XEP-0106: JID Escaping
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst
ISSN (Print) : 2320 – 3765 ISSN (Online): 2278 – 8875 International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering Vol. 2, Issue 5, May 2013 SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst. Prof, Dept. of ECE, Siliguri Institute of Technology, Sukna, Siliguri, West Bengal, India 1 Network Engineer, Network Dept, Ericsson Global India Ltd, India2 Abstract:-. The Secure Internet Live Conferencing (SILC) protocol, a new generation chat protocol provides full featured conferencing services, compared to any other chat protocol. Its main interesting point is security which has been described all through the paper. We have studied how encryption and authentication of the messages in the network achieves security. The security has been the primary goal of the SILC protocol and the protocol has been designed from the day one security in mind. In this paper we have studied about different keys which have been used to achieve security in the SILC protocol. The main function of SILC is to achieve SECURITY which is most important in any chat protocol. We also have studied different command for communication in chat protocols. Keywords: SILC protocol, IM, MIME, security I.INTRODUCTION SILC stands for “SECURE INTERNET LIVE CONFERENCING”. SILC is a secure communication platform, looks similar to IRC, first protocol & quickly gained the status of being the most popular chat on the net. The security is important feature in applications & protocols in contemporary network environment. It is not anymore enough to just provide services; they need to be secure services. The SILC protocol is a new generation chat protocol which provides full featured conferencing services; additionally it provides security by encrypting & authenticating the messages in the network. -

Universidad Pol Facultad D Trabajo
UNIVERSIDAD POLITÉCNICA DE MADRID FACULTAD DE INFORMÁTICA TRABAJO FINAL DE CARRERA ESTUDIO DEL PROTOCOLO XMPP DE MESAJERÍA ISTATÁEA, DE SUS ATECEDETES, Y DE SUS APLICACIOES CIVILES Y MILITARES Autor: José Carlos Díaz García Tutor: Rafael Martínez Olalla Madrid, Septiembre de 2008 2 A mis padres, Francisco y Pilar, que me empujaron siempre a terminar esta licenciatura y que tanto me han enseñado sobre la vida A mis abuelos (q.e.p.d.) A mi hijo icolás, que me ha dejado terminar este trabajo a pesar de robarle su tiempo de juego conmigo Y muy en especial, a Susana, mi fiel y leal compañera, y la luz que ilumina mi camino Agradecimientos En primer lugar, me gustaría agradecer a toda mi familia la comprensión y confianza que me han dado, una vez más, para poder concluir definitivamente esta etapa de mi vida. Sin su apoyo, no lo hubiera hecho. En segundo lugar, quiero agradecer a mis amigos Rafa y Carmen, su interés e insistencia para que llegara este momento. Por sus consejos y por su amistad, les debo mi gratitud. Por otra parte, quiero agradecer a mis compañeros asesores militares de Nextel Engineering sus explicaciones y sabios consejos, que sin duda han sido muy oportunos para escribir el capítulo cuarto de este trabajo. Del mismo modo, agradecer a Pepe Hevia, arquitecto de software de Alhambra Eidos, los buenos ratos compartidos alrrededor de nuestros viejos proyectos sobre XMPP y que encendieron prodigiosamente la mecha de este proyecto. A Jaime y a Bernardo, del Ministerio de Defensa, por haberme hecho descubrir las bondades de XMPP. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Seamonkey Security Update (RHSA-2007-0980)
seamonkey security update (RHSA-2007-0980) Original Release Date: November 8, 2007 Last Revised: November 8, 2007 Number: ASA-2007-459 Risk Level: None Advisory Version: 1.0 Advisory Status: Final 1. Overview: SeaMonkey is an open-source software suite from the Mozilla Foundation which provides a Web browser, Mail and Usenet client, an Internet Relay Chat (IRC) client and an HTML editing utility. Several flaws were found in the way in which SeaMonkey processed certain malformed web content. A web page containing malicious content could cause SeaMonkey to crash or potentially execute arbitrary code as the user running SeaMonkey. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CVE-2007- 5338, CVE-2007-5339, and CVE-2007-5340 to these issues. Several flaws were found in the way in which SeaMonkey displayed malformed web content. A web page containing specially-crafted content could potentially trick a user into surrendering sensitive information. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CVE-2007-1095, CVE-2007-3844, CVE- 2007-3511, and CVE-2007-5334 to these issues. A flaw was found in the SeaMonkey sftp protocol handler. A malicious web page could access data from a remote sftp site, possibly stealing sensitive user data. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the name CVE-2007- 5337 to this issue. A request-splitting flaw was found in the way in which SeaMonkey generates a digest authentication request. If a user opened a specially-crafted URL, it was possible to perform cross-site scripting attacks, web cache poisoning, or other, similar exploits. -

There Are Two Dedicated Dspace IRC (Internet Relay Chat) Channels (I.E
IRC Code of Conduct All DSpace support channels, mailing lists and meetings follow the LYRASIS Code of Conduct. We ask you to remain respectful in all discussions. We also encourage you to report any violations of the code of conduct to LYRASIS (see the Code of Conduct for more details). DSpace chat has moved to Slack Our old IRC channels are essentially unmonitored these days. Instead, we recommend joining our DSpace.org Slack for any chat-based support. You are also welcome to email your question to the dspace-tech Mailing List as an alternative, or choose one of the other DSpace Sup port options. There are two dedicated DSpace IRC (internet relay chat) channels (i.e. "rooms") on the irc.freenode.net server: #dspace (irc://irc.freenode.net/dspace) - all DSpace discussions and live Q & A. This channel is unlogged. #duraspace (irc://irc.freenode.net/duraspace) - Old duraspace community channel (no longer used). As of July 2018, this channel is unlogged. Pri or years logs are still available/archived. If you do not have access to an IRC client, or are new to IRC, the following web interfaces are very easy way to get started: Login to #dspace IRC at: http://webchat.freenode.net?channels=dspace Enter in a nickname of your choice (e.g. firstName_lastName) & click "Connect" Login to #duraspace IRC at: http://webchat.freenode.net?channels=duraspace Enter in a nickname of your choice (e.g. firstName_lastName) & click "Connect" Or you can login to both IRC channels at the same time: http://webchat.freenode.net?channels=duraspace,dspace For a list of IRC client software, see: http://en.wikipedia.org/wiki/Comparison_of_Internet_Relay_Chat_clients Many current Instant Messaging (IM) clients also support IRC. -

Internet Relay Chat. ERIC Digest
ED425743 1999-01-00 Internet Relay Chat. ERIC Digest. ERIC Development Team www.eric.ed.gov Table of Contents If you're viewing this document online, you can click any of the topics below to link directly to that section. Internet Relay Chat. ERIC Digest............................................... 1 WHY USE INTERNET RELAY CHAT?..................................... 2 WHAT IS REQUIRED?........................................................ 2 HOW IS IRC ORGANIZED?.................................................. 3 NETS..............................................................................3 CHANNELS......................................................................3 OPS............................................................................... 3 NICKS.............................................................................4 HOW DO YOU FIND, JOIN, OR CREATE A CHANNEL?............... 4 CAN YOU SEND A PRIVATE MESSAGE?................................ 4 HOW DOES ONE EXIT AN IRC CHAT?................................... 4 WHAT ARE THE DISADVANTAGES OF IRC?............................4 WHAT EDUCATIONAL BENEFITS CAN I EXPECT?....................5 ERIC Identifier: ED425743 Publication Date: 1999-01-00 Author: Simpson, Carol Source: ERIC Clearinghouse on Information and Technology Syracuse NY. Internet Relay Chat. ERIC Digest. ED425743 1999-01-00 Internet Relay Chat. ERIC Digest. Page 1 of 6 www.eric.ed.gov ERIC Custom Transformations Team THIS DIGEST WAS CREATED BY ERIC, THE EDUCATIONAL RESOURCES INFORMATION CENTER. FOR MORE -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
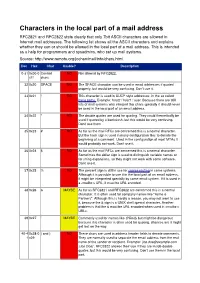
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -

15-441: Computer Networks Project 1: Internet Relay Chat (IRC) Server
15-441: Computer Networks Project 1: Internet Relay Chat (IRC) Server Lead TA: Daegun Won <[email protected]> Assigned: January 21, 2010 Checkpoint 1 due: January 26, 2010 Checkpoint 2 due: February 4, 2010 Final version due: February 16, 2010 1 Introduction The purpose of this project is to give you experience in developing concurrent network applications. You will use the Berkeley Sockets API to write an Internet chat server using a subset of the Internet Relay Chat protocol (IRC)[1]. IRC is a global, distributed, real-time chat system that operates over the Internet. An IRC network consists of a set of interconnected servers. Once users are connected to an IRC server, they can converse with other users connected to any server in the IRC network. IRC provides for group communication, via named channels, as well as personal communication through “private” messages. For more information about IRC, including available client software and public IRC networks, please see The IRC Prelude[2]. If you have not used IRC before, you may want to try it out to get a feel for what it is. For a quick start, log in to an Andrew machine, and run irssi -c irc.freenode.net -n nickname where nickname is the nickname you want to use. Then type /join #networking to join a networking discussion channel. Other channels you might be interested include #gentoo, #redhat, #perl, and #c++. After you have tried out the text mode IRC client, you may want to try out graphical clients such as xchat and chatzilla (part of mozilla). -

Going Live Tutorial Contents
Going Live Tutorial Contents Going Live with Your Online Business 1 Let’s Get Started 2 Domain names, IP addresses and DNS 2 Some advanced terminology 3 Going Live Step by Step 5 1. Getting a domain name 5 2. Setting up your domain & its email settings 5 2a. Adding your domain name to the system 5 2b. Email settings for your domain 7 3. Setting up email 8 3a. Creating mailboxes 8 3b. Creating aliases 8 4. Pointing your domain to us 9 5. Setting up your email client 10 For Advanced Users - using an external DNS service 11 Going Live with Your Online Business When your site is looking hot and you’re ready to rock, you’ll want to take your site out of trial mode and make it live. Taking a site live means a few things: You’re ready to pay for your site. You’re ready to buy a domain name (www.mybusiness.com) and allow people to access your site by typing that address into their web browser. OR you’ve got a domain name that currently goes to your old site, and you want to switch it over to your brand-spanking-new online business. Who is this for? This guide is for anyone who’s ready to take their site live and show it off to the world! Some sections can be skipped by those with more advanced knowledge - these sections will be marked accordingly. Business Catalyst • Going Live Tutorial 1 Let’s Get Started Domain names, IP addresses and DNS If you already know what a domain name is, what an IP address is and how DNS works, you can skip this section.