Accepted Manuscript1.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Valorising the Iot Databox: Creating Value for Everyone Charith Perera1*, Susan Y
TRANSACTIONS ON EMERGING TELECOMMUNICATIONS TECHNOLOGIES Trans. Emerging Tel. Tech. 2017; 28:e3125 Published online 11 November 2016 in Wiley Online Library (wileyonlinelibrary.com). DOI: 10.1002/ett.3125 RESEARCH ARTICLE Valorising the IoT Databox: creating value for everyone Charith Perera1*, Susan Y. L. Wakenshaw2, Tim Baarslag3, Hamed Haddadi4, Arosha K. Bandara1, Richard Mortier5, Andy Crabtree6, Irene C. L. Ng2, Derek McAuley6 and Jon Crowcroft5 1 School of Computing and Communications, The Open University, Walton Hall, Milton Keynes MK7 6AA, UK 2 Warwick Manufacturing Group, University of Warwick, Coventry CV4 7AL, UK 3 University of Southampton, Southampton SO17 1BJ, UK 4 School of Electronic Engineering and Computer Science, Queen Mary University of London, Mile End Road, London E1 4NS, UK 5 Computer Laboratory, University of Cambridge, Cambridge CB3 0FD, UK 6 School of Computer Science, University of Nottingham, Jubilee Campus, Nottingham NG8 1BB, UK ABSTRACT The Internet of Things is expected to generate large amounts of heterogeneous data from diverse sources including physical sensors, user devices and social media platforms. Over the last few years, significant attention has been focused on personal data, particularly data generated by smart wearable and smart home devices. Making personal data available for access and trade is expected to become a part of the data-driven digital economy. In this position paper, we review the research challenges in building personal Databoxes that hold personal data and enable data access by other parties and potentially thus sharing of data with other parties. These Databoxes are expected to become a core part of future data marketplaces. Copyright © 2016 The Authors Transactions on Emerging Telecommunications Technologies Published by John Wiley & Sons, Ltd. -

A Systematic Survey of Firmware Extraction Techniques for Iot Devices
Breaking all the Things | A Systematic Survey of Firmware Extraction Techniques for IoT Devices Sebastian Vasile, David Oswald, and Tom Chothia University of Birmingham [email protected], [email protected], [email protected] Abstract. In this paper, we systematically review and categorize differ- ent hardware-based firmware extraction techniques, using 24 examples of real, wide-spread products, e.g. smart voice assistants (in particular Amazon Echo devices), alarm and access control systems, as well as home automation devices. We show that in over 45% of the cases, an exposed UART interface is sufficient to obtain a firmware dump, while in other cases, more complicated, yet still low-cost methods (e.g. JTAG or eMMC readout) are needed. In this regard, we perform an in-depth investiga- tion of the security concept of the Amazon Echo Plus, which contains significant protection methods against hardware-level attacks. Based on the results of our study, we give recommendations for countermeasures to mitigate the respective methods. 1 Introduction Extracting the firmware from IoT devices is a crucial first step when analysing the security of such systems. From a designer's point of view, preventing the firmware from falling into the hands of an adversary is often desirable: for in- stance, to protect cryptographic keys that identify a device and to impede prod- uct counterfeit or IP theft. The large variety of IoT devices results in different approaches to firmware extraction, depending on the device in question. Past work has looked at the state of security of IoT devices, e.g. -

INGRID KLEINIG · Stunt Actor · Precision Driver
INGRID KLEINIG · stunt actor · precision driver CREDITS FEATURE FILM 2010 THE BURNING MAN [Precision Driver] Burning Man Prod Jonathan Teplitzky 2010 MEI MEI [Stunt Actor] Portal Pictures Pauline Chan 2009 TOMORROW, WHEN THE WAR BEGAN [Stunt Double] Stuart Beattie 2008 MAO’S LAST DANCER [Stunt Double/Precision Driver] Bruce Beresford 2008 AUSTRALIA [Safety Diver] Twentieth Century Fox Baz Luhrman 2007 THE ETERNITY MAN [Movement Director] Goalpost Pictures Julien Temple 2006 BLACK WATER [Ass’t Safety] Aust. Film Commission D. Nerlich, A. Traucki 2005 SUPERMAN RETURNS [Stunt Actor] Red Sun Productions Bryan Singer 2004 SON OF THE MASK [Precision Driver] Dark Horse Ent. Lawrence Guterman TELEVISION 2010 RESCUE SPECIAL OPS SERIES 2&3 [Stunt Double/Stunt Driver] 2010 SEA PATROL SERIES 5 [Stunt Actor] AFFC, Geoff Bennett 2010 COPS L.A.C. [Stunt Double/Stunt Driver] Southern Star Bennett, Zwicky 2010 PANIC AT ROCK ISLAND [Stunt Actor/Double] Goalpost Pictures Tony Tilse 2010 RUSH [Stunt Actor/Stunt Double] Southern Star Prod Andrew Prowse 2010 THE MATTY JOHNS SHOW 2010 DEADLY WOMEN [Stunt Driver] Beyond Productions James Knox 2009 RESCUE SPECIAL OPS SERIES 1 [Stunt Actor/ Stunt Driver] 2009 A MODEL DAUGHTER [ Stunt Actor/Double] CB Productions Tony Tilse 2009 UNDERBELLY 2 [Stunt Double] Australian Film Finance Corporation 2009 ALL SAINTS [ Stunt Double] 7 Network 2008 EAST WEST 101 [Stunt Actor] ABC Peter Andrikidis 2008 FALSE WITNESS [Stunt Double / Precision Driver] Screentime P. Andrikidis 2008 SCORCHED [Stunt Double/Precision Driver] Essential Viewing Group T. Tilse 2008 PACKED TO THE RAFTERS [Precision Driver] 7 Network 2008 GLADIATORS [Stunt Actor] 7 Network 2008 HOME & AWAY [ Stunt Double] 7 Network 2007 MCLEODS DAUGHTERS [Stunt Driver] Endemol Southern Star 2007 CELEBRITY GOTCHA [Stunt Actor] 2006 SEA PATROL [Stunt Double] McElroy All Media 2005 SMALL CLAIMS 3 [Stunt Double / Stunt Driver] Network 10 Tony Tilse 2005 CHASING NATURE [ Stunt Actor/Stunt Driver] Beyond Productions J. -

Civil Charges Still May Be Laid “It’S Important to Keep the Reintroduced the Father of a Man Bob Eibl Said
Lavrick Engineering BOC Gas and Equipment Mechanical Repairs Specialist Labour Air-conditioning Hire Providers New Car Servicing & Warranty Phone: Olympic Way OLYMPIC DAM SA 5725 08 8671 2450 Ph: 86710404 Fax: 86710418 le08060609 Fax: 08 8671 0850 Thursday, June 8, 2006 Your Community Newspaper Ph: (08) 8671 2683 www.themonitor.com.au Fax: (08) 8671 2843 Mission Accomplished Mission ac- complished was the Mark and Rachel Young's resounding message Wedge-Tailed Eagle following an Arid sculpture has landed at the Recovery working bee Arid Recovery site on Sunday, May 28. More than 30 volunteers came along to do maintenance work at the site and complete a number of projects, including mounting a magnificent Wedge Tailed Eagle sculpture at the front entrance. Other works included replacing sand which had shifted at the hide – a shelter used at dusk to observe nocturnal mammals like bettongs and hopping mice eating at dusk. Sand was also replaced over the tunnel entrances to the viewing boxes alongside the hide. A conveyor belt used to stop bilbies digging into control sites was shifted onto a dune bordering the second expansion control site where the previous belt had deteriorated. Arid Recovery media offi cer Chris Schultz said moving the belts was a diffi cult task. Civil charges still may be laid “It’s important to keep the reintroduced The father of a man Bob Eibl said. lives, not just my son's,” A SafeWork SA was killed on July 19, mining safety at the mine. animals out of the second killed in an underground Bob Eibl said the he said. -

2017 Iot & Consumer Electronics Guide
PRESENTED BY 2017 IoT & CONSUMER ELECTRONICS ELECTRONICS COOLING® GUIDE SERIES | www.electronics-cooling.com 2017 IoT & CONSUMER ELECTRONICS GUIDE www.electronics-cooling.com | 2 | Electronics Cooling® Guide 2017 IoT & CONSUMER ELECTRONICS GUIDE TABLE OF CONTENTS Product Matrix (Thermal Management Manufacturers) 6 Product Selector 8 Electronics Cooling of Humans 10 MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management in 12 Consumer-Grade Digital Cameras MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management-Enabled 14 Products at CES 2017 MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management of IoT 19 Hardware: Gateways MP DIVAKAR, PHD Technical Editor, Electronics Cooling Inductive Wireless Charging is 23 Now a Thermal Design Problem DR. VINIT SINGH NuCurrent, CTO REFERENCE SECTION Ecosystems 28 Overview of Components of 29 IoT & Consumer Electronics Products Design Aids & Tools 32 Calculations 33 Index of Advertisers 34 www.electronics-cooling.com | 3 | Electronics Cooling® Guide FOREWARD In this inaugural issue of Electronics Cooling®’s series of digital guides, IoT & Consumer Electronics, we seek to sup- ply you with the latest in thermal management of consumer electronics and the Internet of Things. The intent of these digital guides is to bring you a collection of articles and information on thermal management ma- terials. This issue features a brief description of the ecosystem for thermal management products, an overview of thermal management challenges, and some high-level descriptions of thermal design elements. We also feature more in-depth coverage in longer articles on select products. There are many unique challenges that every thermal management professional has to address with respect to IoT and Consumer Electronics products. -

Google Onhub
built for User Guide OnHub REV1.0.1 1910011984 COPYRIGHT & TRADEMARKS Specifications are subject to change without notice. TP-Link is a registered trademark of TP-Link Technologies Co., Ltd. Google, Google On, OnHub and other trademarks are owned by Google Inc. Other brands and product names are trademarks of their respective holders. Copyright © 2016 TP-Link Technologies Co., Ltd. All rights reserved. http://www.tp-link.com 1 FCC STATEMENT This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures: • Reorient or relocate the receiving antenna. • Increase the separation between the equipment and receiver. • Connect the equipment into an outlet on a circuit different from that to which the receiver is connected. • Consult the dealer or an experienced radio/ TV technician for help. This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: ) 1 This device may not cause harmful interference. -

Iot Or Not Identifying Iot Devices in a Short Time Scale
The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science M.Sc. program - Research Track IoT or NoT Identifying IoT Devices in a Short Time Scale by Haim Levy M.Sc. dissertation, submitted in partial fulfillment of the requirements for the M.Sc. degree, research track, School of Computer Science The Interdisciplinary Center, Herzliya April 2020 This work was carried out under the supervision of Prof. Anat Bremlar- Barr and the assistance of Prof. Zohar Yakhini from the Efi Arazi School of Computer Science, The Interdisciplinary Center, Herzliya. Abstract In recent years the number of IoT devices in home networks has increased dra- matically. Whenever a new device connects to the network, it must be quickly managed and secured using the relevant security mechanism or QoS policy. Thus a key challenge is to distinguish between IoT and NoT devices in a matter of min- utes. Unfortunately, there is no clear indication of whether a device in a network is an IoT. In this paper, we propose different classifiers that identify a device as IoT or non-IoT, in a short time scale, and with high accuracy. Our classifiers were constructed using machine learning techniques on a seen (training) dataset and were tested on an unseen (test) dataset. They successfully classified devices that were not in the seen dataset with accuracy above 95%. The first classifier is a logistic regression classifier based on traffic features. The sec- ond classifier is based on features we retrieve from DHCP packets. Finally, we present a unified classifier that leverages the advantages of the other two classi- fiers. -

Investigating and Prosecuting Cyber Crime: Forensic Dependencies and Barriers to Justice
International Journal of Cyber Criminology Vol 9 Issue 1 January – June 2015 Copyright © 2015 International Journal of Cyber Criminology (IJCC) – Publisher & Editor-in-Chief – K. Jaishankar ISSN: 0973-5089 - January – June 2015. Vol. 9 (1): 55–119. DOI: 10.5281/zenodo.22387 This is an Open Access article distributed under the terms of the Creative Commons Attribution-NonCommercial-ShareAlikeHTU 4.0 International (CC-BY-NC-SA 4.0) License,UTH whichT permits unrestricted non-commercial use,T distribution, and reproduction in any medium, provided the original work is properly cited. ThisT license does not permit commercial exploitation or the creation of derivative works without specific permission. Investigating and Prosecuting Cyber Crime: Forensic Dependencies and Barriers to Justice Cameron S. D. Brown1 Australian National University, Australia Abstract The primary goal of this paper is to raise awareness regarding legal loopholes and enabling technologies, which facilitate acts of cyber crime. In perusing these avenues of inquiry, the author seeks to identify systemic impediments which obstruct police investigations, prosecutions, and digital forensics interrogations. Existing academic research on this topic has tended to highlight theoretical perspectives when attempting to explain technology aided crime, rather than presenting practical insights from those actually tasked with working cyber crime cases. The author offers a grounded, pragmatic approach based on the in-depth experience gained serving with police task-forces, government agencies, private sector, and international organizations. The secondary objective of this research encourages policy makers to reevaluate strategies for combating the ubiquitous and evolving threat posed by cyber- criminality. Research in this paper has been guided by the firsthand global accounts (via the author’s core involvement in the preparation of the Comprehensive Study on Cybercrime (United Nations Office on Drugs and Crime, 2013) and is keenly focused on core issues of concern, as voiced by the international community. -

Avoid the Silos and Help Build the True Internet of Things
Avoid the Silos and Help Build the True Internet of Things April 2016 Aaron Vernon, CTO at Higgns [email protected] I N T R O D U C T I O N ● Aaron Vernon, CTO at Higgns ● Previously I was VP Software Engineering at LIFX and CTO at Two Bulls ● Chair of the AllSeen Alliance Common Frameworks Working Group ● I am going to cover the following: ○ The complexities of the current IoT landscape ○ How this affects companies and users ○ The Internet of Silos example ○ How we can work together better Transports W i F i ● Uses the 802.11 standard ● Standard on all mobile devices and routers ● Has become ubiquitous for users ● Great range ● Great bandwidth ● High power consumption ● High cost ● Onboarding experience can be complicated ● Examples: Nest Cam, LIFX, Canary, Honeywell Lyric B L U E T O O T H S M A R T ● Standard on most mobile devices ● Becoming increasingly ubiquitous ● Low bandwidth ● Medium range ● Low power consumption ● Low cost ● Smart Mesh is being worked on ● Examples: Flic, Ilumi, Elgato Eve Z I G B E E ● Uses the 802.15.4 standard ● Low bandwidth ● Low range ● Low power consumption ● Very low cost ● Forms a mesh network ● Typically requires a hub for the radio ● Known to have interop and interference problems ● Examples: Phillips Hue, large amount of sensors and actuators Z W A V E ● Proprietary - chips developed by a single manufacturer ● Uses different frequencies in different countries ● Low bandwidth ● Medium range ● Low power consumption ● Very low cost ● Forms a mesh network ● Better interoperability and less interference -

Estado Diario Subdirección De Marcas 17/01/2018 1
Estado Diario Subdirección de Marcas 17/01/2018 Sección M1: Observaciones de Forma Solicitud Representante Tipo signo Marca Observaciones 1252792 Patricio de la Barra , en representación de Mixta FITÓ Semillas Fito, S.A. 1252793 Patricio de la Barra , en representación de Mixta FITÓ Semillas Fito, S.A. 1259458 SILVA Y CIA., en representación de Johnson Denominativa JOHNSON CONTROLS Controls Technology Company 1259839 ALESSANDRI & COMPAÑIA, en representación Mixta CENTRAL PERK de Warner Bros. Entertainment Inc. 1265854 SARGENT & KRAHN, en representación de Denominativa STARR STARR INTERNATIONAL COMPANY INC. 1266201 Ricardo Cabrera Fernández, en representación Mixta PUERTAS ABIERTAS de ELEODORO TORRES GONZALEZ 1266365 Jorge Luis Pino Zúñiga, en representación de Mixta BATHLUX BATHROOM EXPERTS HONGYU WANG OTAY 2015, S. L. B-90200320 1266536 Nicolo Antonio Lira Airola Mixta Cerveza Chercán 1270401 JULIO CESAR AVALOS CARROZA, en Denominativa SMART TAPE representación de SOC. COM. SOLCOMER LTDA. 1272227 Patricio Eduardo Aguilera Diaz, en representación Denominativa CRIN DE RARI de Maestra Madre Crin SpA y Agrupación de Artesanas de Rari 1273353 JFM FOOD SPA Denominativa El Bajon del Maipo 1273862 KAREN PUPKIN RUTMAN, en representación de Mixta CLINIK R ODONTOLOGÍA CLINIKR SPA 1274567 Opazo Cancino Francisco Omar Mixta OFC Landi-Hartog 1274704 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta PACERS GAMING en representación de NBA Properties, Inc. 1274708 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta PISTONS GT en representación de NBA Properties, Inc. 1274710 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta CAVS LEGION GC en representación de NBA Properties, Inc. 1274711 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta MAVS GAMING en representación de NBA Properties, Inc. 1 Estado Diario Subdirección de Marcas 17/01/2018 Sección M1: Observaciones de Forma Solicitud Representante Tipo signo Marca Observaciones 1274713 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta KINGS GUARD GAMING en representación de NBA Properties, Inc. -
User Preferences, Network Cookies and Neutrality
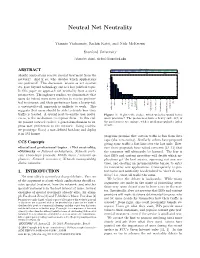
Neutral Net Neutrality Yiannis Yiakoumis, Sachin Katti, and Nick McKeown Stanford University ABSTRACT Alexa ranking 1 10 100 1000 >5000 Should applications receive special treatment from the network? And if so, who decides which applications 10 are preferred? This discussion, known as net neutral- 8 ity, goes beyond technology and is a hot political topic. 6 In this paper we approach net neutrality from a user’s # of users 4 perspective. Through user studies, we demonstrate that 2 users do indeed want some services to receive preferen- tial treatment; and their preferences have a heavy-tail: skai.gr nbc.com cnn.com hulu.com cucirca.eu netflix.com abc.go.com a one-size-fits-all approach is unlikely to work. This speetest.net facebook.com starsports.com mail.google.com usanetwork.com espncricinfo.com ticketmaster.com suggests that users should be able to decide how their intercallonline.com ondemandkorea.com traffic is treated. A crucial part to enable user prefer- Figure 1: If given the choice, which websites would home ences, is the mechanism to express them. To this end, users prioritize? The preferences have a heavy tail: 43% of we present network cookies, a general mechanism to ex- the preferences are unique, with a median popularity index press user preferences to the network. Using cookies, of 223. we prototype Boost, a user-defined fast-lane and deploy it in 161 homes. programs promise that certain traffic is free from data caps (aka zero-rating). Similarly, others have proposed CCS Concepts giving some traffic a fast-lane over the last mile. -

Valorising the Iot Databox: Creating Value for Everyone Charith Perera1*, Susan Y
TRANSACTIONS ON EMERGING TELECOMMUNICATIONS TECHNOLOGIES Trans. Emerging Tel. Tech. (2016) Published online in Wiley Online Library (wileyonlinelibrary.com). DOI: 10.1002/ett.3125 RESEARCH ARTICLE Valorising the IoT Databox: creating value for everyone Charith Perera1*, Susan Y. L. Wakenshaw2, Tim Baarslag3, Hamed Haddadi4, Arosha K. Bandara1, Richard Mortier5, Andy Crabtree6, Irene C. L. Ng2, Derek McAuley6 and Jon Crowcroft5 1 School of Computing and Communications, The Open University, Walton Hall, Milton Keynes MK7 6AA, UK 2 Warwick Manufacturing Group, University of Warwick, Coventry CV4 7AL, UK 3 University of Southampton, Southampton SO17 1BJ, UK 4 School of Electronic Engineering and Computer Science, Queen Mary University of London, Mile End Road, London E1 4NS, UK 5 Computer Laboratory, University of Cambridge, Cambridge CB3 0FD, UK 6 School of Computer Science, University of Nottingham, Jubilee Campus, Nottingham NG8 1BB, UK ABSTRACT The Internet of Things is expected to generate large amounts of heterogeneous data from diverse sources including physical sensors, user devices and social media platforms. Over the last few years, significant attention has been focused on personal data, particularly data generated by smart wearable and smart home devices. Making personal data available for access and trade is expected to become a part of the data-driven digital economy. In this position paper, we review the research challenges in building personal Databoxes that hold personal data and enable data access by other parties and potentially thus sharing of data with other parties. These Databoxes are expected to become a core part of future data marketplaces. Copyright © 2016 The Authors Transactions on Emerging Telecommunications Technologies Published by John Wiley & Sons, Ltd.