Word Boundary Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Noise Reduction Applied to Asteroseismology
PERTURBATIONS OF OBSERVATIONS. NOISE REDUCTION APPLIED TO ASTEROSEISMOLOGY. Javier Pascual Granado CCD 21/10/2009 Contents • Noise characterization and time series analysis Introduction The colors of noise Some examples in astrophysics Spectral estimation • Noise reduction applied to asteroseismology Asteroseismology: Origin and Objetives CoRoT A new method for noise reduction: Phase Adding Method (PAM) Aplications: Numerical experiment Star HD181231 Star 102719279 Javier Pascual Granado CCD 21/10/2009 2 Introduction Javier Pascual Granado CCD 21/10/2009 3 The Colors Of Noise Pink noise Javier Pascual Granado CCD 21/10/2009 4 The Colors Of Noise Red noise Javier Pascual Granado CCD 21/10/2009 5 Some Examples In Astrophysics •Thermal noise due to a nonzero temperature is approximately white gaussian noise. • Photon-shot noise due to statistical fluctuations in the measurements has a Poisson distribution and a power increasing with frequency. It is a problem with weak signals. • Also seismic noise affect to sensible ground instruments like LIGO (gravitational wave detector). Nevertheless, for LISA the noise characterization adopted is a gaussian noise. •Observations of the black hole candidate X-ray binary Cyg X-1 by EXOSAT, show a continuum power spectrum with a pink noise. • In asteroseismology the noise is assumed to be of white gaussian type. Javier Pascual Granado CCD 21/10/2009 6 Time Series: Spectral Estimation A light curve (or a photometric time series) is a set of data points ordered In time. ti-1-ti might not be constant. -
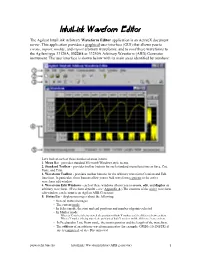
Intuilink Waveform Editor
IntuiLink Waveform Editor The Agilent IntuiLink Arbitrary Waveform Editor application is an ActiveX document server. This application provides a graphical user interface (GUI) that allows you to create, import, modify, and export arbitrary waveforms, and to send these waveforms to the Agilent type 33120A, 33220A or 33250A Arbitrary Waveform (ARB) Generator instrument. The user interface is shown below with its main areas identified by numbers: Let's look at each of these numbered areas in turn. 1. Menu Bar - provides standard Microsoft Windows style menus. 2. Standard Toolbar - provides toolbar buttons for such standard menu functions as Save, Cut, Paste, and Print. 3. Waveform Toolbar - provides toolbar buttons for the arbitrary waveform Creation and Edit functions. In particular, these buttons allow you to Add waveform segments to the active waveform edit window. 4. Waveform Edit Windows - each of these windows allows you to create, edit, and display an arbitrary waveform. (Waveform defaults – see: Appendix A.) The contents of the active waveform edit window can be sent to an Agilent ARB Generator. 5. Status Bar - displays messages about the following: - General status messages. - The current mode. - In Select mode, the start and end positions and number of points selected. - In Marker mode: · When an X marker is being moved, the positions of both X markers and the difference between them. · When a Y marker is being moved, the positions of both Y markers and the difference between them. - In Freehand or Line Draw mode, the cursor position and the length of the waveform. - The address of an arbitrary waveform generator (for example: GPIB0::10::INSTR) if one is connected, or else Disconnected. -

3A Whatissound Part 2
What is Sound? Part II Timbre & Noise Prayouandi (2010) - OneOhtrix Point Never 1 PSYCHOACOUSTICS ACOUSTICS LOUDNESS AMPLITUDE PITCH FREQUENCY QUALITY TIMBRE 2 Timbre / Quality everything that is not frequency / pitch or amplitude / loudness envelope - the attack, sustain, and decay portions of a sound spectra - the aggregate of simple waveforms (partials) that make up the frequency space of a sound. noise - the inharmonic and unpredictable fuctuations in the sound / signal 3 envelope 4 envelope ADSR 5 6 Frequency Spectrum 7 Spectral Analysis 8 Additive Synthesis 9 Organ Harmonics 10 Spectral Analysis 11 Cancellation and Reinforcement In-phase, out-of-phase and composite wave forms 12 (max patch) Tone as the sum of partials 13 harmonic / overtone series the fundamental is the lowest partial - perceived pitch A harmonic partial conforms to the overtone series which are whole number multiples of the fundamental frequency(f) (f)1, (f)2, (f)3, (f)4, etc. if f=110 110, 220, 330, 440 doubling = 1 octave An inharmonic partial is outside of the overtone series, it does not have a whole number multiple relationship with the fundamental. 14 15 16 Basic Waveforms fundamental only, no additional harmonics odd partials only (1,3,5,7...) 1 / p2 (3rd partial has 1/9 the energy of the fundamental) all partials 1 / p (3rd partial has 1/3 the energy of the fundamental) only odd-numbered partials 1 / p (3rd partial has 1/3 the energy of the fundamental) 17 (max patch) Spectrogram (snapshot) 18 Identifying Different Instruments 19 audio sonogram of 2 bird trills 20 Spear (software) audio surgery? isolate partials within a complex sound 21 the physics of noise Random additions to a signal By fltering white noise, we get different types (colors) of noise, parallels to visible light White Noise White noise is a random noise that contains an equal amount of energy in all frequency bands. -

Musical Elements in the Discrete-Time Representation of Sound
0 Musical elements in the discrete-time representation of sound RENATO FABBRI, University of Sao˜ Paulo VILSON VIEIRA DA SILVA JUNIOR, Cod.ai ANTONIOˆ CARLOS SILVANO PESSOTTI, Universidade Metodista de Piracicaba DEBORA´ CRISTINA CORREA,ˆ University of Western Australia OSVALDO N. OLIVEIRA JR., University of Sao˜ Paulo e representation of basic elements of music in terms of discrete audio signals is oen used in soware for musical creation and design. Nevertheless, there is no unied approach that relates these elements to the discrete samples of digitized sound. In this article, each musical element is related by equations and algorithms to the discrete-time samples of sounds, and each of these relations are implemented in scripts within a soware toolbox, referred to as MASS (Music and Audio in Sample Sequences). e fundamental element, the musical note with duration, volume, pitch and timbre, is related quantitatively to characteristics of the digital signal. Internal variations of a note, such as tremolos, vibratos and spectral uctuations, are also considered, which enables the synthesis of notes inspired by real instruments and new sonorities. With this representation of notes, resources are provided for the generation of higher scale musical structures, such as rhythmic meter, pitch intervals and cycles. is framework enables precise and trustful scientic experiments, data sonication and is useful for education and art. e ecacy of MASS is conrmed by the synthesis of small musical pieces using basic notes, elaborated notes and notes in music, which reects the organization of the toolbox and thus of this article. It is possible to synthesize whole albums through collage of the scripts and seings specied by the user. -

White Noise Generator Circuitry and Analysis
UNIVERSITY OF TEXAS AT SAN ANTONIO White Noise Generator Circuitry and Analysis David Sanchez 8/4/2008 Table of Contents Introduction .................................................................................................................................................. 3 Overview of the Circuit ................................................................................................................................ 3 Circuit Subsets .............................................................................................................................................. 4 Noise Generation Stage ........................................................................................................................ 4 Amplification of the Noise Signal .......................................................................................................... 6 Active Low-Pass Filter ........................................................................................................................... 7 Audio Output Stage............................................................................................................................... 8 Analysis ......................................................................................................................................................... 9 Discussion ................................................................................................................................................... 11 Conclusion ................................................................................................................................................. -

Deep Point Correlation Design
Deep Point Correlation Design THOMAS LEIMKÜHLER, MPI Informatik, Saarland Informatics Campus GURPRIT SINGH, MPI Informatik, Saarland Informatics Campus KAROL MYSZKOWSKI, MPI Informatik, Saarland Informatics Campus HANS-PETER SEIDEL, MPI Informatik, Saarland Informatics Campus TOBIAS RITSCHEL, University College London 10,000 10D points / s l1(radSpec(X)- BNOT)+ l1(spec(x(X))- STEP) 2D 1D 2D 1D Applications Point pattern Point Neural network Neural Design specication Design Result spectra Target spectra MC rendering Object placement Dithering Fig. 1. We suggest a framework for designing correlated point patterns. A design specification (left) is used to train an architecture mapping random points to correlated ones (middle). This architecture produces ten-thousands of points per second with use in rendering, object placement or dithering (right). Designing point patterns with desired properties can require substantial ACM Reference Format: effort, both in hand-crafting coding and mathematical derivation. Retaining Thomas Leimkühler, Gurprit Singh, Karol Myszkowski, Hans-Peter Seidel, these properties in multiple dimensions or for a substantial number of points and Tobias Ritschel. 2019. Deep Point Correlation Design. ACM Trans. Graph. can be challenging and computationally expensive. Tackling those two issues, 38, 6, Article 226 (November 2019), 17 pages. https://doi.org/10.1145/3355089. we suggest to automatically generate scalable point patterns from design 3356562 goals using deep learning. We phrase pattern generation as a deep compo- sition of weighted distance-based unstructured filters. Deep point pattern design means to optimize over the space of all such compositions according to 1 INTRODUCTION a user-provided point correlation loss, a small program which measures a pat- Point patterns have many important uses in computer graphics, tern’s fidelity in respect to its spatial or spectral statistics, linear or non-linear linking apparently disparate topics such as natural placement of (e. -

State Estimation Using Gaussian Process Regression for Colored Noise Systems
State Estimation using Gaussian Process Regression for Colored Noise Systems Kyuman Lee Eric N. Johnson School of Aerospace Engineering School of Aerospace Engineering Georgia Institute of Technology Georgia Institute of Technology Atlanta, GA 30332 Atlanta, GA 30332 404-422-3697 404-385-2519 [email protected] [email protected] Abstract—The goal of this study is to use Gaussian process (GP) the times of interest in the system; for brevity such errors are regression models to estimate the state of colored noise systems. called “colored” noise [1]. In audio engineering, electronics, The derivation of a Kalman filter assumes that the process noise physics, and many other fields, the color of a noise signal and measurement noise are uncorrelated and both white. In is generally understood to be some broad characteristic of relaxing those assumptions, the Kalman filter equations were its power spectrum. Different colors of noise have signif- modified to deal with the non-whiteness of each noise source. The standard Kalman filter ran on an augmented system that icantly different properties: for example, as audio signals had white noises and other approaches were also introduced they will sound different to human ears, and as images they depending on the forms of the noises. Those existing methods will have a visibly different texture. In image processing, can only work when the characteristics of the colored noise are the quality of images will directly influence the accuracy perfectly known. However, it is usually difficult to model a noise of locating landmarks. During sampling and transmission, without additional knowledge of the noise statistics. -

Characterization and Comparison of Optical Source Relative Intensity Noise and Effects in Optical Coherence Tomography
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Illinois Digital Environment for Access to Learning and Scholarship Repository CHARACTERIZATION AND COMPARISON OF OPTICAL SOURCE RELATIVE INTENSITY NOISE AND EFFECTS IN OPTICAL COHERENCE TOMOGRAPHY BY SUNGHWAN SHIN THESIS Submitted in partial fulfillment of the requirements for the degree of Master of Science in Electrical and Computer Engineering in the Graduate College of the University of Illinois at Urbana-Champaign, 2010 Urbana, Illinois Adviser: Professor Stephen A. Boppart ABSTRACT This thesis research investigates the effects of optical source noise in optical coherence tomography (OCT). While shot noise, thermal noise and relative intensity noise (RIN) (excess photon noise) constitute optical noise, RIN is the least understood and often the most significant factor limiting the sensitivity of an optical system. The existing and prevalent theory being used for estimating RIN for various light sources in OCT is questionable, and cannot be applied uniformly for different types of sources. The origin of noise in various sources varies significantly, owing to the different physical nature of photon generation. In this thesis, RIN of several OCT light sources are characterized and compared. Light sources include a super-luminescent diode (SLD), an erbium-doped fiber amplifier (EDFA), multiplexed SLDs, and a continuous wave (cw) laser. A method for the reduction of RIN by amplifying the SLD light output by using a gain-saturated semiconductor optical amplifier (SOA) is reported. Also, measurements using a time-domain OCT (TD-OCT) system are performed to verify the effects of optical source noise reduction on OCT data. -

Investigation of Improved Masking Noise for the Speech Privacy
INVESTIGATION OF IMPROVED MASKING NOISE FOR THE SPEECH PRIVACY by Allen Cho APPROVED BY SUPERVISORY COMMITTEE: ___________________________________________ Dr. Issa M. S. Panahi, Chair ___________________________________________ Dr. John H. L. Hansen ___________________________________________ Dr. P. K. Rajasekaran Copyright 2016 Allen Cho All Rights Reserved For the glory of God by the grace of God INVESTIGATION OF IMPROVED MASKING NOISE FOR THE SPEECH PRIVACY by ALLEN CHO, BS THESIS Presented to the Faculty of The University of Texas at Dallas in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE IN ELECTRICAL ENGINEERING THE UNIVERSITY OF TEXAS AT DALLAS December 2016 ACKNOWLEDGMENTS First and above all, I praise God almighty for providing me this opportunity and granting me the capability to proceed successfully. This thesis has come to its present form thanks to the assistance and guidance of several people. I would, therefore, like to offer my sincere thanks to all of them. Foremost, I would like to express my sincere gratitude to my advisor Dr. Issa Panahi for his continuous support for my Master’s degree study and research as well as for his patience, motivation, enthusiasm, and immense knowledge. His guidance helped me throughout my research and writing of this thesis. I could not have imagined having a better advisor and mentor for my graduate study. Besides my advisor, I would like to thank the rest of my thesis committee: Dr. P. K. Rajasekaran, and Prof. John Hansen for their encouragement, insightful comments, and challenging questions. My sincere thanks also goes to Speech Privacy Systems for offering me the valuable opportunity to study and research with their groups and leading me to work on diverse exciting projects. -

A Survey of Blue-Noise Sampling and Its Applications
Yan DM, Guo JW, Wang B et al. A survey of blue-noise sampling and its applications. JOURNAL OF COMPUTER SCIENCE AND TECHNOLOGY 30(3): 439–452 May 2015. DOI 10.1007/s11390-015-1535-0 A Survey of Blue-Noise Sampling and Its Applications 1,2 2 3 ý² Àïå Ê Dong-Ming Yan (î ), Member, CCF, ACM, Jian-Wei Guo ( ), Bin Wang ( ) 2 1,4 ¡· Xiao-Peng Zhang (Ü ), and Peter Wonka 1Visual Computing Center, King Abdullah University of Science and Technology, Thuwal 23955-6900, Saudi Arabia 2National Laboratory of Pattern Recognition, Institute of Automation, Chinese Academy of Sciences, Beijing 100190, China 3School of Software, Tsinghua University, Beijing 100084, China 4Department of Computer Science and Engineering, Arizona State University, Tempe, AZ 85287, U.S.A. E-mail: [email protected]; [email protected]; [email protected] E-mail: [email protected]; [email protected] Received March 9, 2015; revised April 2, 2015. Abstract In this paper, we survey recent approaches to blue-noise sampling and discuss their beneficial applications. We discuss the sampling algorithms that use points as sampling primitives and classify the sampling algorithms based on various aspects, e.g., the sampling domain and the type of algorithm. We demonstrate several well-known applications that can be improved by recent blue-noise sampling techniques, as well as some new applications such as dynamic sampling and blue-noise remeshing. Keywords blue-noise sampling, Poisson-disk sampling, Lloyd relaxation, rendering, remeshing 1 Introduction concentrated spikes in energy. Intuitively, blue-noise sampling generates randomized uniform distributions. -

Electronic Circuit Design for Audio Noise Elimination
DOKUZ EYLÜL UNIVERSITY GRADUATE SCHOOL OF NATURAL AND APPLIED SCIENCES ELECTRONIC CIRCUIT DESIGN FOR AUDIO NOISE ELIMINATION by Şekibe Şebnem TAS July, 2008 İZMİR ELECTRONIC CIRCUIT DESIGN FOR AUDIO NOISE ELIMINATION A Thesis Submitted to the Graduate School of Natural and Applied Sciences of Dokuz Eylül University In Partial Fulfillment of the Requirements for the Degree of Master of Science in Electrical and Electronics Engineering by Şekibe Şebnem TAS July, 2008 İZMİR M.Sc THESIS EXAMINATION RESULT FORM We have read the thesis entitled “ELECTRONIC CIRCUIT DESIGN FOR AUDIO NOISE ELIMINATION” completed by ŞEKİBE ŞEBNEM TAS under supervision of ASSOC. PROF. DR. UĞUR ÇAM and we certify that in our opinion it is fully adequate, in scope and in quality, as a thesis for the degree of Master of Science. Assoc. Prof. Dr. Uğur ÇAM (Jury Member) (Jury Member) Prof.Dr. Cahit HELVACI Director Graduate School of Natural and Applied Sciences ii ACKNOWLEDGEMENTS I would like to thank my advisor Assoc. Prof. Dr. Uğur Çam for his support, encouragement and valuable guidance. I am grateful to him for letting me share his professional knowledge and experience. I would like to thank TÜBİTAK for supporting me financially during my master study. I also would like to thank my colleagues at Vestel R&D department who helped me a lot and gave me the oppurtunity to use R&D laboratories during my research. I am also grateful to Kürşat Sarıarslan for his help and for sharing his experience with me during my study. Finally, I would like to thank my parents for always helping and supporting me throughout my life. -

Paranormal 101
Paranormal 101 The Colors of Noise We've all heard of "White Noise"...probably even saw the flick (I gave it a two thumbs down...or as they used to say "Hated it..."). Remember; Sound and Light obey the same laws of reflection. And with that being said - because the Spectrum of Sound Wave Frequencies are similar to the Spectrum of Light Wave Frequencies the different colors apply to different types of noise based on their distinct frequencies and characteristics. Thus, if the sound wave pattern of Pink Noise were rendered into light waves, the result would be Pink Light, etc. We all know that "White Light" is a combination of all colors in the visible light spectrum. When "White Light" shines through a prism (or water vapor, like when you see a rainbow); the "White Light" is broken apart into the colors of the visible light spectrum. Definitions of the Colors of Noise Black Noise; is noise that has a frequency spectrum of predominantly zero power level over all frequencies except for a few narrow bands or spikes. Basically, Black Noise is silence, no noise at all. Blue Noise; aka Azure Noise, is similar to Pink Noise except the power density increases 3 dB per octave as the frequency increases. In technical terms the density is proportional to the frequency. This can be good noise for dithering (digital audio processing technique used to prevent sound distortion). Brown Noise; has more energy at lower frequencies (decreasing by around 6dB per octave). To the human ear, Brown Noise is similar to White Noise but at a lower frequency.