ELF Cybersecurity Guide 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Transnational Party Alliances Influence National Parties' Policies
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by ZORA Zurich Open Repository and Archive University of Zurich Main Library Strickhofstrasse 39 CH-8057 Zurich www.zora.uzh.ch Year: 2021 How Transnational party alliances influence national parties’ policies Senninger, Roman ; Bischof, Daniel ; Ezrow, Lawrence Abstract: Previous research reports that parties in established European democracies learn from and em- ulate the successful election strategies of foreign incumbents, i.e., successful parties are influential abroad. We theorize that—in addition to incumbency (or success)—exchange takes place through transnational party alliances in the European Union. Relying on party manifesto data and spatial econometric analyses, we show that belonging to the same European Parliament (EP) party group enhances learning and em- ulation processes between national political parties. Estimated short- and long-term effects are approxi- mately two and three times greater when foreign incumbents are in the same EP party group compared to other foreign incumbents. Our results have implications for our understanding of how transnational party groups influence national parties’ policy positions. DOI: https://doi.org/10.1017/psrm.2020.55 Posted at the Zurich Open Repository and Archive, University of Zurich ZORA URL: https://doi.org/10.5167/uzh-196868 Journal Article Accepted Version The following work is licensed under a Creative Commons: Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0) License. Originally published at: Senninger, Roman; Bischof, Daniel; Ezrow, Lawrence (2021). How Transnational party alliances influence national parties’ policies. Political Science Research and Methods:Epub ahead of print. -

Austrian Music Export Handbook
Austrian Music Export Handbook Table of Contents Imprint.................................................................................................................................................................................................. 5 Introduction........................................................................................................................................................................................ 6 PART 1 - GENERAL INFORMATION.................................................................................................................................................... 7 Geogr p!ic l # t nd Tr n$port In%r $tructure.............................................................................................................. 7 Gener l In%ormation ................................................................................................................................................................ 7 Town$ nd Citie$ ...................................................................................................................................................................... ( Admini$tr ti)e #i)i$ion$......................................................................................................................................................... * Tr n$port +Touring in Au$tri ,.............................................................................................................................................. * Import nt Cont ct$, Re" ted Lin.$ .............................................................................................................................. -

ESS9 Appendix A3 Political Parties Ed
APPENDIX A3 POLITICAL PARTIES, ESS9 - 2018 ed. 3.0 Austria 2 Belgium 4 Bulgaria 7 Croatia 8 Cyprus 10 Czechia 12 Denmark 14 Estonia 15 Finland 17 France 19 Germany 20 Hungary 21 Iceland 23 Ireland 25 Italy 26 Latvia 28 Lithuania 31 Montenegro 34 Netherlands 36 Norway 38 Poland 40 Portugal 44 Serbia 47 Slovakia 52 Slovenia 53 Spain 54 Sweden 57 Switzerland 58 United Kingdom 61 Version Notes, ESS9 Appendix A3 POLITICAL PARTIES ESS9 edition 3.0 (published 10.12.20): Changes from previous edition: Additional countries: Denmark, Iceland. ESS9 edition 2.0 (published 15.06.20): Changes from previous edition: Additional countries: Croatia, Latvia, Lithuania, Montenegro, Portugal, Slovakia, Spain, Sweden. Austria 1. Political parties Language used in data file: German Year of last election: 2017 Official party names, English 1. Sozialdemokratische Partei Österreichs (SPÖ) - Social Democratic Party of Austria - 26.9 % names/translation, and size in last 2. Österreichische Volkspartei (ÖVP) - Austrian People's Party - 31.5 % election: 3. Freiheitliche Partei Österreichs (FPÖ) - Freedom Party of Austria - 26.0 % 4. Liste Peter Pilz (PILZ) - PILZ - 4.4 % 5. Die Grünen – Die Grüne Alternative (Grüne) - The Greens – The Green Alternative - 3.8 % 6. Kommunistische Partei Österreichs (KPÖ) - Communist Party of Austria - 0.8 % 7. NEOS – Das Neue Österreich und Liberales Forum (NEOS) - NEOS – The New Austria and Liberal Forum - 5.3 % 8. G!LT - Verein zur Förderung der Offenen Demokratie (GILT) - My Vote Counts! - 1.0 % Description of political parties listed 1. The Social Democratic Party (Sozialdemokratische Partei Österreichs, or SPÖ) is a social above democratic/center-left political party that was founded in 1888 as the Social Democratic Worker's Party (Sozialdemokratische Arbeiterpartei, or SDAP), when Victor Adler managed to unite the various opposing factions. -
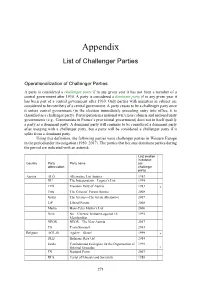
Challenger Party List
Appendix List of Challenger Parties Operationalization of Challenger Parties A party is considered a challenger party if in any given year it has not been a member of a central government after 1930. A party is considered a dominant party if in any given year it has been part of a central government after 1930. Only parties with ministers in cabinet are considered to be members of a central government. A party ceases to be a challenger party once it enters central government (in the election immediately preceding entry into office, it is classified as a challenger party). Participation in a national war/crisis cabinets and national unity governments (e.g., Communists in France’s provisional government) does not in itself qualify a party as a dominant party. A dominant party will continue to be considered a dominant party after merging with a challenger party, but a party will be considered a challenger party if it splits from a dominant party. Using this definition, the following parties were challenger parties in Western Europe in the period under investigation (1950–2017). The parties that became dominant parties during the period are indicated with an asterisk. Last election in dataset Country Party Party name (as abbreviation challenger party) Austria ALÖ Alternative List Austria 1983 DU The Independents—Lugner’s List 1999 FPÖ Freedom Party of Austria 1983 * Fritz The Citizens’ Forum Austria 2008 Grüne The Greens—The Green Alternative 2017 LiF Liberal Forum 2008 Martin Hans-Peter Martin’s List 2006 Nein No—Citizens’ Initiative against -

Wandel Verstehen. Rechte Schützen. Zukunft Gestalten
Friedrich Naumann STIFTUNG FÜR DIE FREIHEIT Wandel verstehen. Rechte schützen. Zukunft gestalten. www.freiheit.org 1963 bis 2013 Jubiläumsschrift Herausgegeben vom Bereich Internationale Politik der Friedrich-Naumann-Stiftung für die Freiheit Gemeinsames Vorwort Internationale Projekte 84 Dr. Wolfgang Gerhardt MdB, Vorsitzender des Vorstandes Nord-Süd-Dialogprogramm am Sitz der Vereinten Nationen, New York 85 Prof. Dr. Jürgen Morlok, Vorsitzender des Kuratoriums 4 Internationale Akademie für Führungskräfte (IAF) 87 Geleitworte Internationale Konferenzen 91 Dr. Guido Westerwelle, Bundesminister des Auswärtigen 6 Internationale Programme 99 Dirk Niebel, Bundesminister für wirtschaftliche Zusammenarbeit und Entwicklung 7 Internationale Kooperation und Vernetzung 100 Wie alles begann. 10 Die bedeutende Rolle der Kooperationspartner 101 Entstehung und Aufbau der internationalen Arbeit Interview mit Dr. Barthold C. Witte 11 Intensive Vernetzung mit nationalen, regionalen und globalen Akteuren 102 Pionierprojekte der Aufbauphase 18 Weltweite Bilanz und künftige Herausforderungen 104 Regionale Schwerpunkte und Projektentwicklungen 24 Bilanz eines halben Jahrhunderts internationaler Arbeit Autor: Dr. h.c. Rolf Berndt, Geschäftsführendes Vorstandsmitglied 105 Südliche Mittelmeerländer (Naher und Mittlerer Osten) 25 Neue Herausforderungen und strategische Ziele für die Auslandsarbeit Subsahara-Afrika 31 Autor: Ulrich Niemann, Bereichsleiter Internationale Politik 111 Lateinamerika 39 Südost- und Ostasien 46 Südasien 54 Mittel-, Südost- und Osteuropa, -

The Impact of the Financial Crisis on European Solidarity
FUTURE OF EUROPEAN INTEGRATION: THE IMPACT OF FINANCIAL CRISIS ON EUROPEAN SOLIDARITY A conference organised by the European Liberal Forum asbl (ELF) with the support of the Friedrich Naumann Foundation for Freedom (Germany), the Centre for Liberal Studies (Czech Republic). With the special support of the Association for International Affairs (Czech Republic). Funded by the European Parliament. Official media coverage by EurActiv.cz. Prague, 6 September 2012 Venue: Kaiserstein Palace, Malostranské náměstí 23/37, 110 00 Prague 1, Czech Republic Contents Synopsis ...................................................................3 Panel #1 ...................................................................4 Panel #2 ...................................................................5 Panel #3 ...................................................................6 Programme .................................................................7 Speakers ...................................................................9 Team ......................................................................14 European Liberal Forum .......................................................15 Friedrich Naumann Foundation for Freedom .......................................17 Association for International Affairs ...............................................18 Logos of organizers and partners . .19 2 Synopsis Although the ongoing crisis in the EU is primarily depicted by the media as an economic one (the “Greek Crisis” or, more precisely, the “Sovereign Debt Crisis”), -

Download All with Our Work on a Daily Basis, All Year Round
EUROPEAN LIBERAL FORUM ANNUAL REPORT 2016 WELCOME ANNUAL REPORT 2016 EUROPEAN LIBERAL FORUM COPYRIGHT 2017 EUROPEAN LIBERAL© FORUM ASBL. All rights reserved. Content is subject to copyright. Any use and re-use requires approval. This publication was co-funded by the European Parliament. The European Parliament is not responsible for the content of this publication, or for any use that may be made of it. WELCOME CONTENTS THE ELF ANNUAL REPORT 2016 WELCOME 02 Letter From the President 04 Foreword by the Executive Director 05 GET TO KNOW US 06 Our Brochures | Connect With Us 07 Where Did You Meet Us in 2016? 08 OUR FOCUS 09 SECURITY EU Defence and Security Policies – Making Europe Safer for Citizens 10 ENERGY AND ENVIRONMENT Europe’s Energy Future 12 MIGRATION AND INTEGRATION Liberal Answers to Challenges on Sea Liberal Answers to Challenges on Land Integration Through Education 14 EUROPEAN VALUES Ralf Dahrendorf Roundtable: Talk for Europe 16 DIGITALISATION Digital Security Duet: Making European Cyber Defences More Resilient Through Public-Private Partnerships 18 List of all projects 20 List of Ralf Dahrendorf Roundtables 2016 21 Photos 22 ABOUT US 31 Member Organisations 32 List of all Member Organisations 70 The Board of Directors 72 The Secretariat 75 Imprint 77 3 EUROPEAN LIBERAL FORUM / ANNUAL REPORT 2016 WELCOME WELCOME LETTER FROM THE PRESIDENT DR JÜRGEN MARTENS The unpredictable and sud- stitutions and for a way to move den political changes that 2016 forward. brought caught all of us in Eu- rope off guard. Brexit, the elec- At ELF, we seek to inspire and tion of Donald Trump as President support these developments. -

Overview Member Organisations – EUROPEAN LIBERAL FORUM
Overview Member Organisations – EUROPEAN LIBERAL FORUM Brussels, 26.01.2018 MEMBER COUNTRY TYPE OF TYPE OF MEMBERSHIP ORGANIZATION ORGANIZATION Academy of Liberalism Estonia Think tank Full membership Sweden Think tank Full membership Bertil Ohlin Institute Bosnia and Foundation Affiliate membership Boris Divković Herzegovina Foundation Centre for Liberal Czech Republic Think tank Full membership Studies Centre for Liberty Lithuania Think tank Full membership Studies Centre Jean Gol Belgium Think tank Full membership Centre Party Sweden Party foundation Full membership International Foundation (CPIF) E2 Think tank Finland Think tank Full membership European Liberal Youth Belgium Youth organization Full membership (LYMEC) Fondazione Critica Italy Foundation Full membership Liberale For Freedom Foundation Hungary Affiliate Member Affiliate membership FORES Sweden Foundation Full membership Foundation Project: Poland Foundation Full membership Polska Forum for Latvia’s Latvia NGO Affiliate membership Future Freedom Research Turkey Research Organisation Affiliate membership Association / Özgürlük Araştırmaları Derneği Friedrich Naumann Germany National organisation Full membership Foundation for Freedom (FNF) Fundaciò Catalanista I Spain Foundation Full membership Demòcrata Fundacja Industrial Poland Foundation Full membership Haya van Netherlands Foundation Full membership Somerenstichting / VVD Int’l Institute for Politics and Czech Republic Institute Full membership Society Institute for Liberal Romania Association Full membership Studies -

Liberal Vision 13 Your Regular Roundup of News from Liberal International
SUBSCRIBE TO THIS NEWSLETTER Liberal International has inaugurated the global Council of Liberal Presidents. Presidents of the regional liberal networks worldwide met virtually to discuss the challenges facing each continent and coordinate cooperation in the global fight to defeat COVID19. Convened by Hakima Elhaité, President of Liberal International, the council of liberal presidents expressed solidarity with the large-scale protests around the world campaigning against violence and systemic racism, ! ! ! ! ! ! ! ! solidarity with the large-scale protests around the world campaigning against violence and systemic racism, affirmed that democracy & the freedom of speech and assembly should not become victims of the pandemic and that only by strengthening multilateral cooperation can the world mitigate the greatest challenges to international peace and stability in our time. The 5 presidents drew up an action plan to address a number of the challenges raised. Read the following statement Joined by: Africa Liberal Network President Gilbert Noël Ouédraogo ALDE Party President Hans van Baalen Council of Asian Liberals and Democrats Chair Bi-Khim Hsiao Red Liberal de América Latina - Relial President Ricardo Gomes WATCH VIDEO 'Everything's Under Control: the pandemic of power-grabs' The coronavirus pandemic has devalued the rule of law, eroded democratic norms and allowed autocrats to tighten their grip on power. This week Hong Kong, Russia, and, just a few hours ago, the Philippines have all seen outrageous abuses of liberal-democratic structures to help autocrats consolidate control. Joining the debate: European Union Commissioner for Justice, Didier Reynders. Open Society European Policy Institute Director, Heather Grabbe Liberal International President, Hakima Elhaité WATCH HERE Hong Kong politician and pro-democracy activist, Emily Lau Covid-19 : Et si le Libéralisme et la Mondialisation sont la solution et non le problème ? Nous avons le plaisir de vous inviter au webinaire sur "Covid-19: .. -

Www. Nowecantsong
Welcome to the Utopia Forums! Register a new account The current time is Fri Nov 13 20:34:07 PST 2020 Utopia Talk / General Talk / Drunk Guy chicgeek Fri Oct 16 10:03:53 Member http://bit.ly/drunkguy [warning, goes from funny to sad to uncomfortable] www.nowecantsong.org Fri Oct 16 10:06:52 Member Social liberalism From Wikipedia, the free encyclopedia Jump to: navigation, search Part of the Politics series on Liberalism Development[show] History of liberal thought Contributions to liberal theory History of classical liberalism Ideas[show] Political liberalism Economic liberalism Political freedom Democratic capitalism Democratic education Individualism Laissez faire Liberal democracy Liberal neutrality Separation of church and state Market economy Open society Popular sovereignty Rights (individual) Schools[show] Classical liberalism Objectivism Conservative liberalism · Cultural liberalism · Green liberalism Liberal conservatism · Libertarianism · Market liberalism National · Neoliberalism Ordoliberalism · Paleoliberalism · Social liberalism Key figures[show] John Locke Adam Smith Thomas Jefferson Thomas Paine David Hume Baron de Montesquieu Immanuel Kant Jeremy Bentham John Stuart Mill Thomas Hill Green John Maynard Keynes Friedrich von Hayek Isaiah Berlin John Rawls · Robert Nozick Bertrand Russell Regional variants[show] Liberalism worldwide Liberalism in Europe Liberalism in the United States Liberalism by country Organisations[show] Liberal parties Liberal International International Federation of Liberal Youth (IFLRY) European Liberal Democrat and Reform Party (ELDR) Alliance of Liberals and Democrats for Europe (ALDE) European Liberal Youth (LYMEC) Council of Asian Liberals and Democrats (CALD) Africa Liberal Network (ALN) Liberal Network for Latin America (Relial) Politics portal v � d � e Social liberalism, a reformulation of 19th century liberalism, rests on the view that unrestrained capitalism is a hindrance to true freedom. -

Forum Libéral Européen European Liberal Forum a Non-Profit
1 Forum Libéral Européen 2 European Liberal Forum 3 4 A non-profit association under Belgian law, founded by private deed dated 21 September 2007, published in the 5 appendices of the Moniteur Belge dated 26 September 2007, under number 07144686. 6 Registered on the Trade Register under company number 0892.305.374. 7 Of which the articles of association have been modified by virtue of the minutes of the following general assemblies: 8 1) General Assembly of 25 January 2008, published in the appendices of the Moniteur Belge 29 July 2008 (under 9 number 08131859); 10 2) General Assembly of 09 October 2009, published in the appendices of the Moniteur Belge 22 October 2009 (under 11 number 09154710); 12 3) General Assembly of 01 October 2010, published in the appendices of the Moniteur Belge 26 January 2006 (under 13 number 11014040); 14 4) General Assembly of 16 September 2011, published in the appendices of the Moniteur Belge 30 December 2011 15 (under number 11197449); 16 5) General Assembly of 27 April 2012, published in the appendices of the Moniteur Belge 17 December 2012 (under 17 number 12208414); 18 6) General Assembly of 26 April 2013, published in the appendices of the Moniteur Belge 17 December 2012 (under 19 number 14003661); 20 7) General Assembly of 25 April 2014, published in the appendices of the Moniteur Belge 21 May 2015 (under 21 number 15072958); 22 8) General Assembly of 19 September 2014, published in the appendices of the Moniteur Belge (see No12); 23 9) Board meeting of 12 June 2015, published in the appendices of -

Europe's Party Politics: Liberal, Illiberal, Or Quasi-Liberal? N° 02 • April 2021
Policy Brief N° 02 April 2021 EUROPE’S PARTY POLITICS: LIBERAL, ILLIBERAL, OR QUASI-LIBERAL? For a time, post-war European politics was dominated by the liberal type of party. These broadly liberal parties were who originally envisaged the idea of a united Europe and subse- quently carried the torch for the advancement of open society in a progressively integrated Europe under rule of law. 1/5 Takis S. Pappas PhD, full-time researcher and writer, Introduction University of Helsinki, Finland Over many decades, Europe’s party systems op- split along many, often crosscutting, divisions that erated as liberal political cartels in which the ma- generate conflict. Liberal parties’ second common jor parties competed for power against each other, characteristic is their understanding of the need largely unchallenged by other party types. Fast for- to behave moderately, seek consensus, and prefer ward to the present day, and the talk around town positive-sum outcomes. This need is best met via is about the decline of the formerly established lib- liberal parties’ third characteristic, which is their eral parties, the proliferation of new populist ones, adherence to safeguards for minority rights and and, ominously enough, the rise of various other the rule of law, as expressed primarily in written so-called anti-system parties – leading to democrat- constitutions. In addition to these three core char- ic backsliding and, potentially, the disintegration of acteristics, the vast majority of Europe’s post-war the European Union. Which part of this