Constant Weight Codes: a Geometric Approach Based on Dissections Chao Tian, Member, IEEE, Vinay A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Combinatorial Analysis of Topological Dissections
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector ADVANCES IN MATHEMATICS 25, 267-285 (1977) A Combinatorial Analysis of Topological Dissections THOMAS ZASLAVSKY Massachusetts Institute of Technology, Cambridge, Massachusetts 02139 From a topological space remove certain subspaces (cuts), leaving connected components (regions). We develop an enumerative theory for the regions in terms of the cuts, with the aid of a theorem on the Mijbius algebra of a subset of a distributive lattice. Armed with this theory we study dissections into cellular faces and dissections in the d-sphere. For example, we generalize known enumerations for arrangements of hyperplanes to convex sets and topological arrangements, enumerations for simple arrangements and the Dehn-Sommerville equations for simple polytopes to dissections with general intersection, and enumerations for arrangements of lines and curves and for plane convex sets to dissections by curves of the 2-sphere and planar domains. Contents. Introduction. 1. The fundamental relations for dissections and covers. 2. Algebraic combinatorics: Valuations and MGbius algebras. 3. Dissections into cells and properly cellular faces. 4. General position. 5. Counting low-dimensional faces. 6. Spheres and their subspaces. 7. Dissections by curves. INTRODUCTION A problem which arises from time to time in combinatorial geometry is to determine the number of pieces into which a certain geometric set is divided by given subsets. Think for instance of a plane cut by prescribed curves, as in a map of a land area crisscrossed by roads and hedgerows, or of a finite set of hyper- planes slicing up a convex domain in a Euclidean space. -

The Dehn-Sydler Theorem Explained
The Dehn-Sydler Theorem Explained Rich Schwartz February 16, 2010 1 Introduction The Dehn-Sydler theorem says that two polyhedra in R3 are scissors con- gruent iff they have the same volume and Dehn invariant. Dehn [D] proved in 1901 that equality of the Dehn invariant is necessary for scissors congru- ence. 64 years passed, and then Sydler [S] proved that equality of the Dehn invariant (and volume) is sufficient. In [J], Jessen gives a simplified proof of Sydler’s Theorem. The proof in [J] relies on two results from homolog- ical algebra that are proved in [JKT]. Also, to get the cleanest statement of the result, one needs to combine the result in [J] (about stable scissors congruence) with Zylev’s Theorem, which is proved in [Z]. The purpose of these notes is to explain the proof of Sydler’s theorem that is spread out in [J], [JKT], and [Z]. The paper [J] is beautiful and efficient, and I can hardly improve on it. I follow [J] very closely, except that I simplify wherever I can. The only place where I really depart from [J] is my sketch of the very difficult geometric Lemma 10.1, which is known as Sydler’s Fundamental Lemma. To supplement these notes, I made an interactive java applet that renders Sydler’s Fundamental Lemma transparent. The applet departs even further from Jessen’s treatment. [JKT] leaves a lot to be desired. The notation in [JKT] does not match the notation in [J] and the theorems proved in [JKT] are much more general than what is needed for [J]. -

Computational Design of Steady 3D Dissection Puzzles
DOI: 10.1111/cgf.13638 EUROGRAPHICS 2019 / P. Alliez and F. Pellacini Volume 38 (2019), Number 2 (Guest Editors) Computational Design of Steady 3D Dissection Puzzles Keke Tang1;2 Peng Song3y Xiaofei Wang4 Bailin Deng5 Chi-Wing Fu6 Ligang Liu4 1 Cyberspace Institute of Advanced Technology, Guangzhou University 2 University of Hong Kong 3 EPFL 4 University of Science and Technology of China 5 Cardiff University 6 The Chinese University of Hong Kong Figure 1: (a&b) TEAPOT - SNAIL dissection puzzle designed by our method; (c) 25 3D-printed pieces; and (d&e) assembled puzzles. Abstract Dissection puzzles require assembling a common set of pieces into multiple distinct forms. Existing works focus on creating 2D dissection puzzles that form primitive or naturalistic shapes. Unlike 2D dissection puzzles that could be supported on a tabletop surface, 3D dissection puzzles are preferable to be steady by themselves for each assembly form. In this work, we aim at computationally designing steady 3D dissection puzzles. We address this challenging problem with three key contributions. First, we take two voxelized shapes as inputs and dissect them into a common set of puzzle pieces, during which we allow slightly modifying the input shapes, preferably on their internal volume, to preserve the external appearance. Second, we formulate a formal model of generalized interlocking for connecting pieces into a steady assembly using both their geometric arrangements and friction. Third, we modify the geometry of each dissected puzzle piece based on the formal model such that each assembly form is steady accordingly. We demonstrate the effectiveness of our approach on a wide variety of shapes, compare it with the state-of-the-art on 2D and 3D examples, and fabricate some of our designed puzzles to validate their steadiness. -

An Algorithm for Creating Geometric Dissection Puzzles
An Algorithm for Creating Geometric Dissection Puzzles Yahan Zhou, [email protected] Rui Wang, [email protected] Department of Computer Science, UMass Amherst Abstract Geometric dissection is a popular category of puzzles. Given two planar figures of equal area, a dissection seeks to partition one figure into pieces that can be reassembled to construct the other figure. In this paper, we present a computational method for creating lattice-based geometric dissection puzzles. Our method starts by representing the input figures on a discrete grid, such as a square or triangular lattice. Our goal is then to partition both figures into the smallest number of clusters (pieces) such that there is a one-to-one and congruent matching between the two sets of clusters. Solving this problem directly is intractable with a brute-force approach. We propose a hierarchical clustering method that can efficiently find near-optimal solutions by iteratively minimizing an objective function. In addition, we modify the objective function to include an area-based term, which directs the solution towards pieces with more balanced sizes. Finally, we show extensions of our algorithm for dissecting 3D shapes of equal volume. 1 Introduction Geometric dissection is a mathematical problem that has enjoyed for a long time great popularity in recre- ational math and art [4,7]. In its basic form, the dissection question asks whether any two shapes of the same area are equi-decomposable, that is, if they can be cut into a finite number of congruent polygonal pieces [4]. Such problems have a rich history originating from the exploration of geometry by the ancient Greeks. -

Proofs from the BOOK
Martin Aigner · Günter M. Ziegler Proofs from THE BOOK Fifth Edition Martin Aigner Günter M. Ziegler Proofs from THE BOOK Fifth Edition Martin Aigner Günter M. Ziegler Proofs from THE BOOK Fifth Edition Including Illustrations by Karl H. Hofmann 123 Martin Aigner Günter M. Ziegler Freie Universität Berlin Freie Universität Berlin Berlin, Germany Berlin, Germany ISBN978-3-662-44204-3 ISBN978-3-662-44205-0(eBook) DOI 10.1007/978-3-662-44205-0 © Springer-Verlag Berlin Heidelberg 2014 This work is subject to copyright. All rights are reserved, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilm or in any other way, and storage in data banks. Duplication of this publication or parts thereof is permitted only under the provisions of the German Copyright Law of September 9, 1965, in its current version, and permission for use must always be obtained from Springer. Violations are liable to prosecution under the German Copyright Law. The use of general descriptive names, registered names, trademarks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. Coverdesign: deblik, Berlin Printed on acid-free paper Springer is Part of Springer Science+Business Media www.springer.com Preface Paul Erdos˝ liked to talk about The Book, in which God maintains the perfect proofs for mathematical theorems, following the dictum of G. H. Hardy that there is no permanent place for ugly mathematics. -

Intendd for Both
A DOCUMENT RESUME ED 040 874 SE 008 968 AUTHOR Schaaf, WilliamL. TITLE A Bibli6graphy of RecreationalMathematics, Volume INSTITUTION National Council 2. of Teachers ofMathematics, Inc., Washington, D.C. PUB DATE 70 NOTE 20ap. AVAILABLE FROM National Council of Teachers ofMathematics:, 1201 16th St., N.W., Washington, D.C.20036 ($4.00) EDRS PRICE EDRS Price ME-$1.00 HC Not DESCRIPTORS Available fromEDRS. *Annotated Bibliographies,*Literature Guides, Literature Reviews,*Mathematical Enrichment, *Mathematics Education,Reference Books ABSTRACT This book isa partially annotated books, articles bibliography of and periodicalsconcerned with puzzles, tricks, mathematicalgames, amusements, andparadoxes. Volume2 follows original monographwhich has an gone through threeeditions. Thepresent volume not onlybrings theliterature up to material which date but alsoincludes was omitted in Volume1. The book is the professionaland amateur intendd forboth mathematician. Thisguide canserve as a place to lookfor sourcematerials and will engaged in research. be helpful tostudents Many non-technicalreferences the laymaninterested in are included for mathematicsas a hobby. Oneuseful improvementover Volume 1 is that the number ofsubheadings has more than doubled. (FL) been 113, DEPARTMENT 01 KWH.EDUCATION & WELFARE OffICE 01 EDUCATION N- IN'S DOCUMENT HAS BEEN REPRODUCED EXACILY AS RECEIVEDFROM THE CO PERSON OR ORGANIZATION ORIGINATING IT POINTS Of VIEW OR OPINIONS STATED DO NOT NECESSARILY CD REPRESENT OFFICIAL OFFICE OfEDUCATION INt POSITION OR POLICY. C, C) W A BIBLIOGRAPHY OF recreational mathematics volume 2 Vicature- ligifitt.t. confiling of RECREATIONS F DIVERS KIND S7 VIZ. Numerical, 1Afironomical,I f Antomatical, GeometricallHorometrical, Mechanical,i1Cryptographical, i and Statical, Magnetical, [Htlorical. Publifhed to RecreateIngenious Spirits;andto induce them to make fartherlcruciny into tilde( and the like) Suut.tm2. -

Hinged Dissection of Polyominoes and Polyforms
Hinged Dissection of Polyominoes and Polyforms Erik D. Demaine¤ Martin L. Demaine¤ David Eppsteiny Greg N. Fredericksonz Erich Friedmanx Abstract A hinged dissection of a set of polygons S is a collection of polygonal pieces hinged together at vertices that can be rotated into any member of S. We present a hinged dissection of all edge-to-edge gluings of n congruent copies of a polygon P that join corresponding edges of P . This construction uses kn pieces, where k is the number of vertices of P . When P is a regular polygon, we show how to reduce the number of pieces to dk=2e(n ¡ 1). In particular, we consider polyominoes (made up of unit squares), polyiamonds (made up of equilateral triangles), and polyhexes (made up of regular hexagons). We also give a hinged dissection of all polyabolos (made up of right isosceles triangles), which do not fall under the general result mentioned above. Finally, we show that if P can be hinged into Q, then any edge-to-edge gluing of n congruent copies of P can be hinged into any edge-to-edge gluing of n congruent copies of Q. 1 Introduction A geometric dissection [8, 13] is a cutting of a polygon into pieces that can be re-arranged to form another polygon. It is well known, for example, that any polygon can be dissected into any other polygon with the same area [2, 8, 14], but the bound on the number of pieces is quite weak. The main problem, then, is to ¯nd a dissection with the fewest possible number of pieces. -
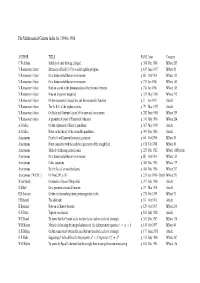
The Mathematical Gazette Index for 1894 to 1908
The Mathematical Gazette Index for 1894 to 1908 AUTHOR TITLE PAGE Issue Category C.W.Adams Stability of cube floating in liquid p. 388 Dec 1908 MNote 285 V.Ramaswami Aiyar Extension of Euclid I.47 to n-sided regular polygons p. 109 June 1897 MNote 41 V.Ramaswami Aiyar On a fundamental theorem in inversion p. 88 Oct 1904 MNote 153 V.Ramaswami Aiyar On a fundamental theorem in inversion p. 275 Jan 1906 MNote 183 V.Ramaswami Aiyar Note on a point in the demonstration of the binomial theorem p. 276 Jan 1906 MNote 185 V.Ramaswami Aiyar Note on the power inequality p. 321 May 1906 MNote 192 V.Ramaswami Aiyar On the exponential inequalities and the exponential function p. 8 Jan 1907 Article V.Ramaswami Aiyar The A, B, C of the higher analysis p. 79 May 1907 Article V.Ramaswami Aiyar On Stolz and Gmeiner’s proof of the sine and cosine series p. 282 June 1908 MNote 259 V.Ramaswami Aiyar A geometrical proof of Feuerbach’s theorem p. 310 July 1908 MNote 264 A.O.Allen On the adjustment of Kater’s pendulum p. 307 May 1906 Article A.O.Allen Notes on the theory of the reversible pendulum p. 394 Dec 1906 Article Anonymous Proof of a well-known theorem in geometry p. 64 Oct 1896 MNote 30 Anonymous Notes connected with the analytical geometry of the straight line p. 158 Feb 1898 MNote 49 Anonymous Method of reducing central conics p. 225 Dec 1902 MNote 110B (note) Anonymous On a fundamental theorem in inversion p. -
A Computational Algorithm for Creating Geometric Dissection Puzzles
A Computational Algorithm for Creating Geometric Dissection Puzzles Yahan Zhou Rui Wang University of Massachusetts Amherst Abstract Geometric dissection is a popular way to create puzzles. Given two input figures of equal area, a dissection seeks to partition one figure into pieces which can be reassembled to construct the other figure. While mathematically it is well-known that a dissection al- ways exists between two 2D polygons, the challenge is to find a solution with as few pieces as possible. In this paper, we present a computational method for creating geometric dissection puzzles. Our method starts by representing the input figures onto a discrete grid, such as a square or triangular lattice. Our goal is then to parti- tion both figures into the smallest number of clusters (pieces) such that there is a one-to-one and congruent matching between the two sets. Directly solving this combinatorial optimization problem is intractable with a brute-force approach. We propose a novel hierar- chical clustering method that can efficiently find an optimal solution by iteratively minimizing an objective function. In addition, we can modify the objective function to include an area-based term, which directs the solution towards pieces with a more balanced size. Fi- nally, we show extensions of our algorithm for dissecting multiple 2D figures, and for dissecting 3D shapes. Figure 1: Four example sets of dissection puzzles created using our Keywords: Geometric puzzles, dissection, optimization. algorithm. The top two rows show 2D dissections – the first is a 4- piece dissection, and the second is a 5-piece dissection of a rectan- 1 Introduction gle with a rasterized octagon. -
![Arxiv:1708.02891V3 [Math.MG] 6 Jun 2018 7.3](https://docslib.b-cdn.net/cover/1097/arxiv-1708-02891v3-math-mg-6-jun-2018-7-3-7751097.webp)
Arxiv:1708.02891V3 [Math.MG] 6 Jun 2018 7.3
AREA DIFFERENCE BOUNDS FOR DISSECTIONS OF A SQUARE INTO AN ODD NUMBER OF TRIANGLES JEAN-PHILIPPE LABBÉ, GÜNTER ROTE, AND GÜNTER M. ZIEGLER Abstract. Monsky’s theorem from 1970 states that a square cannot be dissected into an odd number n of triangles of the same area, but it does not give a lower bound for the area differences that must occur. We extend Monsky’s theorem to “constrained framed maps”; based on this we can apply a gap theorem from semi-algebraic geometry to a polynomial area difference measure and thus get a lower bound for the area differences that decreases doubly-exponentially with n. On the other hand, we obtain the first superpolynomial upper bounds for this problem, derived from an explicit construction that uses the Thue–Morse sequence. Contents 1. Introduction 2 2. Background 3 2.1. Dissection of simple polygons3 2.2. Monsky’s theorem4 2.3. Error measures5 3. Monsky’s theorem for constrained framed maps of dissection skeleton graphs5 3.1. Combinatorial types of dissections6 3.2. Collinearity constraints of dissections6 3.3. Framed maps and constrained framed maps8 3.4. Signed area of a triangular face9 3.5. Monsky’s theorem for constrained framed maps of skeleton graphs 10 4. Area differences of dissections and framed maps 11 5. Lower bound for the range of areas of dissections 13 5.1. Properties of the area difference polynomial 13 5.2. Lower bound using a gap theorem 14 6. Enumeration and optimization results 15 6.1. Enumeration of combinatorial types 15 6.2. Finding the optimal dissection for each combinatorial type 16 6.3. -

Construction and Fabrication of Reversible Shape Transforms
Construction and Fabrication of Reversible Shape Transforms SHUHUA LI, Dalian University of Technology and Simon Fraser University ALI MAHDAVI-AMIRI, Simon Fraser University RUIZHEN HU∗, Shenzhen University HAN LIU, Simon Fraser University and Carleton University CHANGQING ZOU, University of Maryland, College Park OLIVER VAN KAICK, Carleton University XIUPING LIU, Dalian University of Technology HUI HUANG∗, Shenzhen University HAO ZHANG, Simon Fraser University Fig. 1. We introduce a fully automatic algorithm to construct reversible hinged dissections: the crocodile and the Crocs shoe can be inverted inside-out and transformed into each other, bearing slight boundary deformation. The complete solution shown was computed from the input (let) without user assistance. We physically realize the transform through 3D printing (right) so that the pieces can be played as an assembly puzzle. We study a new and elegant instance of geometric dissection of 2D shapes: the iltering scheme picks good inputs for the construction. Furthermore, reversible hinged dissection, which corresponds to a dual transform between we add properly designed hinges and connectors to the shape pieces and two shapes where one of them can be dissected in its interior and then in- fabricate them using a 3D printer so that they can be played as an assembly verted inside-out, with hinges on the shape boundary, to reproduce the other puzzle. With many interesting and fun RIOT pairs constructed from shapes shape, and vice versa. We call such a transform reversible inside-out transform found online, we demonstrate that our method signiicantly expands the or RIOT. Since it is rare for two shapes to possess even a rough RIOT, let range of shapes to be considered for RIOT, a seemingly impossible shape alone an exact one, we develop both a RIOT construction algorithm and a transform, and ofers a practical way to construct and physically realize quick iltering mechanism to pick, from a shape collection, potential shape these transforms. -

Homage to a Pied Puzzler
i i i i Homage to a Pied Puzzler i i i i i i i i i i i i i i i i Homage to a Pied Puzzler Edited by Ed Pegg Jr. Alan H. Schoen Tom Rodgers A K Peters, Ltd. Wellesley, Massachusetts i i i i CRC Press Taylor & Francis Group 6000 Broken Sound Parkway NW, Suite 300 Boca Raton, FL 33487-2742 © 2011 by Taylor & Francis Group, LLC CRC Press is an imprint of Taylor & Francis Group, an Informa business No claim to original U.S. Government works Version Date: 20150225 International Standard Book Number-13: 978-1-4398-6500-2 (eBook - PDF) This book contains information obtained from authentic and highly regarded sources. Reason- able efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers.