Whisper: a Unilateral Defense Against Voip Traffic Re-Identification Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Sound Subsystem Documentation Release 4.13.0-Rc4+
Linux Sound Subsystem Documentation Release 4.13.0-rc4+ The kernel development community Sep 05, 2017 CONTENTS 1 ALSA Kernel API Documentation 1 1.1 The ALSA Driver API ............................................ 1 1.2 Writing an ALSA Driver ........................................... 89 2 Designs and Implementations 145 2.1 Standard ALSA Control Names ...................................... 145 2.2 ALSA PCM channel-mapping API ..................................... 147 2.3 ALSA Compress-Offload API ........................................ 149 2.4 ALSA PCM Timestamping ......................................... 152 2.5 ALSA Jack Controls ............................................. 155 2.6 Tracepoints in ALSA ............................................ 156 2.7 Proc Files of ALSA Drivers ......................................... 158 2.8 Notes on Power-Saving Mode ....................................... 161 2.9 Notes on Kernel OSS-Emulation ..................................... 161 2.10 OSS Sequencer Emulation on ALSA ................................... 165 3 ALSA SoC Layer 171 3.1 ALSA SoC Layer Overview ......................................... 171 3.2 ASoC Codec Class Driver ......................................... 172 3.3 ASoC Digital Audio Interface (DAI) .................................... 174 3.4 Dynamic Audio Power Management for Portable Devices ...................... 175 3.5 ASoC Platform Driver ............................................ 180 3.6 ASoC Machine Driver ............................................ 181 3.7 Audio Pops -

Audio Codecs
Audio Codecs [ AoIP | Leased Line | E1 ] Release date: July 2019 All rights reserved. Permission to reprint or electronically reproduce any document or graphic in whole or in part for any reason is prohibited unless prior written consent is obtained from AVT Audio Video Technolo- gies GmbH. This catalogue has been put together with the utmost digilence. However, no guar- antee for correctness can be given. AVT Audio Video Technologies GmbH cannot be held responsible for any misleading or incorrect information provided throughout this catalogue. AVT Audio Video Technologies GmbH re- serves the right to change specifications at any time without notice. CONTENT General 5 Features & Symbols 6 Overview 8 ISDN + VoIP ● MAGIC D7 XIP & MAGIC DC7 XIP RM Audio Codecs 10 ○ Application: Audio contribution 12 ISDN + AoIP ● MAGIC AC1 XIP & MAGIC AC1 XIP RM Audio Codecs 14 ○ Application: Audio contribution 16 E1 + AoIP ● MAGIC ACip3 & MAGIC ACip3 2M Audio Codecs 18 ○ Application: Audio contribution 20 ○ Application: AoIP distribution 22 ● MAGIC ACip3 (2M) ModNet System 24 ○ Application: Studio-Transmitter-Links 26 Audio Codec Integration ● MAGIC THipPro ACconnect 28 System Manager Upgrade 30 General Audio Codecs are needed for high-quality bitrate, the desired quality and the accept- Audio transmissions over different networks able delay. The EBU names the following Au- like IP, ISDN, 2-Mbit/s (E1) and X.21. Over IP dio algorithms as mandatory to comply with and ISDN, both Leased Line connections as the AoIP standard. G.711, G.722, ISO/MPEG well as temporary dial-up connections can Layer 2 and PCM (for stationary Audio Co- be used. -

Centauri II Multichannel Audio Gateway Codec – a New Generation Conquers the Control-Room
Centauri II Multichannel Audio Gateway Codec conquers the Control-room.– a new generation New! D 6ms Latency D 5.1 / 7.1 Multichannel D Front-panel Hot Keys D Gateway Function D Backup Function D Twin/Quad Codec D ASI Most Audio-Codecs are specialists. The CENTAURI II simply enables you to do everything. An unbeatable range of features makes the CENTAURI II simpler, safer and more cost-effective to use than any other codec. The CENTAURI II is your universal Audio cover the entire range currently in general Considering the extensive system support Codec for every imaginable project. use. Including MPEG, AES Transparent it is clear that the CENTAURI II is an and APT – simultaneously! audio codec for all situations. Whether for There are no networks that can stop a By other manufacturers this would still be Broadcasting, for DVB-H or UMTS trans- CENTAURI II, whether ISDN or Ethernet, a legitimate question but by MAYAH this missions, to name but a few. has long been possible. X.21 or E1. There are no protocols that In light of so much technical sophistica- the CENTAURI II cannot understand. This Combinations of its many and versatile tion, it’s hardly surprising to learn that codec can be simply and easily integrated features permit a wide range of applica- the CENTAURI II is also the first audio into every imaginable IT infrastructure. tions; from Gateway, Backup Codec or codec to offer professional 5.1/7.1 multi- And its more than 15 coding algorithms Streaming-Server to Multichannel Codec. channel transmissions. -

Low Bit-Rate Speech Coding with Vq-Vae and a Wavenet Decoder
ICASSP 2019-2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp. 735-739. IEEE, 2019. DOI: 10.1109/ICASSP.2019.8683277. c 2019 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media, including reprinting/republishing this material for advertising or promotional purposes, creating new collective works, for resale or redistribution to servers or lists, or reuse of any copyrighted component of this work in other works. LOW BIT-RATE SPEECH CODING WITH VQ-VAE AND A WAVENET DECODER Cristina Garbaceaˆ 1,Aaron¨ van den Oord2, Yazhe Li2, Felicia S C Lim3, Alejandro Luebs3, Oriol Vinyals2, Thomas C Walters2 1University of Michigan, Ann Arbor, USA 2DeepMind, London, UK 3Google, San Francisco, USA ABSTRACT compute the true information rate of speech to be less than In order to efficiently transmit and store speech signals, 100 bps, yet current systems typically require a rate roughly speech codecs create a minimally redundant representation two orders of magnitude higher than this to produce good of the input signal which is then decoded at the receiver quality speech, suggesting that there is significant room for with the best possible perceptual quality. In this work we improvement in speech coding. demonstrate that a neural network architecture based on VQ- The WaveNet [8] text-to-speech model shows the power VAE with a WaveNet decoder can be used to perform very of learning from raw data to generate speech. Kleijn et al. [9] low bit-rate speech coding with high reconstruction qual- use a learned WaveNet decoder to produce audio comparable ity. -

UMTS); LTE; Performance Characterization of the Adaptive Multi-Rate Wideband (AMR-WB) Speech Codec (3GPP TR 26.976 Version 10.0.0 Release 10)
ETSI TR 126 976 V10.0.0 (2011-04) Technical Report Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Performance characterization of the Adaptive Multi-Rate Wideband (AMR-WB) speech codec (3GPP TR 26.976 version 10.0.0 Release 10) 3GPP TR 26.976 version 10.0.0 Release 10 1 ETSI TR 126 976 V10.0.0 (2011-04) Reference RTR/TSGS-0426976va00 Keywords GSM, LTE, UMTS ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable Document Format (PDF). In case of dispute, the reference shall be the printing on ETSI printers of the PDF version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: http://portal.etsi.org/chaircor/ETSI_support.asp Copyright Notification No part may be reproduced except as authorized by written permission. -
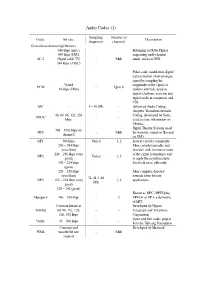
Audio Codec (1)
Audio Codec (1) Sampling Number of Codec bit rate Description frequency channels General (medium to high bit rate) 640 kbps (max.) Belonging to Dolby Digital, 448 kbps (DVD, supporting multi-channel AC-3 Digital cable TV) -Multiaudio, used on DVD 384 kbps (ATSC) Pulse-code modulation, digital representation of an analogue signal by sampling the Varied magnitude of the signal at PCM -Up to 8 64 kbps (DS0) uniform intervals, used in digital telephone systems and digital audio in computers and CDs AAC - 8 – 96 kHz - Advanced Audio Coding, Adaptive Transform Acoustic 48, 64, 66, 132, 256 Coding, developed by Sony, ATRAC -- kbps used to store information on Minidisc, Digital Theatre System, used 768 – 1536 kbps (6- DTS -Multifor in-movie sound on film and channel) on DVD MP1 384 kbps Varied 1, 2 Lowest encoder complexity 256 – 384 kbps More complex encoder and (excellent) decoder, able to remove more 224 – 256 kbps (very of the signal redundancy and MP2 Varied 1, 2 good) to apply the psychoacoustic 192 – 224 kbps threshold more efficiently (good) 224 – 320 kbps More complex, directed (excellent) towards lower bit rate 32, 41.1, 48 MP3 192 – 224 kbps (very 1, 2 applications kHz good) 128 – 192 (good) Known as MPC, MPEGplus, Musepack 160 – 180 kbps - 2 MPEG+ or MP+, a derivative of MP2 Constant bitrate at Developed by Nippon TwinVQ 80, 96, 112, 128, --Telegraph and Telephone 160, 192 kbps Corporation Open and free codec project Vorbis 45 – 500 kbps - - from the Xiph.org Foundation Constant and Developed by Microsoft WMA variable bit rate -Multi -

Ambisonic Coding with Spatial Image Correction Pierre Mahé, Stéphane Ragot, Sylvain Marchand, Jérôme Daniel
Ambisonic Coding with Spatial Image Correction Pierre Mahé, Stéphane Ragot, Sylvain Marchand, Jérôme Daniel To cite this version: Pierre Mahé, Stéphane Ragot, Sylvain Marchand, Jérôme Daniel. Ambisonic Coding with Spatial Image Correction. European Signal Processing Conference (EUSIPCO) 2020, Jan 2021, Amsterdam (virtual ), Netherlands. hal-03042322 HAL Id: hal-03042322 https://hal.archives-ouvertes.fr/hal-03042322 Submitted on 6 Dec 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Ambisonic Coding with Spatial Image Correction Pierre MAHE´ 1;2 Stephane´ RAGOT1 Sylvain MARCHAND2 Jer´ omeˆ DANIEL1 1Orange Labs, Lannion, France 2L3i, Universite´ de La Rochelle, France [email protected], [email protected], [email protected], [email protected] Abstract—We present a new method to enhance multi-mono re-creates the spatial scene based on a mono downmix and coding of ambisonic audio signals. In multi-mono coding, each these spatial parameters. This method has been extended to component is represented independently by a mono core codec, High-Order Ambisonics (HOA) in HO-DirAC [9] where the this may introduce strong spatial artifacts. The proposed method is based on the correction of spatial images derived from the sound field is divided into angular sectors; for each angular sound-field power map of original and degraded ambisonic sig- sector, one source is extracted. -

Input Formats & Codecs
Input Formats & Codecs Pivotshare offers upload support to over 99.9% of codecs and container formats. Please note that video container formats are independent codec support. Input Video Container Formats (Independent of codec) 3GP/3GP2 ASF (Windows Media) AVI DNxHD (SMPTE VC-3) DV video Flash Video Matroska MOV (Quicktime) MP4 MPEG-2 TS, MPEG-2 PS, MPEG-1 Ogg PCM VOB (Video Object) WebM Many more... Unsupported Video Codecs Apple Intermediate ProRes 4444 (ProRes 422 Supported) HDV 720p60 Go2Meeting3 (G2M3) Go2Meeting4 (G2M4) ER AAC LD (Error Resiliant, Low-Delay variant of AAC) REDCODE Supported Video Codecs 3ivx 4X Movie Alaris VideoGramPiX Alparysoft lossless codec American Laser Games MM Video AMV Video Apple QuickDraw ASUS V1 ASUS V2 ATI VCR-2 ATI VCR1 Auravision AURA Auravision Aura 2 Autodesk Animator Flic video Autodesk RLE Avid Meridien Uncompressed AVImszh AVIzlib AVS (Audio Video Standard) video Beam Software VB Bethesda VID video Bink video Blackmagic 10-bit Broadway MPEG Capture Codec Brooktree 411 codec Brute Force & Ignorance CamStudio Camtasia Screen Codec Canopus HQ Codec Canopus Lossless Codec CD Graphics video Chinese AVS video (AVS1-P2, JiZhun profile) Cinepak Cirrus Logic AccuPak Creative Labs Video Blaster Webcam Creative YUV (CYUV) Delphine Software International CIN video Deluxe Paint Animation DivX ;-) (MPEG-4) DNxHD (VC3) DV (Digital Video) Feeble Files/ScummVM DXA FFmpeg video codec #1 Flash Screen Video Flash Video (FLV) / Sorenson Spark / Sorenson H.263 Forward Uncompressed Video Codec fox motion video FRAPS: -

ACELP Speech Codec and Its Overall Comparative Performance Analysis with CELP Based 12.2 Kbps AMR- NB Speech Codec
INTERNATIONAL JOURNAL OF COMPUTERS Volume 12, 2018 Proposed modifications in ITU-T G.729 8 Kbps CS- ACELP speech codec and its overall comparative performance analysis with CELP based 12.2 Kbps AMR- NB speech codec A. Nikunj Tahilramani, B. Ninad Bhatt Abstract— This paper proposes the approach of exploiting the use of excitation codebook structure of standard extended G.729 11.8 Input to the speech encoder is 16-bit PCM from the audio Kbps [1] having 2 non-zero pulses per track in existing standard 8 part of the mobile station terminal. Before encoding, the 64 Kbps CS-ACELP (80 bits/10 ms) speech codec[1]. Proposed Kbit/s data, should be converted to 16 bit linear PCM and 16 approach avoids the use of two algebraic codebook structure for bit linear PCM to the suitable form after synthesis. CS- forward mode as well as for backward mode of G.729E working at ACELP describes the trailed mapping between input blocks 11.8 Kbps with least significant pulse replacement approach for finding optimized excitation codevector. Proposed excitation of 160 past speech samples, 80 present speech samples and codebook structure modification in standard 8 Kbps CS-ACELP (80 40 future speech samples in 16 bit linear PCM format to bits/10 ms) speech codec actuates the bit rate of 11.6 Kbps (116 encoded blocks of 80 bits to output blocks of 240 total speech bits/10 ms) .This paper introduces a comparative analysis between samples [1]. Adaptive multi rate codecs are used by GSM proposed 11.6 Kbps CS-ACELP based speech codec and standard and UMTS [2]. -

Dd 2.0 Codec
Dd 2.0 codec click here to download Dolby Digital is the name for audio compression technologies developed by Dolby . EX adds an extension to the standard channel Dolby Digital codec in the form of matrixed rear channels, creating or channel output. Dolby Digital 2/1 - 2-channel stereo with mono surround (left, right, surround); Dolby Digital. Download latest audio, speech codecs, audio filters and audio plugins: AC3 Filter, CoreVorbis, is an AC3 decompressor for VirtualDub which enables you to perform Dolby Digital AC-3 decoding for Windows ACM. Atrac3+ Plugin Gefen GTV- DDAA. Convert up to channel audio encoded in Dolby Digital Surround to L/R analog audio -- without additional costly equipment. MPEG-2, MPEG2-DVD, MPEGBlu-ray, and MXF OP1a are missing from the format pop-up menu in Adobe Media Encoder CS6. Dolby Digital. Audio Data, Industry Compression*, Windows Media*, Compression Savings. 2 ch x 48 kHz x 16 bits, Dolby Digital at Kbps, WMA 10 Pro at Kbps. This filter decodes the following audio formats: MPEG-1 audio layers I and II. Backward-compatible MPEG-2 audio, layers I and II (ISO/IEC ), mono and. Video Codecs. H; H MP3; AAC; HE-AAC; AC3 (Dolby Digital); EAC3 (Dolby Digital Plus); Vorbis; WMA; PCM . Windows Media Screen Codec 2. transcoding to a higher bit rate bit stream for distribution in the home over an S/PDIF connection for example as DTS at Mbit/s or Dolby Digital at kbit/s. 2. Buy Gefen Digital Audio Decoder (GTV-DDAA): Signal Converters - www.doorway.ru ✓ FREE DELIVERY possible on eligible purchases. -

CELT Overview
Overview of CELT Jean-Marc Valin Timothy B. Terriberry Gregory Maxwell CELT: Constrained Energy Lapped Transform ● Transform codec (MDCT, like MP3, Vorbis) – Short windows (5-22 ms), poor frequency resolution ● Explicitly code energy of each band of the signal – Coarse shape of sound preserved no matter what ● Code remaining details using vector quantization ● Variable time-frequency resolution for transients ● Now uses pitch post-filtering 2 Block Diagram Encoder Decoder Band Q1 energy band energy Pre- Post- Input Window MDCT / Q x -1 WOLA Output filter 3 residual MDCT filter Side information (period and gain) 3 "Lapped Transform" Modified DCT ● The normal DCT causes coding artifacts (sharp discontinuities) between blocks, easily audible ● The "Modified" DCT (MDCT) uses a decaying window to overlap multiple blocks – Same transform used in MP3, Vorbis, AAC, etc. – But with much smaller blocks, less overlap 4 "Constrained Energy" Critical Bands ● Group MDCT coefficients into bands approximating the critical bands (Bark scale) Bark Scale vs. CELT @ 48kHz, Frame Size=256 Bark CELT 0 2000 4000 6000 8000 10000 12000 14000 16000 18000 20000 Frequency (Hz) 5 "Constrained Energy" Coding Band Energy ● Most important psychoacoustic lesson learned from Vorbis: Preserve the energy in each band ● Vorbis does this implicitly with its "floor curve" ● CELT codes the energy explicitly – Coarse energy (6 dB resolution), predicted from previous frame and from previous band – Fine energy, improves resolution where we have available bits, not predicted 6 Coding -

Supported Codecs and Formats Codecs
Supported Codecs and Formats Codecs: D..... = Decoding supported .E.... = Encoding supported ..V... = Video codec ..A... = Audio codec ..S... = Subtitle codec ...I.. = Intra frame-only codec ....L. = Lossy compression .....S = Lossless compression ------- D.VI.. 012v Uncompressed 4:2:2 10-bit D.V.L. 4xm 4X Movie D.VI.S 8bps QuickTime 8BPS video .EVIL. a64_multi Multicolor charset for Commodore 64 (encoders: a64multi ) .EVIL. a64_multi5 Multicolor charset for Commodore 64, extended with 5th color (colram) (encoders: a64multi5 ) D.V..S aasc Autodesk RLE D.VIL. aic Apple Intermediate Codec DEVIL. amv AMV Video D.V.L. anm Deluxe Paint Animation D.V.L. ansi ASCII/ANSI art DEVIL. asv1 ASUS V1 DEVIL. asv2 ASUS V2 D.VIL. aura Auravision AURA D.VIL. aura2 Auravision Aura 2 D.V... avrn Avid AVI Codec DEVI.. avrp Avid 1:1 10-bit RGB Packer D.V.L. avs AVS (Audio Video Standard) video DEVI.. avui Avid Meridien Uncompressed DEVI.. ayuv Uncompressed packed MS 4:4:4:4 D.V.L. bethsoftvid Bethesda VID video D.V.L. bfi Brute Force & Ignorance D.V.L. binkvideo Bink video D.VI.. bintext Binary text DEVI.S bmp BMP (Windows and OS/2 bitmap) D.V..S bmv_video Discworld II BMV video D.VI.S brender_pix BRender PIX image D.V.L. c93 Interplay C93 D.V.L. cavs Chinese AVS (Audio Video Standard) (AVS1-P2, JiZhun profile) D.V.L. cdgraphics CD Graphics video D.VIL. cdxl Commodore CDXL video D.V.L. cinepak Cinepak DEVIL. cljr Cirrus Logic AccuPak D.VI.S cllc Canopus Lossless Codec D.V.L.