Battlefield Ukraine: Finding Patterns Behind Summer Cyber Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

REQUIEM for DONBAS Three Essays on the Costs of War in Ukraine
JOHANNES KEPLER UNIVERSITY LINZ Altenberger Str. 69 4040 Linz, Austria www.jku.at, DVR 0093696 REQUIEM FOR DONBAS Three Essays on the Costs of War in Ukraine By Artem Kochnev A Doctoral Thesis submitted at Department of Economics to obtain the academic degree of Doctor of Philosophy in the Doctoral Program “PhD Program in Economics” Supervisor and First Examiner Second Examiner em. Univ-Prof. Dr. Michael Landesmann Dr. habil. rer. soc. oec. Robert Stehrer May 2020 Abstract The thesis investigates short- and long-term effects of war on the economy of Ukraine. Specifically, it discusses the impact of separatists’ control and subsequent adverse trade policies on the real economy, responses of stock market investors to battle events, and the effect of conflict intensity on reform progress and institutional change in Ukraine. The thesis finds that the impact of war on the economy is most pronounced on the real economy of the war-torn regions. Whereas separatists’ control caused a decline in economic activity by at least 38%, the thesis does not find evidence supporting that the impact of conflict intensity on asset prices and institutional change in Ukraine was linear in parameters. The thesis explains the lack of the linear relationship between asset price move- ments and conflict intensity by investors’ inattention caused by information overload during the early stages of the conflict. Regarding the possible relationship between con- flict and institutional change, the thesis argues that it was electoral competition, not the conflict dynamics, that had an impact on the decision-making process of the policymak- ers in Ukraine. -

Naftogaz of Ukraine 2014 Annual Report
NAFTOGAZ OF UKRAINE 2014 ANNUAL REPORT New Ukraine Europe New rules Market Transparency Naftogaz Reform Europe New Ukraine Europe New rules Naftogaz Market Europe New UkraineNew Transparency Reform Ukraine Naftogaz New rules Europe Naftogaz New Ukraine Market Naftogaz Europe New Ukraine Reform Transparency Naftogaz EuropeReform Europe Naftogaz New Ukraine New rules Transparency New rules Transparency New rules Europe Transparency New Ukraine Naftogaz New rules Europe Market Reform Reform Naftogaz Market Reform TransparencyNew rules Reform Europe New rules Market Reform Transparency New Ukraine Transparency Transparency Naftogaz New Ukraine Naftogaz New rules Reform NaftogazTransparency Market New rules Reform Europe Reform Naftogaz New rules Europe Naftogaz New Ukraine Transparency Market Transparency New rules Naftogaz Transparency Reform Europe New rules Market New Ukraine New Ukraine Transparency New rules New rules Market Market New Ukraine Europe Transparency Reform Europe New Ukraine New Ukraine Naftogaz Transparency New rules Reform New rules Naftogaz New rules New Ukraine Reform Market Europe New rules ReformNaftogaz Transparency Europe Reform Naftogaz Transparency Reform MarketNaftogaz Reform Naftogaz New rules Naftogaz New Ukraine Market Market Naftogaz Transparency Transparency Reform Europe Transparency New rules New rules New rules Reform New Ukraine Market Transparency New rules Naftogaz Market Europe Changing for the future Ukraine’s gas transmission Entry capacity: EUROPE’S LARGEST GAS MARKETS, 2014, bcm NAFTOGAZ AT A -

Daily Insight Ukrproduct and XXI Century in the Spotlight
Focus UKRAINE Scope CAPITAL MARKETS Daily Insight Ukrproduct and XXI Century in the spotlight THURSDAY, 30 APRIL, 2009 RESEARCH INSIGHT Market comment Key rates and indices (as of 29 Apr 2009) Last Daily YTD FX and capital markets yesterday chg1 (%) chg1 (%) The hryvnia weakened towards 8.07/USD as of the end of yesterday after trading Currencies within a thin bound of 8.05-8.07/USD most of the day, according to the Reuters USD/UAH (spot) 8.0700 1.38 3.46 data. The equities shifted broadly higher yesterday, as the PFTS index closed up USD/UAH (1Y NDF) 11.5000 0.00 -14.18 at 333.72 points, up 3.67% compared to the previous session. EUR/USD (spot) 1.3263 0.91 -5.12 Money market Equity market KievPRIME O/N (%) 2.20 20bp -2,078bp KievPRIME 1M (%) 17.10 0bp -668bp XXIC seeks to postpone Eurobond put date to 8 July, 2009 Bond markets As part of its US$175m Eurobond restructuring efforts, XXIC held a conference EMBI+ Ukraine 1,884 0.27 580.14 Equity markets call on 23 April to discuss the proposed restructuring terms. The outcome was PFTS (Ukraine) 333.72 3.67 10.72 twofold: 1) the bondholders representing US$135m in aggregate principal RTS (Russia) 814.78 3.92 28.94 amount have expressed in writing their intention to exercise their put option; and WIG (Poland) 28,273.93 3.50 3.84 2) the bondholders representing the majority of the principal amount have S&P 500 (USA) 873.64 2.16 -3.28 suggested that the company seek a “standstill” to postpone the put exercise date Note: 1) percentage change if not otherwise stated. -

Reforms in Ukraine After Revolution of Dignity
REFORMS IN UKRAINE AFTER REVOLUTION OF DIGNITY What was done, why not more and what to do next This publicaon was produced with financial Responsibility for the informaon and views set out assistance from the EBRD-Ukraine Stabilisaon and in this publicaon lies enrely with the authors. The Sustainable Growth Mul-Donor Account, the EBRD makes no representaon or warranty, express donors of which are Denmark, Finland, France, or implied, as to the accuracy or completeness of the Germany, Italy, Japan, the Netherlands, Norway, informaon set forth in the publicaon. The EBRD Poland, Sweden, Switzerland, the United Kingdom, has not independently verified any of the informaon the United States of America and the European contained in the publicaon and the EBRD accepts Union, the largest donor. The views expressed herein no liability whatsoever for any of the informaon can in no way be taken to reflect the official opinion contained in the publicaon or for any misstatement of the EBRD or any donor of the account. or omission therein. The publicaon remains the property of the EBRD. REFORMS IN UKRAINE AFTER REVOLUTION OF DIGNITY What was done, why not more and what to do next Editors Ivan Miklos Pavlo Kukhta Contents Foreword 4 Introducon What was done, why not more and what to do next: Ukrainian reforms aer the Revoluon of Dignity 7 Chapter 1 Polical economy of reforms: polical system, governance and corrupon 10 Chapter 2 Macroeconomic policies 35 Chapter 3 Rule of law 48 Chapter 4 Energy policy 75 Chapter 5 Business environment 87 Chapter 6 Land reform 101 Chapter 7 Privasaon and SOE reform 112 Chapter 8 Healthcare reform 132 Chapter 9 Ukraine and the European Union 144 Annex 1 Report on reforms in 2016-17 162 Annex 2 The role of the government and MPs in reform implementaon in Ukraine 167 About SAGSUR (Strategic Advisory Group for Support of Ukrainian Reforms) 173 Glossary of terms 174 Foreword Foreword | 4 Foreword Maeo Patrone and Peter M. -

Russia's Hostile Measures in Europe
Russia’s Hostile Measures in Europe Understanding the Threat Raphael S. Cohen, Andrew Radin C O R P O R A T I O N For more information on this publication, visit www.rand.org/t/RR1793 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-1-9774-0077-2 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2019 RAND Corporation R® is a registered trademark. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface This report is the collaborative and equal effort of the coauthors, who are listed in alphabetical order. The report documents research and analysis conducted through 2017 as part of a project entitled Russia, European Security, and “Measures Short of War,” sponsored by the Office of the Deputy Chief of Staff, G-3/5/7, U.S. -

Impact of Political Course Shift in Ukraine on Stock Returns
IMPACT OF POLITICAL COURSE SHIFT IN UKRAINE ON STOCK RETURNS by Oleksii Marchenko A thesis submitted in partial fulfillment of the requirements for the degree of MA in Economic Analysis Kyiv School of Economics 2014 Thesis Supervisor: Professor Tom Coupé Approved by ___________________________________________________ Head of the KSE Defense Committee, Professor Irwin Collier __________________________________________________ __________________________________________________ __________________________________________________ Date ___________________________________ Kyiv School of Economics Abstract IMPACT OF POLITICAL COURSE SHIFT IN UKRAINE ON STOCK RETURNS by Oleksii Marchenko Thesis Supervisor: Professor Tom Coupé Since achieving its independence from the Soviet Union, Ukraine has faced the problem which regional block to integrate in. In this paper an event study is used to investigate investors` expectations about winners and losers from two possible integration options: the Free Trade Agreement as a part of the Association Agreement with the European Union and the Custom Union of Russia, Belarus and Kazakhstan. The impact of these two sudden shifts in the political course on stock returns is analyzed to determine the companies which benefit from each integration decisions. No statistically significant impact on stock returns could be detected. However, our findings suggest a large positive reaction of companies` stock prices to the dismissal of Yanukovych regime regardless of company`s trade orientation and political affiliation. -

Mary Butler Deputy Chief, International Unit Asset Forfeiture and Money Laundering Section Department of Justice, the U.S
Organizers Partners Programmatic Cooperation Framework for Armenia, Azerbaijan, Georgia, Republic of Moldova, Ukraine and Belarus uniter Mediapartners Preventing.Fighting.Acting. International Anti-Corruption Conference November 16th, 2015 Timing Conference section title 08:00 AM Registration 09:30 AM SESSION I Making Ukraine a Success Story 09:30 AM Place: Olympic Yard 10:30 AM 10:30 AM Coffee break 10:50 AM PARALLEL Corruption prevention Investigation of corruption Return of stolen assets SESSIONS II Place: Hall of Champions cases and sanctions Place: Altius 10:50 AM Place: Olympic Yard 12:50 PM 12:50 PM Lunch break 13:50 PM PARALLEL Zero tolerance to Mainstreaming anti-corruption Corruption and SESSIONS III corruption in sectoral and regional reforms business 13:50 PM Place: Hall of Champions Place: Olympic Yard Place: Altius 15:50 PM 15:50 PM Coffee break 16:15 PM SESSION IV Plenary closing session 16:15 PM Place: Olympic Yard 17:15 PM 17:20 PM Networking dinner 19:00 PM SESSION I Making Ukraine a Success Story 09:30 AM Place: Olympic Yard 10:30 AM Moderator: Mr. Andriy Kulikov Senior media-expert, journalist 1. Mr. Pavlo Petrenko Minister of Justice, Ukraine 2. Mr. Goran Klemenčič Minister of Justice, Slovenia 3. Mr. Paweł Wojtunik Head of the Central Anticorruption Bureau, Poland 4. Mr. Arkan El-Seblani Chief Technical Advisor, Anti-Corruption and Integrity in the Arab States, UNDP 5. Mr. Nicola Bonucci Director for Legal Affairs, OECD 6. Mr. Björn Janson Deputy to the Executive Secretary of GRECO, Council of Europe Andriy Kulikov Senior media-expert, journalist Mr. -

Foreign Satellite & Satellite Systems Europe Africa & Middle East Asia
Foreign Satellite & Satellite Systems Europe Africa & Middle East Albania, Austria, Belarus, Belgium, Bosnia & Algeria, Angola, Benin, Burkina Faso, Cameroon, Herzegonia, Bulgaria, Croatia, Czech Republic, Congo Brazzaville, Congo Kinshasa, Egypt, France, Germany, Gibraltar, Greece, Hungary, Ethiopia, Gabon, Ghana, Ivory Coast, Kenya, Iceland, Ireland, Italy, Luxembourg, Macedonia, Libya, Mali, Mauritania, Mauritius, Morocco, Moldova, Montenegro, The Netherlands, Norway, Mozambique, Namibia, Niger, Nigeria, Senegal, Poland, Portugal, Romania, Russia, Serbia, Somalia, South Africa, Sudan, Tanzania, Tunisia, Slovakia, Slovenia, Spain, Sweden, Switzerland, Uganda, Western Sahara, Zambia. Armenia, Ukraine, United Kingdom. Azerbaijan, Bahrain, Cyprus, Georgia, Iran, Iraq, Israel, Jordan, Kuwait, Lebanon, Oman, Palestine, Qatar, Saudi Arabia, Syria, Turkey, United Arab Emirates, Yemen. Asia & Pacific North & South America Afghanistan, Bangladesh, Bhutan, Cambodia, Canada, Costa Rica, Cuba, Dominican Republic, China, Hong Kong, India, Japan, Kazakhstan, Honduras, Jamaica, Mexico, Puerto Rico, United Kyrgyzstan, Laos, Macau, Maldives, Myanmar, States of America. Argentina, Bolivia, Brazil, Nepal, Pakistan, Phillipines, South Korea, Chile, Columbia, Ecuador, Paraguay, Peru, Sri Lanka, Taiwan, Tajikistan, Thailand, Uruguay, Venezuela. Uzbekistan, Vietnam. Australia, French Polynesia, New Zealand. EUROPE Albania Austria Belarus Belgium Bosnia & Herzegovina Bulgaria Croatia Czech Republic France Germany Gibraltar Greece Hungary Iceland Ireland Italy -

Ministry of Energy and Coal Industry of Ukraine Is the Main Executive Au- ‣‣Thority Overseeing and Regulating the Power Sector
Contents FOREWORD 2 SOE PORTFOLIO: SNAPSHOT 4 OBJECTIVES AND STRUCTURE 5 OVERVIEW OF SOE REFORM IN UKRAINE 6 EFFECTIVE REGULATORY FRAMEWORK OF SOEs IN UKRAINE 20 UKRAINIAN ECONOMY 33 OVERVIEW OF PORTFOLIO RESULTS 38 ELECTRICITY 46 OIL & GAS 61 TRANSPORTATION 71 RAILWAYS 73 ROADS 78 AIRPORTS 82 SEA PORTS 88 POSTAL SERVICES 94 MACHINE BUILDING 98 FOOD & AGRICULTURE 113 CHEMICALS 129 COAL MINING 137 BANKING 143 COMPANY PROFILES 153 Agrarian Fund 154 Antonov 155 Centrenergo 156 Coal of Ukraine 157 Electrovazhmash 158 Energoatom 159 Illichivsk Sea Commercial Port 160 Kharkiv State Aviation Enterprise 161 Kharkivoblenergo 162 Khmelnytskoblenergo 163 Kyiv Boryspil 164 Lviv Danylo Halytskyi International Airport 165 Mariupol Sea Commercial Port 166 Mykolayivoblenergo 167 Naftogaz of Ukraine 168 Odesa Commercial Sea Port 169 Odesa Portside Plant 170 Roads of Ukraine 171 State Food and Grain Corporation of Ukraine 172 Sumykhimprom 173 Turboatom 174 Ukrainian Sea Ports Administration 175 Ukrainian State Air Traffic Enterprise 176 Ukrenergo 177 Ukrhydroenergo 178 Ukrposhta 179 Ukrspyrt 180 Ukrzaliznytsia 181 Yuzhny Sea Trade Port 182 Zaporizhyaoblenergo 183 METHODOLOGY NOTE 184 SOE PORTFOLIO 186 ABBREVIATIONS AND DEFINITIONS 191 002 UKRAINE’S TOP-100 STATE-OWNED ENTERPRISES › FULL YEAR 2014 Foreword This is the second report on Ukraine’s 100 largest state-owned enterprises (SOEs) dis- closing their results for the full 2014. Public disclosure of such information is part of the Ukrainian government’s commitment to bring transparency to the SOE sector and communicate the change to the Ukrainian people, local and international investors, and various other stakeholders who want to see Ukraine succeed on the reform path. -

Office of the United Nations High Commissioner for Human Rights
Office of the United Nations High Commissioner for Human Rights Report on the human rights situation in Ukraine 15 April 2014 TABLE OF CONTENTS Page I. EXECUTIVE SUMMARY …………………………………………………. 3 I. INTRODUCTION ……………………………………………………. 6 A. Context B. Universal and regional human rights instruments ratified by Ukraine C. UN human rights response D. Methodology III. UNDERLYING HUMAN RIGHTS VIOLATIONS ……………………… … 10 A. Corruption and violations of economic and social rights B. Lack of accountability for human rights violations and weak rule of law institutions IV. HUMAN RIGHTS VIOLATIONS RELATED TO THE MAIDAN PROTESTS ……………………………………………………… 13 A. Violations of the right to freedom of assembly B. Excessive use of force, killings, disappearances, torture and ill-treatment C. Accountability and national investigations V. CURRENT OVERALL HUMAN RIGHTS CHALLENGES ……………… 15 A. Protection of minority rights B. Freedom of expression, peaceful assembly and the right to information C. Incitement to hatred, discrimination or violence D. Lustration, judicial and security sector reforms VI. SPECIFIC HUMAN RIGHTS CHALLENGES IN CRIMEA …………….. 20 VII. CONCLUSIONS AND RECOMMENDATIONS ………………………….. 22 A. Conclusions B. Recommendations for immediate action C. Long-term recommendations Annex I: Concept Note for the deployment of the UN human rights monitoring mission in Ukraine 2 | P a g e I. EXECUTIVE SUMMARY 1. During March 2014 ASG Ivan Šimonović visited Ukraine twice, and travelled to Bakhchisaray, Kyiv, Kharkiv, Lviv, Sevastopol and Simferopol, where he met with national and local authorities, Ombudspersons, civil society and other representatives, and victims of alleged human rights abuses. This report is based on his findings, also drawing on the work of the newly established United Nations Human Rights Monitoring Mission in Ukraine (HRMMU). -

OLEKSANDR POLONYK (SASHA), Associate
OLEKSANDR POLONYK (SASHA), Associate Oleksandr Polonyk is an associate in the Corporate Department. He focuses on public and private M&A deals, securities offerings and other corporate transactions. Before joining Jenner & Block, Mr. Polonyk practiced law at a top-tier law firm in Ukraine. He represented clients in M&A transactions, IPOs, Eurobond issuances, as well as debt restructurings. He has substantial experience advising clients in the banking, IT, energy, and agriculture sectors. IFLR (Energy and Infrastructure 2016) commended him for his “invaluable can-do attitude.” Mr. Polonyk is fluent in Russian and Ukrainian. Mr. Polonyk’s representative experience in M&A includes the following: OLEKSANDR POLONYK Advised General Dynamics Corporation on its $9.7 billion acquisition of (SASHA) CSRA Inc. Associate Advised Snyder’s-Lance, Inc. on its $6.1 billion sale to Campbell Soup NEW YORK Company Office: 212 891-1684 Email: [email protected] Advised a lead investor on its investment in a developer and operator of greenhouse farms located near major metropolitan areas PRACTICE GROUPS Corporate Advised Altran Technologies SA, an engineering and technology consulting Corporate Finance Mergers & Acquisitions company, on the acquisition of Lohika Systems Inc, a software engineering Securities services firm EDUCATION Advised a Fortune Global 500 company on the acquisition of renewable New York University School of Law, LLM in Corporate Law, 2017 assets in Ukraine Utrecht University School of Law, LLM in Advised on the EUR122 million acquisition -
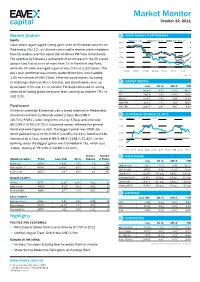
EAVEX Daily ENG Oct 13.Indd
Market Monitor October 13, 2011 Market Update STOCK MARKET PERFORMANCE Equity UX Index RTS Index* WIG 20 Index* 2,500 Local stocks again lagged strong gains seen on European bourses on 2,250 Wednesday (Oct 12), as Ukraine continued to receive a dressingdown from EU leaders over the conviction of former PM Yulia Tymoshenko. 2,000 The approval by Slovakia’s parliament of an increase in the EU’s bank 1,750 bailout fund fueled a rise of more than 2% in Frankfurt and Paris, 1,500 while the UX index managed a gain of only 0.5% to 1,327 points. The 1,250 11-Jul 25-Jul 8-Aug 22-Aug 5-Sep 19-Sep 3-Oct day’s best performer was volume leader Motor Sich, which added * rebased 1.5% on turnover of UAH 13mn. Other top liquid names, including CentrEnergo, Alchevsk Steel, Azovstal, and Ukrsotsbank, were up MARKET INDEXES by between 0.5% and 1%. In London, Ferrexpo continued its strong Last 1D ch 1M ch YTD rebound on fading global recession fears, picking up another 7.9% to UX 1326.4 0.7% 12.7% 45.7% RTS 1407.8 3.9% 13.4% 20.5% USD 3.30. WIG20 2316.7 2.4% 3.0% 15.6% MSCI EM 923.2 1.5% 7.0% 19.8% Fixed Income S&P 500 1207.3 1.0% 4.6% 4.0% Ukrainian sovereign Eurobonds saw a broad rebound on Wednesday. Ukrainian midterm Eurobonds added 2.0p.p. 84.0/88.0 UX INTRADAY OCTOBER 12, 2011 (10.70%/9.58%), while longterms rose by 4.0p.p.