Towards the Unification of Intuitive and Formal Game Concepts with Applications to Computer Chess
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Social Conflict and Sacrificial Rhetoric
CHRISTOPHER ROBERTS Social Conflict and Sacrificial Rhetoric Luther’s Discursive Intervention and the Religious Division of Labor Introduction ‘Sacrifice’ is a religious term whose use extends far beyond the church door. People from all walks of life speak of ‘sacrifice’ when they want to evoke an irreducible conflict in the relations between self, family, and soci- ety. In America, hardly a speech goes by without political leaders insisting upon the necessity and virtue of sacrifice, but rarely will they clarify who is sacrificing what, and to whom. Indeed, this is not only an American phenomenon, as a number of recent texts examining ‘sacrifice’ as a term in various national discourses have shown.1 Such a political and economic deployment of a religious figure demands interpretation, for not only does the rhetoric of sacrifice span the globe,2 it constitutes a problem with a long genealogy. As a key moment in the Western segment of this genealogy, this article will examine the way that Luther’s exegetical work rhetoricalized sacrifice, and, in doing so, constructed a new discursive position, the pas- tor as anti-sophist, or parrhesiast, in the religious division of labor. The overarching question for this inquiry is how did a particular re- ligious ritual like sacrifice come to serve as such a widespread rhetorical figure? When faced with the immense historical distance between, first, the public destruction of wealth or butchering of an animal, and, last, a speech act describing non-ritual phenomena as a sacrifice, one measures the distance not only in years but also in religious and cultural transform- ation. -

CONTENTS Contents
CONTENTS Contents Symbols 5 Preface 6 Introduction 9 1 Glossary of Attacking and Strategic Terms 11 2 Double Attack 23 2.1: Double Attacks with Queens and Rooks 24 2.2: Bishop Forks 31 2.3: Knight Forks 34 2.4: The Í+Ì Connection 44 2.5: Pawn Forks 45 2.6: The Discovered Double Attack 46 2.7: Another Type of Double Attack 53 Exercises 55 Solutions 61 3 The Role of the Pawns 65 3.1: Pawn Promotion 65 3.2: The Far-Advanced Passed Pawn 71 3.3: Connected Passed Pawns 85 3.4: The Pawn-Wedge 89 3.5: Passive Sacrifices 91 3.6: The Kamikaze Pawn 92 Exercises 99 Solutions 103 4 Attacking the Castled Position 106 4.1: Weakness in the Castled Position 106 4.2: Rooks and Files 112 4.3: The Greek Gift 128 4.4: Other Bishop Sacrifices 133 4.5: Panic on the Long Diagonal 143 4.6: The Knight Sacrifice 150 4.7: The Exchange Sacrifice 162 4.8: The Queen Sacrifice 172 Exercises 176 Solutions 181 5 Drawing Combinations 186 5.1: Perpetual Check 186 5.2: Repetition of Position 194 5.3: Stalemate 197 5.4: Fortress and Blockade 202 5.5: Positional Draws 204 Exercises 207 Solutions 210 6 Combined Tactical Themes 213 6.1: Material, Endings, Zugzwang 214 6.2: One Sacrifice after Another 232 6.3: Extraordinary Combinations 242 6.4: A Diabolical Position 257 Exercises 260 Solutions 264 7 Opening Disasters 268 7.1: Open Games 268 7.2: Semi-Open Games 274 7.3: Closed Games 288 8 Tactical Examination 304 Test 1 306 Test 2 308 Test 3 310 Test 4 312 Test 5 314 Test 6 316 Hints 318 Solutions 320 Index of Names 331 Index of Openings 335 THE ROLE OF THE PAWNS 3 The Role of the Pawns Ever since the distant days of the 18th century 3.1: Pawn Promotion (let us call it the time of the French Revolution, or of François-André Danican Philidor) we have known that “pawns are the soul of chess”. -

Learning Long-Term Chess Strategies from Databases
Mach Learn (2006) 63:329–340 DOI 10.1007/s10994-006-6747-7 TECHNICAL NOTE Learning long-term chess strategies from databases Aleksander Sadikov · Ivan Bratko Received: March 10, 2005 / Revised: December 14, 2005 / Accepted: December 21, 2005 / Published online: 28 March 2006 Springer Science + Business Media, LLC 2006 Abstract We propose an approach to the learning of long-term plans for playing chess endgames. We assume that a computer-generated database for an endgame is available, such as the king and rook vs. king, or king and queen vs. king and rook endgame. For each position in the endgame, the database gives the “value” of the position in terms of the minimum number of moves needed by the stronger side to win given that both sides play optimally. We propose a method for automatically dividing the endgame into stages characterised by different objectives of play. For each stage of such a game plan, a stage- specific evaluation function is induced, to be used by minimax search when playing the endgame. We aim at learning playing strategies that give good insight into the principles of playing specific endgames. Games played by these strategies should resemble human expert’s play in achieving goals and subgoals reliably, but not necessarily as quickly as possible. Keywords Machine learning . Computer chess . Long-term Strategy . Chess endgames . Chess databases 1. Introduction The standard approach used in chess playing programs relies on the minimax principle, efficiently implemented by alpha-beta algorithm, plus a heuristic evaluation function. This approach has proved to work particularly well in situations in which short-term tactics are prevalent, when evaluation function can easily recognise within the search horizon the con- sequences of good or bad moves. -

Fundamental Endings CYRUS LAKDAWALA
First Steps : Fundamental Endings CYRUS LAKDAWALA www.everymanchess.com About the Author Cyrus Lakdawala is an International Master, a former National Open and American Open Cham- pion, and a six-time State Champion. He has been teaching chess for over 30 years, and coaches some of the top junior players in the U.S. Also by the Author: Play the London System A Ferocious Opening Repertoire The Slav: Move by Move 1...d6: Move by Move The Caro-Kann: Move by Move The Four Knights: Move by Move Capablanca: Move by Move The Modern Defence: Move by Move Kramnik: Move by Move The Colle: Move by Move The Scandinavian: Move by Move Botvinnik: Move by Move The Nimzo-Larsen Attack: Move by Move Korchnoi: Move by Move The Alekhine Defence: Move by Move The Trompowsky Attack: Move by Move Carlsen: Move by Move The Classical French: Move by Move Larsen: Move by Move 1...b6: Move by Move Bird’s Opening: Move by Move Petroff Defence: Move by Move Fischer: Move by Move Anti-Sicilians: Move by Move Opening Repertoire ... c6 First Steps: the Modern 3 Contents About the Author 3 Bibliography 5 Introduction 7 1 Essential Knowledge 9 2 Pawn Endings 23 3 Rook Endings 63 4 Queen Endings 119 5 Bishop Endings 144 6 Knight Endings 172 7 Minor Piece Endings 184 8 Rooks and Minor Pieces 206 9 Queen and Other Pieces 243 4 Introduction Why Study Chess at its Cellular Level? A chess battle is no less intense for its lack of brevity. Because my messianic mission in life is to make the chess board a safer place for students and readers, I break the seal of confessional and tell you that some students consider the idea of enjoyable endgame study an oxymoron. -

Multilinear Algebra and Chess Endgames
Games of No Chance MSRI Publications Volume 29, 1996 Multilinear Algebra and Chess Endgames LEWIS STILLER Abstract. This article has three chief aims: (1) To show the wide utility of multilinear algebraic formalism for high-performance computing. (2) To describe an application of this formalism in the analysis of chess endgames, and results obtained thereby that would have been impossible to compute using earlier techniques, including a win requiring a record 243 moves. (3) To contribute to the study of the history of chess endgames, by focusing on the work of Friedrich Amelung (in particular his apparently lost analysis of certain six-piece endgames) and that of Theodor Molien, one of the founders of modern group representation theory and the first person to have systematically numerically analyzed a pawnless endgame. 1. Introduction Parallel and vector architectures can achieve high peak bandwidth, but it can be difficult for the programmer to design algorithms that exploit this bandwidth efficiently. Application performance can depend heavily on unique architecture features that complicate the design of portable code [Szymanski et al. 1994; Stone 1993]. The work reported here is part of a project to explore the extent to which the techniques of multilinear algebra can be used to simplify the design of high- performance parallel and vector algorithms [Johnson et al. 1991]. The approach is this: Define a set of fixed, structured matrices that encode architectural primitives • of the machine, in the sense that left-multiplication of a vector by this matrix is efficient on the target architecture. Formulate the application problem as a matrix multiplication. -

Chess-Training-Guide.Pdf
Q Chess Training Guide K for Teachers and Parents Created by Grandmaster Susan Polgar U.S. Chess Hall of Fame Inductee President and Founder of the Susan Polgar Foundation Director of SPICE (Susan Polgar Institute for Chess Excellence) at Webster University FIDE Senior Chess Trainer 2006 Women’s World Chess Cup Champion Winner of 4 Women’s World Chess Championships The only World Champion in history to win the Triple-Crown (Blitz, Rapid and Classical) 12 Olympic Medals (5 Gold, 4 Silver, 3 Bronze) 3-time US Open Blitz Champion #1 ranked woman player in the United States Ranked #1 in the world at age 15 and in the top 3 for about 25 consecutive years 1st woman in history to qualify for the Men’s World Championship 1st woman in history to earn the Grandmaster title 1st woman in history to coach a Men's Division I team to 7 consecutive Final Four Championships 1st woman in history to coach the #1 ranked Men's Division I team in the nation pnlrqk KQRLNP Get Smart! Play Chess! www.ChessDailyNews.com www.twitter.com/SusanPolgar www.facebook.com/SusanPolgarChess www.instagram.com/SusanPolgarChess www.SusanPolgar.com www.SusanPolgarFoundation.org SPF Chess Training Program for Teachers © Page 1 7/2/2019 Lesson 1 Lesson goals: Excite kids about the fun game of chess Relate the cool history of chess Incorporate chess with education: Learning about India and Persia Incorporate chess with education: Learning about the chess board and its coordinates Who invented chess and why? Talk about India / Persia – connects to Geography Tell the story of “seed”. -

Chess Endgames: 6-Man Data and Strategy
CORE Metadata, citation and similar papers at core.ac.uk Provided by Central Archive at the University of Reading Chess endgames: 6-man data and strategy M.S. Bourzutschky, J.A. Tamplin, and G.McC. Haworth [email protected], [email protected], [email protected]; http:// http://www.jaet.org/jat/ Abstract While Nalimov’s endgame tables for Western Chess are the most used today, their Depth-to-Mate metric is not the most efficient or effective in use. The authors have developed and used new programs to create tables to alternative metrics and recommend better strategies for endgame play. Key words: chess: conversion, data, depth, endgame, goal, move count, statistics, strategy 1 Introduction Chess endgames tables (EGTs) to the ‘DTM’ Depth to Mate metric are the most commonly used, thanks to codes and production work by Nalimov [10,7]. DTM data is of interest in itself, even if conversion, i.e., change of force, is more often adopted as an interim objective in human play. However, more effective endgame strategies using different metrics can be adopted, particularly by computers [3,4]. A further practical disadvantage of the DTM metric is that, as maxDTM increases, the EGTs take longer to generate and are less compressible. 1 2 Here, we focus on metrics DTC, DTZ and DTZ50 ; the first two were effectively used by Thompson [19], Stiller [14], and Wirth [20]. New programs by Tamplin [15] and Bourzutschky [2] have already enabled a complete suite of 3-to-5-man DTC/Z/Z50 EGTs to be produced [18]. This note is an update, focusing solely on Tamplin’s continuing work, assisted by Bourzutschky, with the latter code on 6-man, pawnless endgames for which DTC ≡ DTZ and DTC50 ≡ DTZ50. -

Kasparov's Nightmare!! Bobby Fischer Challenges IBM to Simul IBM
California Chess Journal Volume 20, Number 2 April 1st 2004 $4.50 Kasparov’s Nightmare!! Bobby Fischer Challenges IBM to Simul IBM Scrambles to Build 25 Deep Blues! Past Vs Future Special Issue • Young Fischer Fires Up S.F. • Fischer commentates 4 Boyscouts • Building your “Super Computer” • Building Fischer’s Dream House • Raise $500 playing chess! • Fischer Articles Galore! California Chess Journal Table of Con tents 2004 Cal Chess Scholastic Championships The annual scholastic tourney finishes in Santa Clara.......................................................3 FISCHER AND THE DEEP BLUE Editor: Eric Hicks Contributors: Daren Dillinger A miracle has happened in the Phillipines!......................................................................4 FM Eric Schiller IM John Donaldson Why Every Chess Player Needs a Computer Photographers: Richard Shorman Some titles speak for themselves......................................................................................5 Historical Consul: Kerry Lawless Founding Editor: Hans Poschmann Building Your Chess Dream Machine Some helpful hints when shopping for a silicon chess opponent........................................6 CalChess Board Young Fischer in San Francisco 1957 A complet accounting of an untold story that happened here in the bay area...................12 President: Elizabeth Shaughnessy Vice-President: Josh Bowman 1957 Fischer Game Spotlight Treasurer: Richard Peterson One game from the tournament commentated move by move.........................................16 Members at -

Extended Null-Move Reductions
Extended Null-Move Reductions Omid David-Tabibi1 and Nathan S. Netanyahu1,2 1 Department of Computer Science, Bar-Ilan University, Ramat-Gan 52900, Israel [email protected], [email protected] 2 Center for Automation Research, University of Maryland, College Park, MD 20742, USA [email protected] Abstract. In this paper we review the conventional versions of null- move pruning, and present our enhancements which allow for a deeper search with greater accuracy. While the conventional versions of null- move pruning use reduction values of R ≤ 3, we use an aggressive re- duction value of R = 4 within a verified adaptive configuration which maximizes the benefit from the more aggressive pruning, while limiting its tactical liabilities. Our experimental results using our grandmaster- level chess program, Falcon, show that our null-move reductions (NMR) outperform the conventional methods, with the tactical benefits of the deeper search dominating the deficiencies. Moreover, unlike standard null-move pruning, which fails badly in zugzwang positions, NMR is impervious to zugzwangs. Finally, the implementation of NMR in any program already using null-move pruning requires a modification of only a few lines of code. 1 Introduction Chess programs trying to search the same way humans think by generating “plausible” moves dominated until the mid-1970s. By using extensive chess knowledge at each node, these programs selected a few moves which they consid- ered plausible, and thus pruned large parts of the search tree. However, plausible- move generating programs had serious tactical shortcomings, and as soon as brute-force search programs such as Tech [17] and Chess 4.x [29] managed to reach depths of 5 plies and more, plausible-move generating programs fre- quently lost to brute-force searchers due to their tactical weaknesses. -

{Download PDF} Kasparov Versus Deep Blue : Computer Chess
KASPAROV VERSUS DEEP BLUE : COMPUTER CHESS COMES OF AGE PDF, EPUB, EBOOK Monty Newborn | 322 pages | 31 Jul 2012 | Springer-Verlag New York Inc. | 9781461274773 | English | New York, NY, United States Kasparov versus Deep Blue : Computer Chess Comes of Age PDF Book In terms of human comparison, the already existing hierarchy of rated chess players throughout the world gave engineers a scale with which to easily and accurately measure the success of their machine. This was the position on the board after 35 moves. Nxh5 Nd2 Kg4 Bc7 Famously, the mechanical Turk developed in thrilled and confounded luminaries as notable as Napoleon Bonaparte and Benjamin Franklin. Kf1 Bc3 Deep Blue. The only reason Deep Blue played in that way, as was later revealed, was because that very same day of the game the creators of Deep Blue had inputted the variation into the opening database. KevinC The allegation was that a grandmaster, presumably a top rival, had been behind the move. When it's in the open, anyone could respond to them, including people who do understand them. Qe2 Qd8 Bf3 Nd3 IBM Research. Nearly two decades later, the match still fascinates This week Time Magazine ran a story on the famous series of matches between IBM's supercomputer and Garry Kasparov. Because once you have an agenda, where does indifference fit into the picture? Raa6 Ba7 Black would have acquired strong counterplay. In fact, the first move I looked at was the immediate 36 Be4, but in a game, for the same safety-first reasons the black counterplay with a5 I might well have opted for 36 axb5. -

PUBLIC SUBMISSION Status: Pending Post Tracking No
As of: January 02, 2020 Received: December 20, 2019 PUBLIC SUBMISSION Status: Pending_Post Tracking No. 1k3-9dz4-mt2u Comments Due: January 10, 2020 Submission Type: Web Docket: PTO-C-2019-0038 Request for Comments on Intellectual Property Protection for Artificial Intelligence Innovation Comment On: PTO-C-2019-0038-0002 Intellectual Property Protection for Artificial Intelligence Innovation Document: PTO-C-2019-0038-DRAFT-0009 Comment on FR Doc # 2019-26104 Submitter Information Name: Yale Robinson Address: 505 Pleasant Street Apartment 103 Malden, MA, 02148 Email: [email protected] General Comment In the attached PDF document, I describe the history of chess puzzle composition with a focus on three intellectual property issues that determine whether a chess composition is considered eligible for publication in a magazine or tournament award: (1) having one unique solution; (2) not being anticipated, and (3) not being submitted simultaneously for two different publications. The process of composing a chess endgame study using computer analysis tools, including endgame tablebases, is cited as an example of the partnership between an AI device and a human creator. I conclude with a suggestion to distinguish creative value from financial profit in evaluating IP issues in AI inventions, based on the fact that most chess puzzle composers follow IP conventions despite lacking any expectation of financial profit. Attachments Letter to USPTO on AI and Chess Puzzle Composition 35 - Robinson second submission - PTO-C-2019-0038-DRAFT-0009.html[3/11/2020 9:29:01 PM] December 20, 2019 From: Yale Yechiel N. Robinson, Esq. 505 Pleasant Street #103 Malden, MA 02148 Email: [email protected] To: Andrei Iancu Director of the U.S. -
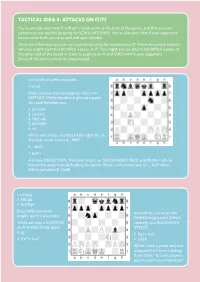
TACTICAL IDEA 4: ATTACKS on F7/F2
TACTICAL IDEA 4: ATTACKS ON f7/f2 You’ve already seen that f7 is Black’s weak point at the start of the game, and that you can sometimes win quickly by going for SCHOLAR’S MATE. You’ve also seen that if your opponent knows what to do you may well end up in trouble. There are other ways you can win quickly by using the weakness on f7. There are several reasons why you might want to SACRIFICE a piece on f7. You might also be able to SACRIFICE a piece at the other end of the board in order to capture on f7 and CHECKMATE your opponent. Some of the tactics are quite complicated. Let’s look at a few examples. 1. e4 c5 Black chooses the very popular SICILIAN DEFENCE. White decides to give up a pawn for rapid development. 2. d4 cxd4 3. c3 dxc3 4. Nxc3 d6 5. Bc4 Nf6 6. e5 White sets a trap, and Black falls right into it. The best move now is 6… Nfd7 6… dxe5 7. Bxf7+ A simple DEFLECTION. The black king is an OVERWORKED PIECE and White’s bishop forces him away from defending the queen. Black’s only move now is 7… Kxf7 when White just plays 8. Qxd8. 1. e4 Nc6 2. Nf3 d6 3. Bc4 Bg4 Black PINS the white Now White can move the knight, but it’s a mistake. PINNED knight with CHECK, White can play a SACRIFICE opening up a DISCOVERED on f7 to DECOY the black ATTACK. king. 5.