I. the Legal, Institutional, &Technical Architecture of ADMS in India
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Feasibility Study on Opium Licensing in Afghanistan
FEASIBILITY STUDY ON OPIUM LICENSING IN AFGHANISTAN FOR THE PRODUCTION OF MORPHINE AND OTHER ESSENTIAL MEDICINES ﻣﻄﺎﻟﻌﻪ اﻣﮑﺎﻧﺎت در ﻣﻮرد ﺟﻮاز دهﯽ ﺗﺮﻳﺎک در اﻓﻐﺎﻧﺴﺘﺎن ﺑﺮای ﺗﻮﻟﻴﺪ ﻣﻮرﻓﻴﻦ و ادوﻳﻪ ﺟﺎت ﺿﺮوری دﻳﮕﺮ Initial Findings – September 2005 Kabul, Afghanistan The British Institute of International and Comparative Law Hugo Warner • University of Calgary Peter Facchini - Jill Hagel University of Ghent Brice De Ruyver - Laurens van Puyenbroeck University of Kabul Abdul Aziz Ali Ahmad - Osman Babury Cheragh Ali Cheragh - Mohammad Yasin Mohsini University of Lisbon Vitalino Canas - Nuno Aureliano • Shruti Patel • University of Toronto Benedikt Fischer Todd Culbert - Juergen Rehm • Wageningen University Jules Bos - Suzanne Pegge • Ali Wardak • The Senlis Council Gabrielle Archer - Juan Arjona - Luke Bryant Marc Das Gupta - Furkat Elmirzaev - Guillaume Fournier Jane Francis - Thalia Ioannidou - Ernestien Jensema Manna Kamio Badiella - Jorrit Kamminga - Fabrice Pothier Emmanuel Reinert - David Spivack - Daniel Werb FEASIBILITY STUDY ON OPIUM LICENSING IN AFGHANISTAN FOR THE PRODUCTION OF MORPHINE AND OTHER ESSENTIAL MEDICINES Initial Findings – September 2005 Kabul, Afghanistan Study Commissioned by The Senlis Council Study Edited and coordinated by David Spivack Editorial team: Juan Arjona, Jane Francis, Thalia Ioannidou, Ernestien Jensema, Manna Kamio Badiella, Fabrice Pothier. Published 2005 by MF Publishing Ltd 17 Queen Anne’s Gate, London SW1H 9BU, UK ISBN: 0-9550798-2-9 Printed and bound in Afghanistan by Jehoon; Printing Press Other publications -

TRAFFIC Post, India Office Newsletter (PDF)
• South Asia unites to curb illegal • India ranks highest in Tiger parts Pg 8 trade in endangered wildlife seizure over last decade • Officers from Uttar Pradesh, Pg 3 Maharashtra, Andhra Pradesh and West Bengal sharpen skills on wildlife law enforcement • Raja and Jackie: The new ATE champions fighting wildlife Pg 3 crime • World leaders echo support to IN FOCUS ensure doubling of world's wild Pg 4 India TRAFFIC © Tiger population • Efforts augmented to ensure sustainable harvesting and trade Pg 4 TRAFFIC Alert (Latest news on of MAPs illegal wildlife trade in India): Pg 5 • TRAFFIC India's film “Don't Buy T Trouble” now available in Hindi • Guard held with zebra skin Pg 5 TRAFFIC INDIA UPD • Customs officials seize Pg 6 ornamental fish at Coimbatore Airport • Five tonnes of Red Sanders logs Pg 7 • Experts link up to combat illegal Pg 5 seized at Gujarat port wildlife trade in Sri Lanka TRAFFIC ALER • Four tonnes of Sea cucumber Pg 7 seized in Tamil Nadu • Email alerts on CITES related Pg 6 SIGNPOST: Other significant Pg 12 OUTPOST issues now available by subscription news stories to read SIGNPOST Pg 10 NEW SECTION WILD CRY : Illegal wildlife trade threatens the future of many species in the © Ola Jennersten Ola © wild. This section highlights the plight of CITES one such species in trade. UPDATE • Tiger killers will be brought to Pg 6 book, says CITES Secretary General Pangolins in peril TRAFFIC POST march 2011 South Asia unites to curb illegal trade in endangered wildlife he eight countries of South Asia—India, Nepal, Pakistan, TAfghanistan, Bangladesh, Bhutan, Maldives and Sri Lanka— joined forces and established the South Asia Wildlife Enforcement Network (SAWEN) to collaborate and co-operate on strengthening wildlife law enforcement in the region. -
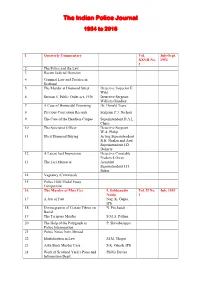
Index of the Indian Police Journal Issues from the Year 1954 to 2016
The Indian Police Journal 1954 to 2016 1 Quarterly Commentary Vol. July-Sept. XXVII No. 1954 3 2 The Police and the Law 3 Recent Judicial Decision 4 Criminal Law and Practice in Scotland 5 The Murder at Diamond Street Detective Inspector E. Wild 6 Section 5, Public Order act, 1936 Detective Sergeant William Grindley 7 A Case of Homicidal Poisoning Dr. Donald Teare 8 Previous Conviction Records Sergeant P.J. Nichols 9 The Case of the Headless Corpse Superintendent D.A.L. Chase 10 The Specialist Officer Detective Sergeant W.A. Philip 11 Illicit Diamond Buying Acting Superintendent B.H. Nealan and Asst. Superintendent J.D. Doherty 12 A Latent heel Impression Detective Constable Frederick Owen 13 The Lari Massacre Assistant Superintendent J.H. Baker 14 Vagrancy (Continued) 15 Police Gold Medal Essay Competition 16 The Murder of Miss Cox I. Sobhanadri Vol. II No. July 1955 Naidu 1 17 A Jest of Fate Nag. K. Gupta, IPS 18 Disintegration of Certain Fibres on N. Pitchandi Burial 19 The Tarapore Murder S.M.A. Pathan 20 The Help of the Polygraph in P. Shivabasappa Police Interrogation 21 Police Notes from Abroad 22 Identification in Law M.M. Thapar 23 Aska Bank Murder Case S.K. Ghosh, IPS 24 Work of Scotland Yard‘s Press and Phillis Davies Information Deptt. 25 Murder or Accident L. Forstner 26 The Finger Prints of Bahadur Khan Shiam Narain 27 A Chain of Forensic V.R. Kher, I.P. Vol. II No. January Laboratories in India 3 1956 28 Belbad Colliery Dacoity N.S. -

A Commentary on the April 2015 and February 2015 Country Information and Guidance Reports Issued on India
THIS DOCUMENT SHOULD BE USED AS A TOOL FOR IDENTIFYING RELEVANT COUNTRY OF ORIGIN INFORMATION. IT SHOULD NOT BE SUBMITTED AS EVIDENCE TO THE HOME OFFICE, THE TRIBUNAL OR OTHER DECISION MAKERS IN ASYLUM APPLICATIONS OR APPEALS © Still Human Still Here 2015 6 August 2015 (COI included up to 13 July 2015) A Commentary on the April 2015 and February 2015 Country Information and Guidance reports issued on India This commentary identifies what the ‘Still Human Still Here’ coalition considers to be the main inconsistencies and omissions between the currently available country of origin information (COI) and case law on India and the conclusions reached in the following Country Information and Guidance (CIG) reports issued by the UK Home Office: o Country information and guidance report: Women fearing gender-based harm/violence, India, April 2015 o Country information and guidance report: Background information, including actors of protection, and internal relocation, India, February 2015 Where we believe inconsistencies have been identified, the relevant section of the CIG report is highlighted in blue. An index of full sources of the COI referred to in this commentary is also provided at the end of the document (COI up to 13 July 2015). This commentary is a guide for legal practitioners and decision-makers in respect of the relevant COI, by reference to the sections of the CIG reports on India. The document should be used as a tool to help to identify relevant COI and the COI referred to can be considered by decision makers in assessing asylum applications and appeals. This document should not be submitted as evidence to the UK Home Office, the Tribunal or other decision makers in asylum applications or appeals. -

International Implementation of Best Practices for Mitigating Insider Threat: Analyses for India and Germany
International Implementation of Best Practices for Mitigating Insider Threat: Analyses for India and Germany Lori Flynn (Software Engineering Institute) Carly Huth (Software Engineering Institute) Palma Buttles-Valdez (Software Engineering Institute) Michael Theis (Software Engineering Institute) George Silowash (Software Engineering Institute) Tracy Cassidy (Software Engineering Institute) Travis Wright (Carnegie Mellon University, Master of Science in Information Security Policy and Management Program) Randy Trzeciak (Software Engineering Institute) April 2014 TECHNICAL REPORT CMU/SEI-2014-TR-008 CERT Division http://www.sei.cmu.edu Copyright 2013 Carnegie Mellon University This material is based upon work funded and supported by the Department of Defense under Contract No. FA8721-05-C-0003 with Carnegie Mellon University for the operation of the Software Engineering Institute, a federally funded research and development center. Any opinions, findings and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the United States Department of Defense. References herein to any specific commercial product, process, or service by trade name, trade mark, manufacturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by Carnegie Mellon University or its Software Engineering Institute. This report was prepared for the SEI Administrative Agent AFLCMC/PZM 20 Schilling Circle, Bldg 1305, 3rd floor Hanscom AFB, MA 01731-2125 NO WARRANTY. THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN “AS-IS” BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. -

Preventing and Combating the Trafficking of Girls in India Using Legal Empowerment Strategies Copyright © International Development Law Organization 2011
Preventing and Combating the Trafficking of Girls in India Using Legal Empowerment Strategies A Rights Awareness and Legal Assistance Program in Four Districts of West Bengal June 2010 – March 2011 Preventing and Combating the Trafficking of Girls in India Using Legal Empowerment Strategies Copyright © International Development Law Organization 2011 International Development Law Organization (IDLO) IDLO is an intergovernmental organization that promotes legal, regulatory and institutional reform to advance economic and social development in transitional and developing countries. Founded in 1983 and one of the leaders in rule of law assistance, IDLO's comprehensive approach achieves enduring results by mobilizing stakeholders at all levels of society to drive institutional change. Because IDLO wields no political agenda and has deep expertise in different legal systems and emerging global issues, people and interest groups of diverse backgrounds trust IDLO. It has direct access to government leaders, institutions and multilateral organizations in developing countries, including lawyers, jurists, policymakers, advocates, academics and civil society representatives. Among its activities, IDLO conducts timely, focused and comprehensive research in areas related to sustainable development in the legal, regulatory, and justice sectors. Through such research, IDLO seeks to contribute to existing Practice and scholarship on priority legal issues, and to serve as a conduit for the global exchange of ideas, best practices and lessons learned. IDLO produces a variety of professional legal tools covering interdisciplinary thematic and regional issues; these include book series, country studies, research reports, policy papers, training handbooks, glossaries and benchbooks. Research for these publications is conducted independently with the support of its country offices and in cooperation with international and national partner organizations. -

Womens' Empowerment
Directory of Voluntary Organisations Women’s Empowerment 2010 Documentation Centre for Women and Children (DCWC) National Institute of Public Cooperation and Child Development 5, Siri Institutional Area, Hauz Khas, New Delhi – 110016 Number of Copies: 100 Copyright: National Institute of Public Cooperation and Child Development, 2010 Project Team Project In-charge : Mrs. Meenakshi Sood Project Team : Ms. Renu Banker Ms. Alpana Kumari Computer Assistance : Mrs. Sandeepa Jain Mr. Abhishek Tiwari Acknowledgements : Ministry of Women and Child Development Planning Commission Voluntary Organisations Ministry of Rural Development Ministry of Panchayati Raj Ministry of Tribal Affairs Ministry of Urban Development DISCLAIMER All efforts have been made to verify and collate information about organisations included in the Directory. Information has been collected from various sources, namely directories, newsletters, Internet, proforma filled in by organisations, telephonic verification, letter heads, etc. However, NIPCCD does not take any responsibility for any error that may inadvertently have crept in. The address of offices of organisations, telephone numbers, e-mail IDs, activities, etc. change from time to time, hence NIPCCD may not be held liable for any incorrect information included in the Directory. Foreword Voluntary organisations play a very important role in society. They take up activities in the area of their expertise and provide support to the community in whose welfare they have interest. Social development has been ranked high on the priority list of Government programmes since Independence, and voluntary organisations have been equal partners in accelerating the pace of development. Being in close proximity to the community, voluntary organisations have done pioneering work in many areas, rendered productive services, highlighted several social problems, undertaken advocacy, and lobbied for the rights of the underprivileged. -

25 Legal Reforms for India
TOWARDS THE RULE OF LAW: 25 LEGAL REFORMS FOR INDIA www.vidhilegalpolicy.in TOWARDS THE RULE OF LAW: 25 LEGAL REFORMS FOR INDIA TOWARDS THE RULE OF LAW: 25 LEGAL REFORMS FOR INDIA The Vidhi Centre for Legal Policy is an independent legal policy advisory group whose mission is to achieve good governance in India by impacting legislative and regulatory design. Authors: Arghya Sengupta Alok Prasanna Kumar Debanshu Mukherjee Dhvani Mehta Ketan Paul Rukmini Das Srijoni Sen © Vidhi Centre for Legal Policy, 2014 Cover image has been licensed from Shutter StockTM . Image copyright © Shutter Stock, 2014 TOWARDS THE RULE OF LAW: 25 LEGAL REFORMS FOR INDIA The mandate of 2014 is unquestionably a watershed in Indian democracy. After nearly three decades, once again, a billion people have laid their hopes on a government to set India free. Almost six and a half decades after 26th January 1950, there are some institutional changes that have become necessary. The foremost is the process of appointment of judges. The Supreme Court of India, and the High Courts, have come to occupy a space of constitutional governance unlike their FOREWoRD counterparts elsewhere, and have played a vital part in the survival of democracy. They have ensured the sensitisation of the system to the need for transparency. It is therefore ironic that judges are appointed to these institutions by a process that is opaque, and as the current controversies establish, extremely fragile. The first reform suggested in this briefing book rightly addresses this issue. The second institution that can be given credit for ensuring the permeation of transparency through what was earlier an opaque government, is the media. -

Copyright Piracy and the Indian Film Industry: a “Realist” Assessment
BANERJEE ARTICLE (Do Not Delete) 10/28/2016 3:03 PM COPYRIGHT PIRACY AND THE INDIAN FILM INDUSTRY: A “REALIST” ASSESSMENT ARPAN BANERJEE* Abstract In India, the academic discourse surrounding intellectual property (IP) has been marked by great skepticism. Global IP laws have been viewed as a Western imposition detrimental to national interests. In this paper, I will make the case for a “realist” approach to film piracy in India, i.e., an approach that is rooted in legal pragmatism and draws from the New Legal Realism (NLR) movement. I will suggest a rough template for such an approach, referring to seven broad elements: a) international relations realism; b) contextualization of IP; c) contextualization of copyright; d) the views and interests of the film industry (including creators); e) the working of the pirate economy; f) Permission is hereby granted for noncommercial reproduction of this Article in whole or in part for education or research purposes, including the making of multiple copies for classroom use, subject only to the condition that the name of the author, a complete citation, and this copyright notice and grant of permission be included in all copies. *Alexander von Humboldt Foundation German Chancellor’s Fellow, Bucerius Law School, Hamburg (2016-17); Assistant Professor and Executive Director, Centre for Intellectual Property and Technology Law, Jindal Global Law School, India (on research leave). A shorter version of this paper was awarded first prize at the 9th ATRIP Essay Competition for Young Researchers in Intellectual Property Law (2015), and presented at the 35th ATRIP Congress at Jagiellonian University, Krakow, 26-29 July, 2016. -

A Heavy Hand: the Use of Force by India's Police
INDIA ARMED VIOLENCE ASSESSMENT Issue Brief Number 3 August 2012 A Heavy Hand The Use of Force by India’s Police There are many circumstances in Indian law grants extraordinary Any democratic society experiences, which the use of force by the police is discretionary powers of arrest to to varying degrees, tension between considered a legitimate action. police officers. the need for safeguards by the police Indeed, even in a democratic society, Although there is no independent and safeguards from the police. police are distinguished by their legal data available on police violence Order and liberty are both essential. authority to use force to coerce citizens and abuses, frequent use of force An authoritarian state can have (Klockars, 1985). Given the high poten is demonstrated by the occurrence virtually complete order without tial for the police to abuse force, of encounter killings1—a severe liberty, but it is impossible to have checks and balances are needed to symptom of police malfeasance. liberty without a minimum degree minimize the use of force and make The most important reforms for con of order enforcement. Democratic officers accountable when they resort trolling the misuse of force by the societies seek to avoid the extremes to it. police have come from the 1993 Na of both anarchy and repression India has approximately 2.4 million tional Human Rights Commission. (Manning, 2010). The police in India men and women in official policing Incidents of excessive use of force are faced with a similar challenge. (IISS, 2011; NCRB, 2011). Their work is by police are unlikely to be The need for coercive policing to regulated by the Indian Constitution, addressed until major reforms in maintain order has been a constant by statute and case law, and by the the criminal justice system are put theme of Indian rule (Rai, 1999). -

Army Journal 2021-22
ISSN 0975-8208 A S P I R E T R U T H I S G O D Army Institute of Law Journal Volume XIV 2021 Peer Reviewed Journal Vol. XIV, 2021 Refereed Journal Since 2006 Listed in UGC-CARE List, 2021 ARMY INSTITUTE OF LAW JOURNAL Vol. XIV, 2021 (ISSN: 0975-8208) Registration No. PUNENG/2007/25057 PATRON Maj Gen Vikram Taneja Chairman, Army Institute of Law EDITOR-IN-CHIEF Dr Tejinder Kaur Principal PUBLICATION-IN-CHARGE Dr Puja Jaiswal Assistant Professor of Law EDITOR Dr Harpreet Kaur Assistant Professor of Law STUDENT EDITOR Mr Shiekhar Panwar B.A. LL.B. 3rd Year Disclaimer: The views expressed in the Articles and all other contributions to the “AIL Journal 2021” singularly belong to the individual authors and do not belong to the Editorial Board or the Army Institute of Law. No part of this publication may be reproduced or transmitted in any form by any means, or stored in any system of any nature without prior permission. Applications for permission to use the material shall be made to the publisher. Although every care has been taken to avoid errors or omissions, this journal is being sold on the condition that information given in this journal is merely for reference and must not be taken as having authority or binding in any way on the authors, publishers and sellers who do not owe any responsibility for any damage or loss to any person, for the result of any action taken on the basis of this work. Copyright © 2021 The Army Institute of Law, Mohali, Punjab. -

COASTAL SECURITY the Indian Experience
IDSA Monograph Series No. 22 September 2013 COASTAL SECURITY The Indian Experience PUSHPITA DAS COASTAL SECURITY: THE INDIAN EXPERIENCE 1 IDSA Monograph Series No. 22 September 2013 COASTAL SECURITY: THE INDIAN EXPERIENCE PUSHPITA DAS 2 | PUSHPITA DAS Institute for Defence Studies and Analyses, New Delhi. All rights reserved. No part of this publication may be reproduced, sorted in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photo-copying, recording or otherwise, without the prior permission of the Institute for Defence Studies and Analyses (IDSA). ISBN: 978-93-82169-22-2 Disclaimer: The views expressed in this Monograph are those of the author and do not necessarily reflect those of the Institute or the Government of India. First Published: September 2013 Price: Rs. 250/- Published by: Institute for Defence Studies and Analyses No.1, Development Enclave, Rao Tula Ram Marg, Delhi Cantt., New Delhi - 110 010 Tel. (91-11) 2671-7983 Fax.(91-11) 2615 4191 E-mail: [email protected] Website: http://www.idsa.in Layout & Cover by: Vaijayanti Patankar Printed at: M/S A. M. Offsetters A-57, Sector-10, Noida-201 301 (U.P.) Mob: 09810888667 E-mail: [email protected] COASTAL SECURITY: THE INDIAN EXPERIENCE 3 CONTENTS Chapters Page no Acknowledgements ...................................................................... 5 Introduction ................................................................................ 7 1. Threats and Challenges to Coastal Security .................. 21 2. Evolution of