Logging NFC Data on a Google Nexus S
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

A Survey on Architectures of Mobile Operating Systems: Challenges and Issues
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 3, March 2015, PP 73-76 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A Survey on Architectures of Mobile Operating Systems: Challenges and Issues Prof. Y. K. Sundara Krishna1 HOD, Dept. of Computer Science, Krishna University Mr. G K Mohan Devarakonda2 Research Scholar, Krishna University Abstract: In the early years of mobile evolution, Discontinued Platforms Current mobile devices are enabled only with voice services Platforms that allow the users to communicate with each other. Symbian OS Android But now a days, the mobile technology undergone Palm OS IOS various changes to a great extent so that the devices Maemo OS Windows Phone allows the users not only to communicate but also to Meego OS Firefox OS attain a variety of services such as video calls, faster Black Berry OS browsing services,2d and 3d games, Camera, 2.1 Symbian OS: This Operating system was Banking Services, GPS services, File sharing developed by NOKIA. services, Tracking Services, M-Commerce and so many. The changes in mobile technology may be due Architecture: to Operating System or Hardware or Network or Memory. This paper presents a survey on evolutions SYMBIAN OS GUI Library in mobile developments especially on mobile operating system Architectures, challenges and Issues in various mobile operating Systems. Application Engines JAVA VM 1. INTRODUCTION Servers (Operating System Services) A Mobile operating system is a System Software that is specifically designed to run on handheld devices Symbian OS Base (File Server, Kernel) such as Mobile Phones, PDA’s. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -

2019 China Military Power Report
OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China ANNUAL REPORT TO CONGRESS Military and Security Developments Involving the People’s Republic of China 2019 Office of the Secretary of Defense Preparation of this report cost the Department of Defense a total of approximately $181,000 in Fiscal Years 2018-2019. This includes $12,000 in expenses and $169,000 in DoD labor. Generated on 2019May02 RefID: E-1F4B924 OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China 2019 A Report to Congress Pursuant to the National Defense Authorization Act for Fiscal Year 2000, as Amended Section 1260, “Annual Report on Military and Security Developments Involving the People’s Republic of China,” of the National Defense Authorization Act for Fiscal Year 2019, Public Law 115-232, which amends the National Defense Authorization Act for Fiscal Year 2000, Section 1202, Public Law 106-65, provides that the Secretary of Defense shall submit a report “in both classified and unclassified form, on military and security developments involving the People’s Republic of China. The report shall address the current and probable future course of military-technological development of the People’s Liberation Army and the tenets and probable development of Chinese security strategy and military strategy, and of the military organizations and operational concepts supporting such development over the next 20 years. -

Ah! Universal Android Rooting Is Back
AH! UNIVERSAL ANDROID ROOTING IS BACK Wen `Memeda` Xu @K33nTeam ABOUT ME Wen Xu a.k.a Memeda @antlr7 • Security research intern at KeenTeam • Android Roo6ng • Soware exploita6on • Senior student at Shanghai Jiao Tong University • Member of LoCCS • Vice-captain of CTF team 0ops • Rank 2rd in the world on CTFTIME AGENDA • Present Situa6on of Android Roo6ng • Awesome Bug (CVE-2015-3636) • Fuzzing • Analysis • Awesome Exploita6on Techniques • Object Re-filling in kernel UAF • Kernel Code Execu@on • Targe@ng 64bit Devices • Future PART I Present Situation PRESENT SITUATION Root for what? • Goal • uid=0(root) gid=0(root) groups=0(root) • Kernel arbitrary read/write • Cleaning • SELinux • … PRESENT SITUATION • SoC (Driver) • Missing argument sani6Za6on (ioctl/mmap) • Qualcomm camera drivers bug CVE-2014-4321, CVE-2014-4324 CVE-2014-0975, CVE-2014-0976 • TOCTTOU • Direct dereference in user space CVE-2014-8299 • Chip by chip A BIG DEAL • Universal root soluon • Universally applied bug • Confronng Linux kernel • Universally applied exploita6on techniques • One exploit for hundreds of thousands of devices • Adaptability (Hardcode) • User-friendly (Stability) • COMING BACK AGAIN! PART II Bug Hunting FUZZING Open source kernel syscall fuzzer • Trinity • hps://github.com/kernelslacker/trinity • Scalability • Ported to ARM Linux FUZZING Let’s take a look at our log when we wake up ;) • Crical paging fault at 0x200200?!! SK: PING SOCKET OBJECT IN KERNEL user_sock_fd = socket(AF_INET, SOCK_DGRAM, IPPROTO_ICMP); 2 3 1 LIST_POISON2 == 0X200200 ping_unhash -
Sprint Complete
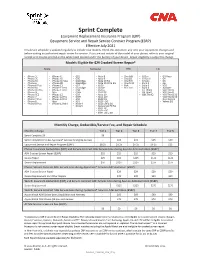
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) Effective July 2021 This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair* Apple Samsung HTC LG • iPhone 5 • iPhone X • GS5 • Note 8 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone XS • GS6 • Note 9 • One E8 • G Flex II • G4 • iPhone 5S • iPhone XS Max • GS6 Edge • Note 20 5G • One M9 • G Stylo • G5 • iPhone 6 • iPhone XR • GS6 Edge+ • Note 20 Ultra 5G • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 11 • GS7 • GS10 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone 11 Pro • GS7 Edge • GS10e • HTC U11 • Stylo 6 • X power • iPhone 6S Plus • iPhone 11 Pro • GS8 • GS10+ • G7 ThinQ • V40 ThinQ • iPhone SE Max • GS8+ • GS10 5G • G8 ThinQ • V50 ThinQ • iPhone SE2 • iPhone 12 • GS9 • Note 10 • G8X ThinQ • V60 ThinQ 5G • iPhone 7 • iPhone 12 Pro • GS9+ • Note 10+ • V60 ThinQ 5G • iPhone 7 Plus • iPhone 12 Pro • A50 • GS20 5G Dual Screen • iPhone 8 Max • A51 • GS20+ 5G • Velvet 5G • iPhone 8 Plus • iPhone 12 Mini • Note 4 • GS20 Ultra 5G • Note 5 • Galaxy S20 FE 5G • GS21 5G • GS21+ 5G • GS21 Ultra 5G Monthly Charge, Deductible/Service Fee, and Repair Schedule -

MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition – Insights and Considerations | 1
MOBILE OPERATING SYSTEM TRANSITION Insights and Considerations Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 1 Introduction A shift in the mobile operating system landscape has occurred over the last several years. The transition from legacy Windows® is well underway. While there remain several distinct choices on the roadmap, the tradeoffs and compromises associated with each have become clearer. This paper will elaborate on these points and provide the reader with guidance on recommended solutions. Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 2 Table of contents 3 Mobile Operating System History 4 Legacy Operating Systems 5 Android Enterprise Evolution 6 How Honeywell Helps 8 Android Lifecycle Management 10 Conclusion and Recommendations Mobile Operating System Transition – Insights and Considerations | www.honeywellaidc.com 3 Mobile Operating System History For the open source Android operating system, Google OEMs and third parties began developing extensions that enabled device management capabilities, provided more control over user actions, and added support for Ten years ago, operating systems for mobile devices in the enterprise space were provided by Microsoft. Windows CE and Windows Mobile (later Windows Embedded Handheld) offered industrial Wi-Fi features and capabilities needed for enterprise deployment, while a robust ecosystem of networks and developer tools and third-party offerings allowed customers to create the solution needed barcode scanning to effectively operate and manage their businesses. Apple had only recently shown the first capabilities. iPhone®. Google acquired Android™ a few years earlier and had yet to see a phone come to market. Other options available at that time were largely focused around the white collar professional user and proved largely unsuitable for the unique needs of the purpose-built enterprise environment. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -

Android Support for Microsoft Exchange in Pure Google Devices
Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of these pure Google devices running Android. Android support by version and device The following AndroidTM versions support Microsoft Exchange information services and security policies: ● Android 4.0.4 (Ice Cream Sandwich) ● Android 4.1 and later (Jelly Bean) The following “pure Google” devices support the Microsoft Exchange services and policies: ● Galaxy Nexus phones running Android ● Nexus S phones running Android ● Motorola Xoom tablets running Android ● Nexus 4 phones running Android ● Nexus 7 tablets running Android ● Nexus 10 tablets running Android Requirements To support Android 4.0 running on pure Google devices, you must be running one of the following versions of Microsoft Exchange: ● Exchange Server 2010 SP1 with Exchange ActiveSync 14.1 ● Exchange Server 2010 with Exchange ActiveSync 14.0 ● Exchange Server 2007 SP1 with Exchange ActiveSync 12.1 ● Exchange Server 2007 with Exchange ActiveSync 12.0 ● Exchange Server 2003 SP2 with Exchange ActiveSync 2.5 The following information applies to the Android platform, including the Settings, Email, Calendar, People, and related apps as built by Google. If a device manufacturer has modified these apps on its own devices, contact the manufacturer for information about support for Exchange features. Supported information services Users can add Microsoft Exchange accounts to their pure Google devices by using the Account & Sync settings available from the Settings or Email app. Android supports the following Exchange information services: ● Adding Exchange user accounts (via an ActiveSync server), and enforcement of some mailbox policies (as described in “Supported security policies,” next). -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

Devices, the Weak Link in Achieving an Open Internet
Smartphones, tablets, voice assistants... DEVICES, THE WEAK LINK IN ACHIEVING AN OPEN INTERNET Report on their limitations and proposals for corrective measures French République February 2018 Devices, the weak link in achieving an open internet Content 1 Introduction ..................................................................................................................................... 5 2 End-user devices’ possible or probable evolution .......................................................................... 7 2.1 Different development models for the main internet access devices .................................... 7 2.1.1 Increasingly mobile internet access in France, and in Europe, controlled by two main players 7 2.1.2 In China, mobile internet access from the onset, with a larger selection of smartphones .................................................................................................................................. 12 2.2 Features that could prove decisive in users’ choice of an internet access device ................ 14 2.2.1 Artificial intelligence, an additional level of intelligence in devices .............................. 14 2.2.2 Voice assistance, a feature designed to simplify commands ........................................ 15 2.2.3 Mobile payment: an indispensable feature for smartphones? ..................................... 15 2.2.4 Virtual reality and augmented reality, mere goodies or future must-haves for devices? 17 2.2.5 Advent of thin client devices: giving the cloud a bigger role? -
![[WEEKLY WIRELESS REPORT] Week Ending September 30, 2011](https://docslib.b-cdn.net/cover/6675/weekly-wireless-report-week-ending-september-30-2011-1036675.webp)
[WEEKLY WIRELESS REPORT] Week Ending September 30, 2011
[WEEKLY WIRELESS REPORT] Week ending September 30, 2011 This Week’s Stories key rhetorical question: "Why not just evolve MeeGo?" The answer, he said, is that "the future belongs to HTML5-based applications, outside of a AT&T Mobility Suffers Huge relatively small percentage of apps ," and Intel Network Outage in Los Angeles believes its investment should shift in that direction. September 26, 2011 But, he added, "shifting to HTML5 doesn't just mean slapping a web runtime on an existing Linux, even AT&T Mobility subscribers in Los Angeles can now one aimed at mobile, as MeeGo has been." text and make calls again on their mobile devices after technicians repaired a widespread network outage that affected millions of people. Sousou said that emphasizing HTML5 means APIs need to evolve with platform technology and by market segment, which a new platform could more AT&T spokesperson Meredith Red said late yesterday easily provide. that a hardware failure led to network issues with about 900 cellular towers across LA. Tizen will reside within the Linux Foundation, be governed by a Technical Steering Group, will be The service problems began at about 3.00 P.M. developed openly, and will support tablets, notebooks, Saturday and contributed to an evening of missed, handsets, smart TVs, and in-vehicle infotainment dropped and failed calls. Service was fully restored systems. early Sunday morning, local time. On the new Tizen.org website, a welcoming Red says it's unclear how many wireless subscribers statement said that Tizen APIs will cover various were affected, but conservative estimates are in the platform capabilities, including messaging, multimedia, millions.