ICB Presentationfinal.Pptx
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Download Volume 13 (PDF)
Volume 13, Summer 2019 Copyright Ó 2019 Assistive Technology Industry Association ISSN 1938-7261 Assistive Technology Outcomes and Benefits | i The Role of Research in Influencing Assistive Technology Products, Policy, and Practice Volume 13, Summer 2019 Assistive Technology Outcomes and Benefits The Role of Research in Influencing Assistive Technology Products, Policy, and Practice Volume 13, Summer 2019 Editor in Chief Focused Issue Editor Jennifer L. Flagg Kathleen M. Murphy Center on KT4TT, University oF BuFFalo American Institutes For Research Publication Managers Associate Editors Victoria A. Holder Kate Herndon Tools For LiFe, Georgia Institute oF Technology American Printing House For the Blind Elizabeth A. Persaud Carolyn P. Phillips Tools For LiFe, Georgia Insitute oF Technology Tools For LiFe, Georgia Institute oF Technology Caroline Van Howe Copy Editor Assistive Technology Industry Association Beverly Nau Assistive Technology Outcomes and Benefits (ATOB) is a collaborative peer-reviewed publication of the Assistive Technology Industry Association (ATIA). Editing policies oF this issue are based on the Publication Manual oF the American Psychological Association (6th edition) and may be Found online at www.atia.org/atob/editorialpolicy. The content does not reflect the position or policy of ATIA and no official endorsement should be inferred. Editorial Board Members and Managing Editors David Banes Beth Poss Managing Director, David Banes Access and Administrator, Montgomery County Schools, Inclusion Services Maryland Russell T. Cross Ben SatterField Director of Clinical Operations, Prentke Romich Research Consultant, Center for AT Company Excellence, Tools For LiFe at Georgia Institute oF Technology Anya Evmenova Associate Professor, Division of Special Judith Schoonover Education and disAbility Research, George Occupational Therapist and AT Consultant, Mason University Sterling, Virginia American Occupational Therapy Association, Lori Geist Inc. -

A Middleware Framework for Application-Aware and User-Specific Energy Optimization in Smart Mobile Devices
Pervasive and Mobile Computing 20 (2015) 47–63 Contents lists available at ScienceDirect Pervasive and Mobile Computing journal homepage: www.elsevier.com/locate/pmc A middleware framework for application-aware and user-specific energy optimization in smart mobile devices Sudeep Pasricha a,∗, Brad K. Donohoo b, Chris Ohlsen c a Colorado State University, Fort Collins, CO 80523, USA b U.S. Department of the Air Force, Roy, UT 84067, UT 84067, USA c Woodward, Inc., Fort Collins, CO 80525, USA article info a b s t r a c t Article history: Mobile battery-operated devices are becoming an essential instrument for business, com- Received 5 August 2014 munication, and social interaction. In addition to the demand for an acceptable level of per- Received in revised form 22 December 2014 formance and a comprehensive set of features, users often desire extended battery lifetime. Accepted 7 January 2015 In fact, limited battery lifetime is one of the biggest obstacles facing the current utility and Available online 14 January 2015 future growth of increasingly sophisticated ``smart'' mobile devices. This paper proposes a novel application-aware and user-interaction aware energy optimization middleware Keywords: framework (AURA) for pervasive mobile devices. AURA optimizes CPU and screen back- Energy optimization Smart mobile systems light energy consumption while maintaining a minimum acceptable level of performance. Pervasive computing The proposed framework employs a novel Bayesian application classifier and management Machine learning strategies based on Markov Decision Processes and Q-Learning to achieve energy savings. Middleware Real-world user evaluation studies on Google Android based HTC Dream and Google Nexus One smartphones running the AURA framework demonstrate promising results, with up to 29% energy savings compared to the baseline device manager, and up to 5×savings over prior work on CPU and backlight energy co-optimization. -

February 2010 Admob Mobile Metrics Report
AdMob Mobile Metrics Report AdMob serves ads for more than 15,000 mobile Web sites and applications around the world. AdMob stores and analyzes the data from every ad request, impression, and click and uses this to optimize ad matching in its network. This monthly report offers a snapshot of its data to provide insight into trends in the mobile ecosystem. February 2010 Find archived reports and sign up for future report notifications at metrics.admob.com. AdMob Mobile Metrics Report February 2010 New and Noteworthy For this month's report, we separate the traffic in our network into three categories – smartphones, feature phones, and mobile Internet devices – to examine the growth rates of each over the past year and look at the traffic share of smartphone operating systems and manufacturers of feature phones. * In February 2010, smartphones accounted for 48% of AdMob’s worldwide traffic, up from 35% in February 2009. The strong growth of iPhone and Android traffic, fueled by heavy application usage, was primarily responsible for the increase. In absolute terms, smartphone traffic increased 193% over the last year. * Feature phones declined from 58% to 35% of AdMob's total traffic as users began switching to smartphones. Although the share of traffic from feature phones as a category declined, in absolute terms traffic grew 31% year-over-year. * The mobile Internet devices category experienced the strongest growth of the three, increasing to account for 17% of traffic in AdMob’s network in February 2010. The iPod touch is responsible for 93% of this traffic; other devices include the Sony PSP and Nintendo DSi. -

Professional Skills in Computer Science Lecture 3: Historical Aspects of Computing
Professional Skills in Computer Science Lecture 3: Historical Aspects of Computing Ullrich Hustadt Department of Computer Science School of Electrical Engineering, Electronics, and Computer Science University of Liverpool Ullrich Hustadt COMP110 Professional Skills in Computer Science L3 { 1 Further milestones The Future Contents 1 Further milestones 2 The Future Fundamental questions Model-View-Controller Relevant learning outcome: 1 Ability to describe and discuss economic, historic, organisational, research, and social aspects of computing as a discipline and computing in practice; Ullrich Hustadt COMP110 Professional Skills in Computer Science L3 { 2 Further milestones The Future What have computers been used for? (Summary) • 1600 { now: Calculation Manipulation of numbers • 1960 { now: Information Processing Manipulation of numbers, text, images, audio, video • 1960 { now: Cognition (Reasoning) Manipulation of knowledge via reasoning / inference • 1970 { now: Interaction Allowing people to communicate, cooperate, compete • 1970 { now: Automation Computer-controlled machines and robots Hypotheses: • The wave of innovation in the 60s and 70s is due to the increased availability of computing resources to more and more researchers • Leadership is mostly due to early exposure to state-of-the-art systems and due to hard work Ullrich Hustadt COMP110 Professional Skills in Computer Science L3 { 3 Further milestones The Future What have computers been used for? What important milestones in the development and use of computers were not covered -

Introduction to Smartphones Beginners Guide TOPIC INTRODUCTION to SMARTPHONES
Tech Savvy Seniors Introduction to Smartphones Beginners Guide TOPIC INTRODUCTION TO SMARTPHONES OVERVIEW Phones used to be all about making calls, but now your mobile can do so much more. The range of new touchscreen smartphones allows you to access the internet, use social media, get live news updates, play music and video, and much more. They almost universally use touchscreens for control, however, which can be a challenge for people new to the technology. WHO IS THIS Maybe you’ve never owned a mobile and are curious WORKSHOP FOR? about why you’d choose a smartphone. Perhaps you want a mobile phone that does more than your current keypad-style handset, or are looking to learn more about the smartphone you already own. This workshop has something to satisfy each of you. WHAT YOU’LL An internet-connected smartphone; either your NEED own or supplied by the workshop organisers. You may need to share a smartphone with others in the workshop. An existing Apple account (or Apple ID), for downloading apps to an iPhone smartphone. An existing Google account (or Google ID), for downloading apps to an Android smartphone. WHAT YOU’LL In this workshop, you will learn the basics of how LEARN to navigate your way around a smartphone with a touchscreen. You will learn how to turn the phone on and off, make and receive calls, add a contact and look up a contact, and change the volume on the phone. You will also learn briefly about apps, what they are, how to download them, and the costs associated with them. -

Android Vs Ios
Android vs iOS By Mohammad Daraghmeh Jack DeGonzaque AGENDA ● Android ○ History ● Samsung S6 ○ System Architecture ○ Processor ○ Performance Metrics ● iOS ○ History ● iPhone 6 ○ System Architecture ○ Processor ○ Performance Metrics ● Samsung S6 vs iPhone 6 Android Android History ● The Android OS was created mainly by three amazing people Andy Rubin, Rich Miner, Nick Sears, and Chris White. ○ Initial development for the OS was to create an operating system for digital cameras and PC integration. ○ After gauging the size of the market for such a product, Rubin and his colleagues decided to target the booming smartphone market. ● In 2005, Google also wanted to venture into the smartphone market and did so by acquiring Android Inc. ○ The primary directive was to develop technologies that are developed and distributed at a significantly lower cost to make it more accessible. ○ In 2008, the first Android running smartphone, the HTC Dream, was released. Android History (Cont.) ● The Android operating system has become one of the most popular operating systems. ○ According to research firm, called Gartner, more than a billion Android devices were sold in 2014, which is roughly five times more than Apple iOS devices sold and three times more Windows machines sold. ● Their attribute to success stems from the fact that Google does not charge for Android, and that most phone manufacturers are making cost effective phones, which results in affordable smartphones and internet services at low costs for consumers to enjoy. SAMSUNG GALAXY S6 System Architecture ● Samsung S6 uses the Exynos 7420 processor, which is developed by Samsung as well. ○ The Exynos 7420 is a 78 mm^2 SoC comprised of 8 cores connected to two L2 cache instances. -

The Ways Young Adults Access Digital Information Cydney Lauren Palmer Louisiana State University and Agricultural and Mechanical College, [email protected]
Louisiana State University LSU Digital Commons LSU Master's Theses Graduate School 2011 There's an app for that: the ways young adults access digital information Cydney Lauren Palmer Louisiana State University and Agricultural and Mechanical College, [email protected] Follow this and additional works at: https://digitalcommons.lsu.edu/gradschool_theses Part of the Mass Communication Commons Recommended Citation Palmer, Cydney Lauren, "There's an app for that: the ways young adults access digital information" (2011). LSU Master's Theses. 711. https://digitalcommons.lsu.edu/gradschool_theses/711 This Thesis is brought to you for free and open access by the Graduate School at LSU Digital Commons. It has been accepted for inclusion in LSU Master's Theses by an authorized graduate school editor of LSU Digital Commons. For more information, please contact [email protected]. THERE’S AN APP FOR THAT: THE WAYS YOUNG ADULTS ACCESS DIGITAL INFORMATION A Thesis Submitted to the Graduate Faculty of the Louisiana State University and Agricultural and Mechanical College in partial fulfillment of the requirements for the degree of Master in Mass Communication in The Manship School of Mass Communication by Cydney Lauren Palmer B.A., Louisiana State University, 2008 December 2011 ACKOWLEDGMENTS First, I would like to thank my parents, Allan and Karin Palmer, for their support and encouragement while pursuing my master’s degree. I would also like to thank Dr. Yongick Jeong for his continuous guidance and support throughout the tedious development of this academic research project. Finally, I would like to thank my additional thesis committee members, Dr. Lance Porter and Dr. -

Running IBM Websphere Application Server on System P and AIX: Optimization and Best Practices
Front cover Running IBM WebSphere Application Server on System p and AIX: Optimization and Best Practices System p and AIX configuration strategies for WebSphere Application Server How JVM runtime and WebSphere Application Server interact with AIX Implementation scenarios Lutz Werner Denefleh Anderson de Sousa Ribeiro Dias Simon Kapadia Monty Poppe Colin Renouf Kwan-Ming Wan ibm.com/redbooks International Technical Support Organization Running IBM WebSphere Application Server on System p and AIX: Optimizaton and Best Practices September 2008 SG24-7347-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition September 2008 This edition applies to IBM WebSphere Application Server Version 6.1, IBM AIX Version 5.3, and IBM AIX Version 6.1. © Copyright International Business Machines Corporation 2008. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . x Preface . xi The team that wrote this book . xi Acknowledgements . xiii Become a published author . xiii Comments welcome. xiv Chapter 1. Introduction to running WebSphere Application Server on System p and AIX . 1 1.1 The whole system view: WebSphere, JVM, AIX, and System p . 2 1.1.1 Points of view . 2 1.1.2 A holistic system approach . 3 1.2 System layers and points of view . 3 1.2.1 Points of view and terminology . 4 1.3 The remainder of this book . 5 Chapter 2. WebSphere on System p and AIX 5 strategies . 7 2.1 Scalability considerations . -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

Android Software Platform Development at Fujitsu
Android Software Platform Development at Fujitsu Makoto Honda Makoto Kobayashi Masahiko Nagumo Yasuhiro Kawakatsu Smartphones using the Android platform first appeared on the market in October 2008. They have since overtaken Apple’s iPhone—the first entry in the smartphone market—in number of units shipped and have helped to bring about major changes in the way that mobile phones are used. Android was developed and is distributed as open source software that a device maker integrates into its own hardware after adding original software technologies. The Android platform evolves in short cycles on the basis of software and hardware developments as the network infrastructure continues to expand in the form of WiMAX and LTE and as usage scenarios and services become increasingly diverse. Fujitsu has been developing Android smartphones with compelling functions and enhanced convenience since December 2010, when it released the REGZA Phone T-01C featuring a water-resistant enclosure, one-seg support, and FeliCa contactless IC card and infrared-communication functions. This paper describes Fujitsu’s approach to smartphone development, focusing on memory management and current-con- sumption management as important elements in the system design of the Android software platform, diverse manner modes for enhancing user convenience, high-picture-quality technol- ogy achieved by using the Mobile REGZA Engine, and audio-visual device-linking technology based on DLNA standards. 1. Introduction and Internet services, the smartphone market share of November 2007 marked the establishment of the Android devices continued to grow, and in fiscal 2011, Open Handset Alliance (OHA) centered about Google it came to exceed 50%. -

ANALYSIS of AUDIO RECORDINGS MADE USING the VOICE RECORDER APPLICATION on ANDROID PHONES by GINA ANTOINETTE DEANGELIS A.A., Arap
ANALYSIS OF AUDIO RECORDINGS MADE USING THE VOICE RECORDER APPLICATION ON ANDROID PHONES by GINA ANTOINETTE DEANGELIS A.A., Arapahoe Community College, 1999 B.S., University of Colorado Denver, 2001 A thesis submitted to the Faculty of the Graduate School of the University of Colorado in partial fulfillment of the requirements for the degree of Master of Science Recording Arts Program 2020 © 2020 GINA ANTOINETTE DEANGELIS ALL RIGHTS RESERVED ii This thesis for the Master of Science degree by Gina Antoinette DeAngelis has been approved for the Recording Arts Program by Catalin Grigoras, Chair Jeff M. Smith Marcus Rogers Date: May 16, 2020 iii DeAngelis, Gina Antoinette (M.S., Recording Arts) Analysis of Audio Recordings Made Using the Voice Recorder Application on Android Phones Thesis directed by Associate Professor Catalin Grigoras ABSTRACT Android is one of the two main operating systems for mobile phones and includes an application for voice recording. Since extensive research has been completed on the "Voice Memos" application for iOS, there remains research to be completed on the default application for the Android OS. This thesis explores the user interface for four different Android phones with four different voice recording application versions. Features, limitations, editing capabilities, file formats and atom structure for each phone are discussed. A testing protocol was created and utilized for the creation of the test recordings. The analysis of those recordings explored authenticity, detected editing and discovered consistencies and inconsistencies between the recordings for each phone. The form and content of this abstract are approved. I recommend its publication. Approved: Catalin Grigoras iv DEDICATION This is dedicated to my parents and my boys who supported me every step of the way. -
Android (Operating System) 1 Android (Operating System)
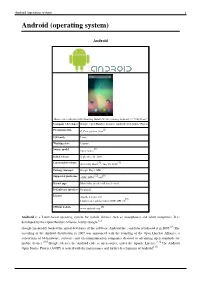
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google.