Internet Safety for Parents, Guardians, and Communities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Excesss Karaoke Master by Artist
XS Master by ARTIST Artist Song Title Artist Song Title (hed) Planet Earth Bartender TOOTIMETOOTIMETOOTIM ? & The Mysterians 96 Tears E 10 Years Beautiful UGH! Wasteland 1999 Man United Squad Lift It High (All About 10,000 Maniacs Candy Everybody Wants Belief) More Than This 2 Chainz Bigger Than You (feat. Drake & Quavo) [clean] Trouble Me I'm Different 100 Proof Aged In Soul Somebody's Been Sleeping I'm Different (explicit) 10cc Donna 2 Chainz & Chris Brown Countdown Dreadlock Holiday 2 Chainz & Kendrick Fuckin' Problems I'm Mandy Fly Me Lamar I'm Not In Love 2 Chainz & Pharrell Feds Watching (explicit) Rubber Bullets 2 Chainz feat Drake No Lie (explicit) Things We Do For Love, 2 Chainz feat Kanye West Birthday Song (explicit) The 2 Evisa Oh La La La Wall Street Shuffle 2 Live Crew Do Wah Diddy Diddy 112 Dance With Me Me So Horny It's Over Now We Want Some Pussy Peaches & Cream 2 Pac California Love U Already Know Changes 112 feat Mase Puff Daddy Only You & Notorious B.I.G. Dear Mama 12 Gauge Dunkie Butt I Get Around 12 Stones We Are One Thugz Mansion 1910 Fruitgum Co. Simon Says Until The End Of Time 1975, The Chocolate 2 Pistols & Ray J You Know Me City, The 2 Pistols & T-Pain & Tay She Got It Dizm Girls (clean) 2 Unlimited No Limits If You're Too Shy (Let Me Know) 20 Fingers Short Dick Man If You're Too Shy (Let Me 21 Savage & Offset &Metro Ghostface Killers Know) Boomin & Travis Scott It's Not Living (If It's Not 21st Century Girls 21st Century Girls With You 2am Club Too Fucked Up To Call It's Not Living (If It's Not 2AM Club Not -

Most Requested Songs of 2015
Top 200 Most Requested Songs Based on millions of requests made through the DJ Intelligence® music request system at weddings & parties in 2015 RANK ARTIST SONG 1 Ronson, Mark Feat. Bruno Mars Uptown Funk 2 Journey Don't Stop Believin' 3 Cupid Cupid Shuffle 4 Swift, Taylor Shake It Off 5 Walk The Moon Shut Up And Dance 6 Williams, Pharrell Happy 7 Black Eyed Peas I Gotta Feeling 8 Diamond, Neil Sweet Caroline (Good Times Never Seemed So Good) 9 Sheeran, Ed Thinking Out Loud 10 V.I.C. Wobble 11 Houston, Whitney I Wanna Dance With Somebody (Who Loves Me) 12 AC/DC You Shook Me All Night Long 13 Bon Jovi Livin' On A Prayer 14 DJ Casper Cha Cha Slide 15 Mars, Bruno Marry You 16 Maroon 5 Sugar 17 Morrison, Van Brown Eyed Girl 18 Usher Feat. Ludacris & Lil' Jon Yeah 19 Legend, John All Of Me 20 B-52's Love Shack 21 Isley Brothers Shout 22 DJ Snake Feat. Lil Jon Turn Down For What 23 Outkast Hey Ya! 24 Brooks, Garth Friends In Low Places 25 Beatles Twist And Shout 26 Pitbull Feat. Ke$Ha Timber 27 Def Leppard Pour Some Sugar On Me 28 Jackson, Michael Billie Jean 29 Sir Mix-A-Lot Baby Got Back 30 Trainor, Meghan All About That Bass 31 Beyonce Single Ladies (Put A Ring On It) 32 Loggins, Kenny Footloose 33 Rihanna Feat. Calvin Harris We Found Love 34 Lynyrd Skynyrd Sweet Home Alabama 35 Bryan, Luke Country Girl (Shake It For Me) 36 Sinatra, Frank The Way You Look Tonight 37 Lmfao Feat. -

Illustration and the Visual Imagination in Modern Japanese Literature By
Eyes of the Heart: Illustration and the Visual Imagination in Modern Japanese Literature By Pedro Thiago Ramos Bassoe A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor in Philosophy in Japanese Literature in the Graduate Division of the University of California, Berkeley Committee in Charge: Professor Daniel O’Neill, Chair Professor Alan Tansman Professor Beate Fricke Summer 2018 © 2018 Pedro Thiago Ramos Bassoe All Rights Reserved Abstract Eyes of the Heart: Illustration and the Visual Imagination in Modern Japanese Literature by Pedro Thiago Ramos Bassoe Doctor of Philosophy in Japanese Literature University of California, Berkeley Professor Daniel O’Neill, Chair My dissertation investigates the role of images in shaping literary production in Japan from the 1880’s to the 1930’s as writers negotiated shifting relationships of text and image in the literary and visual arts. Throughout the Edo period (1603-1868), works of fiction were liberally illustrated with woodblock printed images, which, especially towards the mid-19th century, had become an essential component of most popular literature in Japan. With the opening of Japan’s borders in the Meiji period (1868-1912), writers who had grown up reading illustrated fiction were exposed to foreign works of literature that largely eschewed the use of illustration as a medium for storytelling, in turn leading them to reevaluate the role of image in their own literary tradition. As authors endeavored to produce a purely text-based form of fiction, modeled in part on the European novel, they began to reject the inclusion of images in their own work. -
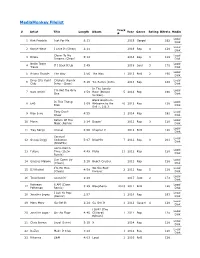
Mediamonkey Filelist
MediaMonkey Filelist Track # Artist Title Length Album Year Genre Rating Bitrate Media # Local 1 Kirk Franklin Just For Me 5:11 2019 Gospel 182 Disk Local 2 Kanye West I Love It (Clean) 2:11 2019 Rap 4 128 Disk Closer To My Local 3 Drake 5:14 2014 Rap 3 128 Dreams (Clean) Disk Nellie Tager Local 4 If I Back It Up 3:49 2018 Soul 3 172 Travis Disk Local 5 Ariana Grande The Way 3:56 The Way 1 2013 RnB 2 190 Disk Drop City Yacht Crickets (Remix Local 6 5:16 T.I. Remix (Intro 2013 Rap 128 Club Intro - Clean) Disk In The Lonely I'm Not the Only Local 7 Sam Smith 3:59 Hour (Deluxe 5 2014 Pop 190 One Disk Version) Block Brochure: In This Thang Local 8 E40 3:09 Welcome to the 16 2012 Rap 128 Breh Disk Soil 1, 2 & 3 They Don't Local 9 Rico Love 4:55 1 2014 Rap 182 Know Disk Return Of The Local 10 Mann 3:34 Buzzin' 2011 Rap 3 128 Macc (Remix) Disk Local 11 Trey Songz Unusal 4:00 Chapter V 2012 RnB 128 Disk Sensual Local 12 Snoop Dogg Seduction 5:07 BlissMix 7 2012 Rap 0 201 Disk (BlissMix) Same Damn Local 13 Future Time (Clean 4:49 Pluto 11 2012 Rap 128 Disk Remix) Sun Come Up Local 14 Glasses Malone 3:20 Beach Cruiser 2011 Rap 128 (Clean) Disk I'm On One We the Best Local 15 DJ Khaled 4:59 2 2011 Rap 5 128 (Clean) Forever Disk Local 16 Tessellated Searchin' 2:29 2017 Jazz 2 173 Disk Rahsaan 6 AM (Clean Local 17 3:29 Bleuphoria 2813 2011 RnB 128 Patterson Remix) Disk I Luh Ya Papi Local 18 Jennifer Lopez 2:57 1 2014 Rap 193 (Remix) Disk Local 19 Mary Mary Go Get It 2:24 Go Get It 1 2012 Gospel 4 128 Disk LOVE? [The Local 20 Jennifer Lopez On the -

Promo Only Country Radiodate
URBAN RADIO ARTIST 05 01 17 OPEN this on your computer. Place your cursor in the “X” Colum. Use the down arrow to move down the cell and place an “X” infront of the song you want played. Forward the file by attachment to [email protected] or F 713-661-2218 X TRK TITLE ARTIST DATE LENGTH BPM STYLE 16 Chill Bill $tone, Rob f./ J. Davi$ & Spooks 11/1/2016 2:58 54 Hip-Hop 16 Chill Bill $tone, Rob f./ J. Davi$ & Spooks 11/1/2016 2:58 54 Hip-Hop JuJu On That Beat (TZ 7 Anthem) & zayion mccall Zay Hilfigerrr 12/1/2016 2:23 80 Hip-Hop JuJu On That Beat (TZ 7 Anthem) & zayion mccall Zay Hilfigerrr 12/1/2016 2:23 80 Hip-Hop 15 Im The Man (Fifty) 50 Cent f./ Sonny Digital 4/1/2016 3:53 98 Hip-Hop 15 Im The Man (Fifty) 50 Cent f./ Sonny Digital 4/1/2016 3:53 98 Hip-Hop 15 Used 2 2 Chainz 13-Nov 3:45 89 Urban 7 Watch Out 2 Chainz 11/1/2015 3:23 65 Hip-Hop 13 I\'m Different 2 Chainz 13-Jan 3:25 97 Hip Hop 12 Riot 2 Chainz 12-May 2:44 65 Hip Hop 22 Gotta Lotta 2 Chainz & Lil Wayne 6/1/2016 3:22 82 Hip-Hop 22 Gotta Lotta 2 Chainz & Lil Wayne 6/1/2016 3:22 82 Hip-Hop 15 Big Amount 2 Chainz f./ Drake 10/1/2016 3:06 67 Hip-Hop 15 Big Amount 2 Chainz f./ Drake 10/1/2016 3:06 67 Hip-Hop 9 Good Drank 2 Chainz f./ Gucci Mane & Quavo 3/1/2017 3:41 66 Hip-Hop 3 No Lie 2 Chainz f./Drake 12-Jul 3:56 65 Urban 9 Netflix 2 Chainz f./Fergie 13-Oct 3:53 62 Rhythm/Urban 2 Feds Watching 2 Chainz f./Pharrell 13-Aug 4:05 70 Rhythm/Urban 15 Milly Rock 2 Milly 2/1/2016 3:39 70 Hip-Hop 15 Milly Rock 2 Milly 2/1/2016 3:39 70 Hip-Hop 10 Milly Rock 2 Milly f./ A$AP -

IN the SUPREME COURT of the STATE of MONTANA Cause No
04/24/2020 IN THE SUPREME COURT OF THE STATE OF MONTANA Case Number: DA 19-0731 Cause No. DA 19-0731 STATE OF MONTANA, Plaintiff and Appellee, v. TRAVIS MICHAEL STAKER, Defendant and Appellant. BRIEF OF APPELLANT On Appeal from the Montana Eighteenth Judicial District Court The Honorable Rienne McElyea, District Judge, Presiding APPEARANCES: MARK J. LUEBECK TIMOTHY C. FOX Angel, Coil & Bartlett Montana Attorney General 125 W. Mendenhall, Suite 201 C. MARK FOWLER Bozeman, Montana 59715 Bureau Chief - Appellate 406.586.1926 215 N. Sanders [email protected] Helena, MT 59620-1401 Attorney for Defendant and Attorneys for Plaintiff and Appellant Appellee Continued on Next Page MARTIN D. LAMBERT Gallatin County Attorney BJORN E. BOYER Deputy County Attorney 1709 W. College Bozeman MT 59715 Attorneys for Plaintiff and Appellee TABLE OF CONTENTS TABLE OF CONTENTS…………………………………………………….….i TABLE OF AUTHORITIES…………………………………………………..iii STATEMENT OF THE ISSUES……………………………………………...1 STATEMENT OF THE CASE…………………………………………………1 STATEMENT OF THE FACTS……………………………………………….3 SUMMARY OF THE ARGUMENTS…………………………………………8 STANDARD OF REVIEW…………………………………………………....10 ARGUMENT……………………………………………………………………10 I. Law Enforcement’s Warrantless Investigation Constituted an Illegal Search and Seizure as Mr. Staker had an Actual Subjective Expectation of Privacy in His Text Message Communication and Society Recognizes His Expectation as Objectively Reasonable………………………………………….10 A. Mr. Staker had an actual expectation of privacy in his cell phone text message communications with “Lily.”………………………………………………………..17 B. Society recognizes Mr. Staker’s actual subjective expectation of privacy in his cell phone text message communication as reasonable………..…………………..21 C. The District Court erred in distinguishing text message communication from oral communication on the basis that text messages are “recorded.”…...….……………...32 D. -

An Introduction to the Study of American Military Marching Cadences
University of Massachusetts Amherst ScholarWorks@UMass Amherst Masters Theses Dissertations and Theses July 2015 Sound-off! An Introduction to the Study of American Military Marching Cadences Travis G. Salley University of Massachusetts Amherst Follow this and additional works at: https://scholarworks.umass.edu/masters_theses_2 Part of the Musicology Commons Recommended Citation Salley, Travis G., "Sound-off! An Introduction to the Study of American Military Marching Cadences" (2015). Masters Theses. 243. https://doi.org/10.7275/6949713 https://scholarworks.umass.edu/masters_theses_2/243 This Open Access Thesis is brought to you for free and open access by the Dissertations and Theses at ScholarWorks@UMass Amherst. It has been accepted for inclusion in Masters Theses by an authorized administrator of ScholarWorks@UMass Amherst. For more information, please contact [email protected]. SOUND-OFF! AN INTRODUCTION TO THE STUDY OF AMERICAN MILITARY MARCHING CADENCES A Thesis Presented by TRAVIS G. SALLEY Submitted to the Graduate School of the University of Massachusetts-Amherst in partial fulfillment Of the requirements for the degree of MASTER OF MUSIC May 2015 Department of Music and Dance © Copyright by Travis G. Salley 2015 All Rights Reserved SOUND-OFF! AN INTRODUCTION TO THE STUDY OF AMERICAN MILITARY MARCHING CADENCES A Thesis Presented by TRAVIS G. SALLEY Approved as to style and content by: _____________________________________ Marianna Ritchey, Chair _______________________________________ Ernie May, Member _______________________________ Jeff Cox, Department Head Department of Music & Dance DEDICATION To Rachel. ACKNOWLEDGEMENTS I would first like to thank my advisor, Dr. Marianna Ritchey. I will be forever grateful for her kindness, guidance, and patience in helping me create this project. -

University of Edinburgh Postgraduate Journal of Culture and the Arts Issue 26 | Spring 2018
University of Edinburgh Postgraduate Journal of Culture and the Arts Issue 26 | Spring 2018 Title The Real Deal: Hip-hop Mixtape Artwork and Black Masculinity Author Emmett Robinson Smith Publication FORUM: University of Edinburgh Postgraduate Journal of Culture & the Arts Issue Number 26 Issue Date Spring 2018 Publication Date 11/06/2018 Editors Maria Elena Torres-Quevedo and Valentina P. Aparicio FORUM claims non-exclusive rights to reproduce this article electronically (in full or in part) and to publish this work in any such media current or later developed. The author retains all rights, including the right to be identified as the author wherever and whenever this article is published, and the right to use all or part of the article and abstracts, with or without revision or modification in compilations or other publications. Any latter publication shall recognise FORUM as the original publisher. The Real Deal: Hip-hop Mixtape Artwork and Black Masculinity Emmett Robinson Smith University of Western Ontario Despite hip-hop’s status as a means of resistance to myriad systems of institutionalized racism, oppression, and poverty, its rise in mainstream popularity has caused a dramatic increase in its corporate monetization. This causes a transfer of control from the artist to the record label, at times jeopardizing hip-hop’s fundamental principles of rebellion, resistance, and risk. An alternative mode of expression, however – the mixtape – puts power back into the hands of hip-hop artists, becoming a crucial vessel for unmitigated artistic expression and meaning. One of the most significant and immediately striking aspects of the mixtape is the cover art. -

Far Beyond the Hype Rap’S Best Artists of Today
6 LIFE&ARTS Wednesday, September 11, 2019 @TheEtCetera The Et Cetera far beyond the hype Rap’s best artists of today Who comes to mind when discussing the top hip-hop art- ists ever? Of course the usual suspects like Tupac and Biggie will be in this discussion. But other all-time greats like Rakim, DMX and OutKast could also be mentioned. I think everyone’s preferences would look a little different. Recently, a hip-hop podcast called “The Brew” tweeted out a list of the “Top 50 Greatest Rappers of All-Time”. The list that resulted in a Twitter uproar of angry fans and members of the music industry. The commenters had several big complaints. For one, no female artists were listed. One-hit wonder and now outspoken hip-hop critic Joe Budden was listed at No. 3. And a number of highly regarded top artists were either ranked horribly or absent from the list altogether. I agree that this list included a truly ridiculous sequence of artists. Upon seeing the list for the first time, I honestly thought it was a joke or a troll. 4. Travis Scott So I decided to create my own Top 10 rankings while ac- Best Song: Pick Up the Phone (featuring Quavo & knowledging that, because I’m 18 years old, my list caters more to the present-day era of rap. So here’s my ranking of todays Young Thug) greatest artists.. 2. Kendrick Lamar Best Album: Astroworld Best Song: B**** Don’t Kill My Vibe Best Album: Good Kid, M.A.A.D City Imagine this. -

BTS' 'Butter' on a Roll, Spends Second Week at No. 1 on Billboard Hot
Bulletin YOUR DAILY ENTERTAINMENT NEWS UPDATE JUNE 7, 2021 Page 1 of 41 INSIDE BTS’ ‘Butter’ on a Roll, • Taylor Swift’s Spends Second Week at No. 1 ‘Evermore’ Returns to No. 1 on Billboard 200 Chart on Billboard Hot 100 • Revealed: BY GARY TRUST Billboard’s 2021 Indie Power Players TS’ “Butter” adds a second week at No. 1 on Sales chart, drops 4-10 on Streaming Songs and rises • Bill Ackman’s UMG the Billboard Hot 100 songs chart, a week 39-32 on Radio Songs. Play: A Bad Deal or after it soared in at the summit, becoming First two weeks at No. 1: “Butter” is the 23rd title Just Too Confusing the South Korean superstar group’s fourth to debut at No. 1 on the Hot 100 and post a second for Investors? Bleader on the list. consecutive week on top, among 54 total No. 1 ar- • Apple Music The song again fends off Olivia Rodrigo’s “Good 4 rivals, making for a 43% second-week success rate. Releases Spatial U,” which holds at No. 2 on the Hot 100, two weeks It’s the third among seven such songs this year, after Audio and Lossless after it launched at No. 1. Olivia Rodrigo’s “Drivers License” spent its first eight Streaming The Hot 100 blends all-genre U.S. streaming (of- weeks at No. 1 (encompassing its entire reign) and • How Premier’s ficial audio and official video), radio airplay and sales Polo G’s “Rapstar” ruled in its first two frames (also Josh Deutsch Is data. -
Year-End Edition 2016
® YEAR-END EDITION 2 01 6 REPUBLIC #1 FOR THIRD STRAIGHT YEAR RCA Runner Up; Columbia Moves 5-3; Def Jam, 9-4; Interscope 5th REPUBLIC continues its reign as the #1 overall label in Mediabase chart share for a third straight year. The 2016 chart year is based on the time period from November 15, 2015 through November 12, 2016. Of the 10 Mediabase formats that comprise overall rankings, Republic landed the #1 spot at four formats: Top 40, Rhythmic, Hot AC and AC. Republic had a total chart share of 17.9%, while scoring over a 20% share at Top 40 (23.7%), Rhythmic (20.2%), and AC (20.2%). OTHER HIGHLIGHTS FOR REPUBLIC THIS YEAR: - The label’s total spins for the year across all formats was 7,539,293 – the second highest total ever – only behind the 9.3 million they had in their record setting 2015. - Over half of the Republic spins came at the Top 40 format, where they scored 3,834,134, over 1.6 million spins ahead of the next closest competitor. - Republic had 1,119,628 spins at Rhythmic and 1,117,379 at Hot AC, with both of those joining the million spin club. - For the second consecutive year, Republic nabbed the top slot honors at Top 40, Rhythmic and AC. - Republic was #3 Urban, #5 at Active Rock, #6 at Urban AC , #7 at Alternative, and #8 at Triple A. - Four of the top 10 artists at Top 40 belonged to Republic with Drake (#4), The Weeknd (#7), Shawn Mendes (#8), and Ariana Grande (#9). -

Various Artists. the Best of Anna Records Vol. 1 1 Sheet
1. Get In Line 2. Shoot Em Up 3. Shine 4. Ruga Rell 5. #1 Movement feat. 40 Cal 6. Young Black & Strapped feat. 40 Cal 7. Damn I'm Cool 8. One Eight Seven 9. Where Ya At? feat. Young Buck 10. If I Die 11. Hardest (Remix) 12. I'm So Special 13. The Ruga Show 14. D.W.S. Hell Rell is back and you’ve got a choice, Get In Line or Get Lined Up. Line up and you’ll get a fresh view from the street with brand new cuts from one of New York’s hottest talents on the mic. Rell’s tougher than Kevlar word play is found throughout from the title track “Get Lined Up” right through the albums closing cut “D.W.S”. Rell’s swagger is real, “All of my songs are real, nothing is sugar coated. They are all full of substance.” For Hell Rell this isn’t a game. He’s not fronting. As he puts it, “rapping just comes naturally to me. I don’t write rhymes down on paper and I don’t practice. It just flows off the top of the dome.” The self professed “hardest out, hungriest out” again lives up to that boastful claim by assembling 15 solid snap shots of the view from the streets. Make your choice, Get In Line or Get Lined Up. PRE-ORDERS ON THIS ITEM ARE DUE BY FEB 17th Format: CD — Cat. No: HKE 7783 — Label: Hellz Kitchin’ Ent. — Available: MAR 10th 39 Broad Street, Suite 4, Quincy, MA 02169 Phone: (617) 845-0088 — Fax: (617) 845-0090 www.trafficent.com DISC ONE 1.