Valorising the Iot Databox: Creating Value for Everyone Charith Perera1*, Susan Y
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Systematic Survey of Firmware Extraction Techniques for Iot Devices
Breaking all the Things | A Systematic Survey of Firmware Extraction Techniques for IoT Devices Sebastian Vasile, David Oswald, and Tom Chothia University of Birmingham [email protected], [email protected], [email protected] Abstract. In this paper, we systematically review and categorize differ- ent hardware-based firmware extraction techniques, using 24 examples of real, wide-spread products, e.g. smart voice assistants (in particular Amazon Echo devices), alarm and access control systems, as well as home automation devices. We show that in over 45% of the cases, an exposed UART interface is sufficient to obtain a firmware dump, while in other cases, more complicated, yet still low-cost methods (e.g. JTAG or eMMC readout) are needed. In this regard, we perform an in-depth investiga- tion of the security concept of the Amazon Echo Plus, which contains significant protection methods against hardware-level attacks. Based on the results of our study, we give recommendations for countermeasures to mitigate the respective methods. 1 Introduction Extracting the firmware from IoT devices is a crucial first step when analysing the security of such systems. From a designer's point of view, preventing the firmware from falling into the hands of an adversary is often desirable: for in- stance, to protect cryptographic keys that identify a device and to impede prod- uct counterfeit or IP theft. The large variety of IoT devices results in different approaches to firmware extraction, depending on the device in question. Past work has looked at the state of security of IoT devices, e.g. -

2017 Iot & Consumer Electronics Guide
PRESENTED BY 2017 IoT & CONSUMER ELECTRONICS ELECTRONICS COOLING® GUIDE SERIES | www.electronics-cooling.com 2017 IoT & CONSUMER ELECTRONICS GUIDE www.electronics-cooling.com | 2 | Electronics Cooling® Guide 2017 IoT & CONSUMER ELECTRONICS GUIDE TABLE OF CONTENTS Product Matrix (Thermal Management Manufacturers) 6 Product Selector 8 Electronics Cooling of Humans 10 MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management in 12 Consumer-Grade Digital Cameras MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management-Enabled 14 Products at CES 2017 MP DIVAKAR, PHD Technical Editor, Electronics Cooling Thermal Management of IoT 19 Hardware: Gateways MP DIVAKAR, PHD Technical Editor, Electronics Cooling Inductive Wireless Charging is 23 Now a Thermal Design Problem DR. VINIT SINGH NuCurrent, CTO REFERENCE SECTION Ecosystems 28 Overview of Components of 29 IoT & Consumer Electronics Products Design Aids & Tools 32 Calculations 33 Index of Advertisers 34 www.electronics-cooling.com | 3 | Electronics Cooling® Guide FOREWARD In this inaugural issue of Electronics Cooling®’s series of digital guides, IoT & Consumer Electronics, we seek to sup- ply you with the latest in thermal management of consumer electronics and the Internet of Things. The intent of these digital guides is to bring you a collection of articles and information on thermal management ma- terials. This issue features a brief description of the ecosystem for thermal management products, an overview of thermal management challenges, and some high-level descriptions of thermal design elements. We also feature more in-depth coverage in longer articles on select products. There are many unique challenges that every thermal management professional has to address with respect to IoT and Consumer Electronics products. -

Google Onhub
built for User Guide OnHub REV1.0.1 1910011984 COPYRIGHT & TRADEMARKS Specifications are subject to change without notice. TP-Link is a registered trademark of TP-Link Technologies Co., Ltd. Google, Google On, OnHub and other trademarks are owned by Google Inc. Other brands and product names are trademarks of their respective holders. Copyright © 2016 TP-Link Technologies Co., Ltd. All rights reserved. http://www.tp-link.com 1 FCC STATEMENT This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures: • Reorient or relocate the receiving antenna. • Increase the separation between the equipment and receiver. • Connect the equipment into an outlet on a circuit different from that to which the receiver is connected. • Consult the dealer or an experienced radio/ TV technician for help. This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: ) 1 This device may not cause harmful interference. -

Iot Or Not Identifying Iot Devices in a Short Time Scale
The Interdisciplinary Center, Herzlia Efi Arazi School of Computer Science M.Sc. program - Research Track IoT or NoT Identifying IoT Devices in a Short Time Scale by Haim Levy M.Sc. dissertation, submitted in partial fulfillment of the requirements for the M.Sc. degree, research track, School of Computer Science The Interdisciplinary Center, Herzliya April 2020 This work was carried out under the supervision of Prof. Anat Bremlar- Barr and the assistance of Prof. Zohar Yakhini from the Efi Arazi School of Computer Science, The Interdisciplinary Center, Herzliya. Abstract In recent years the number of IoT devices in home networks has increased dra- matically. Whenever a new device connects to the network, it must be quickly managed and secured using the relevant security mechanism or QoS policy. Thus a key challenge is to distinguish between IoT and NoT devices in a matter of min- utes. Unfortunately, there is no clear indication of whether a device in a network is an IoT. In this paper, we propose different classifiers that identify a device as IoT or non-IoT, in a short time scale, and with high accuracy. Our classifiers were constructed using machine learning techniques on a seen (training) dataset and were tested on an unseen (test) dataset. They successfully classified devices that were not in the seen dataset with accuracy above 95%. The first classifier is a logistic regression classifier based on traffic features. The sec- ond classifier is based on features we retrieve from DHCP packets. Finally, we present a unified classifier that leverages the advantages of the other two classi- fiers. -

Avoid the Silos and Help Build the True Internet of Things
Avoid the Silos and Help Build the True Internet of Things April 2016 Aaron Vernon, CTO at Higgns [email protected] I N T R O D U C T I O N ● Aaron Vernon, CTO at Higgns ● Previously I was VP Software Engineering at LIFX and CTO at Two Bulls ● Chair of the AllSeen Alliance Common Frameworks Working Group ● I am going to cover the following: ○ The complexities of the current IoT landscape ○ How this affects companies and users ○ The Internet of Silos example ○ How we can work together better Transports W i F i ● Uses the 802.11 standard ● Standard on all mobile devices and routers ● Has become ubiquitous for users ● Great range ● Great bandwidth ● High power consumption ● High cost ● Onboarding experience can be complicated ● Examples: Nest Cam, LIFX, Canary, Honeywell Lyric B L U E T O O T H S M A R T ● Standard on most mobile devices ● Becoming increasingly ubiquitous ● Low bandwidth ● Medium range ● Low power consumption ● Low cost ● Smart Mesh is being worked on ● Examples: Flic, Ilumi, Elgato Eve Z I G B E E ● Uses the 802.15.4 standard ● Low bandwidth ● Low range ● Low power consumption ● Very low cost ● Forms a mesh network ● Typically requires a hub for the radio ● Known to have interop and interference problems ● Examples: Phillips Hue, large amount of sensors and actuators Z W A V E ● Proprietary - chips developed by a single manufacturer ● Uses different frequencies in different countries ● Low bandwidth ● Medium range ● Low power consumption ● Very low cost ● Forms a mesh network ● Better interoperability and less interference -

Estado Diario Subdirección De Marcas 17/01/2018 1
Estado Diario Subdirección de Marcas 17/01/2018 Sección M1: Observaciones de Forma Solicitud Representante Tipo signo Marca Observaciones 1252792 Patricio de la Barra , en representación de Mixta FITÓ Semillas Fito, S.A. 1252793 Patricio de la Barra , en representación de Mixta FITÓ Semillas Fito, S.A. 1259458 SILVA Y CIA., en representación de Johnson Denominativa JOHNSON CONTROLS Controls Technology Company 1259839 ALESSANDRI & COMPAÑIA, en representación Mixta CENTRAL PERK de Warner Bros. Entertainment Inc. 1265854 SARGENT & KRAHN, en representación de Denominativa STARR STARR INTERNATIONAL COMPANY INC. 1266201 Ricardo Cabrera Fernández, en representación Mixta PUERTAS ABIERTAS de ELEODORO TORRES GONZALEZ 1266365 Jorge Luis Pino Zúñiga, en representación de Mixta BATHLUX BATHROOM EXPERTS HONGYU WANG OTAY 2015, S. L. B-90200320 1266536 Nicolo Antonio Lira Airola Mixta Cerveza Chercán 1270401 JULIO CESAR AVALOS CARROZA, en Denominativa SMART TAPE representación de SOC. COM. SOLCOMER LTDA. 1272227 Patricio Eduardo Aguilera Diaz, en representación Denominativa CRIN DE RARI de Maestra Madre Crin SpA y Agrupación de Artesanas de Rari 1273353 JFM FOOD SPA Denominativa El Bajon del Maipo 1273862 KAREN PUPKIN RUTMAN, en representación de Mixta CLINIK R ODONTOLOGÍA CLINIKR SPA 1274567 Opazo Cancino Francisco Omar Mixta OFC Landi-Hartog 1274704 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta PACERS GAMING en representación de NBA Properties, Inc. 1274708 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta PISTONS GT en representación de NBA Properties, Inc. 1274710 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta CAVS LEGION GC en representación de NBA Properties, Inc. 1274711 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta MAVS GAMING en representación de NBA Properties, Inc. 1 Estado Diario Subdirección de Marcas 17/01/2018 Sección M1: Observaciones de Forma Solicitud Representante Tipo signo Marca Observaciones 1274713 ESTUDIO FEDERICO VILLASECA Y COMPAÑIA, Mixta KINGS GUARD GAMING en representación de NBA Properties, Inc. -
User Preferences, Network Cookies and Neutrality
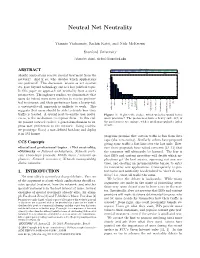
Neutral Net Neutrality Yiannis Yiakoumis, Sachin Katti, and Nick McKeown Stanford University ABSTRACT Alexa ranking 1 10 100 1000 >5000 Should applications receive special treatment from the network? And if so, who decides which applications 10 are preferred? This discussion, known as net neutral- 8 ity, goes beyond technology and is a hot political topic. 6 In this paper we approach net neutrality from a user’s # of users 4 perspective. Through user studies, we demonstrate that 2 users do indeed want some services to receive preferen- tial treatment; and their preferences have a heavy-tail: skai.gr nbc.com cnn.com hulu.com cucirca.eu netflix.com abc.go.com a one-size-fits-all approach is unlikely to work. This speetest.net facebook.com starsports.com mail.google.com usanetwork.com espncricinfo.com ticketmaster.com suggests that users should be able to decide how their intercallonline.com ondemandkorea.com traffic is treated. A crucial part to enable user prefer- Figure 1: If given the choice, which websites would home ences, is the mechanism to express them. To this end, users prioritize? The preferences have a heavy tail: 43% of we present network cookies, a general mechanism to ex- the preferences are unique, with a median popularity index press user preferences to the network. Using cookies, of 223. we prototype Boost, a user-defined fast-lane and deploy it in 161 homes. programs promise that certain traffic is free from data caps (aka zero-rating). Similarly, others have proposed CCS Concepts giving some traffic a fast-lane over the last mile. -

Valorising the Iot Databox: Creating Value for Everyone Charith Perera1*, Susan Y
TRANSACTIONS ON EMERGING TELECOMMUNICATIONS TECHNOLOGIES Trans. Emerging Tel. Tech. (2016) Published online in Wiley Online Library (wileyonlinelibrary.com). DOI: 10.1002/ett.3125 RESEARCH ARTICLE Valorising the IoT Databox: creating value for everyone Charith Perera1*, Susan Y. L. Wakenshaw2, Tim Baarslag3, Hamed Haddadi4, Arosha K. Bandara1, Richard Mortier5, Andy Crabtree6, Irene C. L. Ng2, Derek McAuley6 and Jon Crowcroft5 1 School of Computing and Communications, The Open University, Walton Hall, Milton Keynes MK7 6AA, UK 2 Warwick Manufacturing Group, University of Warwick, Coventry CV4 7AL, UK 3 University of Southampton, Southampton SO17 1BJ, UK 4 School of Electronic Engineering and Computer Science, Queen Mary University of London, Mile End Road, London E1 4NS, UK 5 Computer Laboratory, University of Cambridge, Cambridge CB3 0FD, UK 6 School of Computer Science, University of Nottingham, Jubilee Campus, Nottingham NG8 1BB, UK ABSTRACT The Internet of Things is expected to generate large amounts of heterogeneous data from diverse sources including physical sensors, user devices and social media platforms. Over the last few years, significant attention has been focused on personal data, particularly data generated by smart wearable and smart home devices. Making personal data available for access and trade is expected to become a part of the data-driven digital economy. In this position paper, we review the research challenges in building personal Databoxes that hold personal data and enable data access by other parties and potentially thus sharing of data with other parties. These Databoxes are expected to become a core part of future data marketplaces. Copyright © 2016 The Authors Transactions on Emerging Telecommunications Technologies Published by John Wiley & Sons, Ltd. -

Swann Security with the Google Assistant Setup Guide
THE SWANN SECURITY SERVICE WITH GOOGLE ASSISTANT SETUP GUIDE English 1 SWANN SECURITY WORKS WITH THE GOOGLE ASSISTANT Now it’s even easier to see what’s happening. You can ask your Google Assistant to show your Swann Security Cameras on your TV with Chromecast. Read this guide to learn how to connect your Swann Security cameras to your Google Assistant and enable voice control. GETTING STARTED Before you start, please make sure that: → You have the Swann Security app → You have a Swann Security account with a Swann device(s) paired → You have a Chromecast-connected TV → You have the Google Home app on your phone → You have the Google Assistant (built-in or app) on your phone or a Google Home device installed. For more information about the Google Assistant, see "Get started with the Google Assistant on your phone or tablet" 2 LINKING TO THE GOOGLE ASSISTANT To use Google Assistant voice control with your Swann Security cameras, follow these steps: STEP 1 STEP 2 STEP 3 STEP 4 Open the Google Tap the Home tab Tap + in the top left Choose Set up Home app. at the bottom of the corner. Device. screen. 3 LINKING TO THE GOOGLE ASSISTANT STEP 5 STEP 6 STEP 7 STEP 8 Choose "Have Scroll the list or tap The “Swann To link the Swann something already and search for Security” service Security service, set up" under “Swann Security”. will appear in the you will need your Works with Google. results. Tap it. Swann Security account credentials. 4 LINKING TO THE GOOGLE ASSISTANT STEP 9 STEP 10 STEP 11 Enter the email and Google Assistant Google Assistant is now ready to password associated will link your Swann interact with your cameras. -
Apple Homekit
Avoid the silos and help build the true Internet of Things Introduction ● Aaron Vernon, CTO at Two Bulls ● Been at Two Bulls from the beginning with two stretches away at startups - CTO of Blokify and VP Software Engineering at LIFX ● Member of the AllSeen Alliance Technical Steering Committee ● I am going to cover the following: ○ The complexities of the current IoT landscape ○ How this affects companies and users ○ The Internet of Silos example ○ How we can work together better Transports WiFi ● Uses the 802.11 standard ● Standard on all mobile devices and routers ● Has become ubiquitous for users ● Great range ● Great bandwidth ● High power consumption ● High cost ● Onboarding experience can be complicated ● Examples: Nest Cam, LIFX, Canary, Honeywell Lyric Bluetooth Smart ● Standard on most mobile devices ● Becoming increasingly ubiquitous ● Low bandwidth ● Medium range ● Low power consumption ● Low cost ● Smart Mesh is being worked on ● Examples: Flic, Ilumi, Elgato Eve ZigBee ● Uses the 802.15.4 standard ● Low bandwidth ● Low range ● Low power consumption ● Very low cost ● Forms a mesh network ● Typically requires a hub for the radio ● Known to have interop and interference problems ● Examples: Phillips Hue, large amount of sensors and actuators Z-Wave ● Proprietary - chips developed by a single manufacturer ● Uses different frequencies in different countries ● Low bandwidth ● Medium range ● Low power consumption ● Very low cost ● Forms a mesh network ● Better interoperability and less interference than ZigBee ● Typically requires -

Accepted Manuscript1.0
6850 IEEE INTERNET OF THINGS JOURNAL, VOL. 6, NO. 4, AUGUST 2019 How Do I Share My IoT Forensic Experience With the Broader Community? An Automated Knowledge Sharing IoT Forensic Platform Xiaolu Zhang, Kim-Kwang Raymond Choo ,Senior Member, IEEE , and Nicole Lang Beebe, Senior Member, IEEE Abstract —It is challenging for digital forensic practitioners to typical investigation process, two or more investigators located maintain skillset currency, for example knowing where and how in different cities and/or countries may be forensically examin- to extract digital artifacts relevant to investigations from newer, ing the same (type of) device at the same time [see Fig. 1(a)]. emerging devices (e.g., due to the increased variety of data storage schemas across manufacturers and constantly changing models). As the experience and background of both investigators are This paper presents a knowledge sharing platform, developed likely to vary, the outcomes of the forensic investigations may and validated using an Internet of Things dataset released in the also differ (e.g., in terms of the types and extent of artifacts DFRWS 2017–2018 forensic challenge. Specifically, we present being recovered). an automated knowledge-sharing forensic platform that auto- As the diversity of devices increases (e.g., IoT, wearable, matically suggests forensic artifact schemas, derived from case data, but does not include any sensitive data in the final (shared) embedded, and other digital devices), so does the challenge schema. Such artifact schemas are then stored in a schema pool in the forensic examination of such devices [4]. For example, and the platform presents candidate schemas for use in new cases an investigator who is unfamiliar with a particular device that based on the data presented. -

February, 2016 Say Hello to a Smart Home Business Standard
> High-defini- > Video tion and doorphones IP-enabled could be the > The Google OnHub > This tri-band ASUS cameras give first line of router, which uses RT-AC5300U router you a peek into defence for the Google On app, promises to give what’s happen- your home fits right in with online games a ing at home the decor ‘boost’ while you’re out > The touch screen on the TP-Link Touch P5 router enables you to set up your device without a PC or an app Keeping it connected The backbone of a connected home is its Wi-fi net- work. That network is dependent on routers — the better the router, the more stable the network. A sta- ble network facilitates better streaming and better Security network speeds. Besides, it makes it easier for your devices to communicate with one another. But that’s not the end of the story. is key To make your home network worthwhile, add a media server — which is essentially a hard drive Say hello to a Your home is possibly one of your dearest that would have all your music, movies and photos, possessions. So, wouldn’t you want to keep among other things. Think of it as a personal cloud intruders away? There is no dearth of security that stays connected to your router. At home, you systems in the market. Video doorphones can pull media through Wi-fi to play on your device, allow you to see visitors and speak to them without having to worry about making multiple before you let them in.