Snowbound TIFF Tags.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Microsoft Office Open XML Formats New File Formats for “Office 12”
The Microsoft Office Open XML Formats New File Formats for “Office 12” White Paper Published: June 2005 For the latest information, please see http://www.microsoft.com/office/wave12 Contents Introduction ...............................................................................................................................1 From .doc to .docx: a brief history of the Office file formats.................................................1 Benefits of the Microsoft Office Open XML Formats ................................................................2 Integration with Business Data .............................................................................................2 Openness and Transparency ...............................................................................................4 Robustness...........................................................................................................................7 Description of the Microsoft Office Open XML Format .............................................................9 Document Parts....................................................................................................................9 Microsoft Office Open XML Format specifications ...............................................................9 Compatibility with new file formats........................................................................................9 For more information ..............................................................................................................10 -

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -

MPEG-21 Overview
MPEG-21 Overview Xin Wang Dept. Computer Science, University of Southern California Workshop on New Multimedia Technologies and Applications, Xi’An, China October 31, 2009 Agenda ● What is MPEG-21 ● MPEG-21 Standards ● Benefits ● An Example Page 2 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang MPEG Standards ● MPEG develops standards for digital representation of audio and visual information ● So far ● MPEG-1: low resolution video/stereo audio ● E.g., Video CD (VCD) and Personal music use (MP3) ● MPEG-2: digital television/multichannel audio ● E.g., Digital recording (DVD) ● MPEG-4: generic video and audio coding ● E.g., MP4, AVC (H.24) ● MPEG-7 : visual, audio and multimedia descriptors MPEG-21: multimedia framework ● MPEG-A: multimedia application format ● MPEG-B, -C, -D: systems, video and audio standards ● MPEG-M: Multimedia Extensible Middleware ● ● MPEG-V: virtual worlds MPEG-U: UI ● (29116): Supplemental Media Technologies ● ● (Much) more to come … Page 3 Workshop on New Multimedia Technologies and Applications, Oct. 2009, Xin Wang What is MPEG-21? ● An open framework for multimedia delivery and consumption ● History: conceived in 1999, first few parts ready early 2002, most parts done by now, some amendment and profiling works ongoing ● Purpose: enable all-electronic creation, trade, delivery, and consumption of digital multimedia content ● Goals: ● “Transparent” usage ● Interoperable systems ● Provides normative methods for: ● Content identification and description Rights management and protection ● Adaptation of content ● Processing on and for the various elements of the content ● ● Evaluation methods for determining the appropriateness of possible persistent association of information ● etc. Page 4 Workshop on New Multimedia Technologies and Applications, Oct. -
![Adobe's Extensible Metadata Platform (XMP): Background [DRAFT -- Caroline Arms, 2011-11-30]](https://docslib.b-cdn.net/cover/4654/adobes-extensible-metadata-platform-xmp-background-draft-caroline-arms-2011-11-30-104654.webp)
Adobe's Extensible Metadata Platform (XMP): Background [DRAFT -- Caroline Arms, 2011-11-30]
Adobe's Extensible Metadata Platform (XMP): Background [DRAFT -- Caroline Arms, 2011-11-30] Contents • Introduction • Adobe's XMP Toolkits • Links to Adobe Web Pages on XMP Adoption • Appendix A: Mapping of PDF Document Info (basic metadata) to XMP properties • Appendix B: Software applications that can read or write XMP metadata in PDFs • Appendix C: Creating Custom Info Panels for embedding XMP metadata Introduction Adobe's XMP (Extensible Metadata Platform: http://www.adobe.com/products/xmp/) is a mechanism for embedding metadata into content files. For example. an XMP "packet" can be embedded in PDF documents, in HTML and in image files such as TIFF and JPEG2000 as well as Adobe's own PSD format native to Photoshop. In September 2011, XMP was approved as an ISO standard.[ ISO 16684-1: Graphic technology -- Extensible metadata platform (XMP) specification -- Part 1: Data model, serialization and core properties] XMP is an application of the XML-based Resource Description Framework (RDF; http://www.w3.org/TR/2004/REC-rdf-primer-20040210/), which is a generic way to encode metadata from any scheme. RDF is designed for it to be easy to use elements from any namespace. An important application area is in publication workflows, particularly to support submission of pictures and advertisements for inclusion in publications. The use of RDF allows elements from different schemes (e.g., EXIF and IPTC for photographs) to be held in a common framework during processing workflows. There are two ways to get XMP metadata into PDF documents: • manually via a customized File Info panel (or equivalent for products from vendors other than Adobe). -

XMP SPECIFICATION PART 3 STORAGE in FILES Copyright © 2016 Adobe Systems Incorporated
XMP SPECIFICATION PART 3 STORAGE IN FILES Copyright © 2016 Adobe Systems Incorporated. All rights reserved. Adobe XMP Specification Part 3: Storage in Files NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. Adobe, the Adobe logo, Acrobat, Acrobat Distiller, Flash, FrameMaker, InDesign, Illustrator, Photoshop, PostScript, and the XMP logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. MS-DOS, Windows, and Windows NT are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Apple, Macintosh, Mac OS and QuickTime are trademarks of Apple Computer, Inc., registered in the United States and other countries. UNIX is a trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. All other trademarks are the property of their respective owners. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and noninfringement of third party rights. Contents 1 Embedding XMP metadata in application files . -

Quadtree Based JBIG Compression
Quadtree Based JBIG Compression B. Fowler R. Arps A. El Gamal D. Yang ISL, Stanford University, Stanford, CA 94305-4055 ffowler,arps,abbas,[email protected] Abstract A JBIG compliant, quadtree based, lossless image compression algorithm is describ ed. In terms of the numb er of arithmetic co ding op erations required to co de an image, this algorithm is signi cantly faster than previous JBIG algorithm variations. Based on this criterion, our algorithm achieves an average sp eed increase of more than 9 times with only a 5 decrease in compression when tested on the eight CCITT bi-level test images and compared against the basic non-progressive JBIG algorithm. The fastest JBIG variation that we know of, using \PRES" resolution reduction and progressive buildup, achieved an average sp eed increase of less than 6 times with a 7 decrease in compression, under the same conditions. 1 Intro duction In facsimile applications it is desirable to integrate a bilevel image sensor with loss- less compression on the same chip. Suchintegration would lower p ower consumption, improve reliability, and reduce system cost. To reap these b ene ts, however, the se- lection of the compression algorithm must takeinto consideration the implementation tradeo s intro duced byintegration. On the one hand, integration enhances the p os- sibility of parallelism which, if prop erly exploited, can sp eed up compression. On the other hand, the compression circuitry cannot b e to o complex b ecause of limitations on the available chip area. Moreover, most of the chip area on a bilevel image sensor must b e o ccupied by photo detectors, leaving only the edges for digital logic. -

Digital Forensics Tool Testing – Image Metadata in the Cloud
Digital Forensics Tool Testing – Image Metadata in the Cloud Philip Clark Master’s Thesis Master of Science in Information Security 30 ECTS Department of Computer Science and Media Technology Gjøvik University College, 2011 Avdeling for informatikk og medieteknikk Høgskolen i Gjøvik Postboks 191 2802 Gjøvik Department of Computer Science and Media Technology Gjøvik University College Box 191 N-2802 Gjøvik Norway Digital Forensics Tool Testing – Image Metadata in the Cloud Abstract As cloud based services are becoming a common way for users to store and share images on the internet, this adds a new layer to the traditional digital forensics examination, which could cause additional potential errors in the investigation. Courtroom forensics evidence has historically been criticised for lacking a scientific basis. This thesis aims to present an approach for testing to what extent cloud based services alter or remove metadata in the images stored through such services. To exemplify what information which could potentially reveal sensitive information through image metadata, an overview of what information is publically shared will be presented, by looking at a selective section of images published on the internet through image sharing services in the cloud. The main contributions to be made through this thesis will be to provide an overview of what information regular users give away while publishing images through sharing services on the internet, either willingly or unwittingly, as well as provide an overview of how cloud based services handle Exif metadata today, along with how a forensic practitioner can verify to what extent information through a given cloud based service is reliable. -

OASIS CGM Open Webcgm V2.1
WebCGM Version 2.1 OASIS Standard 01 March 2010 Specification URIs: This Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1-index.html (AUTHORITATIVE) PDF: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/os/webcgm-v2.1.zip Previous Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1-index.html (AUTHORITATIVE) PDF: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/cs02/webcgm-v2.1.zip Latest Version: XHTML multi-file: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1-index.html PDF: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1.pdf XHTML ZIP archive: http://docs.oasis-open.org/webcgm/v2.1/latest/webcgm-v2.1.zip Declared XML namespaces: http://www.cgmopen.org/schema/webcgm/ System Identifier: http://docs.oasis-open.org/webcgm/v2.1/webcgm21.dtd Technical Committee: OASIS CGM Open WebCGM TC Chair(s): Stuart Galt, The Boeing Company Editor(s): Benoit Bezaire, PTC Lofton Henderson, Individual Related Work: This specification updates: WebCGM 2.0 OASIS Standard (and W3C Recommendation) This specification, when completed, will be identical in technical content to: WebCGM 2.1 W3C Recommendation, available at http://www.w3.org/TR/webcgm21/. Abstract: Computer Graphics Metafile (CGM) is an ISO standard, defined by ISO/IEC 8632:1999, for the interchange of 2D vector and mixed vector/raster graphics. -

Development of National Digital Evidence Metadata
JOIN (Jurnal Online Informatika) Volume 4 No. 1 | Juni 2019 : 24-27 DOI: 10.15575/join.v4i1.292 Development of National Digital Evidence Metadata Bambang Sugiantoro Magister of Informatics, UIN Sunan Kalijaga, Yogyakarta, Indonesia [email protected] Abstract- The industrial era 4.0 has caused tremendous disruption in many sectors of life. The rapid development of information and communication technology has made the global industrial world undergo a revolution. The act of cyber-crime in Indonesia that utilizes computer equipment, mobile phones are increasingly increasing. The information in a file whose contents are explained about files is called metadata. The evidence items for cyber cases are divided into two types, namely physical evidence, and digital evidence. Physical evidence and digital evidence have different characteristics, the concept will very likely cause problems when applied to digital evidence. The management of national digital evidence that is associated with continued metadata is mostly carried out by researchers. Considering the importance of national digital evidence management solutions in the cyber-crime investigation process the research focused on identifying and modeling correlations with the digital image metadata security approach. Correlation analysis reads metadata characteristics, namely document files, sounds and digital evidence correlation analysis using standard file maker parameters, size, file type and time combined with digital image metadata. nationally designed the highest level of security is needed. Security-enhancing solutions can be encrypted against digital image metadata (EXIF). Read EXIF Metadata in the original digital image based on the EXIF 2.3 Standard ID Tag, then encrypt and insert it into the last line. -

JPEG Standard
JPEG standard JPEG: “Joint Photographic Experts Group” Formally: ISO/IEC JTC1/SC29/WG10 Working Group 10 International (JBIG, JPEG) Organization for Subcommittee 29 Standardization Joint ISO/IEC (Coding of Audio, Technical International Picture, Multimedia Committee Electrotechnical and Hypermedia (Information Commission Information) Technology) Joint effort with CCITT (International Telephone and Telegraph Consultative Committee, now ITU-T) Study Group VIII Work commenced in 1986 International standard ISO/IEC 10918-1 and CCITT Rec. T.81 in 1992 Widely used for image exchange, WWW, and digital photography Motion-JPEG is de facto standard for digital video editing Bernd Girod: EE398A Image and Video Compression JPEG standard no. 1 JPEG: image partition into 8x8 block 8x8 blocks Padding of right boundary blocks Padding of lower boundary blocks Bernd Girod: EE398A Image and Video Compression JPEG standard no. 2 Baseline JPEG coder DC Huffman tables dc quantization indices Differential coding VLC Level 8x8 Uniform Compressed scalar image data input offset DCT quantization image Zig-zag Run-level scan coding VLC Compressed image data ac quantization indices Quantization tables AC Huffman tables Bernd Girod: EE398A Image and Video Compression JPEG standard no. 3 Recommended quantization tables Based on psychovisual threshold experiments Luminance Chrominance, subsampled 2:1 16 11 10 16 24 40 51 61 17 18 24 47 99 99 99 99 12 12 14 19 26 58 60 55 18 21 26 66 99 99 99 99 14 13 16 24 40 57 69 56 24 26 56 99 99 99 99 99 14 17 22 29 51 87 80 62 47 66 99 99 99 99 99 99 18 22 37 56 68 109 103 77 99 99 99 99 99 99 99 99 24 36 55 64 81 104 113 92 99 99 99 99 99 99 99 99 49 64 78 87 103 121 120 101 99 99 99 99 99 99 99 99 72 92 95 98 112 100 103 99 99 99 99 99 99 99 99 99 [JPEG Standard, Annex K] Bernd Girod: EE398A Image and Video Compression JPEG standard no. -
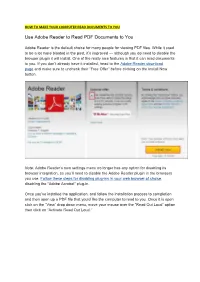
Use Adobe Reader to Read PDF Documents to You
HOW TO MAKE YOUR COMPUTER READ DOCUMENTS TO YOU Use Adobe Reader to Read PDF Documents to You Adobe Reader is the default choice for many people for viewing PDF files. While it used to be a lot more bloated in the past, it’s improved — although you do need to disable the browser plugin it will install. One of the really nice features is that it can read documents to you. If you don’t already have it installed, head to the Adobe Reader download page and make sure to uncheck their “Free Offer” before clicking on the Install Now button. Note: Adobe Reader’s own settings menu no longer has any option for disabling its browser integration, so you’ll need to disable the Adobe Reader plugin in the browsers you use. Follow these steps for disabling plug-ins in your web browser of choice, disabling the “Adobe Acrobat” plug-in. Once you’ve installed the application, and follow the installation process to completion and then open up a PDF file that you’d like the computer to read to you. Once it is open click on the “View” drop down menu, move your mouse over the “Read Out Loud” option then click on “Activate Read Out Loud.” Alternatively, you can click “Ctrl,” “Shift,” and “Y” (Ctrl+Shift+Y) on your keyboard to activate the feature. Once the feature is activated, you can click on a single paragraph to make windows read it back to you. Another option would be to navigate to the “View” menu, then “Read Out Loud” and select an option that fits your needs as shown in the Image below. -

EXIF: a Format Is Worth a Thousand Words
NATIONAL LAW ENFORCEMENT AND CORRECTIONS TECHNOLOGY CENTER A program of the Office of Justice Programs’ National Institute of Justice From Winter 2007 TechBeat TECH b • e • a • t Dedicated to Reporting Developments in Technology for Law Enforcement, Corrections, and Forensic Sciences EXIF: A Format Is Worth A Thousand Words he National Center for Missing & Exploited Children if they are used only to open the file. If, however, these T revealed in a June 2005 study that 40 percent of arrest- programs are used to modify an image, they can destroy ed child pornography possessors had both sexually the Exif data. victimized children and were in possession of child pornog- The most important data may be the thumbnail image raphy. Due in part to the increasing prevalence of child exploitation and pornography, the digital photograph has linked to the photograph. Thumbnails are saved in their now become a fixture in gathering and examining forensic own hidden file (a thumbs.db file placed in folders con- evidence in such cases. taining images on the computer), and changes to an image may not always transfer to the corresponding Investigators who frequently handle child pornogra- thumbnail. If an original image is wiped from a disk using phy cases usually have (or know where to access) the a program such as Secure Clean™ or BCWipe®, the thumb- tools and the knowledge to obtain evidence associated nail may still be available. Officers have encountered situ- with contraband images. Nevertheless, law enforcement ations in which the victim’s or perpetrator’s face was officers who do not handle these cases on a regular basis blurred or concealed in the full image, but the thumbnail may be unaware of the important data that can be depicted an older version that revealed the obscured derived from digital images.