A Collection of Papers from the 2017 Conference Series and Nuclear Scholars Initiative
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Appendix 7 Investment in Independent Production
APPENDIX 7 INVESTMENT IN INDEPENDENT PRODUCTION ABRIDGED Appendix 7 - Expenditures on Programming and Development on Independent Productions in Quebec (Condition of licence 23) CBC English Television 2019-2020 SUMMARY Programming Expenditure* All Independents* Quebec independents Percentage 131,425,935 5,895,791 4.5% Development Expenditures All Independents Quebec independents Percentage #### #### 8.5% Note: * Expenses as shown in Corporation's Annual Reports to the Commission, line 5 (Programs acquired from independent producers), Direct Operation Expenses section. Appendix 7-Summary Page 1 ABRIDGED APPENDIX 7 - CANADIAN INDEPENDENT PRODUCTION EXPENDITURES - DETAILED REPORT CBC English Television 2019-2020 Program Title Expenditures* Producer / Address Producer's Province A Cure For What Hails You - 2013 #### PYRAMID PRODUCTIONS 1 INC 2875 107th Avenue S.E. Calgary Alberta Alberta Digging in the Dirt #### Back Road Productions #102 – 9955 114th Street Edmonton Alberta Alberta Fortunate Son #### 1968 Productions Inc. 2505 17TH AVE SW STE 223 CALGARY Alberta Alberta HEARTLAND S 1-7 #### Rescued Horse Season Inc. 223, 2505 - 17th Avenue SW Calgary Alberta Alberta HEARTLAND S13 #### Rescued Horse Season Inc. 223, 2505 - 17th Avenue SW Calgary Alberta Alberta HEARTLAND X #### Rescued Horse Season Inc. 223, 2505 - 17th Avenue SW Calgary Alberta Alberta HEARTLAND XII #### Rescued Horse Season Inc. 223, 2505 - 17th Avenue SW Calgary Alberta Alberta Lonely #### BRANDY Y PRODUCTIONS INC 10221 Princess Elizabeth Avenue Edmonton, Alberta Alberta Narii - Love and Fatherhood #### Hidden Story Productions Ltd. 347 Sierra Nevada Place SW Calgary Alberta T3H3M9 Alberta The Nature Of Things - A Bee's Diary #### Bee Diary Productions Inc. #27, 2816 - 34 Ave Edmonton Alberta Alberta A Shine of Rainbows #### Smudge Ventures Inc. -
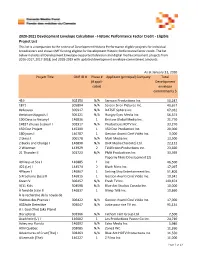
CMF 2020-2021 Development Historic Performance Project List.Xlsx
2020‐2021 Development Envelope Calculation ‐ Historic Performance Factor Credit ‐ Eligible Project List This list is a companion to the review of Development Historic Performance eligible projects for individual broadcasters and shows CMF funding eligible for Development Historic Performance factor credit. The list below includes all Development Envelope‐supported television and digital media component projects from 2016‐2017, 2017‐2018, and 2018‐2019 with updated development envelope commitment amounts. As at January 31, 2020 Project Title CMF ID # Phase # Applicant (principal) Company Total (if appli‐ Development cable) envelope commitments $ 419 302150 N/A Sarrazin Productions Inc. 50,247 1871 305894 N/A Screen Siren Pictures Inc. 40,657 #elleaussi 305917 N/A DATSIT Sphère inc. 67,032 #relationshipgoals I 305121 N/A Hungry Eyes Media Inc. 56,374 100 Days to Victory I 146836 1 Bristow Global Media Inc. 21,770 14837 choses à savoir I 302917 N/A Productions KOTV Inc. 33,270 150 Doc Project 145309 1 150 Doc Production Inc. 20,000 180 jours I 146787 1 Gestion Avanti Ciné Vidéo Inc. 3,000 2 bleus I 306578 N/A Maki Media inc 13,500 2 Bucks and Change I 146890 N/A DHX Media (Toronto) Ltd. 22,112 2 Wiseman 143929 2 Téléfiction Productions inc. 23,660 21 Thunder II 301723 N/A PMA Productions Inc. 33,369 Paperny Films Development (2) 40 Days at Sea I 146885 1 Inc. 46,500 422 (Le) I 144574 2 Blach Films Inc. 17,097 4Player I 146867 1 Sinking Ship Entertainment Inc. 51,806 5 Prochains (Les) III 146815 1 Gestion Avanti Ciné Vidéo Inc. -

Honorary Police and the Parish Hall Enquiry System in the Channel Island of Jersey
_________________________________________________________________________Swansea University E-Theses Constructing justice in an island community: honorary police and the parish hall enquiry system in the Channel Island of Jersey. Miles, Helen M How to cite: _________________________________________________________________________ Miles, Helen M (2007) Constructing justice in an island community: honorary police and the parish hall enquiry system in the Channel Island of Jersey.. thesis, Swansea University. http://cronfa.swan.ac.uk/Record/cronfa42251 Use policy: _________________________________________________________________________ This item is brought to you by Swansea University. Any person downloading material is agreeing to abide by the terms of the repository licence: copies of full text items may be used or reproduced in any format or medium, without prior permission for personal research or study, educational or non-commercial purposes only. The copyright for any work remains with the original author unless otherwise specified. The full-text must not be sold in any format or medium without the formal permission of the copyright holder. Permission for multiple reproductions should be obtained from the original author. Authors are personally responsible for adhering to copyright and publisher restrictions when uploading content to the repository. Please link to the metadata record in the Swansea University repository, Cronfa (link given in the citation reference above.) http://www.swansea.ac.uk/library/researchsupport/ris-support/ Constructing Justice in an Island Community: Honorary Police and the Parish Hall Enquiry System in the Channel Island of Jersey Helen M. Miles Submitted to the University of Wales in fulfilment of the requirements for the Degree of Doctor of Philosophy Swansea University November 2007 ProQuest Number: 10797959 All rights reserved INFORMATION TO ALL USERS The quality of this reproduction is dependent upon the quality of the copy submitted. -

Copyright © 2014 Patrick James Schreiner All Rights Reserved. The
Copyright © 2014 Patrick James Schreiner All rights reserved. The Southern Baptist Theological Seminary has permission to reproduce and disseminate this document in any form by any means for purposes chosen by the Seminary, including, without limitation, preservation, or instruction. PEOPLE AND PLACE: A SPATIAL ANALYSIS OF THE KINGDOM IN MATTHEW __________________ A Dissertation Presented to the Faculty of The Southern Baptist Theological Seminary __________________ In Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy __________________ by Patrick James Schreiner December 2014 APPROVAL SHEET PEOPLE AND PLACE: A SPATIAL ANALYSIS OF THE KINGDOM IN MATTHEW Patrick James Schreiner Read and Approved by: __________________________________________ Jonathan T. Pennington (Chair) __________________________________________ Gregg R. Allison __________________________________________ Robert L. Plummer Date ______________________________ To Hannah, with whom I have made the vow of the “Shining Barrier” TABLE OF CONTENTS Page LIST OF ABBREVIATIONS . vii LIST OF TABLES . ix LIST OF FIGURES . x PREFACE . xi Chapter Part 1: Space: The Final Frontier 1. THE ECLIPSE OF SPACE. 1 A Spatial Turn and Biblical Studies . 9 Thesis . 12 Outline of Argument . 17 2. THE PRESENCE OF JESUS AND THE SPATIAL KINGDOM . 20 Introduction . 20 Immanuel . 21 The Spatial Kingdom in Matthew . 28 Conclusion . 38 3. SPATIAL THEORY . 41 Spatial Theory . 41 Critical Spatiality . 52 Conclusion . 58 iv Chapter Page Part 2: Jesus vs. Beelzebul 4. LORD OF HEAVEN AND EARTH . 61 Introduction . 60 Beelzebul and the Baal Cycle . 65 Conclusion . 82 5. IF BY THE SPIRIT: THE SPIRIT, THE SPATIAL KINGDOM AND THE NEW EXODUS . 84 Exorcisms as Spatial and Body Oriented . 84 The Spirit in Matthew . -

Alaskan Malamute AKC Champions
CH date Champ Name Sex DOB Sire Dam CH Aabara of Redhorse D 8/25/1953 Moosecat M'Loot Banshee of Husky-Pak 11/17/2006 CH Abenaki's Hot Piece Of Ice B 1/28/2004 Quinault's Catch Me If Yukon Quinault's Haulin Ice 10/16/2011 CH Abenaki's I'Ll Take Allavit D 9/7/2007 Sno Shire's Center Ice Nanuke's I'Ll Have Nunavit 12/31/1979 CH Acadia's Christmas Cajun B 10/23/1972 Cajun Serjeant Acadia's Nina Nikki of Amorok CH Acadia's Nina Nikki of Amorok B 9/26/1970 Winterhaven's Kotzebue Cajun Winterhaven's Gypsy of Amorok 12/31/1976 CH Acadia's Panda of Arctica B 2/10/1972 Winterhaven's Kotzebue Cajun Delilah of North Wind 12/31/1976 CH Acadia's Ragin' Cajun D 10/10/1973 Cajun Serjeant Acadia's Nina Nikki of Amorok 12/31/1982 CH Acadia's Tundra Star D 10/30/1977 Tigara's Corinthian Cajun Tigara's C'Est Bonne of Tumleh 12/31/1984 CH Acamar's Rassmus D 3/19/1981 Sunak's Hyak Naksala's Capella 4/15/2011 CH Adair 'N' Hug 501 Buttonfly At Ixa D 11/10/2009 Frostfield All About Alex Aurora Adair'N'Hug Trolley 6/25/2005 CH Adair 'N' Hug Antarctic Emperor D 12/15/2000 Nanukes Lockport Louie Adair 'N' Hug Echo of Staghorn 5/18/2012 CH Adair 'N' Hug Brand New Day B 4/4/2010 Adair'n'hug S Wonderful Life Adair'N'Hug My Favorite One 10/15/2004 CH Adair N Hug Divine Design B Williwaw's River Dance Atanik Adair'n'hug By Grace 4/12/2003 CH Adair 'N' Hug Echo of Louie D 12/15/2000 Nanukes Lockport Louie Adair 'N' Hug Echo of Staghorn 2/15/1999 CH Adair 'N' Hug Echo of Staghorn B 8/31/1997 Nanukes Take No Prisoners Staghorn's Serene Siren 6/25/2002 CH Adair 'N' Hug Futures -

RCAFJ 2013 Fall 1. Editor's Message 2
IN THIS ISSUE “BIG WAR” AIR POWER FOR “SMALL WAR” OPERATIONS A RETURN TO ROYAL CANADIAN AIR FORCE RANKS: A HISTORICAL EXAMINATION ROYAL CANADIAN AIR FORCE OPERATIONAL-LEVEL EDUCATION: AN UPDATE TERMINOLOGY TALK - ARTICLE 5 AIRMINDEDNESS: AN ESSENTIAL ELEMENT OF AIR POWER AND MUCH MORE! THE ROYAL CANADIAN AIR FORCE JOURNAL is an official publication of the Commander Royal Canadian Air Force (RCAF) and is published quarterly. It is a forum for discussing concepts, issues and ideas that are both crucial and central to aerospace power. The Journal is dedicated to disseminating the ideas and opinions of not only RCAF personnel, but also those civilians who have an interest in issues of aerospace power. Articles may cover the scope of air force doctrine, training, leadership, lessons learned and air force operations: past, present or future. Submissions on related subjects such as ethics, technology and air force history are also invited. This Journal is therefore dedicated to the expression of mature professional thought on the art and science of air warfare and is central to the intellectual health of the RCAF. It ser ves as a vehicle for the continuing education and professional development of all ranks and personnel in the RCAF as well as members from other environments, employees of government agencies and academia concerned with air force affairs. EDITORIAL STAFF Editor-in-Chief: Colonel Martin Cournoyer, CD Senior Editor: Major William March, CD, MA EDITORIAL BOARD Colonel William Lewis (Retired), OMM, CD, M Eng, M Ed, MBA, MDS, PhD Lieutenant-Colonel -

THE LEADING SOURCE for PROGRAM INFORMATION LIST 0419__Layout 1 3/17/19 4:51 PM Page 1 *LIST 419 ALT2.Qxp LIS 1006 LISTINGS 3/21/19 10:49 AM Page 3
*LIST_0418_COVER_LIS_1006_LISTINGS 3/21/19 4:00 PM Page 1 WWW.WORLDSCREENINGS.COMTVLISTINGS APRIL 2019 MIPTV EDITION THE LEADING SOURCE FOR PROGRAM INFORMATION LIST_0419__Layout 1 3/17/19 4:51 PM Page 1 *LIST_419_ALT2.qxp_LIS_1006_LISTINGS 3/21/19 10:49 AM Page 3 IN THIS ISSUE TV LISTINGS 3 Xavier Riddle and the Secret Museum (w.t.) 3 21 4K MEDIA O (Kids 4-7 animation adventure comedy, 74x11 4K Media Jetpack Distribution (1-212) 590-2100 min. & 1x55 min.) Follow the adventures of 9 Story Media Group Xavier, Yadina and Brad as they travel back in Kanal D International Stand: R7.B12 time to meet famous heroes of the past and 4 Keshet International Contact: Jennifer Buzzelli, sales cnslt.; Kristen learn how to be their own heroes of the present. Gray, GM, SVP, operations & business & legal A+E Networks Kew Media Distribution affairs; Mark Kirk, SVP, digital. ABS-CBN Corporation Lightning International PROGRAM HIGHLIGHTS Albatross World Sales 22 Yu-Gi-Oh! VRAINS (Animation, 46x30 min.) Alfred Haber Distribution Duelists worldwide plug into LINK VRAINS to all3media international Lionsgate Entertainment compete in fast-paced competition. But this cyberspace is under attack by a team of hackers 6 Madd Entertainment determined to destroy the virtual realm. Allspark (formerly Hasbro Studios) MarVista Entertainment Yu-Gi-Oh! The Dark Side of Dimensions APC Kids Mattel (Animation, 1x110 min.) A decade after the finale that bid farewell to the franchise’s original story- Armoza Formats Mediatoon Distribution line, this movie marks the return of the original Moon and Me Artist View Entertainment 23 creator, the iconic hero and the classic charac- Atlantyca Entertainment ters idolized worldwide. -

FMC Credit Rendement Historique De
Crédit de rendement historique pour le calcul des Enveloppes de développement 2021‐2022 – Liste des projets admissibles Cette liste accompagne l’évaluation des projets admissibles à des crédits de rendement historique de développement par télédiffuseur et montre le financement admissible du FMC pour le crédit de rendement historique. La liste ci‐dessous comprend tous les projets financés par une enveloppe de développement en 2017‐2018, 2018‐2019 et 2019‐2020 et les montants mis à jour des engagements. En date du 31 décembre 2020 Titre du projet No d’identi‐ Année de Société requérante Montant total (en fication du financement (principale) dollars) des FMC du FMC engagements $ #elleaussi 305917 2018‐2019 Sphère Média inc. 67 032 #relationshipgoals I 305121 2018‐2019 Hungry Eyes Media Inc. 56 374 10‐4 I 309538 2019‐2020 Gestion Avanti Ciné Vidéo Inc. 16 839 14837 choses à savoir I 302917 2017‐2018 Productions KOTV Inc. 33 270 1871 305894 2018‐2019 Screen Siren Pictures Inc. 40 657 2 bleus I 306578 2018‐2019 Maki Media inc 13 500 21 Thunder II 301723 2017‐2018 PMA Productions Inc. 33 369 419 302150 2017‐2018 Sarrazin Productions Inc. 50 247 419 307045 2019‐2020 Sarrazin Productions Inc. 55 489 6teen V 306457 2018‐2019 Fresh TV Inc. 149 874 9/11 Kids 304598 2018‐2019 Blue Ant Studios Canada Inc. 10 000 À fond de train V 309567 2019‐2020 GROUPE BLIMP INC. 16 373 À la recherche de la noyée de Rivières des Prairies I 306422 2018‐2019 Gestion Avanti Ciné Vidéo Inc. 12 616 A$$hole Detective 303047 2017‐2018 Juste pour rire TV inc. -

CMF 2021-2022 Development Historic Performance Project List.Xlsx
2021‐2022 Development Envelope Calculation ‐ Historic Performance Factor Credit ‐ Eligible Project List This list is a companion to the review of Development Historic Performance eligible projects for individual broadcasters and shows CMF funding eligible for Development Historic Performance factor credit. The list below includes all Development Envelope‐supported projects from 2017‐2018, 2018‐2019, and 2019‐2020 with updated development envelope commitment amounts. As at December 31, 2020 Project Title CMF ID # Year of Applicant (principal) Company Total CMF Development Funding envelope commitments $ #elleaussi 305917 2018‐2019 Sphère Média inc. 67,032 #relationshipgoals I 305121 2018‐2019 Hungry Eyes Media Inc. 56,374 10‐4 I 309538 2019‐2020 Gestion Avanti Ciné Vidéo Inc. 16,839 14837 choses à savoir I 302917 2017‐2018 Productions KOTV Inc. 33,270 1871 305894 2018‐2019 Screen Siren Pictures Inc. 40,657 2 bleus I 306578 2018‐2019 Maki Media inc 13,500 21 Thunder II 301723 2017‐2018 PMA Productions Inc. 33,369 419 302150 2017‐2018 Sarrazin Productions Inc. 50,247 419 307045 2019‐2020 Sarrazin Productions Inc. 55,489 6teen V 306457 2018‐2019 Fresh TV Inc. 149,874 9/11 Kids 304598 2018‐2019 Blue Ant Studios Canada Inc. 10,000 À fond de train V 309567 2019‐2020 GROUPE BLIMP INC. 16,373 À la recherche de la noyée de Rivières des Prairies I 306422 2018‐2019 Gestion Avanti Ciné Vidéo Inc. 12,616 A$$hole Detective 303047 2017‐2018 Juste pour rire TV inc. 91,134 A.I. God (The) (aka Planet Disruptors) 303366 2017‐2018 Fathom Film Group Ltd. -

Elder-At-The-Fire: Missional Generativity Jo A
Digital Commons @ George Fox University Doctor of Ministry Theses and Dissertations 2-25-2016 Elder-At-The-Fire: Missional Generativity Jo A. Harlow George Fox University, [email protected] This research is a product of the Doctor of Ministry (DMin) program at George Fox University. Find out more about the program. Recommended Citation Harlow, Jo A., "Elder-At-The-Fire: Missional Generativity" (2016). Doctor of Ministry. Paper 131. http://digitalcommons.georgefox.edu/dmin/131 This Dissertation is brought to you for free and open access by the Theses and Dissertations at Digital Commons @ George Fox University. It has been accepted for inclusion in Doctor of Ministry by an authorized administrator of Digital Commons @ George Fox University. For more information, please contact [email protected]. GEORGE FOX UNIVERSITY ELDER-AT-THE-FIRE: MISSIONAL GENERATIVITY A DISSERTATION SUBMITTED TO THE FACULTY OF GEORGE FOX EVANGELICAL SEMINARY IN CANDIDACY FOR THE DEGREE OF DEPARTMENT OF MINISTRY BY JO A. HARLOW PORTLAND, OREGON FEBRUARY 2016 George Fox Evangelical Seminary George Fox University Portland, Oregon CERTIFICATE OF APPROVAL ________________________________ DMin Dissertation ________________________________ This is to certify that the DMin Dissertation of Jo A. Harlow has been approved by the Dissertation Committee on February 25, 2016 for the degree of Doctor of Ministry in Semiotics and Future Studies. Dissertation Committee: Primary Advisor: Derek Voorhees, DMin Secondary Advisor: W. David Phillips, DMin Lead Mentor: Leonard I. Sweet, PhD Expert Advisor: W. David Phillips, DMin Copyright © 2016 by Jo A. Harlow All rights reserved. All biblical quotations are from the New International Version unless otherwise noted. ii This project is dedicated to the memory of: My grandmother, Mary E. -

CMPA (Formerly CFTPA) Signatory Producers 2015 to 2017 (Extended to June 30, 2019) Animation up to April 9, 2019
CMPA (formerly CFTPA) Signatory Producers 2015 to 2017 (extended to June 30, 2019) Animation up to April 9, 2019 1380099 Ontario Inc (c.o.b. Heroic Film Company) for ""Captain Flamingo 1380099 Ontario Incorporated (c.o.b. Heroic Film Company) for ""Capta 1722065 Ontario Inc. for ""Oops 'n Daisy"" 1757712 Ontario, Inc for "Wild Kratts" 2245988 Ontario Ltd for ""DOT"" 2311545 Ontario Inc., 2492765 Ontario Inc. (to be renamed Pipe Dream Development Ltd.) for ""Mia & Codie"" 2576344 Ontario Inc. for ""The Book Hungry Bears"" 3A Productions Inc. for ""The 3 Amigonauts"" 6Teen Productions (Season 4), Ltd. For "6Teen cycle 4" 6Teen Productions Inc. for ""6Teen (Season III)"" 9 Story Development Inc. for ""Full Metal Janet"" 9 Story Development Inc for ""Bewitched"" 9 Story Development Inc for ""Dog & Pony Show"" 9 Story Development Inc for ""Joe Meteor"" 9 Story Development Inc for ""Julia Child"" 9 Story Development Inc for ""Top Wing"" 9 Story Development Inc. for ""Alexaland"" 9 Story Development Inc. for ""Apocalicious"" 9 Story Development Inc. for ""Dylan"" 9 Story Development Inc. for ""Heck"" 9 Story Development Inc. for ""Karma's World"" 9 Story Development Inc. for ""Little Critter"" 9 Story Development Inc. for ""Open Season"" 9 Story Development Inc. for ""Otis"" 9 Story Development Inc. for ""Schnarg"" 9 Story Development Inc. for ""Space Cadets"" 9 Story Development Inc. for ""Top Wing II"" 9 Story Entertainment Inc for ""Beluga Bay"" 9 Story Entertainment Inc for ""Hugo & Dash"" 9 Story Entertainment Inc for "Julia, Child" 9 Story Entertainment Inc for ""Super Movers (aka Imagination Movers) 9 Story Entertainment Inc. for ""Almost Naked Animals"" 9 Story Entertainment Inc. -

Selecttv-City Layout 1
Changing the Conversation About Mental Health 1.5 x 2.5” ad Sullivan A Publication of The Chronicle Journal September 18 - 24, 2021 ‘The Wonder Years’ returns, For more information or to order, contact: but with a new cast and place WAKEFIELD OIL CHANGE www.wakefieldoilcheck.com Elisha “EJ” Williams stars in a new version of Phone: 807-345-1121 3 x 5” ad “The Wonder Years” premiering Wednesday on CTV and ABC. Wakefield Oil City BY JAY BOBBIN SelectTV® Published every Saturday by The Chronicle-Journal New characters live At 75 South Cumberland Street, Thunder Bay Ont. P7B 1A3 Hilda Caverly, Interim General Manager, Director of Finance and Circulation ‘The Wonder Years’ in reboot Phone 343-6200 or Toll-free 1-800-465-3914 CHANNEL GUIDE Broadcast Q r Cable Qr Bell ExpressVu/Star Choice 49/49 ^ 210/37 CBLT - CBC Toronto H 509/504 CNBC , # 90/707 CBLFT - CBC French/Toronto I 508/502 CNN Headline News ^ % 223/304 CKPR - CTV/Thunder Bay -/- Broadcast News $ & 222/314 CHFD - Thunder Bay K 618/524 DTOUR _ -/- KSTP - ABC/Minneapolis L 554/544 Teletoon ) ( 265/353 TV Ontario M 556/540 Family Channel ) 400/424 TSN - The Sports Network N 294/529 WPCH - Ind./Atlanta * -/- Shaw Cable TV O 625/548 The Comedy Network + -/- WCCO - CBS/Minneapolis P 292/539 Turner Classic Movies , -/- KTCA - PBS/Minneapolis Q 603/561 The Food Network - -/- KARE - NBC/Minneapolis R 411/457 Outdoor Life . 570/580 Much Music S 522/506 History Television / 501/391 CTV NEWSNET T 627/528 Space A new version of “The 0 502/390 CBC Newsworld U 293/609 AMC Wonder Years” premieres Wednesday on CTV and ABC.