Q3 Consumer Endpoint Protection Jul-Sep 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Ids/Ips
--,.---------------------------------- EO THONG TIN vA TRUYEN THONG CONG HOA xA HOI CHiT NGHIA VII::T NAM DQc qp -T\I' Do - Hl}.nh Phuc S6:'u5J1BTTTT-VNCERT Ha NQi, ngay • V/v Huang dful dam bao an toan thong : /\p C8AJj S:'~~G'lGrf~P CAOSJ Vi~TNAM tin cho cac C6ng/Trang thOng tin di~n t\r 'IAN PliCl,G Dill J,tN"A NO: ~. s6: .2.-.4.6 . T';ProAN CON~ ~PCSYN DEN Ngay:.OLLi.o.1.-1. .' eJ!. Aj0.,t N "'-I. "/I'<'~~""..•••••••••.•Cac Bi), COquan ngang Bi), COquan trvc thui)c C phu. nr~(c)N) iJE N~y:!l1..W~.ILUBND cac tinh, thanh ph5 trvc thui)c Trung uang, Chuy~n:....I(<r... ~~..r••••••••• .............. Th\Ic hi~n chi d:;to cua Thu tuOng Chinh pM v~ vi~c dam bao an toan 17~ong tin cho cac c6ng thong tin di~n tu, dang thai ~S th5ng nh~t v~ ni)i dung va ~ phuang phap quan Iy an t01m thong tin theo yeu cau cua Nghi diM cua Chinh phu s5 4312011/ND-CP ngay 13/612011, Bi) Thong tin va Truy~n thOng hUOng d~n cac co quan nha nuac triSn khai ap d\lng tM li~u "HuOng d~ mi)t s5 bi~n phap ky thu~t co ban dam bao an t01mcho c6ng/trang thong tin di~n ill". Hi li~u nay bao gam mi)t s5 bi~n phap ky thu~t thiSt ySu nh~t nh~m dam bao xay d\Iilg va v~ hanh an toan cac c6ng/trang thOng tin di~n ill va dugc trinh bay trong van ban gui kern theo cong van nay. -

Anyconnect および Host Scan のアンチウイルス/アンチスパイウェア
AnyConnect および Host Scan のアンチウイルス/アンチスパイウェア/ファイアウォール サポート表 AnyConnect ポスチャ モジュールにより、AnyConnect Secure Mobility クライアントはホストにインス トールされているオペレーティング システム、およびアンチウイルス、アンチスパイウェア、ファイアウォールの 各ソフトウェアを識別できます。 Host Scan アプリケーションはポスチャ モジュールのコンポーネントに含まれ る、こうした情報を収集するアプリケーションです。 AnyConnect 3.0 より、Host Scan パッケージは AnyConnect Secure Mobility クライアントおよび Cisco Secure Desktop(CSD)の共有コンポーネントになっています。 それ以前は、Host Scan パッケージは CSD を インストールすることによってのみ利用可能になるコンポーネントの 1 つでした。 Host Scan パッケージを CSD から分離したのは、CSD の一部として提供されていたときよりも、ユー ザが頻繁に Host Scan サポート表を更新できるようにするためです。 このサポート表には、ユーザが動的なア クセス ポリシーで使用しているアンチウイルス/アンチスパイウェア/ファイアウォール アプリケーションの製品 名とバージョン情報が記載されています。 シスコでは、Host Scan パッケージに Host Scan アプリケーション、 Host Scan サポート表、および他のコンポーネントを含めて提供しています。 Host Scan サポート表のリスト アンチウイルス アプリケーション総合リスト アンチスパイウェア アプリケーション総合リスト ファイアウォール アプリケーション総合リスト Windows 用アンチウイルス Windows 用アンチスパイウェア Windows 用ファイアウォール Linux 用アンチウイルス Linux 用ファイアウォール Mac OS 用アンチウイルス Mac OS 用アンチスパイウェア Mac OS 用ファイアウォール A B C D E F G H I J K L M N O P Q R S T U V W X Y Z AA AB AC AD AE ファイル データ ファ バージョ データ ファイ データ ファイル データ ファイ エンジンのバー RTP の RTP の 前回のスキャン スキャン/クリー システムのフル アンイン GUI のアク トレイ アイコンの トレイ アイコン 有効期 脅威ログの取 スキャン プログラ フル スキャンの進捗 インストール ディ 一括スキャ メモリ スキャ アンチウイルス製品名 ライブ更新 サービス GUI の表示 のスキャ 有効日の取得 更新の進捗表示 プログラム言語の取得 イル dir の取 市場での別名 ン ルの時刻 のバージョン ルの署名 ジョン チェック 設定 時刻 ニング スキャン ストール ティブ化 表示 の非表示 限 得 ムの実行 表示 レクトリの取得 ン ン 1 ン 得 2 3 360Safe.com 4 360 Antivirus 1.x 9989999898888898 8888 8 9 8 9 9 9 88 5 360杀毒 1.x 9999988898888898 8889 8 8 8 9 9 9 88 6 AEC, spol. s r.o. 7 TrustPort Antivirus 2.x 8888998899888999 9888 8 9 8 9 8 988 8 Agnitum Ltd. -

Checks to Avoid Malware Protect Your Laptop with Security Essentials
What is Malware? Malware is software that can infect you computer and can be a virus or malicious software that can harm & slow your system or try to steal your personal information. To help avoid malware follow the check list below. Checks to avoid Malware Check you have updated Antivirus software installed such as Microsoft Security Essentials Install and run an Anti-Malware program such as Malwarebytes Uninstall any Peer 2 Peer software such as Limewire or Vuze Be careful with email attachments and never respond to mails asking for your password Protect your Laptop with Security Essentials Microsoft Security Essentials is a free antivirus software product for Windows Vista, 7 & 8. It pro- vides protection against different types of malware such as computer virus, spyware, rootkits, trojans & other malicious software. Download & install Security Essentials from the following link http:// www.microsoft.com/security_essentials/ Clear Infections using Malwarebytes Malware bytes is free to download & install from http://www.malwarebytes.org Once installed it is recommended that you run a Full Scan of your laptop to check for any malware that may reside on the system. Once complete, follow the on screen instructions to finish removing any threats found. You should regularly run updates and scans to ensure your system remains clean. It is also advisable to scan external storage devices such as USB keys as they can spread infections. If the above criteria are fully met, ISS staff at the service desk on the ground floor of the library are happy to investigate problems on your laptop For more information go to http://www.dcu.ie/iss ISS online service desk: https://https://iss.servicedesk.dcu.ie Follow ISS on Twitter @ISSservice . -

Mind Your Own Business: a Longitudinal Study of Threats and Vulnerabilities in Enterprises
Mind your Own Business: A Longitudinal Study of Threats and Vulnerabilities in Enterprises Abstract—Enterprises own a significant fraction of the hosts to, financial assets, and security investment. Thus, it is very connected to the Internet and possess valuable assets, such as likely that the best practices mentioned above do not equally financial data and intellectual property, which may be targeted apply to all of them. by attackers. They suffer attacks that exploit unpatched hosts and install malware, resulting in breaches that may cost millions Currently, it is not clear how the security posture of in damages. Despite the scale of this phenomenon, the threat and enterprises differ according to different factors and whether vulnerability landscape of enterprises remains under-studied. The enterprises are indeed more secure than consumer hosts, i.e., security posture of enterprises remains unclear, and it’s unknown if their security investment is paying off. In this paper, we aim whether enterprises are indeed more secure than consumer hosts. to throw light into these questions by conducting a large-scale To address these questions, we perform the largest and longest longitudinal measurement study of enterprise security. We an- enterprise security study up to date. Our data covers nearly alyze the enterprise threat landscape including the prevalence 3 years and is collected from 28K enterprises, belonging to 67 industries, which own 82M hosts and 73M public-facing servers. of malware and PUP in enterprise hosts and how common security practices, such as vulnerability patching and operating Our measurements comprise of two parts: an analysis of system updates are handled. -

Testing Anti-Virus in Linux: How Effective Are the Solutions Available for Desktop Computers?
Royal Holloway University of London ISG MSc Information Security thesis series 2021 Testing anti-virus in Linux: How effective are the solutions available for desktop computers? Authors Giuseppe Raffa, MSc (Royal Holloway, 2020) Daniele Sgandurra, Huawei, Munich Research Center. (Formerly ISG, Royal Holloway.) Abstract Anti-virus (AV) programs are widely recognized as one of the most important defensive tools available for desktop computers. Regardless of this, several Linux users consider AVs unnec- essary, arguing that this operating system (OS) is “malware-free”. While Windows platforms are undoubtedly more affected by malicious software, there exist documented cases of Linux- specific malware. In addition, even though the estimated market share of Linux desktop sys- tems is currently only at 2%, it is certainly possible that it will increase in the near future. Considering all this, and the lack of up-to-date information about Linux-compatible AV solutions, we evaluated the effectiveness of some anti-virus products by using local installations, a well- known on-line malware scanning service (VirusTotal) and a renowned penetration testing tool (Metasploit). Interestingly, in our tests, the average detection rate of the locally-installed AV programs was always above 80%. However, when we extended our analysis to the wider set of anti-virus solutions available on VirusTotal, we found out that the average detection rate barely reached 60%. Finally, when evaluating malicious files created with Metasploit, we verified that the AVs’ heuristic detection mechanisms performed very poorly, with detection rates as low as 8.3%.a aThis article is published online by Computer Weekly as part of the 2021 Royal Holloway informa- tion security thesis series https://www.computerweekly.com/ehandbook/Royal-Holloway-Testing-antivirus- efficacy-in-Linux. -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

Webroot Secureanywhere User Guide Complete Edition
User Guide for the Complete Edition Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot SecureAnywhere User Guide for the Complete Edition Version 8.0.1; May, 2012 © 2011- 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is a trademark of Webroot Software, Inc. All other product and company names mentioned may be trademarks or registered trademarks of their respective owners. Contents 1: Getting Started . .1 Installing the software. .2 Using the main interface. .5 Using the system tray menu. .6 Viewing the protection status . .7 Creating a Webroot account. .8 Adding PCs to your account . .9 Adding mobile devices to your account . .10 Viewing the PC security status online . .11 2: Scans . .15 About scans . .16 Running an immediate scan. .17 Running a custom scan . .19 Changing the scan schedule . .21 Changing scan settings . .23 3: Shields . .25 About shields . .26 Changing Realtime shield settings . .27 Changing Behavior shield settings . .29 Changing Core System shield settings . .31 Changing Web Threat shield settings . .33 4: Firewall. .35 About the firewall . .36 Changing firewall alert settings . .37 Managing network applications . .38 5: Quarantine . .41 About quarantine . .42 Managing quarantined items . .43 Managing file detection . .45 Using antimalware tools . .47 Saving a threat log . .49 6: Identity Protection. .51 About the Identity shield. .52 Changing Identity shield settings . .53 Managing protected applications . .55 Managing protected websites. .57 7: Password Management . .61 About Password Management . .62 Downloading the Passwords component . .63 Capturing login credentials in a website. -

Mcafee Epolicy Orchestrator DATA SHEET
DATA SHEET McAfee ePolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage by offering more time to exploit the gap not seen between the tools and do damage. In addition, the cybersecurity workforce is limited and needs to be empowered to manage cybersecurity complexity. The McAfee® ePolicy Orchestrator® (McAfee ePO™) management platform removes the time-consuming and potential human error effort and inspires those responsible to manage security quicker and with higher efficacy. Fundamental Security Proven Advanced Security Management Start with the fundamentals. Core to any security More than 30,000 businesses and organizations trust architecture is the ability to monitor and control the the McAfee ePO console to manage security, streamline health of endpoints and systems. Industry standards and automate compliance processes, and increase such as Center for Internet Security (CIS) Controls and overall visibility across endpoint, network, and security National Institute of Standards Technology (NIST) SP operations. Big companies rely on the McAfee ePO 800 153 security and privacy controls call this out as console’s highly scalable architecture, allowing large a must. The McAfee ePO console allows you to gain enterprises to manage hundreds and thousands of critical visibility and set and automatically enforce nodes from a single console. The McAfee ePO console policies to ensure a healthy security posture across provides an enterprise security administrator with the your enterprise. Policy management and enforcement opportunity to simplify policy maintenance, pull in third- across security products for your entire enterprise party threat intelligence leveraging Data Exchange Layer is accomplished from a single console, removing the (DXL), and integrate policies bi-directionally with an array complexity of managing multiple products. -
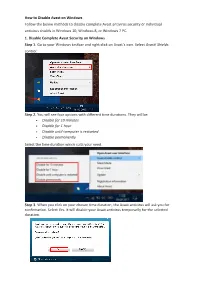
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Eset Endpoint Security
ESET ENDPOINT SECURITY User Guide Microsoft® Windows® 8 / 7 / Vista / XP / 2000 / Home Server Click here to download the most recent version of this document ESET ENDPOINT SECURITY Copyright ©2013 by ESET, spol. s r. o. ESET Endpoint Security was developed by ESET, spol. s r. o. For more information visit www.eset.com. All rights reserved. No part of this documentation may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise without permission in writing from the author. ESET, spol. s r. o. reserves the right to change any of the described application software without prior notice. Worldwide Customer Support: www.eset.com/support REV. 17. 4. 2013 Contents 4.2.1 Filt..e..r.i.n...g.. m....o..d..e..s............................................................44 1. ES.E..T. .E..n.d..p..o.i.n..t. .S.e..c.u..r.i.t.y.......................5 4.2.2 Fir.e..w...a..l.l. .p..r.o...f.i.l.e..s...........................................................45 4.2.3 Co.n..f..i.g..u..r.i.n...g.. a..n...d.. .u..s..i.n..g.. .r.u..l.e..s........................................46 1.1 Syste.m... .r.e..q.u..i.r.e..m...e.n..t.s..................................................5 4.2.3.1 Rules.. .s.e..t..u..p...................................................................47 1.2 Preve.n..t.i.o..n.................................................................5 4.2.3.2 Editin...g.. r..u..l.e..s.................................................................47 4.2.4 Co.n..f..i.g..u..r.i.n...g. -

Printmgr File
ˆ200F$l2ZLVgqon1gÈŠ 200F$l2ZLVgqon1g¨ VDI-W7-PR3-1248 SYMANTEC CORPORATION Donnelley Financial12.6.30 EGV yanns0ap24-May-2018 22:26 EST 594139 TX 1 2* SYMANTEC CORP PAL HTM ESS 0C Page 1 of 1 UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM SD SPECIALIZED DISCLOSURE REPORT Symantec Corporation (Exact Name of Registrant as Specified in its Charter) Delaware 000-17781 77-0181864 (State or other jurisdiction of (Commission (IRS Employer incorporation or organization ) File Number) Identification No.) 350 Ellis Street, Mountain View, California 94043 (Address of Principal Executive Offices) (Zip Code) Nicholas R. Noviello, Executive Vice President and Chief Financial Officer (650) 527-8000 (Name and telephone number, including area code, of the person to contact in connection with this report.) Not Applicable (Former Name or Former Address, if Changed Since Last Report) Check the appropriate box below to indicate the rule pursuant to which this form is being filed, and provide the period to which the information in this form applies: Rule 13p-1 under the Securities Exchange Act (17 CFR 240.13p-1) for the reporting period January 1 to December 31, 2017 ˆ200F$l2ZLVhV$Vk6$Š 200F$l2ZLVhV$Vk6$ VDI-W7-PFL-0639 SYMANTEC CORPORATION Donnelley Financial12.6.29 EGV ahern0ap24-May-2018 23:14 EST 594139 TX 2 3* SYMANTEC CORP PAL HTM ESS 0C Page 1 of 1 Item 1.01. Conflict Minerals Disclosure and Report. Conflict Minerals Disclosure A copy of the Conflict Minerals Report of Symantec Corporation (“Symantec”) for the reporting period January 1 to December 31, 2017 is filed as Exhibit 1.01 to this specialized disclosure report on Form SD and is also available at Symantec’s website at https://www.symantec.com/about/corporate-responsibility/resources/corporate-responsibility-policies .