Ccleaner APT Attack: a Technical Look Inside
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Ccleaner Download for Pc Windows 7 Ccleaner for Windows
ccleaner download for pc windows 7 CCleaner for Windows. CCleaner for Windows is a free PC optimizer that frees up space on your computer by r emoving unnecessary files such as cookies, unused data, and temporary files . This Piriform’s programme runs regular checks and finds those elements that slow down your computer performance . What is the CCleaner application? CCleaner is used to clean and tune up the operating system of the PC. With CCleaner, we can carry out a thorough cleaning of the PC in a simple way, which will allow us to gain space on the hard disk and prevent the PC from slowing down. It is one of those free tools for PC that works exceptionally well when it comes to deleting temporary files . CCleaner is a free , closed-source programme that can be downloaded to various devices and has been developed by the private software company Piriform Ltd , based in London, UK. Its launch date was September 23, 2003. Over the years it has undergone several updates and versions on the three platforms on which it is available: Windows, MacOS and Android . By downloading CCleaner, the software allows the cleaning up of different files, as well as optimisation of the operating system . In addition, it is capable of uninstalling multiple programmes from the interface and disabling certain applications from being executed at system startup. The benefits that the device in question derives from downloading CCleaner are improved boot speed , reduced system load and release of wasted disk space . Also, access becomes much faster. What are the benefits of downloading CCleaner? To be more specific, the useful tasks that CCleaner performs are as follows: Deleting unnecessary files Deleting temporary files and other data Freeing up hard disk space Disabling programs whose start-up is linked to the system boot Eliminating application waste Deleting browsing histories Cleaning the registry Identifying duplicate files Correcting errors that cause problems. -
How to Know What Drivers to Download
how to know what drivers to download How do I find the hard drive type and specifications? If you'd like to view detailed information about your hard disk drives, solid-state drives, or external storage devices attached to your computer, we recommend the methods below. System Information in Windows 10. In Windows 10, you can view information about your hardware (including disks) using the System Information utility . To open the System Information utility in Windows 10: Press the Windows key, type System Information , and press Enter . Or, you can use the Run box to open the System Information utility. Press the Windows key + R keyboard shortcut. In the Run box, type msinfo32 . Press Enter or click OK . In the System Information window that opens, in the left window pane, you'll see a list of hardware categories. Expand Components , then Storage . Then, choose Drives , Disks , or any category you'd like to view. Earlier versions of Microsoft Windows. In earlier versions of Microsoft Windows, you can open the System Information utility by following the steps below. Click Start and then click the Programs folder. Click Accessories and then the System Information or System Tools folder. Open the System Information file. In the System Information window, click the + symbol next to Components . Click the + next to Storage and click Drives . In the right-side of the window, you see information about the hard drive including its capacity and serial number. IBM-compatible users. IBM-compatible users can usually enter the computer's BIOS setup to view additional information about their hard drive. -

Download Date 24/09/2021 14:31:55
To Upgrade or Not To Upgrade Application Item Type Thesis Authors Francisco, Neil Download date 24/09/2021 14:31:55 Link to Item http://hdl.handle.net/20.500.12648/1799 To Upgrade or Not To Upgrade Application __________________________ A Master's Thesis Project Presented to the Department of Communication and Information Design __________________________ In Partial Fulfillment of the Requirements for the Master of Science Degree State University of New York Polytechnic Institute By Neil Francisco May 2021 TO UPGRADE OR NOT TO UPGRADE SUNY POLYTECHNIC INSTITUTE DEPARTMENT OF INFORMATION DESIGN AND TECHNOLOGY CERTIFICATE OF APPROVAL Approved and recommended for acceptance as a thesis in partial fulfillment of the requirements for the degree of Master of Science in Information Design and Technology. ____________________June 11, 2021 DATE ________________________________ Dr. Kathryn Stam Thesis Advisor ____________________ DATE ________________________________ Dr. Ryan Lizardi Second Reader 2 TO UPGRADE OR NOT TO UPGRADE ABSTRACT New Technology consists of new hardware devices, computational workflows, digital advances, and information systems. As technology continues to evolve over the years, this never-ending cycle of new devices and experiences will always be present amongst consumers. Traditionally, new hardware devices are intriguing because they are designed to improve our access to information, media, and a connection to the digital world, but does this mean our previous-gen devices are no longer valuable? This project involves creating a prototype application designed for both computer and mobile interfaces to help improve the accessibility to information and the overall user experience with an older device. The “To Upgrade or Not To Upgrade” app will inform end-users of their older technological device specifications and suggest hardware/software methods to unlock their full potential. -

Datasheets Datasheet
PROFESSIONAL DATASHEETSDATASHEET Get that fresh ‘new PC’ feeling back with CCleaner Professional If your PC is slow, crashing or running out of hard drive space, CCleaner Professional is the solution. Its patented cleaner clears the clutter from your hard drive, removes junk from the Windows Registry, and protects your privacy by removing tracking cookies and browser history. All without touching your documents, music, videos and other files. If you have more than one person using your PC, CCleaner Professional can clean multiple user profiles. With system monitoring it keeps an eye on your system in the background and cleans when needed. It updates itself automatically, so you’ve always got the latest version. And if you have any questions, our priority technical support team has answers. Regain your PC’s speed, stability and privacy with CCleaner Professional. CCLEANER PROFESSIONAL HIGHLIGHTS 1. CCleaner Professional analyzes PCs to see what can be cleaned. You decide when and what to clean. 2. The patented Registry cleaner locates and fixes problems in the Windows Registry so that Windows remains stable on your PC. 3. CCleaner Professional removes tracking cookies, while keeping the cookies you need to access web-based applications like Gmail and Facebook. MADE BY For more information contact [email protected] www.piriform.com PROFESSIONAL DATASHEET CCLEANER PROFESSIONAL: A FASTER, MORE RELIABLE PC – INSTANTLY Make your PC last longer CCleaner Professional speeds up your PC and recovers hard drive space. It’s like getting a brand-new PC for a fraction of the cost. Easy to use If you can use email, you can use CCleaner Professional. -
Using Speccy to Report on Your Computer Components
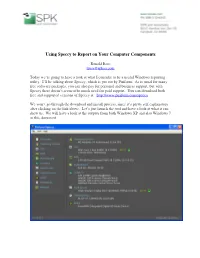
Using Speccy to Report on Your Computer Components Ronald Ross [email protected] Today we’re going to have a look at what I consider to be a useful Windows reporting utility. I’ll be talking about Speccy, which is put out by Piriform. As is usual for many free software packages, you can also pay for personal and business support, but with Speccy there doesn’t seem to be much need for paid support. You can download both free and supported versions of Speccy at: http://www.piriform.com/speccy We won’t go through the download and install process, since it’s pretty self explanatory after clicking on the link above. Let’s just launch the tool and have a look at what it can show us. We will have a look at the outputs from both Windows XP and also Windows 7 in this document. In the screen shot above, we see summary information for a Windows XP, 32-bit machine. Each of the items listed in the left hand panel can be drilled down into for expanded information. Before we have a more detailed look at some of the components we see summarized, it might be useful to look at some of the general features of Speccy. Above we see that it is possible to take a full snapshot of a machine’s information. This snapshot can be reloaded later by Speccy for analysis, or comparison with some other snapshot. It’s also possible to publish the snapshot to a webpage with the Publish Snapshot… menu choice. -

Defraggler Windows 10 Download Free - Reviews and Testimonials
defraggler windows 10 download free - Reviews and Testimonials. It's great to hear that so many people have found Defraggler to be the best defrag tool available. Here's what people are saying in the media: "Defraggler is easy to understand and performs its job well. if you want to improve computer performance, this is a great place to start." Read the full review. LifeHacker. "Freeware file defragmentation utility Defraggler analyzes your hard drive for fragmented files and can selectively defrag the ones you choose. The graphical interface is darn sweet." Read the full review. PC World. "Defraggler will show you all your fragmented files. You can click one to see where on the disk its various pieces lie, or defragment just that one. This can be useful when dealing with very large, performance critical files such as databases. Piriform Defraggler is free, fast, marginally more interesting to watch than the default, and has useful additional features. What's not to like?" Read the full review. - Features. Most defrag tools only allow you to defrag an entire drive. Defraggler lets you specify one or more files, folders, or the whole drive to defragment. Safe and Secure. When Defraggler reads or writes a file, it uses the exact same techniques that Windows uses. Using Defraggler is just as safe for your files as using Windows. Compact and portable. Defraggler's tough on your files – and light on your system. Interactive drive map. At a glance, you can see how fragmented your hard drive is. Defraggler's drive map shows you blocks that are empty, not fragmented, or needing defragmentation. -

Windows Apps Will Help You Get the Most out of Your New PC (Digitaltrends.Com)
Free Windows 10 Applications MARCH 21, 2019 SIR Computer & Tech Leadership Team CAT Tech Advisors (The “Experts”) Phil Goff Derek Southern Dean Steichen Barry Brown Frank May Neil Schmidt CAT Support Team Dan Green (Treasurer) Nick Bowes (Asst. Treasurer) Dick Curry (Coffee Master) Bill Phelon (Membership) Windows 10 App News Articles Several 1 st of Year Tech articles about Windows 10 Apps: Useful and Unknown Software and Tools of 2018 for Windows (ampercent.com) Top 35 free apps for Windows 10 (computerworld.com) The 20 Best Productivity Apps for Windows in 2018 (zapier.com) 2019 list: Best free software for a new Windows 10 (windowsreport.com) Our favorite Windows apps will help you get the most out of your new PC (digitaltrends.com) SIR Area 16 Computer & Technology Group “Tech Advisors” Windows Store How do you load “apps”? Windows Store Find it in your “Start” screen Or just type “Store” in the search bar Download program from web site PC Utility Apps Flipboard News aggregator Personalize to include articles of interest to you: Technology CNET Mobile Technology The DYI PC Home Automation Etc., etc. Available for PC, mobile Free (Windows Store) Also available for Mac Digital Trends Microsoft “OfficeOnline” Web based MS Office View, edit and create Office files on your browser Get many of the features of Word, Excel, Powerpoint and OneNote Somewhat similar to Google Docs Free (Windows Store) Computerworld FreeOffice Office productivity suite Similar to WORD, EXCEL, etc. Runs inside your favorite -
Using Ccleaner to Maintain Your Windows System
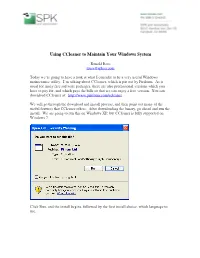
Using CCleaner to Maintain Your Windows System Ronald Ross [email protected] Today we’re going to have a look at what I consider to be a very useful Windows maintenance utility. I’m talking about CCleaner, which is put out by Piriform. As is usual for many free software packages, there are also professional versions which you have to pay for, and which pays the bills so that we can enjoy a free version. You can download CCleaner at: http://www.piriform.com/ccleaner We will go through the download and install process, and then point out many of the useful features that CCleaner offers. After downloading the binary, go ahead and run the install. We are going to run this on Windows XP, but CCleaner is fully supported on Windows 7. Click Run, and the install begins, followed by the first install choice, which language to use. Select the language of choice, and click OK. At this point, the install can begin. Click Next to continue. Have a look at the license, and if you decide to continue, click on “I Agree”. Here is where it gets more interesting. Make the choices in the Install Options that suit your tastes. I don’t much care for shortcuts cluttering up my desktop, for example, but you may feel differently. Click Install or Advanced to continue. Here, we are going to click Advanced, which will take us to the next panel. Usually the default for this install option is best, but perhaps you are sharing this computer with a child, or some other person that you don’t fully trust to always do the right thing when it comes to computers. -

Release 343 Graphics Drivers for Windows, Version 344.48. RN
Release 343 Graphics Drivers for Windows - Version 344.48 RN-W34448-01v02 | September 22, 2014 Windows Vista / Windows 7 / Windows 8 / Windows 8.1 Release Notes TABLE OF CONTENTS 1 Introduction to Release Notes ................................................... 1 Structure of the Document ........................................................ 1 Changes in this Edition ............................................................. 1 2 Release 343 Driver Changes ..................................................... 2 Version 344.48 Highlights .......................................................... 2 What’s New in Version 344.48 ................................................. 3 What’s New in Release 343..................................................... 5 Limitations in This Release ..................................................... 8 Advanced Driver Information ................................................. 10 Changes and Fixed Issues in Version 344.48.................................... 14 Open Issues in Version 344.48.................................................... 15 Windows Vista/Windows 7 32-bit Issues..................................... 15 Windows Vista/Windows 7 64-bit Issues..................................... 15 Windows 8 32-bit Issues........................................................ 17 Windows 8 64-bit Issues........................................................ 17 Windows 8.1 Issues ............................................................. 18 Not NVIDIA Issues.................................................................. -

Architecture for Analyzing Potentially Unwanted Applications
Architecture for analyzing Potentially Unwanted Applications Alberto Geniola School of Science Thesis submitted for examination for the degree of Master of Science in Technology. Espoo 10.10.2016 Thesis supervisor: Prof. Tuomas Aura Thesis advisor: M.Sc. Markku Antikainen aalto university abstract of the school of science master’s thesis Author: Alberto Geniola Title: Architecture for analyzing Potentially Unwanted Applications Date: 10.10.2016 Language: English Number of pages: 8+149 Department of Computer Science Professorship: Information security Supervisor: Prof. Tuomas Aura Advisor: M.Sc. Markku Antikainen The spread of potentially unwanted programs (PUP) and its supporting pay par install (PPI) business model have become relevant issues in the IT security area. While PUPs may not be explicitly malicious, they still represent a security hazard. Boosted by PPI companies, PUP software evolves rapidly. Although manual analysis represents the best approach for distinguishing cleanware from PUPs, it is inapplicable to the large amount of PUP installers appearing each day. To challenge this fast evolving phenomenon, automatic analysis tools are required. However, current automated malware analisyis techniques suffer from a number of limitations, such as the inability to click through PUP installation processes. Moreover, many malware analysis automated sandboxes (MSASs) can be detected, by taking advantage of artifacts affecting their virtualization engine. In order to overcome those limitations, we present an architectural design for imple- menting a MSAS mainly targeting PUP analysis. We also provide a cross-platform implementation of the MSAS, capable of running PUP analysis in both virtual and bare metal environments. The developed prototype has proved to be working and was able to automatically analyze more that 480 freeware installers, collected by the three top most ranked freeware websites, such as cnet.com, filehippo.com and softonic.com. -
Recuva Software Free Download Full Version for Windows 8 ->>->>->>
Recuva Software Free Download Full Version For Windows 8 ->>->>->> http://shurll.com/78fy0 1 / 5 2 / 5 You..may..want..to..scan..your..system..for..spyware..and..viruses,..as..they..may..interfere..with..yo ur..ability..to..connect..to..Yahoo!Close..Update..Your..Review..Since..you've..already..submitted..a..r eview..for..this..product,..this..submission..will..be..added..as..an..update..to..your..original..reviewEd itors'....Review+....by:....Download.com....staff....on....September....10,....2014....Recuva....undeletes. ...files;....recovers....data....from....corrupted,....damaged,....and....reformatted....discs;....restores....u nsaved....Word....documents;....and....securely....deletes....files....so....they're....unrecoverable,....eve n....by....RecuvaAnother....Picture....recovery....software....(that's....free)....is....TestDisk....and....it's... .sister....program....PhotoRecThank...you,...manIncluding..both..32-bit..and..64-bit..versions,..but..not ..RT..tablet..editions.Builds..We..also..offer..a..portable..version..for..installing..on..USB..thumb..drive sreviewed....on....October....19,....2015....Read....all....reviews....Review........You....may....also....like... .....Recuva....PortableA....portable....tool....to....restore....accidentally....deleted....filesFreeEnglish....S peccyA....simple....way....to....get....your....system....specificationsFreeEnglish....DefragglerFree....def ragmenter....from....the....creators....of....CCleanerFreeEnglish....Speccy....Portable....Easy....portable. ...system....information....tool....for....your....PCFreeEnglish........Features........about....Recuva....list... -
Name Link Description
Name Link Description Rufus https://rufus.akeo.ie/ Create bootable USB drives the easy way Super Micro http://www.supermicro.com/support/ This is your one-stop area for access to product-specific resources resources/ including BIOS, Drivers, Manuals and Memory Compatibility Lists. Please choose from the following options: CCleaner http://download.cnet.com/CCleaner/? CCleaner is a freeware system optimization, privacy and cleaning tool. It tag=main;dlStartKitList removes unused files from your system allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. Glary http://download.cnet.com/Glary- Glary Utilities is a comprehensive system cleaner and performance booster Utilities/3000-2094_4- for your PC that includes an excellent suite of tools. You can take 10508531.html?tag=main;dlStartKit advantage of 1-Click Maintenance, or pick and choose the operations you'd List like the app to perform, all through its streamlined and intuitive interface. Kaspersky http://download.cnet.com/Kaspersky- Kaspersky Virus Removal Tool automatically removes viruses, Trojans, Virus Virus-Removal-Tool-2015/3000- rootkits, adware, or spyware. Removal 2239_4-76079830.html?tag=main;lsr Tool 2015 Tweaking.co http://www.bleepingcomputer.com/d A free suite of administration tools and system monitors that allows a user m ownload/tweakingcom-technicians- to quickly perform diagnostics on a computer. These tools allows for Technicians toolbox/ quickly fixing common problems on a computer or diagnosing what could Toolbox be causing them. It should be noted that this free version is only available for non-commercial users.