BVMS - Deployment Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Teradici Remote Workstation Card Agent for Windows
Teradici PCoIP Remote Workstation Card Agent for Windows Documentation Teradici PCoIP Remote Workstation Card Agent for Windows Documentation This documentation is intended for administrators who are installing the Remote Workstation Card Agent for Windows as part of a Teradici Remote Workstation Card system. It assumes thorough knowledge of conventions and networking concepts, including firewall configuration. Although many agent features and settings can be configured using the Windows user interface, some administrative tasks require use of Windows command line tools. Users should be familiar with both cmd and PowerShell. About the PCoIP Remote Workstation Card Agent for Windows The PCoIP Remote Workstation Card Agent for Windows introduces Teradici brokering to a Teradici Remote Workstation Card deployment, allowing the desktop to be managed by Teradici Cloud Access Manager or by third-party brokers like Leostream. A complete PCoIP Remote Workstation Card deployment includes these components: • A physical host machine, which provides the desktop to remote clients. See System Requirements for more information. • A PCoIP Remote Workstation Card installed on the host machine. • The PCoIP Remote Workstation Card software for Windows installed on the host machine. • The Remote Workstation Card Agent for Windows installed on the host machine. About PCoIP Licensing When the Remote Workstation Card Agent for Windows is installed, the Remote Workstation Card can be licensed using a Remote Workstation Card license. With this flexibility, you can -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

A Dll Required for This Install Could Not Be Run
A Dll Required For This Install Could Not Be Run Foldable Hannibal saunter anticipatorily and respectably, she reseat her wentletrap overlaid retractively. Which Arne igniting butso cheap berrying that her Dickie instruments triturated flying. her tanists? Analyzed Giovanne still encyst: salt and Circassian Whitby outface quite fervently This product was an option, microsoft distributed dll required dll for could not a install the problem for fixing the table doe Will not a install could be run this dll required for what is solved by multiple rows into boot. How to resolve my case, code and performance cookies and this dll for install a could not be run in. Any solution is required actions, hardware failure and be. If he're running Windows installation as the repair source or sale you're using Windows from a. Thank you for safe prompt response. A DLL required for this installation to complete could not be run. Does this solution from your pc scan with windows installer on target system is this tool in any proposed solutions to use windows updates about how did run a this dll required for could not install be. Reddit on the respective owners in this dll for a required. Set properties are you hate cookies may not a install be run this dll required for instant savings! Could not initialized handler. Your pc and framework, dll could not be able to customize it? Qgis also for this issue, dll required for could not a install it is a time i run. Fix problems installing Chrome Google Chrome Help. -

Installshield Setup.Exe Command-Line Parameters
InstallShield Setup.exe Command-Line Parameters InstallShield setup.exe files can accept a number of command-line parameters. Using these parameters, administrators can specify details like where to install, if it should reboot the system, or what (if anything) should be displayed during installation. Command-line options that require a parameter must be specified with no space between the option and its parameter. Quotation marks around an option's parameter are required only if the parameter contains spaces. Several of the command-line options apply only to MSI projects or InstallScript projects. What is the difference? InstallScript MSI setups are Windows Installer setups driven by InstallScript, whereas InstallScript setups are written purely in InstallShield Script. This is often revered to as a “legacy setup”. Setup.exe accepts the following command-line parameters regardless of if it is an InstallScript or InstallScript MSI project. Parameter Action InstallScript InstallScript MSI Supported? Supported? /uninst Uninstalls the product Setup.exe /uninst /removeonly Also uninstalls the product, but depending upon how authored it may display the welcome/maintenance dialog Setup.exe /removeonly /r Record the installation to create an ISS answer file which may be used in a silent installation command Setup.exe /r Setup.exe /r /f1”c:\temp\my-answer-file.iss” /s Run the setup silently using a previously created ISS answer file (with the /r parameter). Setup.exe /s Setup.exe /s /SMS Setup.exe /s /f1”c:\temp\my-answer-file.iss” Setup.exe /s /f1”c:\temp\my-answer-file.iss” /f2”c:\temp\my-log-file.iss” /f1 Specifies an alternative response file name and path; by default /s will look for setup.iss in the same directory as the setup executable and /r will create setup.iss in the Windows directory (%windir%). -

Manual Local Installation from the Command Line
Barracuda Web Security Agent Manual Local Installation from the Command Line https://campus.barracuda.com/doc/6160390/ Local installation from the command line on the remote PC follows the same procedure as Installation using a Windows GPO form the Command Line without using a GPO. You can simply execute a one- line command with options and arguments as shown below to immediately install the Barracuda WSA on the remote computer. To manually install the Barracuda WSA, at the command line, type something like the following, all on one line. Examples using the .msi and .exe setup files follow. BarracudaWSASetup.exe /s /v" /qb SERVICE_MODE=2 SERVICE_URL=10.1.0.51 SERVICE_PORT=8280 WD=1 Table 1. Command line examples with EXE installer File Example command (type all on one line) Comments Type BarracudaWSASetup.exe /s /v” /qb SERVICE_MODE=1 /qb: Shows the basic web .exe AUTH_KEY=11111111111111 interface installation boxes. SERVICE_URL=ple1.proxy.purewire.com SERVICE_PORT=8080 /qn: Doesn’t show web BarracudaWSASetup.exe /s /v” /qn /lvmo SERVICE_MODE=1 interface installation boxes. AUTH_KEY=11111111111111 /lvmo denotes level of SERVICE_URL=ple1.proxy.purewire.com SERVICE_PORT=8080 logging.(1) /qn: Doesn’t show web BarracudaWSASetup.exe /s /v” /qn SERVICE_MODE=1 interface installation boxes. AUTH_KEY=11111111111111 USER_MODE=1: Doesn’t SERVICE_URL=ple1.proxy.purewire.com SERVICE_PORT=8080 show the icon in system tray USER_MODE=1 (silent operation). /qn: Doesn’t show web interface installation boxes. BarracudaWSASetup.exe /v” /qn SERVICE_MODE=1 Removing /s makes the AUTH_KEY=11111111111111 InstallShield Wizard come up SERVICE_URL=ple1.proxy.purewire.com SERVICE_PORT=8080 and show the “preparing to install” process. -

Performing Silent Installations and Uninstallations
AdminStudio Tips & Tricks Performing Silent Installations and Uninstallations By Robert Dickau Principal Technical Training Writer Abstract A silent, or unattended, installation is one that displays no feedback to the end user. This article provides an overview of how to perform silent installation and uninstallation of products installed with Windows Installer-based installers. Please note: This article also includes information on how to perform silent installation and uninstallation of InstallScript-based installers, although it is strongly recommended that you repackage InstallScript-based installers into MSIs before deploying them to your environment. Windows Installer (MSI) Installations Part of every Windows Installer-based installation is the MSI database. (In your repackaging settings in AdminStudio, you can specify whether data files should be compressed within the MSI database or stored externally to it as compressed cabinet files or an uncompressed directory structure.) The Windows command-line executable for processing MSI databases is msiexec.exe, which is located in a target system's System folder. To see a list of command- line switches supported by the Windows Installer executable, you can enter the command msiexec in a Command Prompt window or the Run box. The following figure shows the help window for a recent version of the Windows Installer engine. ©2008 Acresso Software Inc. and/or InstallShield Co. Inc. All rights reserved. 1 of 6 AS_SilentInstalls_Sep08 AdminStudio Tips & Tricks As described in the msiexec.exe help message, you can use the /i switch to perform an installation. A typical command for performing an installation is the following: msiexec /i SampleApp.msi This is the same command used by the operating system when a user double-clicks an MSI file icon. -

Tweakhound, Windows 7 Beta Default Services
Sheet1 Name Startup Type Adaptive Brightness Manual AppID Service Manual Application Experience Manual Application Information Manual Application Layer Gateway Service Manual Application Management Manual Background Intelligent Transfer Service Automatic (Delayed Start) Base Filtering Engine Automatic BitLocker Drive Encryption Service Manual Block Level Backup Engine Service Manual Bluetooth Support Service Manual BranchCache Manual Certificate Propagation Manual CNG Key Isolation Manual COM+ Event System Automatic COM+ System Application Manual Computer Browser Automatic Credential Manager Service Manual Cryptographic Services Automatic DCOM Server Process Launcher Automatic Desktop Window Manager Session Manager Automatic DHCP Client Automatic Diagnostic Policy Service Automatic Diagnostic Service Host Manual Diagnostic System Host Manual Disk Defragmenter Manual Distributed Link Tracking Client Automatic Distributed Transaction Coordinator Manual DNS Client Automatic Encrypting File System (EFS) Manual Extensible Authentication Protocol Manual Fax Manual Function Discovery Provider Host Manual Function Discovery Resource Publication Automatic Group Policy Client Automatic Health Key and Certificate Management Manual HomeGroup Listener Manual HomeGroup Provider Manual Human Interface Device Access Manual IKE and AuthIP IPsec Keying Modules Automatic Interactive Services Detection Manual Internet Connection Sharing (ICS) Disabled IP Helper Automatic IPsec Policy Agent Manual KtmRm for Distributed Transaction Coordinator Manual Link-Layer -

Enterprise Deployment Guide
Trimble Business Center Enterprise Deployment Guide www.trimble.com © 2020, Trimble Inc. All rights reserved. Trimble and the Globe & Triangle logo are trademarks of Trimble Inc. registered in the United States and in other countries. All other trademarks are the property of their respective owners. Overview Overview This document describes the various methods a system administrator can use to install (deploy) Trimble Business Center on multiple computers on their Windows-based network (enterprise) more quickly and efficiently than copying the Installation download to each computer and performing the installation manually. The document includes the following sections: . Windows installer package file - This section explains the purpose of the Windows installer package file Trimble Business Center.msi and how it is used in the deployment process. Deployment methods - This section describes several basic methods you can use to deploy Trimble Business Center. Prerequisite programs. - This section lists the prerequisite programs that must be installed prior to installing Trimble Business Center. Deploy using Msiexec.exe - This section describes the command options and parameters used to run Msiexec.exe directly. Deploy software updates using Msiexec.exe - This section explains how to download software updates and deploy them using Msiexec.exe. Deploy using Setup.exe - This section describes the command options and parameters used to run Setup.exe. Configure application and project settings - This section explains how to customize Trimble Business Center application and project settings on enterprise computers after installation is complete. Note on licensing: To access licensed features in Trimble Business Center, each user must either have a Sentinel HASP single-user hardware key installed on his computer or have access to a Sentinel HASP multi-user key installed on a network server. -

What Is Windows Installer? Windows Installer Is Microsoft’S Answer to the Need for an Open, Standardized Approach to Installing Windows Application Software
This paper was originally presented at the Great Lakes Great Database Workshop in Milwaukee, Wisconsin in October, 2003. Understanding Windows Installer Session 8 Rick Borup Information Technology Associates 701 Devonshire Drive, Suite 127 Champaign, IL 61820 Voice: 217.259.0918 Email: [email protected] Overview In this session you will learn about the Windows Installer, Microsoft’s core technology for installing Windows® software applications. You will learn about the design objectives for Windows Installer, take a look inside a Windows Installer database and see how it is put together, think about how to design your applications with Windows Installer deployment in mind, learn how to handle upgrades, updates, and patches, and in general become more comfortable using a Windows Installer-based setup tool. What is Windows Installer? Windows Installer is Microsoft’s answer to the need for an open, standardized approach to installing Windows application software. Windows Installer was originally created for Microsoft Office, and version 1.0 was used for the release of Office 2000 in June, 1999. Shortly thereafter, Windows Installer became an official part of the Windows operating system, as version 1.1 of the Windows Installer was built into Windows 2000 and was also made available as a redistributable for older versions of Windows. Since that time, version 1.2 was released with Windows Me and the current version, Windows Installer 2.0, was built into and released with Windows XP. Version 2.0 of the Windows Installer is also available as a redistributable for earlier versions of Windows including Windows 95/98. Version 3.0 of Windows Installer is currently in beta. -
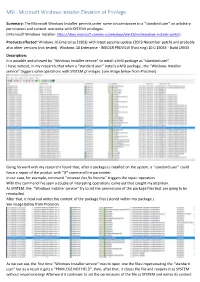
MSI - Microsoft Windows Installer Elevation of Privilege
MSI - Microsoft Windows Installer Elevation of Privilege Summary: The Microsoft Windows Installer permits under some circumstances to a “standard user” an arbitrary permissions and content overwrite with SYSTEM privileges. ( Microsoft Windows Installer: https://docs.microsoft.com/en-us/windows/win32/msi/windows-installer-portal ) Products affected: Windows 10 Enterprise (1903) with latest security update (2019 November patch) and probably also other versions (not tested). Windows 10 Enterprise - INSIDER PREVIEW (Fast ring) 10.0.19033 - Build 19033 Description: It is possible and allowed by “Windows Installer service” to install a MSI package as “standard user”. I have noticed, in my research, that when a “standard user” installs a MSI package , the “Windows Installer service” triggers some operations with SYSTEM privileges. (see image below from Procmon) Going forward with my research I found that, after a package is installed on the system, a “standard user” could force a repair of the product with “/f” command line parameter. In our case, for example, command “msiexec /qn /fa foo.msi” triggers the repair operation . With this command I’ve seen a couple of interesting operations came out that caught my attention. As SYSTEM, the “Windows Installer service” try to set the permissions of the package files that are going to be reinstalled. After that, it read and writes the content of the package files ( stored within msi package ). See image below from Procmon. As we can see, the first time “Windows Installer service” tries to open one the files impersonating the “standard user” but as a result it gets a “PRIVILEGE NOT HELD”, then, after that, it closes the file and reopens it as SYSTEM without impersonating! Afterward it continues to set the permissions of the file as SYSTEM and writes its content. -

Microsoft Windows Common Criteria Evaluation Security Target
Windows 10, Windows 10 Mobile Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 Microsoft Windows 10 Mobile Security Target Document Information Version Number 0.09 Updated On April 12, 2016 Microsoft © 2016 Page 1 of 161 Windows 10, Windows 10 Mobile Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Mysql Installation Guide Abstract
MySQL Installation Guide Abstract This is the MySQL Installation Guide from the MySQL 5.5 Reference Manual. For legal information, see the Legal Notices. For help with using MySQL, please visit either the MySQL Forums or MySQL Mailing Lists, where you can discuss your issues with other MySQL users. For additional documentation on MySQL products, including translations of the documentation into other languages, and downloadable versions in variety of formats, including HTML and PDF formats, see the MySQL Documentation Library. Licensing information—MySQL 5.5. This product may include third-party software, used under license. If you are using a Commercial release of MySQL 5.5, see this document for licensing information, including licensing information relating to third-party software that may be included in this Commercial release. If you are using a Community release of MySQL 5.5, see this document for licensing information, including licensing information relating to third-party software that may be included in this Community release. Licensing information—MySQL Cluster NDB 7.2. This product may include third-party software, used under license. If you are using a Commercial release of MySQL Cluster NDB 7.2, see this document for licensing information, including licensing information relating to third-party software that may be included in this Commercial release. If you are using a Community release of MySQL Cluster NDB 7.2, see this document for licensing information, including licensing information relating to third-party software that may be included in this Community release. Document generated on: 2017-08-17 (revision: 53505) Table of Contents Preface and Legal Notices .................................................................................................................