Gartner's Magic Quadrant for Endpoint Protection Platform 2010
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Overview of Client Management Suite 7.1 Hands-On Lab
Overview of Client Management Suite 7.1 Hands-On Lab Description If you are new to Altiris Client Management Suite, this lab is an excellent place to start. This introduction lab provides a hands-on overview of the suite going through many steps of IT lifecycle management. It includes the basics on software and patch management, deployment, migration, remote assistance, and more to start you on your path to effective client management. At the end of this lab, • Create an inventory policy and run reports to view the you should be able to collected data • Describe the available methods for delivering and metering software within a real-world environment • Describe the process of staging and deploying patches to systems and applications within a network environment • Use Deployment Solution 7.1 to perform an OS Migration Notes . The lab will be directed and will provide you with step-by- step walkthroughs of key features. Feel free to follow along with the instructor, or you may optionally perform this lab at your own pace. Be sure to ask your instructor any questions you may have. Thank you for coming to our lab session. Introduction Altiris® Client Management Suite™ reduces the total cost of owning client systems by automating time-consuming and redundant tasks. By minimizing the efforts and costs associated with deploying, managing, securing and troubleshooting client systems, organizations can gain control of their environments. This easy-to-use, integrated suite of solution software for Windows, Mac and Linux is designed to address IT management needs for desktop and notebook computers throughout their entire IT lifecycle. -

India Business Volume 2 Symantec Size
Business Superbrands- 2nd edition(Main) 8/27/08 4:12 AM Page 136 Market 30% of the world’s email traffic. At the as Global Market Share Leader in Enterprise Adware, spyware, worms, viruses, trojans, company’s three security operation centres – Backup; Backup and Recovery Software; Core spam… computer users the world over are one of which is in India – employees analyse Storage Management Software; and Email Active now familiar with these gremlins that often and correlate emerging threats to help Archiving. Between 2006 and 2007, in the make working on a PC or laptop a nightmare. customers prepare for and withstand attacks. Gartner Magic Quadrants, the company was There is a universal quest for a protector.The Powerful protection – and only available from listed as a leader in PC Configuration Life Cycle one name that has become virtually Symantec – is the company credo. Its pedigree Management; Managed Security Services synonymous with computer software, is supported by other illustrious names and Providers (NA); Storage Services; Security particularly in the realms of security and includes industry leaders such as Veritas, Altiris Information and Event Management; Email information management is Symantec. and Brightmail (Source: archival data). Active Archiving; Content Monitoring and Headquartered in Cupertino, California, the Filtering for Data Loss Prevention and Email US$ 5.19 billion (Rs. 20,760 crore) company Achievements Security Boundary. operates in more than 40 countries and is part Its aptitude to successfully integrate acquired During the last two years, the accolades and of the NASDAQ and Fortune 500 listing. technologies has kept Symantec at the front of recognition have been overwhelming. -

Altiris™ Software Management Solution 7.1 SP2 from Symantec™ User Guide Altiris™ Software Management Solution 7.1 SP2 from Symantec™ User Guide
Altiris™ Software Management Solution 7.1 SP2 from Symantec™ User Guide Altiris™ Software Management Solution 7.1 SP2 from Symantec™ User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Legal Notice Copyright © 2011 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, and Altiris are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations. -

Server Management Suite 8.1 Release Notes
Symantec™ Server Management Suite 8.1 powered by Altiris™ technology Release Notes Symantec™ Server Management Suite 8.1 powered by Altiris™ technology Release Notes Legal Notice Copyright © 2017 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and Altiris and Symantec or Altiris are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. Symantec Corporation 350 Ellis Street Mountain View, CA 94043 http://www.symantec.com Technical Support Symantec Technical Support maintains support centers globally. Technical Support’s primary role is to respond to specific queries about product features and functionality. The Technical Support group also creates content for our online Knowledge Base. The Technical Support group works collaboratively with the other functional areas within Symantec to answer your questions in a timely fashion. -

Overall Messaging/Description (We'll Want to Highlight
Storage and Availability Management Group Data Protection Group At-a-Glance PROFILE Symantec provides enterprise customers with storage management, high availability and data protection solutions across heterogeneous storage and server platforms in both physical and virtual environments. These solutions enable companies to standardize on a single layer of infrastructure software that works on every major distributed operating system and supports every major storage device, database and application. Storage and Availability Management – Symantec’s storage management and high availability family of products provide storage management, storage resource management, storage utilization management, storage area network, or SAN management, storage virtualization and replication, allowing enterprises to ensure the availability of critical applications and data. Products include Veritas CommandCentral Storage, Veritas Storage Foundation and Veritas Cluster Server. Data Protection – Symantec’s data protection family of products is designed to ensure successful backup and recovery of information and systems for organizations across all market segments, from small and medium-sized businesses to large enterprises, using the latest disk, tape, deduplication, indexing and virtual technologies. Products include Veritas NetBackup Platform, Symantec Backup Exec and Symantec Backup Exec System Recovery. LEADERSHIP • Rob Soderbery, senior vice president, Storage and Availability Management Group • Deepak Mohan, senior vice president, Data Protection Group Symantec Corp., 2008 1 STORAGE AND AVAILABILITY MANAGEMENT PRODUCTS Veritas Storage Foundation Veritas Storage Foundation from Symantec provides a complete solution for heterogeneous online storage management. Based on the industry-leading Veritas Volume Manager and Veritas File System, it provides a standard set of integrated tools to centrally manage explosive data growth, maximize storage hardware investments, provide data protection and adapt to changing business requirements. -

Altiris™ IT Analytics Solution 7.1 SP2 from Symantec™ User Guide Altiris™ IT Analytics Solution 7.1 from Symantec™ User Guide
Altiris™ IT Analytics Solution 7.1 SP2 from Symantec™ User Guide Altiris™ IT Analytics Solution 7.1 from Symantec™ User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Legal Notice Copyright © 2011 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo, Altiris, and any Altiris or Symantec trademarks are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This Symantec product may contain third party software for which Symantec is required to provide attribution to the third party (“Third Party Programs”). Some of the Third Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Please see the Third Party Legal Notice Appendix to this Documentation or TPIP ReadMe File accompanying this Symantec product for more information on the Third Party Programs. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. -

Altiris™ Software Management Solution from Symantec Users Guide
Altiris™ Software Management Solution from Symantec Users Guide Version 7.0 SP2 Altiris™ Software Management Solution from Symantec Users Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 7.0 SP2 Legal Notice Copyright © 2010 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, and Altiris are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations. -
HOW to USE THIS DOCUMENT: Buying Programs
___________________________________________________________________________________ HOW TO USE THIS DOCUMENT: You can find a key word to use in your search on the repository. • You can use Ctrl + F to search this entire document. • You can also jump to a particular group and manually scroll. Buying Programs Which includes: Express Buying Program Certificate Services Which includes: MPKI for SSL; SSL Certificate; Roots and Audits; Managed PKI (MPKI) Online Services Which includes: CloudSOC (CASB) (formerly Elastica); Web Security Service; DLP Cloud; VIP; Cyber Security Services Education and Technical Services Which includes Customer Success; Training Consumer Software Which includes Norton Enterprise Software Which includes SEP and ATP Version 2019.09.20 ___________________________________________________________________________________ Buying Programs Use These Key Word To Look for These Associated Documents Express Buying Program • Express Buying Program Terms and Conditions [Back to Top] Version 2019.09.20 ___________________________________________________________________________________ Certificate Services Symantec completed its divestiture of its certificate services to DigiCert on October 31, 2017. For standard agreements, service descriptions, audit reports and root policies relevant to the Certificate Authority business (including Symantec, Thawte, GeoTrust, and RapidSSL), please visit the Certificate Authority Repository. [Back to Top] Version 2019.09.20 ___________________________________________________________________________________ -

Altiris Symantec™ Endpoint Protection Integration Component 7.1 SP2 User Guide Altiris Symantec™ Endpoint Protection Integration Component 7.1 SP2 User Guide
Altiris Symantec™ Endpoint Protection Integration Component 7.1 SP2 User Guide Altiris Symantec™ Endpoint Protection Integration Component 7.1 SP2 User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Legal Notice Copyright © 2011 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo, Altiris, and any Altiris or Symantec trademarks are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations. -

Magic Quadrant for Endpoint Protection Platforms Published: 2 January 2013
This research note is restricted to the personal use of [email protected] G00239869 Magic Quadrant for Endpoint Protection Platforms Published: 2 January 2013 Analyst(s): Peter Firstbrook, John Girard, Neil MacDonald The endpoint protection platform provides a collection of security utilities to protect PCs and tablets. Vendors in this market compete on the quality of their protection capabilities, the depth and breadth of features, and the ease of administration. Strategic Planning Assumption By 2017, more than 50% of end-user devices will be restricted to running only apps that have been preinspected for security and privacy risks, up from 20% today. Market Definition/Description The enterprise endpoint protection platform (EPP) market is a composite market primarily made up of collections of products. These include: ■ Anti-malware ■ Anti-spyware ■ Personal firewalls ■ Host-based intrusion prevention ■ Port and device control ■ Full-disk and file encryption, also known as mobile data protection ■ Endpoint data loss prevention (DLP) ■ Vulnerability assessment ■ Application control (see Note 1) ■ Mobile device management (MDM) These products and features are typically centrally managed and ideally integrated by shared policies. This research note is restricted to the personal use of [email protected] This research note is restricted to the personal use of [email protected] DLP, MDM and vulnerability assessment are also evaluated in their own Magic Quadrant or MarketScope analyses. Longer term, portions of these markets will get subsumed by the EPP market, as the personal firewall, host intrusion prevention, device control and anti-spyware markets have in the past. EPP suites are a logical place for convergence of these functions. -
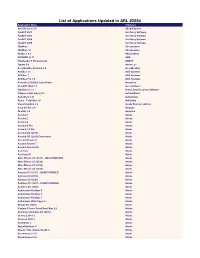
List of Applications Updated in ARL #2554
List of Applications Updated in ARL #2554 Application Name Publisher SyncBackLite 8.6 2BrightSparks TaxACT 2001 2nd Story Software TaxACT 2003 2nd Story Software TaxACT 2004 2nd Story Software TaxACT 2005 2nd Story Software 3DxWare 3Dconnexion 3DxWare 10 3Dconnexion HotDocs 6.3 AbacusNext PROMOD IV 11 ABB FineReader 6 Professional ABBYY Typora 0.9 Abner Lee AccuWeather Desktop 1.8 AccuWeather ACDSee 3.1 ACD Systems ACDSee 7 ACD Systems ACDSee Pro 7.0 ACD Systems Acoustica CD/DVD Label Maker Acoustica CutePDF Writer 3 Acro Software ISO Burner 1.1 Active Data Recovery Software FlySpeed SQL Query 3.3 ActiveDBSoft ActivePerl 5.16 ActiveState Rome - Total War 1.0 Activision Visual Lighting 2.4 Acuity Brands Lighting Easy-CD Pro 2.0 Adaptec OneSite 5.6 Adaptiva Acrobat 1 Adobe Acrobat 2 Adobe Acrobat 4 Adobe Acrobat 6 Pro Adobe Acrobat 7.0 Pro Adobe Acrobat DC (2019) Adobe Acrobat DC (2020) Continuous Adobe Acrobat Reader 6 Adobe Acrobat Reader 7 Adobe Acrobat Reader DC Adobe AcroTray Adobe AcroTray XI Adobe After Effects CC (2015) - UNAUTHORIZED Adobe After Effects CC (2018) Adobe After Effects CC (2019) Adobe After Effects CC (2020) Adobe Animate CC (2017) - UNAUTHORIZED Adobe Animate CC (2019) Adobe Animate CC (2020) Adobe Audition CC (2015) - UNAUTHORIZED Adobe Audition CC (2020) Adobe Authorware Runtime 4 Adobe Authorware Runtime 5 Adobe Authorware Runtime 7 Adobe Authorware Web Player 6 Adobe Bridge CC (2020) Adobe Capture Classic FormFlow Filler 2.2 Adobe Character Animator CC (2020) Adobe Connect 2019.3 Adobe Connect 2020.1 Adobe Contribute -

Symantec 2006 Analyst Day
Symantec 2006 Analyst Day May 31, 2006 Welcome Helyn Corcos Vice President Investor Relations Forward Looking Statements This presentation contains forward-looking statements regarding our financial and business results, including statements relating to projections of future revenue and earnings per share, and projections of deferred revenue, amortization of acquisition-related intangibles and deferred compensation changes. Such forward-looking statements involve known and unknown risks, uncertainties and other factors that may cause our actual results, levels of activity, performance or achievements to differ materially from results expressed in or implied by this presentation, including, among others: whether we can successfully develop new products and the degree to which these gain market acceptance; the sustainability of recent growth rates, particularly in consumer products; the anticipation of the growth of certain market segments; the positioning of our products in those segments; the competitive environment in the software industry; general market conditions; acquisition-related risks; fluctuations in currency exchange rates; and changes to operating systems and product strategy by vendors of operating systems Additional information concerning these and other risk factors is contained in the Risk Factors section of our Form 10-Q for the quarter ended December 31, 2005 We assume no obligation to update any forward-looking information contained in this presentation Symantec 2006 Analyst Day GAAP to Non-GAAP Reconciliation In addition