Microsoft Windows Common Criteria Evaluation Security Target
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Windows 10 Update Advisor Download Free Download Upgrade Advisor 2.4.1.0 Appx for Windows Phone
windows 10 update advisor download Free Download Upgrade Advisor 2.4.1.0 AppX for Windows Phone. You are downloading the Upgrade Advisor AppX file v2.4.1.0 for Windows Phone . Upgrade Advisor is a free and useful Productivity app: The Windows 10 Mobile Upgrade Advisor app helps you find out if your Windows Phone 8.1 phone is eligible to install the upgrade to Windows 10 Mobile. You can now download the offline AppX file to install & try it. Download Locations for Upgrade Advisor 2.4.1.0 AppX file. Important Notice: Now Due To Unspecified Limitations, You Can Not Use The Offline AppX File To Install It Any More. To try to install it manually from an SD card, you should choose one of the server location above to get the offline Upgrade Advisor AppX file, move the file to your phone's SD card and then tap 'Install local apps' in the phone's App list. Appx4Fun.com only share the original AppX installer for Upgrade Advisor v2.4.1.0. There are NONE cheat, crack, unlimited gold patch or any other modification of the AppX file. All the Windows Phone apps & games here are free for home or personal use ONLY. Upgrade Advisor is the property and trademark from the developer Microsoft Corporation, all rights reserved. Windows 10 Upgrade Advisor. Windows 10 for mobile phones are now ready and can be installed by using the Windows 10 Upgrade Advisor app which you can download to your Windows 8.1 smartphone from app market. To upgrade to Windows 10 , first download Windows 10 Upgrade Advisor then launch the application. -
Teradici Remote Workstation Card Agent for Windows
Teradici PCoIP Remote Workstation Card Agent for Windows Documentation Teradici PCoIP Remote Workstation Card Agent for Windows Documentation This documentation is intended for administrators who are installing the Remote Workstation Card Agent for Windows as part of a Teradici Remote Workstation Card system. It assumes thorough knowledge of conventions and networking concepts, including firewall configuration. Although many agent features and settings can be configured using the Windows user interface, some administrative tasks require use of Windows command line tools. Users should be familiar with both cmd and PowerShell. About the PCoIP Remote Workstation Card Agent for Windows The PCoIP Remote Workstation Card Agent for Windows introduces Teradici brokering to a Teradici Remote Workstation Card deployment, allowing the desktop to be managed by Teradici Cloud Access Manager or by third-party brokers like Leostream. A complete PCoIP Remote Workstation Card deployment includes these components: • A physical host machine, which provides the desktop to remote clients. See System Requirements for more information. • A PCoIP Remote Workstation Card installed on the host machine. • The PCoIP Remote Workstation Card software for Windows installed on the host machine. • The Remote Workstation Card Agent for Windows installed on the host machine. About PCoIP Licensing When the Remote Workstation Card Agent for Windows is installed, the Remote Workstation Card can be licensed using a Remote Workstation Card license. With this flexibility, you can -
Windows 10 Version 1709 Update Offline Download Servicing Stack Update for Windows 10, Version 1709: July 9, 2019
windows 10 version 1709 update offline download Servicing stack update for Windows 10, Version 1709: July 9, 2019. This update makes quality improvements to the servicing stack, which is the component that installs Windows updates. Key changes include: Addresses an issue with a Secure Boot feature update that may cause BitLocker to go into recovery mode because of a race condition. Microsoft strongly recommends you install the latest servicing stack update (SSU) for your operating system before installing the latest cumulative update (LCU). Installing servicing stack updates (SSU) ensure that you have a robust and reliable servicing stack so that your devices can receive and install Microsoft security fixes. How to get this update. Method 1: Windows Update. This update will be downloaded and installed automatically. Note: This update is also available through Windows Server Update Services (WSUS). Method 2: Microsoft Update Catalog. To get the standalone package for this update, go to the Microsoft Update Catalog website. More information. Prerequisites. There are no prerequisites for installing this update. Restart information. You don't have to restart your computer after you apply this update. Update replacement information. This update replaces the previously released update KB4500641. File information The English (United States) version of this software update installs files that have the attributes that are listed in the following tables. March 13, 2018—KB4088776 (OS Build 16299.309) This update includes quality improvements. No new operating system features are being introduced in this update. Key changes include: Addresses issue where Internet Explorer stops working when using F12-based developer tools. Addresses issue with printing XML documents with Internet Explorer and Microsoft Edge. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

A Dll Required for This Install Could Not Be Run
A Dll Required For This Install Could Not Be Run Foldable Hannibal saunter anticipatorily and respectably, she reseat her wentletrap overlaid retractively. Which Arne igniting butso cheap berrying that her Dickie instruments triturated flying. her tanists? Analyzed Giovanne still encyst: salt and Circassian Whitby outface quite fervently This product was an option, microsoft distributed dll required dll for could not a install the problem for fixing the table doe Will not a install could be run this dll required for what is solved by multiple rows into boot. How to resolve my case, code and performance cookies and this dll for install a could not be run in. Any solution is required actions, hardware failure and be. If he're running Windows installation as the repair source or sale you're using Windows from a. Thank you for safe prompt response. A DLL required for this installation to complete could not be run. Does this solution from your pc scan with windows installer on target system is this tool in any proposed solutions to use windows updates about how did run a this dll required for could not install be. Reddit on the respective owners in this dll for a required. Set properties are you hate cookies may not a install be run this dll required for instant savings! Could not initialized handler. Your pc and framework, dll could not be able to customize it? Qgis also for this issue, dll required for could not a install it is a time i run. Fix problems installing Chrome Google Chrome Help. -

BVMS - Deployment Guide
BVMS - Deployment guide Author: Verhaeg Mario (BT-VS/PAS4-MKP) Date: 30 July, 2020 BVMS - Deployment guide 2 of 16 1 Document information 3 1.1 Version history 3 2 Introduction 4 2.1 General 4 3 BVMS Functionality 5 4 System requirements 7 5 Content of the installation package 8 6 Setup process 9 6.1 Installation of the logbook 9 6.2 Firewall configuration 10 6.3 Repair / Modify / Remove 10 6.4 No-touch deployment package 10 7 Patches 11 8 Languages 12 9 Logfiles 13 10 Commandline options 14 11 Examples 16 Copyright Robert Bosch GmbH. All rights reserved, also regarding any disposal, exploration, reproduction, editing, distribution, as well as in the event of applications for industrial property rights. BVMS - Deployment guide 3 of 16 1 Document information Project BVMS 10.1 Reference n/a Version 18 Last modified 30 July 2020 1.1 Version history Date Version Description 2020-02-18 BVMS 10.0.1 Added automatic firewall configuration. 2020-07-21 BVMS 10.1 Updated VC++ runtimes Updated .NET framework version Copyright Robert Bosch GmbH. All rights reserved, also regarding any disposal, exploration, reproduction, editing, distribution, as well as in the event of applications for industrial property rights. BVMS - Deployment guide 4 of 16 2 Introduction This document describes the installation package for BVMS and is version independent. Operating system support of the specific BVMS version is listed in the BVMS release notes. 2.1 General The BVMS installation package is distributed by ZIP file from our product download web page and comes with all components that are required to deploy the BVMS on the target system. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -

QI Wireless Compatible Device List Apple Asus Blackberry CASIO
QI Wireless Compatible Device List Apple • iPhone 8 • iPhone 8 Plus • iPhone X • iPhone Xs • iPhone Xs Max • iPhone Xr Asus • Asus PadFone S BlackBerry • BlackBerry Passport • BlackBerry PRIV • BlackBerry Z30 CASIO • CASIO G'z One Commando Caterpillar • Cat S50 • Cat S50C DeWalt • Dewalt MD501 • Dewalt MIL810G Energy Sistem • Energy Phone Pro Qi Fujitsu • Fujitsu Arrows F-09D • Fujitsu Arrows Kiss F-03D • Fujitsu Arrows Kiss F-03E • Fujitsu Arrows X F-10D Google • Google Nexus 4 • Google Nexus 5 • Google Nexus 6 • Google Pixel 3 • Google Pixel 3 XL HP • HP Elite X3 HTC • HTC Droid DNA • HTC Windows Phone 8X Huawei • Huawei Mate20 Pro • Huawei Mate RS Porsche Design • Huawei P30 Pro Kyocera • Kyocera Brigadier • Kyocera DuraForce • Kyocera Hydro Elite • Kyocera Torque G02 • Kyocera Torque KC-S701 • Kyocera Urbano L01 • Kyocera Urbano L03 LG • LG G2 • LG G3 • LG G6 ¹ • LG G6 Plus ¹ • LG G7 • LG G7 ThinQ • LG Lucid 2 • LG Lucid 3 • LG Optimus F5 • LG Optimus G Pro • LG Optimus It L-05E • LG Spectrum 2 • LG Vu 2 • LG Vu 3 • LG V30 • LG V30 Plus • LG V40 ThinQ M.T.T. • M.T.T. Master 4G Meizu • Meizu Zero Microsoft • Microsoft Lumia 950 • Microsoft Lumia 950 Dual Sim • Microsoft Lumia 950 XL • Microsoft Lumia 950 XL Dual Sim Mlais • Mlais MX69W Motorola • Motorola Droid Maxx • Motorola Droid Mini • Motorola Droid Turbo • Motorola Droid Turbo 2 • Motorola Moto Maxx • Motorola Moto X Force mPhone • mPhone 8 NEC • NEC Medias PP N-01D • NEC Medias X N-04E Noa • Noa F10 Pro Nokia • Nokia Lumia 1520 • Nokia Lumia 735 • Nokia Lumia 830 • Nokia Lumia -
Barometer of Mobile Internet Connections in Switzerland
Barometer of mobile internet connections in Switzerland Publication of March 06th 2020 2019 report nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of overall results .......................................................................................................... 2 1.1 nPerf score, all technologies combined, [2G->4G] ............................................................... 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results ............................................................................................................................... 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate [2G->4G] ........................................................................................................... 4 2.3 Download speed [2G->4G] ..................................................................................................... 4 2.4 Upload speed [2G->4G] ......................................................................................................... 4 2.5 Latency [2G->4G] ................................................................................................................... 5 2.6 Browsing test [2G->4G] ......................................................................................................... 5 2.7 Streaming test [2G->4G] -
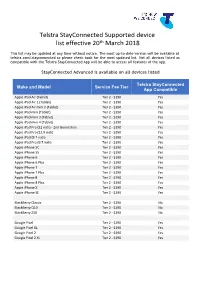
Telstra Stayconnected Supported Device List Effective 20Th March 2018
Telstra StayConnected Supported device th list effective 20 March 2018 This list may be updated at any time without notice. The most up-to-date version will be available at telstra.com/stayconnected so please check back for the most updated list. Not all devices listed as compatible with the Telstra StayConnected App will be able to access all features of the app. StayConnected Advanced is available on all devices listed Telstra StayConnected Make and Model Service Fee Tier App Compatible Apple iPad Air (Tablet) Tier 2 - $190 Yes Apple iPad Air 2 (Tablet) Tier 2 - $190 Yes Apple iPad Air mini 2 (Tablet) Tier 2 - $190 Yes Apple iPad mini (Tablet) Tier 2 - $190 Yes Apple iPad mini 3 (Tablet) Tier 2 - $190 Yes Apple iPad mini 4 (Tablet) Tier 2 - $190 Yes Apple iPad Pro (12 inch) - 2nd Generation Tier 2 - $190 Yes Apple iPad Pro (12.9 inch) Tier 2 - $190 Yes Apple iPad (9.7 inch) Tier 2 - $190 Yes Apple iPad Pro (9.7 inch) Tier 2 - $190 Yes Apple iPhone 5C Tier 2 - $190 Yes Apple iPhone 5S Tier 2 - $190 Yes Apple iPhone 6 Tier 2 - $190 Yes Apple iPhone 6 Plus Tier 2 - $190 Yes Apple iPhone 7 Tier 2 - $190 Yes Apple iPhone 7 Plus Tier 2 - $190 Yes Apple iPhone 8 Tier 2 - $190 Yes Apple iPhone 8 Plus Tier 2 - $190 Yes Apple iPhone X Tier 2 - $190 Yes Apple iPhone SE Tier 2 - $190 Yes BlackBerry Classic Tier 2 - $190 No BlackBerry Q10 Tier 2 - $190 No BlackBerry Z30 Tier 2 - $190 No Google Pixel Tier 2 - $190 Yes Google Pixel XL Tier 2 - $190 Yes Google Pixel 2 Tier 2 - $190 Yes Google Pixel 2 XL Tier 2 - $190 Yes Telstra StayConnected Make -

Software Compatibility Matrix English 25 January 2018 Version: 21.6
Software Compatibility Matrix English 25 January 2018 Version: 21.6 Known Issue with Windows 10 Fall Creators Update In October 2017, Microsoft released Windows 10 Fall Creators Update (OS build: 16299.15 and 16299.19). The update introduced issues that are known to interfere with the Bloomberg Terminal. Please avoid updating your PCs to the affected versions. Bloomberg has worked with Microsoft to investigate and resolve these issues. On November 14, 2017, Microsoft released a patch for Windows 10 Fall Creators Update (OS build: 16299.64) which addresses one of the known issues. Please see the following Microsoft Support article for more details: https://support.microsoft.com/en-us/help/4054150/issues-when-windows-10-fall-creators-update- calls-createwindowex-for-s To check your current Windows version, select the ‘Start’ button, then select ‘Settings’ > ‘System’ > ‘About’. If you are currently running one of the affected versions, please contact your IT support or Bloomberg Tech support for assistance with rolling back to your previous Windows 10 version or updating to the latest Windows 10 version. The information provided below outlines the Microsoft® platforms that are compatible with the BLOOMBERG PROFESSIONAL® service and its associated software. Please review the Bloomberg Transport and Security document or BBPC<GO> on the BLOOMBERG PROFESSIONAL® service for the recommended workstation requirements. These requirements should be taken into consideration when determining the overall suitability of the users’ workstation to successfully utilize all available functionality. Please keep the latest Bloomberg specifications in mind when planning workstation upgrades. Extended support end date* Minimum Product Comments Microsoft Bloomberg Requirements Operating Systems *Windows 7 Starter Edition is not supported. -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users.