How-To-Secure-Your-Computer.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Ccleaner Download for Pc Windows 7 Ccleaner for Windows
ccleaner download for pc windows 7 CCleaner for Windows. CCleaner for Windows is a free PC optimizer that frees up space on your computer by r emoving unnecessary files such as cookies, unused data, and temporary files . This Piriform’s programme runs regular checks and finds those elements that slow down your computer performance . What is the CCleaner application? CCleaner is used to clean and tune up the operating system of the PC. With CCleaner, we can carry out a thorough cleaning of the PC in a simple way, which will allow us to gain space on the hard disk and prevent the PC from slowing down. It is one of those free tools for PC that works exceptionally well when it comes to deleting temporary files . CCleaner is a free , closed-source programme that can be downloaded to various devices and has been developed by the private software company Piriform Ltd , based in London, UK. Its launch date was September 23, 2003. Over the years it has undergone several updates and versions on the three platforms on which it is available: Windows, MacOS and Android . By downloading CCleaner, the software allows the cleaning up of different files, as well as optimisation of the operating system . In addition, it is capable of uninstalling multiple programmes from the interface and disabling certain applications from being executed at system startup. The benefits that the device in question derives from downloading CCleaner are improved boot speed , reduced system load and release of wasted disk space . Also, access becomes much faster. What are the benefits of downloading CCleaner? To be more specific, the useful tasks that CCleaner performs are as follows: Deleting unnecessary files Deleting temporary files and other data Freeing up hard disk space Disabling programs whose start-up is linked to the system boot Eliminating application waste Deleting browsing histories Cleaning the registry Identifying duplicate files Correcting errors that cause problems. -

[email protected]
PRIVACY TOOLKIT FOR LIBRARIANS [email protected] libraryfreedomproject.org/resources/privacy-toolkit-for-librarians/ THREAT MODELING ● assets ● adversaries ● capabilities ● consequences how much trouble are you willing to go through in order to try to prevent those? FREE SOFTWARE FOSS: the freedom to run, copy, distribute, study, change and improve the software (gnu.org) -vs. proprietary software -why does this matter for privacy? -most of these tools are free software SAFER BROWSING ● who owns your browser? ● what is a browser extension? ● Firefox and Tor ● Firefox privacy settings ● Firefox extensions menu ENCRYPTED WEBSITES ● what is encryption? 1. confidentiality 2. authenticity 3. integrity ● http vs https ● HTTPS Everywhere ● Let's Encrypt THIRD PARTY TRACKING ● cookies ● widgets ● analytics ● beacons ● behavioral advertising ● Privacy Badger This is a real image from an online marketing company. SEARCH TRACKING ● Google, Bing, and Yahoo collect and store your searches ● DuckDuckGo does not. They even have an extension! ● alerting patrons: “You might notice that your search engine looks different” ● embedded Google searchbars: Google Sharing TERMS OF SERVICE Image credit: xkcd.com E.U.L.A. = end user license agreement Terms of Service; Didn't Read WIFI SECURITY ● Open wifi access and plausible deniability ● Closed wifi encryption (authenticity – and integrity) ● Wired network snooping is possible but requires a physical connection FILE DELETION Clean system and protect privacy: trash, logs, recent places, cache, session data, etc CCLeaner – Windows and Mac OSX, not FOSS *Windows users, do not ever use the registry cleaner! Bleachbit – Windows and Linux, FOSS Deep Freeze/Clean Slate on patron PCs: very useful, easy to use, but not totally secure deletion. -

Versatile Exploitation Techniques: Drone Hacking and Jamming with Raspberry-Pi and Wi-Fi Pineapple
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-9, Issue-1, November 2019 Versatile Exploitation Techniques: Drone Hacking and Jamming with Raspberry-Pi and Wi-Fi Pineapple J Caroline El Fiorenza, Revanth Kumar Lokku, Kirthika Sivakumar, M Reene Stephanie Unmanned aerial (UAVs) vehicles, or drones, are an Abstract—The utilization of Internet-of-Things (IoT) unmanned aerial vehicle that has no pilot ready, and are innovation is developing exponentially as more shoppers and explored by either a remote control, or by ready PCs. Drones organizations recognize the benefits offered by the savvy and are normally partitioned into three unique sorts of classes: (a) shrewd gadgets. The major purpose of this paper arose due to the reason that since drone innovation is a quickly rising segment recreational, (b) business and (c) military drones. inside the IoT and the danger of hacking couldn't just purpose an The expansion of recreational drone usage has prompted information break, it could likewise represent a noteworthy discourses in regards to the security of the unregulated drone hazard to the open well-being. On account of their flexible usage, and how to maintain a strategic distance from specialist applications and access to ongoing data, commercial drones are abusing airspace rules. At a similar time as buyers utilized used across a wide variety of smart city applications. However, with many IoT devices, security is frequently an untimely idea, drones as specialists, organizations have progressively leaving numerous drones helpless against programmers. What is investigated utilizing rambles for business use. being done in this paper is that this paper examines the present In 2016 they uncovered that they were trying a conveyance condition of automation security and exhibits a lot of Wi-Fi administration where clients could get little bundles up to five empowered drone vulnerabilities. -

Datasheets Datasheet
PROFESSIONAL DATASHEETSDATASHEET Get that fresh ‘new PC’ feeling back with CCleaner Professional If your PC is slow, crashing or running out of hard drive space, CCleaner Professional is the solution. Its patented cleaner clears the clutter from your hard drive, removes junk from the Windows Registry, and protects your privacy by removing tracking cookies and browser history. All without touching your documents, music, videos and other files. If you have more than one person using your PC, CCleaner Professional can clean multiple user profiles. With system monitoring it keeps an eye on your system in the background and cleans when needed. It updates itself automatically, so you’ve always got the latest version. And if you have any questions, our priority technical support team has answers. Regain your PC’s speed, stability and privacy with CCleaner Professional. CCLEANER PROFESSIONAL HIGHLIGHTS 1. CCleaner Professional analyzes PCs to see what can be cleaned. You decide when and what to clean. 2. The patented Registry cleaner locates and fixes problems in the Windows Registry so that Windows remains stable on your PC. 3. CCleaner Professional removes tracking cookies, while keeping the cookies you need to access web-based applications like Gmail and Facebook. MADE BY For more information contact [email protected] www.piriform.com PROFESSIONAL DATASHEET CCLEANER PROFESSIONAL: A FASTER, MORE RELIABLE PC – INSTANTLY Make your PC last longer CCleaner Professional speeds up your PC and recovers hard drive space. It’s like getting a brand-new PC for a fraction of the cost. Easy to use If you can use email, you can use CCleaner Professional. -
Download Ubuntu Torrent to Install on Virtualbox Top 7 Torrent Clients for Ubuntu & Other Linux Distributions
download ubuntu torrent to install on virtualbox Top 7 Torrent Clients for Ubuntu & Other Linux Distributions. Looking for the best torrent client for Ubuntu ? Indeed, there are a number of torrent clients available for Linux. Even though I’ve primarily mentioned Ubuntu, you can get most of them working on any other Linux distribution out there. You can also check the best download managers for Ubuntu if you’re not just looking for torrent downloaders. In this article, among all the available torrent clients for Linux, I’m going to curate the best ones that you should try. Best torrent programs for Ubuntu and other Linux distributions. No matter what your preferences are, a torrent client needs to have the essential features needed along with an easy-to-use interface. Here, you’ll find the list of the best torrent clients for Linux. Note: This list is in no particular order of ranking. Some applications mentioned here are not open source. They are listed here because they are available on Linux and the article’s focus is on Linux. 1. qBittorent. qBittorrent is one of the most popular open-source torrent clients available across multiple platforms. The user interface (which is based on Qt) is quite simple and gets the job done. It supports magnet links as well. In addition to the basic functionalities, you also get a bunch of useful features like the web user interface, the ability to tweak the speeds, configuring the number of connections per torrent download, and more such options. You can take a look at their GitHub page to explore the source code. -

Defraggler Windows 10 Download Free - Reviews and Testimonials
defraggler windows 10 download free - Reviews and Testimonials. It's great to hear that so many people have found Defraggler to be the best defrag tool available. Here's what people are saying in the media: "Defraggler is easy to understand and performs its job well. if you want to improve computer performance, this is a great place to start." Read the full review. LifeHacker. "Freeware file defragmentation utility Defraggler analyzes your hard drive for fragmented files and can selectively defrag the ones you choose. The graphical interface is darn sweet." Read the full review. PC World. "Defraggler will show you all your fragmented files. You can click one to see where on the disk its various pieces lie, or defragment just that one. This can be useful when dealing with very large, performance critical files such as databases. Piriform Defraggler is free, fast, marginally more interesting to watch than the default, and has useful additional features. What's not to like?" Read the full review. - Features. Most defrag tools only allow you to defrag an entire drive. Defraggler lets you specify one or more files, folders, or the whole drive to defragment. Safe and Secure. When Defraggler reads or writes a file, it uses the exact same techniques that Windows uses. Using Defraggler is just as safe for your files as using Windows. Compact and portable. Defraggler's tough on your files – and light on your system. Interactive drive map. At a glance, you can see how fragmented your hard drive is. Defraggler's drive map shows you blocks that are empty, not fragmented, or needing defragmentation. -

Windows Apps Will Help You Get the Most out of Your New PC (Digitaltrends.Com)
Free Windows 10 Applications MARCH 21, 2019 SIR Computer & Tech Leadership Team CAT Tech Advisors (The “Experts”) Phil Goff Derek Southern Dean Steichen Barry Brown Frank May Neil Schmidt CAT Support Team Dan Green (Treasurer) Nick Bowes (Asst. Treasurer) Dick Curry (Coffee Master) Bill Phelon (Membership) Windows 10 App News Articles Several 1 st of Year Tech articles about Windows 10 Apps: Useful and Unknown Software and Tools of 2018 for Windows (ampercent.com) Top 35 free apps for Windows 10 (computerworld.com) The 20 Best Productivity Apps for Windows in 2018 (zapier.com) 2019 list: Best free software for a new Windows 10 (windowsreport.com) Our favorite Windows apps will help you get the most out of your new PC (digitaltrends.com) SIR Area 16 Computer & Technology Group “Tech Advisors” Windows Store How do you load “apps”? Windows Store Find it in your “Start” screen Or just type “Store” in the search bar Download program from web site PC Utility Apps Flipboard News aggregator Personalize to include articles of interest to you: Technology CNET Mobile Technology The DYI PC Home Automation Etc., etc. Available for PC, mobile Free (Windows Store) Also available for Mac Digital Trends Microsoft “OfficeOnline” Web based MS Office View, edit and create Office files on your browser Get many of the features of Word, Excel, Powerpoint and OneNote Somewhat similar to Google Docs Free (Windows Store) Computerworld FreeOffice Office productivity suite Similar to WORD, EXCEL, etc. Runs inside your favorite -
Using Ccleaner to Maintain Your Windows System
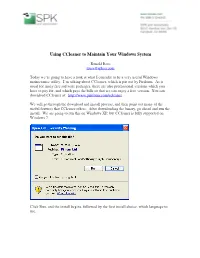
Using CCleaner to Maintain Your Windows System Ronald Ross [email protected] Today we’re going to have a look at what I consider to be a very useful Windows maintenance utility. I’m talking about CCleaner, which is put out by Piriform. As is usual for many free software packages, there are also professional versions which you have to pay for, and which pays the bills so that we can enjoy a free version. You can download CCleaner at: http://www.piriform.com/ccleaner We will go through the download and install process, and then point out many of the useful features that CCleaner offers. After downloading the binary, go ahead and run the install. We are going to run this on Windows XP, but CCleaner is fully supported on Windows 7. Click Run, and the install begins, followed by the first install choice, which language to use. Select the language of choice, and click OK. At this point, the install can begin. Click Next to continue. Have a look at the license, and if you decide to continue, click on “I Agree”. Here is where it gets more interesting. Make the choices in the Install Options that suit your tastes. I don’t much care for shortcuts cluttering up my desktop, for example, but you may feel differently. Click Install or Advanced to continue. Here, we are going to click Advanced, which will take us to the next panel. Usually the default for this install option is best, but perhaps you are sharing this computer with a child, or some other person that you don’t fully trust to always do the right thing when it comes to computers. -

Ccleaner & Defraggler Performance Report
CCleaner & Defraggler Performance Report (September 2017) Windows 7 & Windows 10 Performance Benchmark Document: CCleaner & Defraggler Performance Report Authors: M. Baquiran, D. Wren Company: PassMark Software Date: 27 September 2017 File: Piriform_CCleaner_Performance_Ed2.docx Edition 2 CCleaner & Defraggler Performance Report PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 SUMMARY ........................................................................................................................................................ 3 PRODUCTS AND VERSIONS ............................................................................................................................... 4 TEST RESULTS ................................................................................................................................................... 5 BENCHMARK 1 – DISK SPACE RECOVERED FROM INITIAL CLEANUP ..................................................................................... 5 BENCHMARK 2 – DISK SPACE RECOVERED PER WEEK ....................................................................................................... 5 BENCHMARK 4 – CHANGE IN FREE RAM ...................................................................................................................... 6 BENCHMARK 4 – MACHINE BOOT TIME ....................................................................................................................... -

Turhat Tiedostot Pois Bleachbitillä
Turhat tiedostot pois BleachBitillä Peruskäyttäjälle.net Ohjeen versio 17.1.2021 Tämä teos on lisensoitu Creative Commons Nimeä-EiKaupallinen-EiMuutoksia 4.0 Kan- sainvälinen -lisenssillä. Tarkastele lisenssiä osoitteessa https://creativecommons.org/li- censes/by-nc-nd/4.0/deed.fi Voit jakaa tätä teosta, kunhan mainitset selkeästi sen alkuperäksi ja tekijäksi Peruskäyttä- jälle.net -sivuston. Peruskäyttäjälle.netin Creative Commons-esittely (https://peruskayttajalle.net/tie- toja.php#cc) Lisätietoa Creative Commonsista suomeksi (https://creativecommons.fi/) © Peruskäyttäjälle.net. Tämä ohje on lisensoitu Creative Commons Nimeä-EiKaupallinen- EiMuutoksia 4.0 Kansainvälinen -lisenssillä 1 Sisällysluettelo 1 Johdanto .............................................................................................................................................................. 3 2 BleachBitin asentaminen ............................................................................................................................ 3 3 BleachBitin asetukset ................................................................................................................................... 8 4 Tietojen poistaminen .................................................................................................................................. 11 © Peruskäyttäjälle.net. Tämä ohje on lisensoitu Creative Commons Nimeä-EiKaupallinen- EiMuutoksia 4.0 Kansainvälinen -lisenssillä 2 1 Johdanto BleachBit (https://www.bleachbit.org/) on turhien tiedostojen -

Download the Full Digital Security Training Curriculum
Digital Security Training Curriculum A holistic and contextualized training curriculum for Digital Security Trainers and Human Rights Defenders in Uganda. Acknowledgments The design of this Digital Security Training Curriculum to provide a comprehensive and holistic reference for Human Rights Defenders and other Digital Security trainers in Uganda was supported by a diverse network of individuals and organizations. These included the DHRLab Project. We thank each of them for their valuable contribution to the development process of this curriculum, as well as for their ongoing efforts to increasing digital security awareness in Uganda. The content was shaped and greatly enriched by the following people who contributed their knowledge, insights and first-hand experience throughout the consultative process. In particular, we would like to thank Andrew Gole, (Encrypt Uganda) Lindsey Kukunda, (Her Empire) Kelly Daniel Kigonya, (IFreedom) Brian Byaruhanga, (DPI), Joseph Kasozi (HRCU), Fred Drapari (DPI) Sandra Kwikiriza (Her Internet) Kettie Kahume (Her Internet) Innocent Adriko (DLI), Emma Magambo (HRNJ), Ruth Apolot, Sonia Karungi, Ruth Atim, Shane Senyonga (Cloud & Pillar), Ben Kerry Mawejje, David Idoru (NGO Forum), and Eddie Muhumuza (Her Internet). Credits All the content in this curriculum was sourced and customized to fit the context of human rights defenders in Uganda from the following Online sources under the Creative Commons Attribution-Share Alike Unported 3.0 license by multiple authors. Level up (http://level-up.cc) Safer Journo Digital Security resources for Media Trainers (Internews) Security in a box - https://securityinabox.org/en/ Cyber women – Institute for War and Peace Reporting - https://iwpr.net/ Surveillance Self Defence https://ssd.eff.org/en How to Use this Curriculum This Curriculum uses the Activity-Discussion-Inputs-Deepening- “Adults learn best when they Synthesis approach, also referred to as the ADIDS approach to learning. -
Malware Prevention Tools
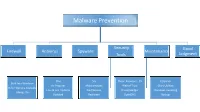
Malware Prevention Security Good Firewall Antivirus Spyware Maintenance Tools Judgment One One Three Browsers - CV CCleaner Built Into Windows AV Program Malwarebytes Web of Trust Glary Utilities Other Options Available Free & Fee Options Paid Version Privacy Badger Windows Tweaking Always On Updated Real-time OpenDNS Backup Malware Prevention Tools • Firewall - included with the Windows operating system, is real-time • Antivirus – start with MS Security Essentials available www.ninite.com , is real-time • Spyware – free version Malwarebytes available www.ninite.com , free version can be upgraded to paid version, free version is not real-time • Browsers – Internet Explorer comes with the Windows operating system, Google Chrome and Mozilla Firefox are available from www.ninite.com , all browsers are free • Web of Trust – free, available https://www.mywot.com/en/download , real-time • Privacy Badger - https://www.eff.org/privacybadger , available Chrome & Firefox only, free, real-time • OpenDNS – free, available https://www.opendns.com/home-internet-security/opendns-ip-addresses/ • CCleaner – free, available www.piriform.com , paid version not needed, and or, or both • Glary Utilities – free, available www.ninite.com , run 2x per month, update do not upgrade • Windows Tweaking – free, 38 features by default, “direct download only”, careful what you click on http://www.tweaking.com/content/page/windows_repair_all_in_one.html , run in Safe Mode • Backup – three “free” choices 1. Windows backup built into OS, files & folders and image backup available 2. EaseUs – free, available http://www.todo-backup.com/products/home/free-backup-software.htm , files & folders and image 3. Bvckup 2 – free, simple backup, available https://bvckup2.com/ , files only, non encrypted, very fast • FYI – The Sun City Computer Club will more than likely “host” some or all of the foregoing, www.ninite.com is the safest source for a variety of “free” downloads, if a product is not available on ninite.com, install software only from the vendors website! Malware Removal Process 1.