Cells: a Virtual Mobile Smartphone Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -
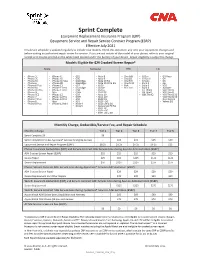
Sprint Complete
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) Effective July 2021 This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair* Apple Samsung HTC LG • iPhone 5 • iPhone X • GS5 • Note 8 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone XS • GS6 • Note 9 • One E8 • G Flex II • G4 • iPhone 5S • iPhone XS Max • GS6 Edge • Note 20 5G • One M9 • G Stylo • G5 • iPhone 6 • iPhone XR • GS6 Edge+ • Note 20 Ultra 5G • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 11 • GS7 • GS10 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone 11 Pro • GS7 Edge • GS10e • HTC U11 • Stylo 6 • X power • iPhone 6S Plus • iPhone 11 Pro • GS8 • GS10+ • G7 ThinQ • V40 ThinQ • iPhone SE Max • GS8+ • GS10 5G • G8 ThinQ • V50 ThinQ • iPhone SE2 • iPhone 12 • GS9 • Note 10 • G8X ThinQ • V60 ThinQ 5G • iPhone 7 • iPhone 12 Pro • GS9+ • Note 10+ • V60 ThinQ 5G • iPhone 7 Plus • iPhone 12 Pro • A50 • GS20 5G Dual Screen • iPhone 8 Max • A51 • GS20+ 5G • Velvet 5G • iPhone 8 Plus • iPhone 12 Mini • Note 4 • GS20 Ultra 5G • Note 5 • Galaxy S20 FE 5G • GS21 5G • GS21+ 5G • GS21 Ultra 5G Monthly Charge, Deductible/Service Fee, and Repair Schedule -

Android Support for Microsoft Exchange in Pure Google Devices
Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of these pure Google devices running Android. Android support by version and device The following AndroidTM versions support Microsoft Exchange information services and security policies: ● Android 4.0.4 (Ice Cream Sandwich) ● Android 4.1 and later (Jelly Bean) The following “pure Google” devices support the Microsoft Exchange services and policies: ● Galaxy Nexus phones running Android ● Nexus S phones running Android ● Motorola Xoom tablets running Android ● Nexus 4 phones running Android ● Nexus 7 tablets running Android ● Nexus 10 tablets running Android Requirements To support Android 4.0 running on pure Google devices, you must be running one of the following versions of Microsoft Exchange: ● Exchange Server 2010 SP1 with Exchange ActiveSync 14.1 ● Exchange Server 2010 with Exchange ActiveSync 14.0 ● Exchange Server 2007 SP1 with Exchange ActiveSync 12.1 ● Exchange Server 2007 with Exchange ActiveSync 12.0 ● Exchange Server 2003 SP2 with Exchange ActiveSync 2.5 The following information applies to the Android platform, including the Settings, Email, Calendar, People, and related apps as built by Google. If a device manufacturer has modified these apps on its own devices, contact the manufacturer for information about support for Exchange features. Supported information services Users can add Microsoft Exchange accounts to their pure Google devices by using the Account & Sync settings available from the Settings or Email app. Android supports the following Exchange information services: ● Adding Exchange user accounts (via an ActiveSync server), and enforcement of some mailbox policies (as described in “Supported security policies,” next). -

Udynamo Compatibility List
uDynamo Compatibility List Reader Manuf. Device Name Alt. Model Info Model Info OS OS Version Carrier Date Added Date Tested Type iDynamo 5 Apple iPad Air 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad Air* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad with Retina Display* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 3 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPhone 5c* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5s* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPod touch (5th* generation) Lightning N/A iOS N/A N/A iPod iDynamo 5 Apple iPhone 6* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 6 Plus* Lightning N/A iOS N/A N/A Phone iDynamo Apple iPad (3rd generation) 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 2 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPhone 4s 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 4 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 3GS 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPod touch (3rd and 4th generation) 30 PIN N/A iOS N/A N/A iPod uDynamo Acer liquid MT liquid MT Android 2.3.6 101.18 1/24/14 1/24/14 uDynamo Alcatel Alcatel OneTouch Fierce 7024W Android 4.2.2 101.18 3/6/14 3/6/14 uDynamo ALCATEL Megane ALCATEL ONE TOUCH 5020T Android 4.1.2 101.18 8/10/15 8/10/15 uDynamo ALCATEL ALCATEL ONE TOUCH IDOL X ALCATEL -

Android Software Platform Development at Fujitsu
Android Software Platform Development at Fujitsu Makoto Honda Makoto Kobayashi Masahiko Nagumo Yasuhiro Kawakatsu Smartphones using the Android platform first appeared on the market in October 2008. They have since overtaken Apple’s iPhone—the first entry in the smartphone market—in number of units shipped and have helped to bring about major changes in the way that mobile phones are used. Android was developed and is distributed as open source software that a device maker integrates into its own hardware after adding original software technologies. The Android platform evolves in short cycles on the basis of software and hardware developments as the network infrastructure continues to expand in the form of WiMAX and LTE and as usage scenarios and services become increasingly diverse. Fujitsu has been developing Android smartphones with compelling functions and enhanced convenience since December 2010, when it released the REGZA Phone T-01C featuring a water-resistant enclosure, one-seg support, and FeliCa contactless IC card and infrared-communication functions. This paper describes Fujitsu’s approach to smartphone development, focusing on memory management and current-con- sumption management as important elements in the system design of the Android software platform, diverse manner modes for enhancing user convenience, high-picture-quality technol- ogy achieved by using the Mobile REGZA Engine, and audio-visual device-linking technology based on DLNA standards. 1. Introduction and Internet services, the smartphone market share of November 2007 marked the establishment of the Android devices continued to grow, and in fiscal 2011, Open Handset Alliance (OHA) centered about Google it came to exceed 50%. -
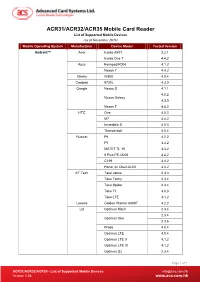
Supported Mobile Devices of Acr3x Swipe Card Reader
ACR31/ACR32/ACR35 Mobile Card Reader List of Supported Mobile Devices (as of November 2016) Mobile Operating System Manufacturer Device Model Tested Version Android™ Acer Iconia A501 3.2.1 Iconia One 7 4.4.2 Asus Fonepad K004 4.1.2 Nexus 7 4.4.2 Cherry W500 4.0.4 Coolpad 8730L 4.3.0 Google Nexus S 4.1.1 4.0.2 Nexus Galaxy 4.3.0 Nexus 7 4.4.2 HTC One 4.0.3 M7 4.4.2 Incredible S 4.0.3 Thunderbolt 4.0.4 Huawei P6 4.2.2 P7 4.4.2 MATE7 TL 10 4.4.2 6 Plus PE-UL00 4.4.2 C199 4.4.2 Honor 4x Che2-UL00 4.4.2 KT Tech Take Janus 2.3.3 Take Tachy 2.3.4 Take Spider 2.3.4 Take Fit 4.0.3 Take LTE 4.1.2 Lenovo Golden Warrior A808T 4.2.2 LG Optimus Mach 2.3.4 2.3.4 Optimus One 2.3.6 Prada 4.0.4 Optimus LTE 4.0.4 Optimus LTE II 4.1.2 Optimus LTE III 4.1.2 Optimus Q2 2.3.4 Page 1 of 7 www.acs.com ACR31/ACR32/ACR35 - List of Supported Mobile Devices [email protected] .hk Version 1.08 www.acs.com.hk Mobile Operating System Manufacturer Device Model Tested Version Optimus Big 4.0.4 2.3.4 Optimus Ex 4.0.4 Optimus LTE TAG 4.0.4 4.0.4 Optimus G 4.1.2 4.4.2 4.0.4 Optimus Vu 4.1.2 4.1.2 Optimus Vu II 4.2.2 4.4.2 4.2.2 Optimus Vu III 4.4.2 4.1.2 G Pro 4.4.2 G Pro 2 4.4.2 4.1.2 Optimus GX 4.4.2 4.2.2 Optimus G2 4.4.2 5.0.1 4.4.2 G3 5.0.0 4.4.2 G3 Cat6 5.0.1 G3 Screen 4.4.4 G4 5.1.0 4.2.2 G FLEX 4.4.2 G FLEX 2 5.1.1 Volt 5.0.2 Band Play 5.1.1 Gentle 5.1.1 V10 5.1.1 Class 5.1.1 Tab 8.4 4.2.2 Page 2 of 7 www.acs.com ACR31/ACR32/ACR35 - List of Supported Mobile Devices [email protected] .hk Version 1.08 www.acs.com.hk Mobile Operating System Manufacturer Device Model Tested -

Owner's Guide
Owner’s Guide 22 Legal Copyright © 2011 Google Inc. All rights reserved. Google, the stylized Google logo, Android, the stylized Android logo, Nexus, the stylized Nexus logo, Nexus S, and the stylized Nexus S logo, are trademarks of Google Inc. All other company and product names may be trademarks of the companies with which they are associated. Availability of Google applications, services, and features may vary by country, carrier, and manufacturer. For more information about your Nexus S phone, visit http://www.nexusshelp.com. Nexus S Owner’s Guide Nexus S Owner’s Guide 33 Contents Contents 3 Your phone and accessories 4 What’s in the box 5 Getting to know your phone 6 Installing the battery, and SIM card 7 Open the phone’s back cover 7 Replace the phone’s back cover 8 Remove or insert the battery 8 Remove or insert a SIM card 10 Charging your phone 11 Charge the phone 11 Using the headset 12 Turning the phone on and off 13 Turn on the phone 13 Unblock a SIM 14 Turn off the phone 14 Nexus S Owner’s Guide Nexus S Owner’s Guide Your phone and accessories 44 Your phone and accessories Your Google™ Nexus S™ phone comes with a number of accessories, including a headset, USB cable, and charger. For safety reasons, the battery is not shipped inside the phone, so you need to insert it and charge it fully before using your phone. This guide describes the parts of your phone, how to install and charge the battery, how to turn the phone on and off, and other useful information. -
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -
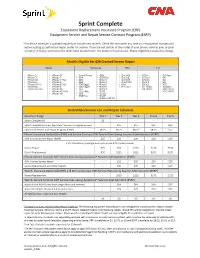
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP)
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair Apple Samsung HTC LG • iPhone 5 • iPhone SE • Grand Prime • GS9 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone 7 • GS4 • GS9 Plus • One E8 • G Flex II • G4 • iPhone 5S • iPhone 7 Plus • GS5 • Note 3 • One M9 • G Stylo • G5 • iPhone 6 • iPhone 8 • GS6 • Note 4 • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 8 Plus • GS6 Edge • Note 5 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone X • GS6 Edge+ • Note 8 • HTC U11 • G7 ThinQ • X power • iPhone 6S Plus • iPhone XS • GS7 • Note 9 • G8 ThinQ • V40 ThinQ • iPhone XS Max • GS7 Edge • GS10 • V50 ThinQ • iPhone XR • GS8 • GS10e • GS8 Plus • GS10+ • Galaxy S10 5G Deductible/Service Fee and Repair Schedule Monthly Charge Tier 1 Tier 2 Tier 3 Tier 4 Tier 5 Sprint Complete $9 $9 - - - - Sprint Complete (Includes AppleCare® Services for eligible devices) - $15 $15 $15 $19 Equipment Service and Repair Program (ESRP) $8.25 $8.25 $8.25 $8.25 $11 Phone: Insurance Deductibles (ERP) and Service Contract ADH Service Fees during Asurion Administration (ESRP) ADH Cracked Screen Repair (ESRP) $25 $29 $29 $29 $29 ESRP standalone coverage does not include $29 cracked screens. -

Mobile Banking
Mobile Banking Click To Begin Register Your Device Before you begin, you must first register your phone by logging into home banking. Start by selecting the types of services you wish to access on your phone. Click on the “Not Sure? Click here to compare the services” link for more information on the types of services available. * When selecting Alert Banking, you must make sure that you setup the type of alerts you wish to receiving within home banking services. Register Your Device Select time zone and accounts you wish to access. You can also give your accounts a short nickname for texting purposes. Register Your Device Enter your mobile phone number: Register Your Device You will receive a text message on your phone containing the activation code. Enter the activation code here and click Activate. Register Your Device You may now begin using your phone for mobile banking. In the next step, you will select your phone type for more details. Click On Your Type Of Phone iPhone Based on your selection of services when you registered your device, you will receive a text message with further instructions for each service. For more information on how to access these services, please select from the options below: SMS (Text Banking) WAP (Mobile Browser) APP (Downloadable Application from iTunes) iPhone – SMS (Text Banking) During the registration process, you will receive a text message with information on how to access and use SMS (text Banking). iPhone – SMS (Text Banking) Text to 59289. Type HIST + account nickname to receive a list of transactions for that account. -

Device Compatibility APPLE™ COMPATIBILITY
Device Compatibility Android devices running the required software must also have a microUSB port and support powered USB OTG. iOS devices running the required software must be equipped with a lightning connector port. Visit the Help Center for more detailed explanations of Android requirements and iOS requirements. APPLE™ COMPATIBILITY Works with and tested against: iPhone XS Max iPhone XS iPhone XR iPhone X iPhone 8 Plus iPhone 8 iPhone 7+ iPhone 7 iPhone SE iPhone 5 iPhone 5c iPhone 5s iPhone 6 iPhone 6+ iPhone 6s iPhone 6s+ iPhone SE iPod Touch 5th Generation Works with, but not optimized for: iPad Mini (all versions) iPad Air iPad 4th Generation Not compatible with: iPhone 4s or lower iPad 3 or lower iPod Touch 4 or lower iPad Pro ANDROID™ COMPATIBILITY Works with and tested against: Motorola Moto X Motorola Moto G Samsung Galaxy S3 Samsung Galaxy S4 Samsung Galaxy S5 (except some running 5.1.1*) Samsung Galaxy S6 Samsung Galaxy S6 Edge Samsung Galaxy S7 Samsung Galaxy S7 Edge Samsung Galaxy Note 2 Samsung Galaxy Note 3 Samsung Galaxy Note 4 Samsung Galaxy Note 8 Samsung Galaxy Note Edge HTC One Mini 2 (requires adapter) HTC One A9 (requires adapter) HTC One M8 (requires adapter) HTC One M9 (requires adapter) HTC Desire EYE (requires adapter) HTC Desire 820 (requires adapter) Google Nexus 5 (requires adapter) Google Nexus 6 (requires reversible adapter or cable) Google Nexus 5x (requires USB-C adapter) Google Nexus 6p (requires USB-C adapter) Google Pixel (Requires USB-C adapter) -

See List of Compatible Mobile Devices
Compatible Mobile Devices List Apple iOS Devices Azden i-Coustics products are fully compatible with the latest Apple iOS devices, including: iPhone 11 Pro*, 11*, Xr*, X* 8*, 8 Plus*, 7*, 7 Plus*, 6s, 6s Plus, SE, iPad Pro, iPad, iPad mini and iPod touch. *Use with iPhone models 7 and newer requires the use of Apple’s Lightning to headphone audio adapter Compatibility extends to earlier models as follows: iPhone 3G and newer (2008) iPad 2 and newer (2010) nd iPod Touch 2 Gen and newer (2008) Android Devices GOOGLE Motorola Samsung PIXEL 1, 2, 3* & 4* (all versions) Razr* All GALAXY NOTE MODELS NEXUS 4 Motorola One* Including Note10* & Note9 NEXUS 5 Moto G5, G6, G7 NEXUS 6 Moto E4, E5, E6 ALL GALAXY S MODELS* NEXUS 7 Moto Z2*, Z3*, Z4 Including S10 and S20 NEXUS 8 Moto X4 NEXUS 9 DROID RAZR M All GALAXY Tab Models NEXUS 10 DROID RAZR HD NEXUS ONE DROID RAZR MAXX HD Galaxy Z* NEXUS S PHOTON Q 4G LTE Galaxy A50 / A20 / A10e GALAXY NEXUS ATRIX HD Champ Neo DUOS DROID RAZR MAXX GALAXY Music HTC DROID RAZR GALAXY S Duos All HTC models including: ELECTRIFY 2 GALAXY Ace Plus DEFY XT GALAXY Beam HTC U12+* DROID 4 GALAXY Pocket HTC U11*/U11 Life* ATRIX 2 Black White HTC One models ADMIRAL Galaxy Mini 2 HTC Desire models ELECTRIFY GALAXY Y Duos Droid DNA PHOTON 4G GALAXY W HTC Evo 4G LTE i867 OMNIA W Droid Incredible 4G LTE TITANIUM GALAXY Xcover HTC One SV TRIUMPH GALAXY Nexus HTC 8XT ATRIX 4G GALAXY Ace GALAXY Gio LG GALAXY Fit GALAXY mini V50, V40, V35, V30, V30+ Nexus S G8X, G8, G7, G6, G5, G4 OMNIA 7 OPTIMUS G GALAXY 551 OPTIMUS L7, L5, L3, L2 GALAXY 580 Wave 723 * On Android devices, compatibility requires using the manufacturer’s USB-C adapter for headsets This list is not exhaustive and there may be some compatible devices not shown.