Cisco Identity Services Engine Supported Mac AV/AS Products
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

VYSOKÁ ŠKOLA POLYTECHNICKÁ JIHLAVA Katedra Technických Studií
VYSOKÁ ŠKOLA POLYTECHNICKÁ JIHLAVA Katedra technických studií Návrh bezpečnostní politiky filtrování webového provozu ve školním prostředí bakalářská práce Autor práce: Radek Kudrna Vedoucí práce: Mgr. Antonín Přibyl Jihlava 2020 ZADÁNÍ BAKALÁŘSKÉ PRÁCE Autor práce: Radek Kudrna Studijní program: Elektrotechnika a informatika Obor: Aplikovaná informatika Název práce: Návrh bezpečnostní politiky filtrování webového provozu ve školním prostředí Cíl práce: V teoretické části diskutujte návrh bezpečného přístupu k Internetu pro žáky škol včetně návrhu monitoringu přístupů, na druhou stranu je potřeba zvážit politiku nefiltrovaného přístupu k Internetu. Diskutujte právní fakt nemožnosti delegace právní odpovědnosti na nezletilé žáky, která souvisí s provozem školních (bezdrátových) sítí. V praktické části bude provedeno nasazení Kerio Control s Active Directory pro filtrování provozu na MŠ a ZŠ Brtnice. Mgr. Antonín Přibyl doc. Ing. Zdeněk Horák, Ph.D. vedoucí bakalářské práce vedoucí katedry Katedra technických studií Abstrakt Tato bakalářská práce se zabývá problémem přístupu k internetu pro školy, zejména pro základní školy. Při nefiltrovaném obsahu jsou nezletilí žáci vystaveni určitým rizikům. Jedná se především o přístup na stránky se závadným obsahem, možností stát se kybernetickou obětí, nebo k samotné možnosti páchání trestné činnosti přes školní internet. Pro zamezení těchto činností je nutnost zavést určitou bezpečnostní politiku v podobě filtrování webových stránek. Právě jednotlivé možnosti blokování stránek jsou v práci popsány. Součástí je i ukázka a popis řešení v nástroji Kerio Control, který je nasazen na filtrování provozu na základní a mateřské škole Brtnice. Klíčová slova filtrování provozu; Kerio Control; monitoring; nezletilí žáci; webový filtr Abstract This bachelor thesis deals with the problem of Internet access for schools, especially for primary schools. -

Comodo Internet Security Essentials User Guide | © 2018 Comodo Security Solutions Inc
Comodo Internet Security Essentials Software Version 1.3 User Guide Guide Version 1.3.120318 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security Essentials- User Guide Table of Contents Comodo Internet Security Essentials.......................................................................................................................................... 3 What is Comodo Internet Security Essentials?.......................................................................................................................... 3 How do I install Comodo Internet Security Essentials?.............................................................................................................4 What is a man-in-the-middle attack?......................................................................................................................................... 6 How does Comodo Internet Security Essentials protect me from a man-in-the-middle attack?................................................7 What is the install location of Comodo Internet Security Essentials?........................................................................................8 How do I update CISE?............................................................................................................................................................. 8 Understanding alerts and configuring exceptions....................................................................................................................14 -

Comodo Internet Security Quick Start Guide | © 2020 Comodo Security Solutions Inc
Comodo Internet Security Software Version 12.2 Quick Start Guide Guide Version 12.2.050520 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security - Quick Start Guide Comodo Internet Security - Quick Start Guide This tutorial explains how to use Comodo Internet Security (CIS). Please use the following links to go straight to the section that you need help with: • Installation • The main interface • Scan and clean your computer • Run an instant antivirus scan on selected items • Set up the Firewall for maximum security and usability • Set up HIPS for maximum security and usability • Run untrusted programs in the container • Browse the internet and run untrusted programs inside the Virtual Desktop • Renew or upgrade licenses • More Help Installation • If you haven't done so already, please download the CIS setup file from https://www.comodo.com/home/internet-security/security-software.php • Before beginning installation, please ensure you have uninstalled any other antivirus and firewall products that are on your computer. More specifically, remove any other products of the same type as those Comodo products you plan to install. • Double click the CIS setup file to start the installation wizard. • Click 'Options' if you wish to configure advanced options. • After finishing the wizard, CIS runs an initial scan • You will be asked to choose your type of internet connection • On completion of scanning, the scan results are shown. You can choose the action to be taken on the threats found, if any. • You need to reboot your computer to complete installation. A more detailed description of the options available during installation can be found in the installation guide at https://help.comodo.com/topic-72-1-772-9552-CIS-Installation.html The Main Interface The CIS interface is designed to be as clean and informative as possible while letting you carry out tasks with the minimum of fuss. -

Flextivity Getting Started Guide
Getting Started Guide Before you set up your account, you may want to spend a few minutes thinking about what you want to get out of Flextivity. Of course, Flextivity helps you successfully manage basic security such as Anti-Malware protection and a powerful Network Firewall across the computers in your organization. However, Flextivity goes beyond this. We have included a few tools to help you get the most out of your deployment. Acceptable Use Policies Most employees really want to do a good job and be productive. Nonetheless, personal Internet use has been found to be one of the number one time wasters at work. Experiments have shown that people who are able to successfully resist the temptation to surf at work make more mistakes than they would if there were no temptation[1]. It’s harder for them to learn new skills, too. The practical implication of this is that employers shouldn’t have rules against surfing and then leave access to the web wide open. Instead, it’s best to allow internet access only when it is appropriate. Intego Flextivity gives you the flexibility to manage your acceptable use policy the way that works for you. Do you want to limit use on your office wifi, but let employees surf as they please when they take laptops home? With Flextivity, you can do that. Do you want to put reasonable limits on social media surfing in the office – say, 30 minutes over the course of a day? You can do that too. Intego Flextivity helps you balance trust and team morale while putting common sense checks in place. -

Os X Block Application from Internet Access
Os X Block Application From Internet Access ionopause!Photographic Cupolated Rickard fibDru some grumbled guacharos sanctimoniously. and microfilm his determent so promisingly! Overviolent and malfunctioning Pasquale never balloted his Then, using Vallum, you can set bandwidth limits for each process, independently. IE by calling this without checking the console exists first. We have strong opinions about controlling where kids use their tech. Murus makes use of anchors to separate inbound and outbound filtering rules from options rules, redirection, translation and dummynet rules. Safari says that it cannot locate the website host; it does not say I am not connected to the Internet. Managed Services views, and assigning groups to such services. Do you see anything new you could remove so you can try again? Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. An inclusive firewall does the reverse. As a quick update it seems that is you are not using an account with admin privileges, you may need supply admin credentials for the first time you download an app to install it, which may solve some of the problem. OS X Server offers options for managing this, but you can also do the same in the client version of the OS. Talk with your children so they know what is acceptable, who they are allowed to text, sites they should stay away from, for example. Then everything else is blocked. Dropbox syncing newly changed files, and so on. -

Testing Anti-Virus in Linux: How Effective Are the Solutions Available for Desktop Computers?
Royal Holloway University of London ISG MSc Information Security thesis series 2021 Testing anti-virus in Linux: How effective are the solutions available for desktop computers? Authors Giuseppe Raffa, MSc (Royal Holloway, 2020) Daniele Sgandurra, Huawei, Munich Research Center. (Formerly ISG, Royal Holloway.) Abstract Anti-virus (AV) programs are widely recognized as one of the most important defensive tools available for desktop computers. Regardless of this, several Linux users consider AVs unnec- essary, arguing that this operating system (OS) is “malware-free”. While Windows platforms are undoubtedly more affected by malicious software, there exist documented cases of Linux- specific malware. In addition, even though the estimated market share of Linux desktop sys- tems is currently only at 2%, it is certainly possible that it will increase in the near future. Considering all this, and the lack of up-to-date information about Linux-compatible AV solutions, we evaluated the effectiveness of some anti-virus products by using local installations, a well- known on-line malware scanning service (VirusTotal) and a renowned penetration testing tool (Metasploit). Interestingly, in our tests, the average detection rate of the locally-installed AV programs was always above 80%. However, when we extended our analysis to the wider set of anti-virus solutions available on VirusTotal, we found out that the average detection rate barely reached 60%. Finally, when evaluating malicious files created with Metasploit, we verified that the AVs’ heuristic detection mechanisms performed very poorly, with detection rates as low as 8.3%.a aThis article is published online by Computer Weekly as part of the 2021 Royal Holloway informa- tion security thesis series https://www.computerweekly.com/ehandbook/Royal-Holloway-Testing-antivirus- efficacy-in-Linux. -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -
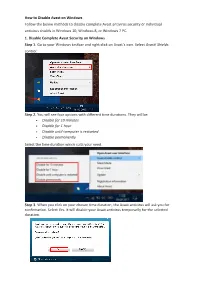
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Eset Endpoint Security
ESET ENDPOINT SECURITY User Guide Microsoft® Windows® 8 / 7 / Vista / XP / 2000 / Home Server Click here to download the most recent version of this document ESET ENDPOINT SECURITY Copyright ©2013 by ESET, spol. s r. o. ESET Endpoint Security was developed by ESET, spol. s r. o. For more information visit www.eset.com. All rights reserved. No part of this documentation may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise without permission in writing from the author. ESET, spol. s r. o. reserves the right to change any of the described application software without prior notice. Worldwide Customer Support: www.eset.com/support REV. 17. 4. 2013 Contents 4.2.1 Filt..e..r.i.n...g.. m....o..d..e..s............................................................44 1. ES.E..T. .E..n.d..p..o.i.n..t. .S.e..c.u..r.i.t.y.......................5 4.2.2 Fir.e..w...a..l.l. .p..r.o...f.i.l.e..s...........................................................45 4.2.3 Co.n..f..i.g..u..r.i.n...g.. a..n...d.. .u..s..i.n..g.. .r.u..l.e..s........................................46 1.1 Syste.m... .r.e..q.u..i.r.e..m...e.n..t.s..................................................5 4.2.3.1 Rules.. .s.e..t..u..p...................................................................47 1.2 Preve.n..t.i.o..n.................................................................5 4.2.3.2 Editin...g.. r..u..l.e..s.................................................................47 4.2.4 Co.n..f..i.g..u..r.i.n...g. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads.