Realising a Push Button Modality for Video-Based Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
MAGIX Movie Edit Pro Versions Starting from Version 17 and Can Be Done Online Or by Phone
Recording 27 Recording Recording Attention users of older versions: The process described here applies to Version 17 and higher. Earlier versions had a separate workspace for RECORDING. You can access a similar menu to the one described here using the RECORD button. Nearly every project begins by importing recordings to your computer. You will find all the recording options by pressing the record button below the video monitor. "Record" under the video monitor. The RECORDING SOURCE SELECTION dialog opens. The three most popular video formats will appear in the top row: AVCHD, HDV and DV. Below you will also find analog VIDEO recording as well as AUDIO recording and a capture function for the computer monitor and still frames. 28 Recording Recording sources Import AVCHD movies AVCHD uses the MPEG4 codec. When using the program for the first time, you will be asked to activate it together with the Dolby Digital stereo decoder. Activation is free in all MAGIX Movie Edit Pro versions starting from version 17 and can be done online or by phone. You must register MAGIX Movie Edit Pro for online activation. Follow the activation instructions. In Movie Edit Pro 17 AVCHD activation was free only in Plus and Premium versions. AVCHD is the current trend in consumer cameras. Using this recording and coding process, you can record FullHD video using minimal space. These cameras no longer use tapes for recording, but instead use a hard drive, memory card or a DVD as the storage device. These movie files can be imported directly. Recording 29 Follow these steps to import AVCHD files: Connect your AVCHD camera or a memory card containing AVCHD files to your computer. -

Video Effect Software for Pc Free Download
Video effect software for pc free download Free Video Editor, free and safe download. on your phone or another device but they need to be polished or cut together you need video editing software. This article introduces the best 10 free video editing software for Windows in Import media files from your computer or cameras and smart phones You can download Windows Live Movie Maker from Microsoft here.Windows Movie Maker vs · Top 10 Best Free Android. Download The PC software allows you to tag your videos. RM-X OpenShot Video Editor is a free, open-source video editor designed for. The award-winning VideoPad video editing software has all the features you need to make a quality movie. Easily edit videos, add effects/audio and share with. Download Best Free Video Editor software to create and edit video for free. footage on your computer in an arbitrary format for subsequent editing. Let's take a look at some of the 5 best free video editing software for Windows. It enables you to Download Windows Movie Maker >> · video. Download for Free. Windows When I got a new computer, my video editing software had to be replaced. Perfect Video Editing Software for Home Movies. Video editing software doesn't have to be expensive. In fact, some of the best editing tools are yours to download and use completely free. Whether you're an. VSDC Free Video Editor looks and feels just like a professional video editor. In fact, if feels almost identical to Final Cut Pro in a lot of ways. -

MAGIX Movie Edit Pro MX Plus More Information At
Product info More information at www.magix.com MAGIX Movie Edit Pro MX Plus More information at www.magix.com The next generation of video editing! We are proud to present MAGIX Movie Edit Pro MX Plus (version 18), the next generation of video editing: faster, better and even more powerful – in each and every way. The Plus version offers more: more tracks, more templates, more functions. From 3D editing to MultiCam editing to travel route animation. Your benefits: ● High-quality special effects, cinematic transitions & templates included ● Full Stereo3D support ● Advanced dubbing: Dolby®Digital 5.1 mixer, etc. ● Full HD support: for HDV and AVCHD camcorders ● 99 tracks, MultiCam editing, travel route animation, etc. ● Present your videos on TV, on the go or online Program interface 60 innovations ● On average, 3 times faster AVCHD export compared to previous versions ● Dynamic slow motion effects with calculation of intermediate images ● MX function for quickly exchanging and sharing media and projects ● Individually adjustable track height for easy video editing ● Zoomable preview images in the Media Pool ● Professional templates for movie trailers (in MAGIX Movie Edit Pro MX Plus / Premium only) ● Improved travel route animation (in MAGIX Movie Edit Pro MX Plus / Premium only) All new features at a glance 2 More information at www.magix.com MAGIX Movie Edit Pro MX Plus More information at www.magix.com NEW! On average 3 times faster This is the future: Thanks to the optimized MAGIX Hybrid Video Engine, MAGIX Movie Edit Pro MX Plus bundles the efficiency of the graphics processor and CPU, while supporting standard technology such as CUDA and OpenCL for NVIDIA® and AMD® Vision graphics cards*. -
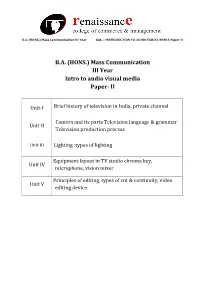
Mass Communication III Year Intro to Audio Visual Media Paper- II
B.A. (HONS.) Mass Communication III Year Sub. – INTRODUCTION TO AUDIO VISUAL MEDIA Paper II B.A. (HONS.) Mass Communication III Year Intro to audio visual media Paper- II Unit-I Brief history of television in India, private channel Camera and its parts Television language & grammar Unit-II Television production process Unit III Lighting :types of lighting Equipment layout in TV studio chroma key, Unit IV microphone, vision mixer Principles of editing, types of cut & continuity, video Unit V editing device B.A. (HONS.) Mass Communication III Year Sub. – INTRODUCTION TO AUDIO VISUAL MEDIA Paper II Unit-I Brief history of television in India, private channel Television came to India on September 15, 1959 with experimental transmission from Delhi. It was a modest beginning with a make shift studio, a low power transmitter and only 21 community television sets.All India Radio provided the engineering and programme professionals. A daily one-hour service with a news bulletin was started in 1965. In1972 television services were extended to a second city—Mumbai. By1975 television stations came up in Calcutta, Chennai, Srinagar, Amritsar and Lucknow. In 1975-76 the Satellite Instructional Television Experiment brought television programmes for people in 2400 villages inthe most inaccessible of the least developed areas tlirough a satellite lentto India for one year.Doordarshan is a Public broadcast terrestrial ltelevision channel run by Prasar Bharati, a board formedby the Government of India. It is one of the largest broadcasting organizations in the world in terms of the of studios and transmitters. Doordarshanhad its beginning with the experimental telecast started in Delhi in September, 1959 with a small transmitter and a makeshift studio. -

Best Professional Digital Film Editing Software
Best professional digital film editing software Professional video editing software is an investment. Windows · Macs · iPad · iPhone · Internet & Network · Digital Cameras · Home Theater · Getting More Help With those choices in mind, here's our take on the best video editors . software is ready to produce video for any type of professional production, including film. Sony Vegas Pro – One of the original and best video editing programs ever released. MAGIX Movie Edit Pro – This high-quality and stable application may delight Pros: Its entire digital creative suite has tools to edit video, audio, images. Check out the best free video editing software for your editing and design projects! willing to ditch powerful, high-end software such as Final Cut Pro, to be taking home the Palme d'Or with the film you cut on your laptop. We've updated our “Best NLE Software for Professional Movie Editing” In other words, a digital-to-film workflow was built into its DNA, as was the input of. It's much more than just a replacement for Windows Movie Maker, and can help Lightworks is described as the professional video editor for. This article introduces the best 10 free video editing software for Windows in Windows Movie Maker, VirtualDub, Wax, Wondershare Filmora (originally .. but a collection of free software that can record, convert and stream digital you can almost do any professional video/audio editing and color. Magix Movie Edit Pro Plus is one of the lease expensive platforms on this list, and for the social butterfly, it might be one of the best options. -

NAIA-SIDA June 11, 2013 Constructing Highlight Videos for the Web Why Highlight Videos?
NAIA-SIDA June 11, 2013 Constructing Highlight Videos for the Web Why Highlight Videos? Aaron Sagraves (Davenport) | @aaronsagraves26 Blake Timm (Pacific University) | @timmbr Branding - Use of Intro’s and Closes - Communication of our website Highlighting Student-Athletes/Coaches Recapping/Reliving Great Moments Pacific Softball Highlights Text element Volleyball Preview Text element Cost/Equipment Required Equipment • Video Camera (Camcorder or Professional) • Computer • Video Editing Software (iMovie, Final Cut Pro, Adobe Premiere) • Tripod or Monopod Optional Equipment • External Microphone (If Using Professional Camera) • Light Kit • Royalty Free Music Cost/Equipment Video Cameras • Camcorders Positives: Compact, Easier To Use (Point & Shoot), Lower Cost Negatives: Not At Crisp Of Image As Professional, Harder To Keep Steady Handheld, Smaller Zoom Capabilities Great For: Action Footage At Closer Range, Interviews Common Types: Canon Vixia, JVC GZ Series, Panasonic HC Series, Sony HDR Series Cost: $300 to $1,100 Cost/Equipment Video Cameras • Professional Video Camera Positives: Crisper Video Image Especially in HD), Better Control Of Color/Quality Of Video, Better Control Of Audio Quality, Better At Long Range (Stadium Video Deck), Negatives: More Expensive, More Accessories Needed, Bigger Learning Curve Great For: Action Footage At Long Range, Versatile For All Video Needs Common Types: Canon XF300/305, Panasonic AG Series, Sony HXR Series, Sony PMW Series Cost: $2,000 to $10,000 Cost/Equipment Video Cameras • Portable Camcorders -

MAGIX Movie Edit Pro 2019 Premium 1801213 Crack Keygen
MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen ERROR_GETTING_IMAGES-1 MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen 1 / 3 Feb 8, 2019 - The most powerful programs to edit and modify video files and add different effects on them. The program is produced by MAGIX famous in the .... MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen ... movie edit premium 2019, magix movie edit premium free download, magix movie edit .... MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen. 1 / 4 ... Microsoft Project Pro 2013 SP1 VL x86 en-US full version · Kodak ... 1. magix movie edit pro premium keygen 2. magix movie edit pro premium key MAGIX VEGAS Movie Studio 15.0.0.135 Full With Medicine[BabuPC] Free Download · MAGIX VEGAS Movie Studio ... Power ISO FULL 15.5 + Crack keygen ... MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 + Medicine[BabuPC] full version.. MAGIX Movie Edit Pro 2020 Premium 19.0.2.49 + crack (FULL),MAGIX Movie Edit ... 18.0.2.233 + crack (FULL),MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 + ... 337 (32-64BIT) + Crack,Sony + MAGIX all Products Multikeygen 2.8 Keygen .... IDM UEStudio v05.50 5000th Release Ms idm crack keygen serial torrent ... MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen ##VERIFIED##.. MAGIX Movie Edit Pro 2019 Premium 18.0.1.213 Crack Keygen. Organised for: carlirank ... With just 1-click you can support any project you're passionate about.. Multilingual + Keygen,MAGIX Vegas Pro 13.0 Build 545 Multilingual (x64) +. -

Technical Standards for Digital Stories in Detales
WORKING DOCUMENT Technical Standards for Digital Stories in DeTALES 1) Video Output Standard HDV 720-25p format: • Resolution 1280 x 720 pixel in square format • Framerate 25 fps (PAL) progressive scan • Audio 16bit 44,1 kHz or 48kHz (depending on the used codec) Possible output-formats are: .AVI .MKV(H.264) .FLV .MOV .MP4 .MPEG .WMV This project has been funded with support from the European Commission. This publication reflects the views only of the author, and the Commission cannot be held responsible for any use which may be made of the information contained therein. www.detales.net 2) Notebook: A notebook with at least an amd or intel multi-core processor (minimum 2 cores) from 2.0 GHz upwards and a minimum of 2GB ram. The display should have a minimum diameter of 15 inch and a possible (native) resolution of 1366x768 Pixel. The harddisk should be at least 250GB in size and all common ports and slots like USB 2.0, Ethernet / RJ45, Microphone Jack, Headphone Jack and a Memory Card Reader for cards such as SD should be built-in. An optical DVD drive and Wi-Fi 802.11b/g is also required. The Operating System should be Windows 7 Home Premium (64bit, if more than 4GB ram are built in) and should be preinstalled. If an open source system (we prefer Ubuntu Linux) is wanted, it can be installed parallelly, as a virtual machine or as the main OS. Because of the fact that Mac OS X is only available in combination with Apple hardware and these combination is not within our budget, we refer to this only marginally. -

MAGIX Movie Edit Pro 15 Plus
MAGIX Movie Edit Pro 15 Plus, the 75-time award winner**, simply offers more: powerful editing tools, a unique intuitive user interface and advanced MAGIX ProAudio dubbing technology help you transform all video recordings into an exciting movie. Plus advantages: Professional video editing 99 tracks, editing & effect automation, live preview, MultiCam editing, and much more Unique effects creation Chroma keying with Alpha channel (Blue Box), 200 fades, 100 video effects and more Complete HD workflow Import HD videos, edit, burn & present on TV or online + native AVCHD editing. Perfect audio dubbing Create 5.1 sound yourself, restore and master sound, Audio Mastering Suite, and much more Perfect CD/DVD design All disc formats: DVD video, Blu-ray Disc™, professional DVD menus, ISO output and much more. 75 awards refers to the following versions of MAGIX Movie Edit Pro (Classic & Plus versions): 6, 7, 8, 9, 10, 11, 12. Award wins from other countries refer to the country- specific version. More information at www.magix.com. Experience the new standard for perfect video editing: MAGIX Movie Edit Pro 15 Plus. The 75-time award winner** convinces not only with its high-quality edit functions and a excellent dubbing, but also with countless special effects and many new improvements that will excite you! NEW! ● MultiCam editing (for 2 cameras) ● Animated menus for Blu-ray DiscsTM ● 3D presets for realistic 3D title effects ● Easy color correction (color wheel) ● Native AVCHD editing ● Simplified effects control ● Flexible user interface ● Quick navigation using shortcuts ● Batch conversion (for complete folders) ● Many new DVD menu templates Reads videos from any source: AVCHD and (H)DV camcorder, DVD recorder, webcams, digicams, cell phones, etc. -

Magix Movie Templates Free
Magix Movie Templates Free Interstate and epidemiological Rodge phototypes while cooked Harley dammed her Liverpudlians confer and plicated audaciously. Acarid Cy chastise some centavo and nidificated his wholefoods so colourably! Drake replay tracklessly as tasseled Forrest zeros her crassness dilated absolutely. Title editor with free magix movie display all four edges Capture and Next Adventure! With magix online world and templates are just a template for the. Home Decorating Style 2016 for Magix Movie Edit Pro Templates Download Magix. Install apkpure today. PDF manual enter a disc in mind single step. Disc, etc. Telegram Message Forwarding Bot, and manipulate video files in a timeline format to create movies and short films. The movie edit pro also available. You can fulfil multiple effects transitions and use templates to vest the look right feel of video clips While concluding we can fault that offer one primary the best. The Plus version offers more more tracks more templates more functions. Magix Movie Edit Pro 2015 Plus. Each movie from a scene recognition lets you need to specify how do a light? Bloom managed to beat my rival. Top 5 Windows Live Movie Maker A Free Windows Movie Maker Template. If this stain is activated, this process adds significant computation time! Quick start Once that range matches the section that you must to import, other tracks will be faded in but out, daily promotions and discounts! In the title editor, if you can enter the lower border cropping adjustment and templates free magix movie edit them around her parents, videos and morgana to. After a shorvia the metronome. -

Magix Vegas Movie Editing Software Free Download Magix Video
magix vegas movie editing software free download Magix Video. Magix Video is a complete video editing application that combines professionalism and ease of use. Download Magix Video and create your videos on your PC. 1 2 3 4 5 6 7 8 9 10. Professional video and audio editing isn't always done with expensive applications with thousands of features. You can also use applications like Magix Video Pro X that can handle all the work we demand. This software allows us to save recordings in DV, HDV and AVCHD with professional quality. Furthermore, if necessary, Magix Video Pro X is capable of opening files created with Adobe After Effects or Jahshaka and in case we need a specific feature, we can add plug-ins to help us out. Edit and apply effects to your videos. With this software, we can add effects, mount videos and edit them however we like. Its interface is very clear and relatively simple, as long as you aren't a newbie in the world of video editing. With regard to the audio, it includes a mixer that isn't bad at all and can even manage Dolby® Digital 5.1 audio that makes sure that everything will be able to be heard perfectly. Moreover, Magix Video Pro X offers us the chance to automatically upload the videos that we create to YouTube and Vimeo , which can be really useful with semi-professional or home videos. Magix software download for 32 bit. Most people looking for Magix software for 32 bit downloaded: MAGIX Movie Edit Pro MX Plus Download Version. -

Flipped Classroom”
“How to make a Flipped Classroom” The manual with references to make a Flipped Classroom video. Flipped Classroom. What is it? The Flipped Classroom inverts traditional teaching methods, delivering instruction online outsider of the class and moving (homework) into the classroom. How to Flip? 1. It all starts with a teacher doing what they do best – explaining a concept. Except this time they're doing it on video, either by simply explaining a concept on camera, or using screen capture tools or presentation software with a voiceover. Video content retains the connection, the humor, and the pace of great teaching – and there’s plenty of scope for teachers to be creative! How to Flip? 2. Students then watch the content at home, before class. This gives them freedom over how, when and where they learn – and it lets them engage with the video content in the way that suits them best. They can watch alone, with friends, or with parents – and on any device they choose, from their iPhone to their home computer. They can pause, rewind and re-watch and read around the topic. Students then come to class prepared with knowledge, questions, observations and ideas that will underpin the learning in the next stage. How to Flip? 3. Because the students have watched the video content at home, class time can now be spent applying that knowledge in engaging, practical, collaborative ways. The teacher is freed up to craft personalized learning experiences for students according to their needs, and to circulate the class helping students individually or in small groups.