Bursting the Bubble? Russian A2/AD in the Baltic Sea Region
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Analysis of Cyberwarfare Ethics As It Pertains to Civilian Computer Networks/Infrastructures
Analysis of Cyberwarfare Ethics as It Pertains to Civilian Computer Networks/Infrastructures Vanessa Paradine Terms of Reference and Scope The Department of Defense (DoD) currently operates more than fifteen thousand different computer networks across four thousand military installations around the world, with as many as seven million DoD computers and telecommunications tools in use in eighty-eight countries.1 These networks experience over six million unauthorized probes per day.2 Due to the close integration of DoD and commercial networks, an attack within the cyber domain may significantly impact critical civilian infrastructures and networks. For the purpose of this article, the following definitions are pro vided: • Cyberspace, as defined by the National Security Presidential Di rective 541H0meland Security Presidential Directive 23, is "the interdependent network of information technology infrastruc tures, and includes the Internet, telecommunications networks, computer systems, and embedded processors and controllers in critical industries."3 • Cyberspace operations is defined as "the employment of cy berspace capabilities where the primary purpose is to achieve military objectives or effects in or through cyberspace."4 • Cyberwarfare/cyberattack has not been defined by the Depart ment of the Defense (DoD); however, according to Deputy Defense Secretary William J. Lynn III, it can include a range of things-"from exploitation and exfiltration of data to degrada tion of networks to destruction of networks or even physical equipment, physical property."5 • Cyber Threats6 o Virtual-nonkinetic threats to DoD information networks that are just as real and damaging as physical threats. 34 Internatianal Journal of Intelligence Ethics, Vol. 4, No. 1 / Spring/Summer 2013 Analysis of Cyberwarfare Ethics 35 o Physical-kinetic threats mixed with nonkinetic threats; can severely impact the effectiveness of military joint operations. -

Hay River Welcome to the 2018 Arctic Winter Games!
FIND YOUR POWER March 18th - 24th 2018 ARCTIC WINTER GAMES PARTICIPANT HANDBOOK HAY RIVER WELCOME TO THE 2018 ARCTIC WINTER GAMES! Welcome and congratulations for being a part of the 2018 South Slave Arctic Winter games! This handbook will provide you with all the information you will need to have the best experience in Hay River! We look forward to seeing you during the games. PRESIDENT’S MESSAGE On behalf of the 2018 Host Society I want to welcome you to the 2018 South Slave Arctic Winter Games! As a past Arctic Winter Games athlete and coach, I know the tremendous effort it has taken each of you to get to this point in your Games journey. Just as you have been preparing for the 2018 Games, the communities of Hay River and Fort Smith, and our friends from other communities, have been pre- paring for this day. Over the last three years, volunteer committees and staff have been working tirelessly to plan and organize a Games that you are sure to enjoy and remember. It is guaranteed to be a fast-paced week of intense com- petition and exciting cultural performances, so please enjoy every moment! I am tremendously proud to welcome you to the magnificent South Slave Re- gion and I wish you the very best of luck in all your pursuits! I know that each of you will Find Your Power through your participation at the 2018 Games! Gregory Rowe President, 2018 South Slave Arctic Winter Games ACCOMMODATIONS Athletes and team staff participating in the 2018AWG will be staying at the following Athletes’ Villages in Hay River: Diamond Jenness Secondary -

Games Kick Off with a Party
POWERED BY THE OFFICIAL NEWSPAPER OF THE ARCTIC WINTER GAMES MARCH 19, 2018 Games kick off with a party Yukon athlete aims to break record The Arctic Winter Games flame is lit Team profiles of Nunavut and Alberta North Thorsten Gohl photo 2 ULU NEWS, Monday, March 19, 2018 ULU NEWS, Monday, March 19, 2018 3 Let the Arctic Winter Games begin TJ Kaskamin of Fort Good Hope carries the NWT flag into the March 18 open- ing ceremony in Hay River for the 2018 South Slave Arctic Winter Games. Paul Bickford/NNSL photo Arctic Winter Games launched with ceremony in Hay River by Paul Bickford Winter Games Host Society, Lynn Napier-Buckley of Fort Winter Olympics in Pyeong- Olympic Games." The entertainment for Northern News Services recalled the region's failed Smith, Chief Roy Fabian of Chang, South Korea – wel- The late Pat Bobinski, a the evening included the After years of planning attempt to obtain the games K'atlodeeche First Nation and coming the athletes to his Hay River volunteer who was Hay River Filipino March- and work, the 2018 South for 2008. Kristy Duncan, the federal hometown. instrumental in developing the ing Band, The JBT Jiggers Slave Arctic Winter Games "With renewed vision and minister of Sport and Persons "I'm proud to say that sport of biathlon in the NWT from Fort Smith's Joseph Burr officially kicked off with a a lot of determination we bid with Disabilities. I'm an Arctic Winter Games and a long-time member of the Tyrrell School, the Tuktoyak- flashy opening ceremony on on the 2018 games, and here Hay River's Olympic biath- alumnus," he said. -

Cornell Alumni News Volume 49, Number 7 November 15, 1946 Price 20 Cents
Cornell Alumni News Volume 49, Number 7 November 15, 1946 Price 20 Cents Dawson Catches a Pass from Burns in Yale Game on Schoellkopf Field "It is not the finding of a thing, but the making something out of it after it is found, that is of consequence ' —JAMES RUSSELL LOWELL Why some things get better all the time TAKE THE MODERN ELECTRIC LIGHT BULB, for ex- Producing better materials for the use of industry ample. Its parts were born in heat as high as 6,000° F. and the benefit of mankind is the work of Union ... in cold as low as 300° below zero . under crush- Carbide. ing pressure as great as 3,000 pounds per square inch. Basic knowledge and persistent research are re- Only in these extremes of heat, cold and pressure quired, particularly in the fields of science and en- did nature yield the metal tungsten for the shining gineering. Working with extremes of heat and cold, filament. argon, the colorless gas that fills the bulb and with vacuums and great pressures, Units of UCC . and the plastic that permanently seals the glass now separate or combine nearly one-half of the many to the metal stem. And it is because elements of the earth. of such materials that light bulbs today are better than ever before. The steady improvement of the TTNION CARBIDE V-/ AND CARBON CORPORATION electric light bulb is another in- stance of history repeating itself. For man has always Products of Divisions and Units include— had to have better materials before he could make ALLOYS AND METALS CHEMICALS PLASTICS ELECTRODES, CARBONS, AND BATTERIES better things. -

Attribution and Response to Cybercrime/Terrorism/Warfare Susan W
Journal of Criminal Law and Criminology Volume 97 Article 2 Issue 2 Winter Winter 2007 At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare Susan W. Brenner Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Susan W. Brenner, At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare, 97 J. Crim. L. & Criminology 379 (2006-2007) This Symposium is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. 0091-4169/07/9702-0379 THE JOURNALOF CRIMINAL LAW & CRIMINOLOGY Vol. 97. No. 2 Copyright 0 2007 by NorthwesternUniversity. Schoolof Low Printedin U.S.A. "AT LIGHT SPEED": ATTRIBUTION AND RESPONSE TO CYBERCRIME/TERRORISM/WARFARE SUSAN W. BRENNER* This Article explains why and how computer technology complicates the related processes of identifying internal (crime and terrorism) and external (war) threats to social order of respondingto those threats. First, it divides the process-attribution-intotwo categories: what-attribution (what kind of attack is this?) and who-attribution (who is responsiblefor this attack?). Then, it analyzes, in detail, how and why our adversaries' use of computer technology blurs the distinctions between what is now cybercrime, cyberterrorism, and cyberwarfare. The Article goes on to analyze how and why computer technology and the blurring of these distinctions erode our ability to mount an effective response to threats of either type. -

Palestinian Forces
Center for Strategic and International Studies Arleigh A. Burke Chair in Strategy 1800 K Street, N.W. • Suite 400 • Washington, DC 20006 Phone: 1 (202) 775 -3270 • Fax : 1 (202) 457 -8746 Email: [email protected] Palestinian Forces Palestinian Authority and Militant Forces Anthony H. Cordesman Center for Strategic and International Studies [email protected] Rough Working Draft: Revised February 9, 2006 Copyright, Anthony H. Cordesman, all rights reserved. May not be reproduced, referenced, quote d, or excerpted without the written permission of the author. Cordesman: Palestinian Forces 2/9/06 Page 2 ROUGH WORKING DRAFT: REVISED FEBRUARY 9, 2006 ................................ ................................ ............ 1 THE MILITARY FORCES OF PALESTINE ................................ ................................ ................................ .......... 2 THE OSLO ACCORDS AND THE NEW ISRAELI -PALESTINIAN WAR ................................ ................................ .............. 3 THE DEATH OF ARAFAT AND THE VICTORY OF HAMAS : REDEFINING PALESTINIAN POLITICS AND THE ARAB - ISRAELI MILITARY BALANCE ................................ ................................ ................................ ................................ .... 4 THE CHANGING STRUCTURE OF PALESTINIAN AUTHORITY FORC ES ................................ ................................ .......... 5 Palestinian Authority Forces During the Peace Process ................................ ................................ ..................... 6 The -

On the Military Utility of Spectral Design in Signature Management: a Systems Approach
National Defence University Series 1: Research Publications No. 21 On the Military Utility of Spectral Design in Signature Management: a Systems Approach On the Military Utility of Spectral Design in Signature On the Military Utility of Spectral Design in Signature Management: a Systems Approach Kent Andersson Kent Andersson National Defence University PL 7, 00861 HELSINKI Tel. +358 299 800 www.mpkk.fi ISBN 978-951-25-2998-8 (pbk.) ISBN 978-951-25-2999-5 (PDF) ISSN 2342-9992 (print) ISSN 2343-0001 (web) Series 1, No. 21 The Finnish Defence Forces KENT ANDERSSON ON THE MILITARY UTILITY OF SPECTRAL DESIGN IN SIGNATURE MANAGEMENT: A SYSTEMS APPROACH Doctoral dissertation for the degree of Doctor of Military Sciences to be presented, with the consent of the Finnish National Defence University, for public examination in Sverigesalen, at the Swedish Defence University, Drottning Kristinas väg 37, in Stockholm, on Friday 13th of April at 1 pm. NATIONAL DEFENCE UNIVERSITY HELSINKI 2018 NATIONAL DEFENCE UNIVERSITY SERIES 1: RESEARCH PUBLICATIONS NO. 21 FINSKA FÖRSVARSUNIVERSITETET SERIE 1: FORSKINGSPUBLIKATIONER NR. 21 ON THE MILITARY UTILITY OF SPECTRAL DESIGN IN SIGNATURE MANAGEMENT: A SYSTEMS APPROACH KENT ANDERSSON NATIONAL DEFENCE UNIVERSITY HELSINKI 2018 Kent Andersson: On the Military Utility of Spectral Design in Signature Management: a Sys- tems Approach National Defence University, Finland Series 1: Research Publications No. 21 Doctoral dissertation Finska Försvarshögskolan Publikationsserie 1: Forskingspublikationer nr. 21 Doktorsavhandling Author: Lt Col, Tech. Lic. Kent Andersson Supervising professor: Professor Jouko Vankka, National Defence University, Finland Preliminary examiners: Professor Harold Lawson, Prof. Emeritus, ACM, IEEE and INCOSE Fellow, IEEE Computer pioneer, Sweden Professor Christer Larsson, Lund University, Sweden Official opponents: Professor Jari Hartikainen, Finnish Defence Research Agency, Finland Professor Harold Lawson, Prof. -

When Are Foreign Volunteers Useful? Israel's Transnational Soldiers in the War of 1948 Re-Examined
This is a repository copy of When are Foreign Volunteers Useful? Israel's Transnational Soldiers in the War of 1948 Re-examined. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/79021/ Version: WRRO with coversheet Article: Arielli, N (2014) When are Foreign Volunteers Useful? Israel's Transnational Soldiers in the War of 1948 Re-examined. Journal of Military History, 78 (2). pp. 703-724. ISSN 0899- 3718 Reuse Items deposited in White Rose Research Online are protected by copyright, with all rights reserved unless indicated otherwise. They may be downloaded and/or printed for private study, or other acts as permitted by national copyright laws. The publisher or other rights holders may allow further reproduction and re-use of the full text version. This is indicated by the licence information on the White Rose Research Online record for the item. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ promoting access to White Rose research papers Universities of Leeds, Sheffield and York http://eprints.whiterose.ac.uk/ White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/79021/ Paper: Arielli, N (2014) When are foreign volunteers useful? Israel's transnational soldiers in the war of 1948 re-examined. Journal of Military History, 78 (2). 703 - 724. White Rose Research Online [email protected] When are Foreign Volunteers Useful? Israel’s Transnational Soldiers in the War of 1948 Re-examined Nir Arielli Abstract The literature on foreign, or “transnational,” war volunteering has fo- cused overwhelmingly on the motivations and experiences of the vol- unteers. -

Framing Mali Swedish Media Portrayal of an Armed Conflict
Framing Mali Swedish media portrayal of an armed conflict Niklas Norberg Department of Media Studies, Department of Journalism, Media and C ommunication Studies (JMK) Master’s Thesis in Journalism 30 EC TS Journalism Studies Master’s Programme in Journalism (120 EC TS) Spring term 2018 Supervisor: Magnus Danielson Examiner: C hristian C hristensen Framing Mali: Swedish media portrayal of an armed conflict Master's thesis Niklas Norberg VT18 Abstract Research has shown that news media reporting on foreign affairs tend to rely heavily on official sources (e.g. Schwalbe, 2013; Entman, 2004; Lawrence, 2009). This thesis analyse whether this is the case in Swedish news media reporting on the armed conflict in Mali, where Sweden has troops sanctioned by the UN. A more broader perspective is also analysed: How does the news media portray the armed conflict, and are there any differences between national daily newspapers (considered more “sober”) and national evening newspapers (considered more sensational)? An inductive framing analysis is used to identify frames not available in previous research. These frames, together with frames identified in other studies, are then used in a quantitative content analysis to measure to what extent the frames occur in the texts. Among the most important findings were that Swedish news media did in fact rely on Swedish official reporting to a large extent. The two evening newspapers, Aftonbladet and Expressen, used Swedish official sources in approximately 60% of their articles. The daily newspapers, Dagens Nyheter and Svenska Dagbladet, used Swedish official sources in about 35% of their articles. The main source used was also analyzed: This showed that Swedish official sources were the most common, in between 23% to 62% of the articles. -

Explosive Weapon Effectsweapon Overview Effects
CHARACTERISATION OF EXPLOSIVE WEAPONS EXPLOSIVEEXPLOSIVE WEAPON EFFECTSWEAPON OVERVIEW EFFECTS FINAL REPORT ABOUT THE GICHD AND THE PROJECT The Geneva International Centre for Humanitarian Demining (GICHD) is an expert organisation working to reduce the impact of mines, cluster munitions and other explosive hazards, in close partnership with states, the UN and other human security actors. Based at the Maison de la paix in Geneva, the GICHD employs around 55 staff from over 15 countries with unique expertise and knowledge. Our work is made possible by core contributions, project funding and in-kind support from more than 20 governments and organisations. Motivated by its strategic goal to improve human security and equipped with subject expertise in explosive hazards, the GICHD launched a research project to characterise explosive weapons. The GICHD perceives the debate on explosive weapons in populated areas (EWIPA) as an important humanitarian issue. The aim of this research into explosive weapons characteristics and their immediate, destructive effects on humans and structures, is to help inform the ongoing discussions on EWIPA, intended to reduce harm to civilians. The intention of the research is not to discuss the moral, political or legal implications of using explosive weapon systems in populated areas, but to examine their characteristics, effects and use from a technical perspective. The research project started in January 2015 and was guided and advised by a group of 18 international experts dealing with weapons-related research and practitioners who address the implications of explosive weapons in the humanitarian, policy, advocacy and legal fields. This report and its annexes integrate the research efforts of the characterisation of explosive weapons (CEW) project in 2015-2016 and make reference to key information sources in this domain. -

2018 U.S. Under-18 Men's National Team Game Notes Preliminary Round Vs
2018 U.S. UNDER-18 MEN’S NATIONAL TEAM GAME NOTES 2018 IIHF UNDER-18 MEN’S WORLD CHAMPIONSHIP | CHELYABINSK & MAGNITOGORSK, RUSSIA PRELIMINARY ROUND GAME #1 • USA (0-0-0-1) VS. SWITZERLAND (0-0-0-1) • METALLURG ICE RINK (CAPACITY: 7,500) • APRIL 20, 2018 TONIGHT'S GAME THINGS WORTH MENTIONING The U.S. Under-18 Men's National Team faces Switzerland this The United States has only lost 18 preliminary round games afternoon in its second preliminary round matchup in Group A and has only lost one preliminary round game to Switzerland... play at the 2018 IIHF Under-18 Men's World Championship here Team USA will be led by Mattias Samuelsson (Voorhees, N.J./ in Magnitogorsk, Russia. Puck drop is set for 3:30 p.m. local USAH NTDP) who will serve as team captain while Ty Emberson and 6:30 a.m. ET and will be televised in the U.S. live on NHL (Eau Claire, Wis./ USAH NTDP), Patrick Giles (Chevy Chase, Network. Md./ USAH NTDP), Jonathan Gruden (Rochester, Mich./ USAH Switzterland is coming off a 3-1 loss to Sweden in its opening NTDP) and Jake Pivonka (Naperville, Ill./ USAH NTDP) will serve preliminary round game on Thursday afternoon at Metallurg as alternate captains ... Team USA has two returning players, Ice Rink. Kyen Sopa picked up the lone goal for Switzerland in Joel Farabee (Cicero, N.Y.) and Oliver Wahlstrom (Quincy, the loss and goaltender Luca Hollenstein made 30 saves on 33 Mass.) from last year's gold-medal team and both scored in the shots. -
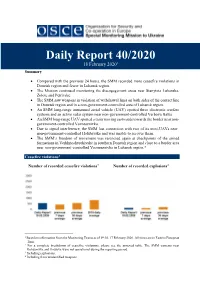
Daily Report 40/2020 18 February 20201 Summary
- 1 - Daily Report 40/2020 18 February 20201 Summary • Compared with the previous 24 hours, the SMM recorded more ceasefire violations in Donetsk region and fewer in Luhansk region. • The Mission continued monitoring the disengagement areas near Stanytsia Luhanska, Zolote and Petrivske. • The SMM saw weapons in violation of withdrawal lines on both sides of the contact line in Donetsk region and in a non-government-controlled area of Luhansk region. • An SMM long-range unmanned aerial vehicle (UAV) spotted three electronic warfare systems and an active radar system near non-government-controlled Verbova Balka. • An SMM long-range UAV spotted a train moving eastwards towards the border near non- government-controlled Voznesenivka. • Due to signal interference, the SMM lost connection with two of its mini-UAVs near non-government-controlled Holubivske and was unable to recover them. • The SMM’s freedom of movement was restricted again at checkpoints of the armed formations in Verkhnoshyrokivske in southern Donetsk region and close to a border area near non-government-controlled Voznesenivka in Luhansk region.* Ceasefire violations2 Number of recorded ceasefire violations3 Number of recorded explosions4 1 Based on information from the Monitoring Teams as of 19:30, 17 February 2020. All times are in Eastern European Time. 2 For a complete breakdown of ceasefire violations, please see the annexed table. The SMM cameras near Bohdanivka and Hnutove were not operational during the reporting period. 3 Including explosions. 4 Including from unidentified weapons. - 2 - Map of recorded ceasefire violations - 3 - In Donetsk region, the SMM recorded more ceasefire violations, including more explosions (about 105), compared with the previous 24 hours (15 explosions).