Nortonlifelock to Acquire Avira
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton Antivirus™ 2009 Feature Comparison Chart
Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton AntiVirus™ 2009 Feature Comparison Chart Feature Norton 360 Norton Internet Norton Explanation Version 3.0 Security 2009 AntiVirus 2009 Core Protection Antivirus ✔ ✔ ✔ Detects and removes viruses, Internet worms, and Trojan horses Antispyware ✔ ✔ ✔ Prevents spyware from infecting the PC Email and instant messaging protection ✔ ✔ ✔ Monitors email and instant messaging so users can exchange files without exchanging threats Antispam ✔ ✔ Automatically filters out annoying and fraudulent or phishing email from the user’s email inbox Advanced Protection Botnet detection ✔ ✔ ✔ Detects and prevents others from taking control of the PC, accessing private information, or using the computer to host an attack Rootkit detection ✔ ✔ ✔ Finds and removes threats that are hidden deep in the operating system Norton™ Insight ✔ ✔ ✔ Includes innovative, intelligence-driven technology for faster, fewer, shorter scans Norton™ Pulse Updates ✔ ✔ ✔ Delivers rapid pulse updates every 5 to 15 minutes for protection against new threats Smart, two-way firewall ✔ ✔ Makes intelligent incoming and outgoing security decisions without interrupting users to ask them each time Enhanced browser protection ✔ ✔ ✔ Secures against Web-based attacks that use browser vulnerabilities to infect PCs with malware Real-time behavioral protection ✔ ✔ ✔ Provides enhanced, real-time protection (SONAR™) Wireless network security protection ✔ ✔ Checks the status of wireless network security and provides expert advice on managing -

Mind Your Own Business: a Longitudinal Study of Threats and Vulnerabilities in Enterprises
Mind your Own Business: A Longitudinal Study of Threats and Vulnerabilities in Enterprises Abstract—Enterprises own a significant fraction of the hosts to, financial assets, and security investment. Thus, it is very connected to the Internet and possess valuable assets, such as likely that the best practices mentioned above do not equally financial data and intellectual property, which may be targeted apply to all of them. by attackers. They suffer attacks that exploit unpatched hosts and install malware, resulting in breaches that may cost millions Currently, it is not clear how the security posture of in damages. Despite the scale of this phenomenon, the threat and enterprises differ according to different factors and whether vulnerability landscape of enterprises remains under-studied. The enterprises are indeed more secure than consumer hosts, i.e., security posture of enterprises remains unclear, and it’s unknown if their security investment is paying off. In this paper, we aim whether enterprises are indeed more secure than consumer hosts. to throw light into these questions by conducting a large-scale To address these questions, we perform the largest and longest longitudinal measurement study of enterprise security. We an- enterprise security study up to date. Our data covers nearly alyze the enterprise threat landscape including the prevalence 3 years and is collected from 28K enterprises, belonging to 67 industries, which own 82M hosts and 73M public-facing servers. of malware and PUP in enterprise hosts and how common security practices, such as vulnerability patching and operating Our measurements comprise of two parts: an analysis of system updates are handled. -

Norton™ Utilities Premium: User Manual
Norton™ Utilities Premium User Manual Norton Utilities Premium User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright © 2018 Symantec Corporation. All rights reserved. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. Any use, modification, reproduction release, performance, display or disclosure of the Licensed Software and Documentation by the U.S. Government shall be solely in accordance with the terms of this Agreement. -
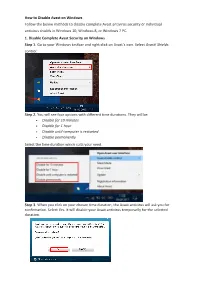
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Printmgr File
ˆ200F$l2ZLVgqon1gÈŠ 200F$l2ZLVgqon1g¨ VDI-W7-PR3-1248 SYMANTEC CORPORATION Donnelley Financial12.6.30 EGV yanns0ap24-May-2018 22:26 EST 594139 TX 1 2* SYMANTEC CORP PAL HTM ESS 0C Page 1 of 1 UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM SD SPECIALIZED DISCLOSURE REPORT Symantec Corporation (Exact Name of Registrant as Specified in its Charter) Delaware 000-17781 77-0181864 (State or other jurisdiction of (Commission (IRS Employer incorporation or organization ) File Number) Identification No.) 350 Ellis Street, Mountain View, California 94043 (Address of Principal Executive Offices) (Zip Code) Nicholas R. Noviello, Executive Vice President and Chief Financial Officer (650) 527-8000 (Name and telephone number, including area code, of the person to contact in connection with this report.) Not Applicable (Former Name or Former Address, if Changed Since Last Report) Check the appropriate box below to indicate the rule pursuant to which this form is being filed, and provide the period to which the information in this form applies: Rule 13p-1 under the Securities Exchange Act (17 CFR 240.13p-1) for the reporting period January 1 to December 31, 2017 ˆ200F$l2ZLVhV$Vk6$Š 200F$l2ZLVhV$Vk6$ VDI-W7-PFL-0639 SYMANTEC CORPORATION Donnelley Financial12.6.29 EGV ahern0ap24-May-2018 23:14 EST 594139 TX 2 3* SYMANTEC CORP PAL HTM ESS 0C Page 1 of 1 Item 1.01. Conflict Minerals Disclosure and Report. Conflict Minerals Disclosure A copy of the Conflict Minerals Report of Symantec Corporation (“Symantec”) for the reporting period January 1 to December 31, 2017 is filed as Exhibit 1.01 to this specialized disclosure report on Form SD and is also available at Symantec’s website at https://www.symantec.com/about/corporate-responsibility/resources/corporate-responsibility-policies . -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted -

RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC
NOT FOR RELEASE, PUBLICATION OR DISTRIBUTION, IN WHOLE OR IN PART, DIRECTLY OR INDIRECTLY, IN, INTO OR FROM ANY JURISDICTION WHERE TO DO SO WOULD CONSTITUTE A VIOLATION OF THE RELEVANT LAWS OR REGULATIONS OF SUCH JURISDICTION FOR IMMEDIATE RELEASE THIS ANNOUNCEMENT CONTAINS INSIDE INFORMATION 10 August 2021 RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC. to be effected by means of a Scheme of Arrangement under Part 26 of the Companies Act 2006 Summary Further to the announcements made by NortonLifeLock Inc. (“NortonLifeLock”) and Avast plc (“Avast” or the “Company”) on 14 July 2021, the boards of NortonLifeLock and Avast are pleased to announce that they have reached agreement on the terms of a recommended merger of Avast with NortonLifeLock, in the form of a recommended offer by Nitro Bidco Limited (“Bidco”), a wholly- owned subsidiary of NortonLifeLock, for the entire issued and to be issued ordinary share capital of the Company (the “Merger”). It is intended that the Merger will be effected by means of a Court- sanctioned scheme of arrangement under Part 26 of the Companies Act (the “Scheme”). The boards of NortonLifeLock and Avast believe the Merger has compelling strategic logic and represents an attractive opportunity to create a new, industry leading consumer Cyber Safety business, leveraging the established brands, technical expertise and innovation of both groups to deliver substantial benefits to consumers, shareholders and other stakeholders. Under the terms of the Merger, Avast Shareholders will be entitled to receive: for each Avast Share held: USD 7.61 in cash and 0.0302 of a New NortonLifeLock Share in respect of their entire holding of Avast Shares (the “Majority Cash Option”). -

FS-TST) Is a Software Package That Supports the Testing of Disk Imaging Tools
NISTIR 7103-B Forensic Software Testing Support Tools Test Summary Report Serban Gavrila VDG, Inc. Elizabeth Fong Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 NIST National Institute of Standards and Technology Technology Administration U.S. Department of Commerce NISTIR 7103-B Forensic Software Testing Support Tools Test Summary Report Serban Gavrila VDG, Inc. Elizabeth Fong Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 April 2004 U.S.DEPARTMENT OF COMMERCE Donald L. Evans, Secretary TECHNOLOGY ADMINISTRATION Phillip J. Bond, Under Secretary of Commerce for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Ardent L. Bement, Jr., Director Forensic Software Testing Support Tools Test Summary Report Serban Gavrila* Elizabeth Fong ** ABSTRACT The Computer Forensics Tool Testing (CFTT) project at the National Institute of Standards and Technology (NIST), an agency of the United States Department of Commerce, provides a measure of confidence in the software tools used in computer forensic investigations. CFTT focuses on a class of tools called disk-imaging tools that copy or “image” hard disk drives. Forensic Software Testing Support Tools (FS-TST) is a software package that supports the testing of disk imaging tools. FS-TST includes 15 tools that perform hard disk initialization, faulty disk simulation, hard disk comparisons, extraction of information from a hard disk, and copying of disks or disk partitions. This NIST Interagency/Internal Report consists of two parts. Part A, covers the planning, design and specification of testing the tools included in the FS-TST package. Part B, which is this document, covers the test summary report. -

Aluria Security Center Avira Antivir Personaledition Classic 7
Aluria Security Center Avira AntiVir PersonalEdition Classic 7 - 8 Avira AntiVir Personal Free Antivirus ArcaVir Antivir/Internet Security 09.03.3201.9 x64 Ashampoo FireWall Ashampoo FireWall PRO 1.14 ALWIL Software Avast 4.0 Grisoft AVG 7.x Grisoft AVG 6.x Grisoft AVG 8.x Grisoft AVG 8.x x64 Avira Premium Security Suite 2006 Avira WebProtector 2.02 Avira AntiVir Personal - Free Antivirus 8.02 Avira AntiVir PersonalEdition Premium 7.06 AntiVir Windows Workstation 7.06.00.507 Kaspersky AntiViral Toolkit Pro BitDefender Free Edition BitDefender Internet Security BullGuard BullGuard AntiVirus BullGuard AntiVirus x64 CA eTrust AntiVirus 7 CA eTrust AntiVirus 7.1.0192 eTrust AntiVirus 7.1.194 CA eTrust AntiVirus 7.1 CA eTrust Suite Personal 2008 CA Licensing 1.57.1 CA Personal Firewall 9.1.0.26 CA Personal Firewall 2008 CA eTrust InoculateIT 6.0 ClamWin Antivirus ClamWin Antivirus x64 Comodo AntiSpam 2.6 Comodo AntiSpam 2.6 x64 COMODO AntiVirus 1.1 Comodo BOClean 4.25 COMODO Firewall Pro 1.0 - 3.x Comodo Internet Security 3.8.64739.471 Comodo Internet Security 3.8.64739.471 x64 Comodo Safe Surf 1.0.0.7 Comodo Safe Surf 1.0.0.7 x64 DrVirus 3.0 DrWeb for Windows 4.30 DrWeb Antivirus for Windows 4.30 Dr.Web AntiVirus 5 Dr.Web AntiVirus 5.0.0 EarthLink Protection Center PeoplePC Internet Security 1.5 PeoplePC Internet Security Pack / EarthLink Protection Center ESET NOD32 file on-access scanner ESET Smart Security 3.0 eTrust EZ Firewall 6.1.7.0 eTrust Personal Firewall 5.5.114 CA eTrust PestPatrol Anti-Spyware Corporate Edition CA eTrust PestPatrol