Linux Network Administrators Guide Remote Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Comodo Antispam Gateway Software Version 1.5
Comodo Antispam Gateway Software Version 1.5 Administrator Guide Guide Version 1.5.082412 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo Antispam Gateway - Administrator Guide Table of Contents 1 Introduction to Comodo Antispam Gateway........................................................................................................................... 4 1.1 Release Notes............................................................................................................................................................. 5 1.2 Purchasing License .................................................................................................................................................... 6 1.3 Adding more Users, Domains or Time to your Account .................................................................................................6 1.4 License Information................................................................................................................................................... 10 2 Getting Started................................................................................................................................................................... 13 2.1 Incoming Filtering Configuration ................................................................................................................................ 13 2.1.1 Configuring Your Mail Server.................................................................................................................................. -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
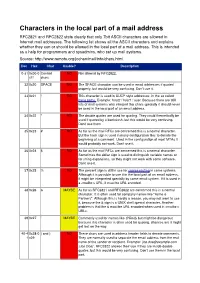
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -
DNS Manager User Guide VF
Vodafone Hosted Services: DNS Manager User Guide DNS Manager User Guide 1 Vodafone Hosted Services: DNS Manager User Guide DNS Manager What is DNS Manager ? DNS Manager allows the end-user to edit their domain’s zone file, including A (address) records, CNAME (canonical name) records and MX (mail exchange) records. What is the Default Zone File ? If the end-user selects “Edit Zone File” and clicks “Next”, their current zone file will be displayed at the top of the screen. By default, their zone file will contain several important records. Any changes to these records may cause serious problems with their website and email performance. What is DNS ? DNS (Domain Name System or Domain Name Service) catalogs and updates information in regards to domain names. DNS converts domain names into IP addresses. DNS usually contains a set of zone files that lists the types of redirection that will be done. 2 Vodafone Hosted Services: DNS Manager User Guide What are Zone Files ? Four types of records are important in a zone file: • A records • CNAME records • MX records • Start of Authority (SOA) domain.com points to 216.251.43.17 mail.domain.com points to 69.49.123.241 mail will be delivered to 10 mx1c1.megamailservers.com first mail will be delivered to 100 mx2c1.megamailservers.com second mail will be delivered to 110 Resource Record Abbreviations The end-users domain name is called their “origin”. The origin is appended to all names in the zone file that do not end in a dot. For example, if their domain is yourname.com, the entry “www” in the zone file is equal to www.yourname.com. -

Streamline the Process - a Real Life Example Yadong Zhang, Oxford Health Plans, Trumbull, CT
Streamline the Process - A Real Life Example Yadong Zhang, Oxford Health Plans, Trumbull, CT ABSTRACT This paper presents a real life example on the evolution of a A SHELL SCRIPT TO THE RESCUE monthly report application. The application uses SAS/SQLâ pass â Now you get the DBF report that needs to be sent to the through and Base SAS to develop report and email the final business user. In our case, we run SAS on a UNIX box, product to the end user. The application also archives the log and our business users are on an NT server. So we and report automatically. either FTP the report to a shared place, or if the file is small enough, we email it to the user. That's exactly INTRODUCTION what I did in the first two runs: I FTP’d the file to my PC It is common for a SAS programmer to develop reports running and emailed it as an attachment. Tedious and time on a regular basis. How do you simplify the process? How do consuming, I began to hate it the third time I did it. So I you make your program to do the 'thinking' for you? This paper called on a shell script to the rescue. will present some tips on this subject. report.sh #!/bin/ksh PROBLEM # Declare shell variables On the first day of each month, produce a report on transitional ¶PGMDIR=/project/pgms care in DBF format, using tables on an Oracleâ data warehouse. ·PROG=report ¸RPTDATE="`date '+%Y-%m-%d'`" SOLUTION ¹ADM="yzhang@exchange-server" ºMAILTO="USER1@exchange-server As always, there is more than one way to do it in SAS. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Managing Sendmail Services in Oracle® Solaris 11.4
® Managing sendmail Services in Oracle Solaris 11.4 Part No: E61008 November 2020 Managing sendmail Services in Oracle Solaris 11.4 Part No: E61008 Copyright © 2002, 2020, Oracle and/or its affiliates. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" -

Master Thesis Characterizing Sender Policy Framework Configurations At
Master Thesis Characterizing Sender Policy Framework Configurations at Scale Gabri¨elMathay Kahraman Monday 7th September, 2020 A thesis presented for the degree of Master of Science Computer Science Design and Analysis of Communication Systems (DACS) Chair: prof. dr. ir. Aiko Pras Supervisor: dr. ir. Mattijs Jonker Co-supervisors: ir. Olivier van der Toorn and dr. Doina Bucur Abstract Phishing involves disguising oneself as a trustworthy entity in electronic communication, for example, by pretending to send e-mail on behalf of a company. Phishing e-mails can be prevented if domains implement e-mail security techniques. One of the techniques to improve e-mail security is the Sender Policy Framework (SPF). To enable SPF, the administrator of a domain can specify an SPF policy in the DNS zone of the domain. The SPF policy determines which IP addresses are authorised to send e-mail from the administrator's domain. When an e-mail server receives an e-mail, the e-mail server retrieves the SPF policy of the sender's domain. Next, the IP address of the sender will be queried against the SPF record, and the response of this query determines how to handle the incoming e-mail. The SPF standard was released over six years ago. Even though six years have passed, the research community does not yet have a thorough understanding of the characteristics of SPF use. What we miss is an understanding of how SPF policies are configured, how SPF policies have changed over time, and what the problematic trends are of SPF use. In this Thesis, we address the missing of a large scale analysis on SPF policies over time.