Government-Wide Cyber Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2 | 2013 2 | Volume Issue ISSN 2190-3387 Law
2 | 2013 Volume 4 (2013) Issue 2 ISSN 2190-3387 Law and Electronic Commerce Information Technology, Intellectual Property, Journal of Articles Online Sexual Harassment: Issues & Solutions by Mohamed Chawki, Yassin el Shazly Breathing Space for Cloud-Based Business Models: Exploring the Matrix of Copyright Limitations, Safe Harbours and Injunctions by Martin Senftleben A Model Framework for publishing Grey Literature in Open Access by Matěj Myška, Jaromír Šavelka Injunctions against innocent Third Parties: The Case of Website Blocking by Martin Husovec Evaluation of the Role of Access Providers Discussion of Dutch Pirate Bay Case Law and Introducing Principles on Directness, Effectiveness, Costs, Relevance and Time by Arno R. Lodder, Nicole S. van der Meule Das Verhältnis zwischen Urheberrecht und Wissenschaft: Auf die Perspektive kommt es an! by Alexander Peukert Editors: Thomas Dreier Axel Metzger Gerald Spindler Lucie Guibault Miquel Peguera Journal of Intellectual Property, Information Technology and Table Of Contents Electronic Commerce Law Volume 4 Issue 2, August 2013 Articles www.jipitec.eu [email protected] Online Sexual Harassment: Issues & Solutions A joint publication of: by Mohamed Chawki, Yassin el Shazly 71 Prof. Dr. Thomas Dreier, M. C. J., Karlsruhe Institute of Technology, Vincenz-Prießnitz-Str. 3, Breathing Space for Cloud-Based Business Models: 76131 Karlsruhe Exploring the Matrix of Copyright Limitations, Safe Prof. Dr. Axel Metzger, LL. M., Harbours and Injunctions Exploring the Matrix of Institute for Legal Informatics, -

Net Neutrality Reloaded
Luca Belli Editor Net Neutrality Reloaded: Net Neutrality Reloaded: Zero Rating, Specialised Service, Ad Blocking and Traffic Management Zero Rating, Specialised Service, Annual Report of the UN IGF Dynamic Coalition on Net Neutrality Ad Blocking and Traffic Management Luca Belli Editor Annual Report of the UN IGF This Report is the 2016 outcome of the IGF Dynamic Coalition on Network Neutrality (DCNN). The Report gathers a series of case studies on a variety Dynamic Coalition of net neutrality issues from the perspective of different stakeholders. The double purpose of this report is to trigger meaningful discussion on net on Net Neutrality neutrality trends, while providing informative material that may be used by researchers, policy-makers and civil society alike. Researchers, practitioners and policy-makers regularly contribute to the DCNN report, providing a wide range of heterogeneous views. Preface by Tim Wu In 2016, Zero Rating was by large the most debated net neutrality issue, as reflected by the considerable number of contributions focusing on the topic within this report. Such high number of analyses on zero rating seems particularly useful to meet the increasing demand of research exploring the pros and cons of price discrimination practices. Furthermore, the report examines other very relevant and discussed topics, such as specialised services, ad blocking and reasonable traffic management, providing useful insight on some of the most recent policy evolutions in a variety of countries. Net Neutrality Reloaded: Zero Rating, -

Combating Spyware in the Enterprise.Pdf
www.dbebooks.com - Free Books & magazines Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fit the demands of our cus- tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you will find an assortment of value-added features such as free e-booklets related to the topic of this book, URLs of related Web site, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of exper- tise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE EBOOKS For readers who can’t wait for hard copy, we offer most of our titles in download- able Adobe PDF form. These eBooks are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our ebooks onto servers in corporations, educational institutions, and large organizations. -

Darknet As a Source of Cyber Threat Intelligence: Investigating Distributed and Reflection Denial of Service Attacks
Darknet as a Source of Cyber Threat Intelligence: Investigating Distributed and Reflection Denial of Service Attacks Claude Fachkha A Thesis in The Department of Electrical and Computer Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy at Concordia University Montreal, Quebec, Canada November 2015 c Claude Fachkha, 2015 CONCORDIA UNIVERSITY SCHOOL OF GRADUATE STUDIES This is to certify that the thesis prepared By: Claude Fachkha Darknet as a Source of Cyber Threat Intelligence: Entitled: Investigating Distributed and Reflection Denial of Service Attacks and submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy complies with the regulations of the University and meets the accepted standards with respect to originality and quality. Signed by the final examining committee: 'U'HERUDK'\VDUW*DOH Chair 'U0RKDPPDG=XONHUQLQH External Examiner 'U-RH\3DTXHW External to Program 'U5DFKLGD'VVRXOL Examiner 'U5RFK+*OLWKR Examiner 'U0RXUDG'HEEDEL Thesis Supervisor Approved by 'U$EGHO5D]LN6HEDN Chair of Department or Graduate Program Director 'U$PLU$VLI Dean of Faculty ABSTRACT Cyberspace has become a massive battlefield between computer criminals and com- puter security experts. In addition, large-scale cyber attacks have enormously ma- tured and became capable to generate, in a prompt manner, significant interruptions and damage to Internet resources and infrastructure. Denial of Service (DoS) attacks are perhaps the most prominent and severe types of such large-scale cyber attacks. Furthermore, the existence of widely available encryption and anonymity techniques greatly increases the difficulty of the surveillance and investigation of cyber attacks. In this context, the availability of relevant cyber monitoring is of paramount im- portance. -

DS0122 1007 FISE:DS0100 0605 FT EE.Qxd.Qxd
FaceTime Internet Security Edition™ Total Control for Web and Real-Time Internet Communications About FaceTime Internet Security FaceTime Internet Security Edition is the next generation Internet security solution, providing Edition total control over web usage and real-time communications. For the first time, enterprises FaceTime Internet Security Edition can enable, secure and manage all Internet channels – web browsing, IM, P2P, Skype, and enables the safe and productive use chat - with unified policy management through a single access point. FaceTime Internet of the Internet including web brows- Security Edition combines state-of-the-art IM & P2P security with an industry leading URL ing, IM, P2P, Skype and other real- filtering database and award winning gateway anti-spyware solution. time communications applications. Purpose-built and integrated to pro- Real-time Communications in the Enterprise vide total visibility and control, Internet communications have evolved from point-to-point channels such as email to real- FaceTime Internet Security Edition time, presence-oriented communications like IM, P2P file-sharing, Skype, and web confer- allows organizations to implement encing. For the new generation of workers, access to real-time communications is an powerful policies that detect, assumption; if it’s not available, they will download it to their computer regardless of policy, secure, manage and enable real- because they know what a positive impact these applications can have on effectiveness and time collaborative applications while efficiency. preventing malware threats, mini- mizing information leakage, and FaceTime terms these real-time communications applications ‘greynets’ – often installed by control employee Internet use. end users without the permission or knowledge of the IT department and use highly evasive techniques to circumvent the existing security infrastructure. -

Instructional Objectives
Information Security Governance & Compliance Assessment Essentials: Strategies for Staying Current with Technology Douglas Brown – CISM, CISSP, Security Solutions Architect HP Security and Risk Management HP Services © 2006 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice Instructional objectives • Share enabling technologies taxonomy as it applies to the P5 Model • Familiarize one’s self with common technologies encountered during security engagements • Understand HP’s security product portfolio • Understand HP’s strategy in selecting and aligning with 3rd party partners • Know where to go for “quick” education on security tools 5/25/2007 2 1 Agenda • Assessing technology controls • Technology types • Emerging technologies • Enabling technologies • Applying enabling technologies • HP security technologies • Consultant resources • Security technology predictions • Breakout 5/25/2007 3 Assessing Technology Controls © 2006 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice 2 Assessing technology controls • Role and responsibility − Understand technology in place to manage/mitigate threats • Why are they using it? • How are they using it? • How could they use it better? − Recognize that you won’t know every technology in use • Clients expect us to know every single tool as an expert • Use probing questions to mask lack of awareness of a particular technology 5/25/2007 5 Technology ecosystem Firewall Rules Management What -

Understanding Packet Voice Protocols
Understanding Packet Voice Protocols Introduction Over the past decade, the telecommunications industry has witnessed rapid changes in the way people and organizations communicate. Many of these changes spring from the explosive growth of the Internet and from applications based on the Internet Protocol (IP). The Internet has become a ubiquitous means of communication, and the total amount of packet-based network traffic has quickly surpassed traditional voice (circuit-switched) network traffic (DataQuest, 1998). In the wake of these technology advancements, it has become clear to telecommunications carriers, companies, and vendors that voice traffic and services will be one of the next major applications to take full advantage of IP. This expectation is based on the impact of a new set of technologies generally referred to as voice over IP (VoIP) or IP telephony. VoIP supplies many unique capabilities to the carriers and customers who depend on IP or other packet-based networks. The most important benefits include the following: · Cost Savings: By moving voice traffic to IP networks, companies can reduce or eliminate the toll charges associated with transporting calls over the public switched telephone network (PSTN). Service providers and end users can also conserve bandwidth by investing in additional capacity only when it is needed. This is made possible by the distributed nature of VoIP and by reduced operations costs as companies combine voice and data traffic onto one network. · Open Standards and Multivendor Interoperability: By adopting open standards, both businesses and service providers can purchase equipment from multiple vendors and eliminate their dependency on proprietary solutions. · Integrated Voice and Data Networks: By making voice "just another IP application," companies can build truly integrated networks for voice and data. -

OSINT Handbook September 2020
OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 Aleksandra Bielska Noa Rebecca Kurz, Yves Baumgartner, Vytenis Benetis 2 Foreword I am delighted to share with you the 2020 edition of the OSINT Tools and Resources Handbook. Once again, the Handbook has been revised and updated to reflect the evolution of this discipline, and the many strategic, operational and technical challenges OSINT practitioners have to grapple with. Given the speed of change on the web, some might question the wisdom of pulling together such a resource. What’s wrong with the Top 10 tools, or the Top 100? There are only so many resources one can bookmark after all. Such arguments are not without merit. My fear, however, is that they are also shortsighted. I offer four reasons why. To begin, a shortlist betrays the widening spectrum of OSINT practice. Whereas OSINT was once the preserve of analysts working in national security, it now embraces a growing class of professionals in fields as diverse as journalism, cybersecurity, investment research, crisis management and human rights. A limited toolkit can never satisfy all of these constituencies. Second, a good OSINT practitioner is someone who is comfortable working with different tools, sources and collection strategies. The temptation toward narrow specialisation in OSINT is one that has to be resisted. Why? Because no research task is ever as tidy as the customer’s requirements are likely to suggest. Third, is the inevitable realisation that good tool awareness is equivalent to good source awareness. Indeed, the right tool can determine whether you harvest the right information. -

Using Social Media and Social Network Analysis in Law Enforcement
C O R P O R A T I O N Using Social Media and Social Network Analysis in Law Enforcement Creating a Research Agenda, Including Business Cases, Protections, and Technology Needs John S. Hollywood, Michael J. D. Vermeer, Dulani Woods, Sean E. Goodison, Brian A. Jackson n April 2017, the National Institute of Justice convened an expert panel to assess, and identify high-priority needs Key Findings for, law enforcement’s use of two closely linked tech- nologies that have potential to provide key information • Expert panelists characterized business cases for employing social Ineeded to address crime risks, hold offenders accountable, media and social network analysis in law enforcement, including and ensure physical safety: social media analysis and social monitoring for short-term safety threats in postings; identifying network analysis. Social media analysis consists of meth- those at high risk of involvement in violence, either acutely or ods and tools to collect and analyze text, photos, video, chronically; and investigating specific crimes and organized crime and other material shared via social media systems, such networks. as Facebook and Twitter. Social network analysis is a type of data analysis that investigates social relationships and • The panel also specified a core case not to do: monitoring of First structures as represented by networks (which can also be Amendment–protected activity for vague purposes. called graphs). Social media, given that it reflects relation- • The panel specified a framework for providing computer security, ships inherently, is a key source of data for social network privacy, and civil rights protections when employing social media analysis; conversely, social network analysis is one key type and social network analysis. -
The Development of Deep Packet Inspection Platform and Its Applications
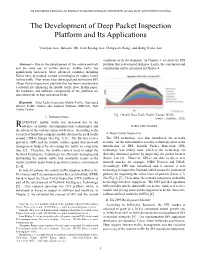
3rd International Conference on Intelligent Computational Systems (ICICS'2013) January 26-27, 2013 Hong Kong (China) The Development of Deep Packet Inspection Platform and Its Applications Yoonjae. Lee, Junseok. Oh, Joon Kyung. Lee, Dongwon. Kang, and Bong Gyou. Lee conditions of its development. In Chapter 3, we show the DPI Abstract— Due to the development of the mobile network platform that is developed in Korea. Lastly, the conclusion and and the wide use of mobile devices, mobile traffic has contribution will be presented in Chapter 4. significantly increased. Most advanced countries including Korea have developed various technologies to reduce heavy mobile traffic. This research has developed and utilized the DPI (Deep Packet Inspection) platform that has been considered as a solution for enhancing the mobile traffic flow. In this paper, the hardware and software components of the platform are described with its four utilization fields. Keywords—Deep Packet Inspection, Mobile Traffic, High-speed Internet Traffic Control and Analysis Platform (HITCAP), Data Traffic Control Fig. 1 Mobile Data Traffic Profile (Europe, Wi-Fi) I. INTRODUCTION (Source: Sandvine, 2012) ECENTLY, mobile traffic has increased due to the R advance of mobile telecommunication technologies and II. RELATED WORKS the advent of the various connected devices. According to the research of Sandvine company, mobile data has the peak traffic A. Deep Packet Inspection around 2 PM in Europe (See Fig. 1) [1]. The Internet service The DPI technology was first introduced for network providers (ISP) and the mobile carriers spend their network security. As the representative security technology prior to the management budgets by decreasing the traffic in congestion introduction of DPI, Stateful Packet Inspection (SPI) time [2]. -

Optimal Techn Ology G Uidance
Report Comprehensive Information Technology Assessment August 10, 2016 Optimal TechnologyOptimal Guidance Optimal Technology Guidance Technology Optimal Client Locations Coast-to-Coast Practice Locations California Illinois Minnesota North Carolina 800.806.3080 www.clientfirstcg.com Comprehensive IT Assessment Report City of West Covina, CA TABLE OF CONTENTS ENGAGEMENT PURPOSE AND BACKGROUND ............................................ 3 Comprehensive Information Technology Assessment Objective ......................................... 3 Deliverables ........................................................................................................................... 3 Methodology and Approach .................................................................................................. 4 CURRENT INFORMATION TECHNOLOGY ENVIRONMENT SUMMARY .............. 5 Summary IT Environment ..................................................................................................... 5 Key Statistics and Metrics ..................................................................................................... 6 IT STRATEGIES, GOALS, AND OBJECTIVES ............................................ 10 INFORMATION TECHNOLOGY (IT) PRINCIPLES ......................................... 13 Vision / Mission Statement .................................................................................................. 13 IT INITIATIVES ...................................................................................... 14 Introduction ......................................................................................................................... -

Warren Harrop Thesis
Using immersive real-time collaboration environments to manage IP networks A thesis submitted for the degree of Doctor of Philosophy Warren Harrop, BEng(Hons)(Telecommunications and Internet Technologies) & BAppSc(Multimedia Technologies) (Swinburne University), Centre for Advanced Internet Architectures, Faculty of Science, Engineering and Technology, Swinburne University of Technology, Melbourne, Victoria, Australia. August 21, 2014 Declaration This thesis contains no material which has been accepted for the award to the candidate of any other degree or diploma, except where due reference is made in the text of the examinable outcome. To the best of the candidate’s knowledge this thesis contains no material previously published or written by another person except where due reference is made in the text of the examinable outcome; and where the work is based on joint research or publications, discloses the relative contributions of the respective workers or authors. Warren Harrop Centre for Advanced Internet Architectures (CAIA) - Faculty of Science, Engineering and Technology Swinburne University of Technology August 21, 2014 iii Publications arising from this thesis Some preliminary results and discussions in this thesis have been previously published in peer- reviewed literature: W. Harrop and G. Armitage, “Intuitive Real-Time Network Monitoring Using Visually Orthog- onal 3D Metaphors,” in Australian Telecommunications Networks & Applications Conference 2004 (ATNAC 2004), Sydney, Australia, 8-10 December 2004, pp. 276–282. [Online]. Available: http: //caia.swin.edu.au/pubs/ATNAC04/harrop-armitage-ATNAC2004.pdf W. Harrop and G. Armitage, “Modifying first person shooter games to perform real time network monitoring and control tasks,” in NetGames ’06: Proceedings of 5th ACM SIGCOMM workshop on Network and system support for games.