirit of Wi-Fi
Rf: Wi-Fi_Text Dt: 09-Jan-2003 The Spirit of Wi-Fi where it came from where it is today and where it is going by Cees Links Wi-Fi pioneer of the first hour All rights reserved, © 2002, 2003 Cees Links The Spirit of Wi-Fi Table of Contents 0. Preface...................................................................................................................................................1 1. Introduction..........................................................................................................................................4 2. The Roots of Wi-Fi: Wireless LANs...................................................................................................9 2.1 The product and application background: networking ..............................................................9 2.2 The business background: convergence of telecom and computers? ......................................14 2.3 The application background: computers and communications ...............................................21 3. The original idea (1987 – 1991).........................................................................................................26 3.1 The radio legislation in the US .................................................................................................26 3.2 Pioneers .....................................................................................................................................28 3.3 Product definition ......................................................................................................................30 -

Unit 3 Basics of Network Technology
UNIT 3 BASICS OF NETWORK TECHNOLOGY Structure 3.0 Objectives 3.1 Introduction 3.2 Network Concept and Classification 3.2.1 Advantages of Networks 3.2.2 Network Classification 3.3 Local Area Network (LAN) Overview 3.3.1 LAN Topologies 3.3.2 LAN Access Methods 3.4 Wide Area Network 3.4.1 WAN Topologies 3.4.2 WAN Switching Methods 3.4.3 WAN Devices/Hardware 3.5 Wireless Technology 3.5.1 WiFi 3.5.2 WiMax 3.6 Summary 3.7 Answers to Self Check Exercises 3.8 Keywords 3.9 References and Further Reading 3.0 OBJECTIVES After going through this Unit, you will be able to: explain the concept of computer networks; understand different application of networks; differentiate between different types of computer networks based on size, connection and functioning; compare the different network topologies used in LAN and WAN; understand the working of LAN access methods; explain the working of networking devices used in WAN; know the importance of using networked system; and understand the concept of wireless technologies and standards. 3.1 INTRODUCTION With the ICT revolution the functioning of organisations has changed drastically. In a networked scenario organisations often need several people (may be at different locations) to input and process data simultaneously. In order to achieve this, a computer-networking model in which a number of separate but interconnected computers do the job has replaced the earlier standalone-computing model. By linking individual computers over 4 7 Network Fundamentals a network their productivity has been increased enormously. A most distinguishing characteristic of a general computer network is that data can enter or leave at any point and can be processed at any workstation. -

IEEE 802.5 (Token Ring) LAN
IEEE 802.5 (Token Ring) LAN Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF IEEE 802.5 (Token Ring): Ring Topology Shared ring medium: all nodes see all frames Round Robin MAC Protocol: determines which station can transmit A special 3-byte pattern, the token, circulates around the ring perpetually and represents the "right to transmit" This establishes round-robin media access Data flow is unidirectional All data flows in a particular direction around the ring; nodes receive frames from their upstream neighbor and forward them to their downstream neighbor Data rate: 4 or 16 Mbps R R R R IEEE 802.5 (Token Ring) Operation The token bit sequence circulates around the ring. Each station forwards the token if it does not have a frame to transmit. A station with data to send seizes the token (repeater now in transmit state) and begins sending it’s frame. It can transmit for length of time called the Token Hold Time (THT) = 10 mseconds. Each station forwards the frame. The destination station notices its address and saves a copy of the frame as it also forwards the frame. When the sender sees its frame return, it drains it from the ring and reinserts a token. When the last bit of the returning frame has been drained, the repeater switches immediately to the listen state. IEEE 802.5 (Token Ring) using a Hub The star-wired ring topology uses the physical layout of a star in conjunction with the token-passing data transmission method. -

The Network Stack (1) L41 Lecture 5 Dr Robert N
1/25/17 The Network Stack (1) L41 Lecture 5 Dr Robert N. M. Watson 25 January 2017 Reminder: where we left off last term • Long, long ago, but in a galaxy not so far away: • Lecture 3: The Process Model (1) • Lecture 4: The Process Model (2) • Lab 2: IPC buffer size and the probe effect • Lab 3: Micro-architectural effects of IPC • Explored several implied (and rejected) hypotheses: • Larger IO/IPC buffer sizes amortise system-call overhead • A purely architectural (SW) review dominates • The probe effect doesn’t matter in real-world workloads L41 Lecture 5 – The Network Stack (1) 1 1/25/17 This time: Introduction to Network Stacks Rapid tour across hardware and software: • Networking and the sockets API • Network-stack design principles: 1980s vs. today • Memory flow across hardware and software • Network-stack construction and work flows • Recent network-stack research L41 Lecture 5 – The Network Stack (1) Networking: A key OS function (1) • Communication between computer systems • Local-Area Networks (LANs) • Wide-Area Networks (WANs) • A network stack provides: • Sockets API and extensions • Interoperable, feature-rich, high-performance protocol implementations (e.g., IPv4, IPv6, ICMP, UDP, TCP, SCTP, …) • Security functions (e.g., cryptographic tunneling, firewalls...) • Device drivers for Network Interface Cards (NICs) • Monitoring and management interfaces (BPF, ioctl) • Plethora of support libraries (e.g., DNS) L41 Lecture 5 – The Network Stack (1) 2 1/25/17 Networking: A key OS function (2) • Dramatic changes over 30 years: 1980s: Early packet-switched networks, UDP+TCP/IP, Ethernet 1990s: Large-scale migration to IP; Ethernet VLANs 2000s: 1-Gigabit, then 10-Gigabit Ethernet; 802.11; GSM data 2010s: Large-scale deployment of IPv6; 40/100-Gbps Ethernet .. -
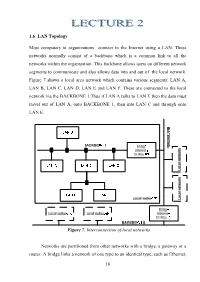
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges.