RSA Key Extraction Via Low-Bandwidth Acoustic Cryptanalysis∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MASTERCLASS GNUPG MASTERCLASS You Wouldn’T Want Other People Opening Your Letters and BEN EVERARD Your Data Is No Different
MASTERCLASS GNUPG MASTERCLASS You wouldn’t want other people opening your letters and BEN EVERARD your data is no different. Encrypt it today! SECURE EMAIL WITH GNUPG AND ENIGMAIL Send encrypted emails from your favourite email client. our typical email is about as secure as a The first thing that you need to do is create a key to JOHN LANE postcard, which is good news if you’re a represent your identity in the OpenPGP world. You’d Ygovernment agency. But you wouldn’t use a typically create one key per identity that you have. postcard for most things sent in the post; you’d use a Most people would have one identity, being sealed envelope. Email is no different; you just need themselves as a person. However, some may find an envelope – and it’s called “Encryption”. having separate personal and professional identities Since the early 1990s, the main way to encrypt useful. It’s a personal choice, but starting with a single email has been PGP, which stands for “Pretty Good key will help while you’re learning. Privacy”. It’s a protocol for the secure encryption of Launch Seahorse and click on the large plus-sign email that has since evolved into an open standard icon that’s just below the menu. Select ‘PGP Key’ and called OpenPGP. work your way through the screens that follow to supply your name and email address and then My lovely horse generate the key. The GNU Privacy Guard (GnuPG), is a free, GPL-licensed You can, optionally, use the Advanced Key Options implementation of the OpenPGP standard (there are to add a comment that can help others identify your other implementations, both free and commercial – key and to select the cipher, its strength and set when the PGP name now refers to a commercial product the key should expire. -

Securing Email Through Online Social Networks
SECURING EMAIL THROUGH ONLINE SOCIAL NETWORKS Atieh Saberi Pirouz A thesis in The Department of Concordia Institute for Information Systems Engineering (CIISE) Presented in Partial Fulfillment of the Requirements For the Degree of Master of Applied Science (Information Systems Security) at Concordia University Montreal,´ Quebec,´ Canada August 2013 © Atieh Saberi Pirouz, 2013 Concordia University School of Graduate Studies This is to certify that the thesis prepared By: Atieh Saberi Pirouz Entitled: Securing Email Through Online Social Networks and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science (Information Systems Security) complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the final examining commitee: Dr. Benjamin C. M. Fung Chair Dr. Lingyu Wang Examiner Dr. Zhenhua Zhu Examiner Dr. Mohammad Mannan Supervisor Approved Chair of Department or Graduate Program Director 20 Dr. Christopher Trueman, Dean Faculty of Engineering and Computer Science Abstract Securing Email Through Online Social Networks Atieh Saberi Pirouz Despite being one of the most basic and popular Internet applications, email still largely lacks user-to-user cryptographic protections. From a research perspective, designing privacy preserving techniques for email services is complicated by the re- quirement of balancing security and ease-of-use needs of everyday users. For example, users cannot be expected to manage long-term keys (e.g., PGP key-pair), or under- stand crypto primitives. To enable intuitive email protections for a large number of users, we design Friend- lyMail by leveraging existing pre-authenticated relationships between a sender and receiver on an Online Social Networking (OSN) site, so that users can send secure emails without requiring direct key exchange with the receiver in advance. -

Exploiting Switching Noise for Stealthy Data Exfiltration from Desktop Computers
Your Noise, My Signal: Exploiting Switching Noise for Stealthy Data Exfiltration from Desktop Computers Zhihui Shao∗ Mohammad A. Islam∗† Shaolei Ren University of California, Riverside University of Texas at Arlington University of California, Riverside [email protected] [email protected] [email protected] ABSTRACT program’s usage pattern of CPU resources, if detected by another Attacks based on power analysis have been long existing and stud- program, can be modulated for information transfer between the ied, with some recent works focused on data exfiltration from victim two [50, 57]. Consequently, to mitigate data theft risks, enterprise systems without using conventional communications (e.g., WiFi). users commonly have restricted access to outside networks — all Nonetheless, prior works typically rely on intrusive direct power data transfer from and to the outside is tightly scrutinized. measurement, either by implanting meters in the power outlet or Nevertheless, such systems may still suffer from data exfiltration tapping into the power cable, thus jeopardizing the stealthiness of at- attacks that bypass the conventional communications protocols tacks. In this paper, we propose NoDE (Noise for Data Exfiltration), (e.g., WiFi) by transforming the affected computer into a transmitter a new system for stealthy data exfiltration from enterprise desk- and establishing a covert channel. For example, the transmitting top computers. Specifically, NoDE achieves data exfiltration over computer can modulate the intensity of the generated acoustic a building’s power network by exploiting high-frequency voltage noise by varying its cooling fan or hard disk spinning speed to ripples (i.e., switching noises) generated by power factor correction carry 1/0 bit information (e.g., a high fan noise represents “1” and circuits built into today’s computers. -

Digital Security for Activists
Training the Motivated: Digital Security for Activists Glencora Borradaile Kelsy Kretschmer Abstract School of Electrical Engineering School of Public Policy The state of global surveillance and the political and Computer Science Sociology Program environment has many activists caring more about their Oregon State University Oregon State University online security culture. We report on the initiation of a Corvallis, OR 97331, USA Corvallis, OR 97331, USA Digital Security for Activists program and a pilot study of an [email protected] [email protected] introductory seminar. Pre- and post-surveys of the seminar will form an initial assessment of what kind of intervention might increase the security practices of activists and to inform the design of program offerings. We report on the pre-surveys from three offerings of the seminar. Introduction In collaboration with the Civil Liberties Defense Center (CLDC), the first author had been offering informal digital security trainings for activists and their lawyers. After the fall elections in the U.S., requests for these trainings increased dramatically and shortly thereafter we launched a Digital Security for Activists (DSA) program. The DSA program’s intent is to align with the CLDC mission (“to defend and uphold civil liberties through education, outreach, litigation, legal support, and assistance”) and enable citizen activists to assert their constitutional rights while organizing online. Copyright is held by the author/owner. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee. Poster In order to provide trainings that are useful and effective, we presented at the 13th Symposium on Usable Privacy and Security (SOUPS 2017). -

Gnu Privacy Guard (Gnupg) Mini Howto (English)
Gnu Privacy Guard (GnuPG) Mini Howto (English) Brenno J.S.A.A.F. de Winter (English) <brenno@dew int er . com> Michael Fischer v. Mollard (German) <f i s cher @math .uni- goettingen. de> Arjen Baart <arj en@andromeda .nl> Version 0.1.4 August 10, 2004 This documents explains how to use the GNU Privacy Guard (GnuPG), an Open Source OpenPGP compatible encryption system To keep this program totally free the use of the RSA algorithm and other patented algorithm has been avoided. The document was originally written by Michael Fischer v. Mollar in German. The text has been translated and adjusted on some points and cannot be considered as a full one-on-one copy. Contents 1 Concepts 2 1.1 Public Key Encryption .............................................................................................................................................. 2 1.2 Digital Signatures ..................................................................................................................................................... 3 1.3 Web of trust .............................................................................................................................................................. 3 1.4 Boundaries to security .............................................................................................................................................. 3 2 Installation 4 2.1 Sources for GnuPG. ................................................................................................................................................. -

Online Self Defense – Black Belt Level
Online Self Defense – Black Belt Level Review - White Belt Level 1.Do your updates 2.Use good antivirus/antimalware software 3.A long password is a strong password 4.Be suspicious of all emails, particularly those asking you to click on links, or that have attachments. Review – Yellow Belt 1.Always verify t!at you are on the we#site you mean to be 2.$et #rowser to more secure settings 3.Use privacy enhancing browser plugins 4.$can everything you download %.Only download programs from the official we#site Review - Green Belt Level ● (nformation is the currency of the internet ● )rivacy has finincial as well as ethical implications ● *a"e sure that your connection is encrypted +,--)$. ● Anonymizing we# proxies can help ● 1)Ns are better ● -or Browser is even better Review – Brown Belt Level 1.Unencrypted email is like sending a postcard instead of a letter 2.-o encrypt email use *ozilla -!under#ird with the 3nigmail plugin 3.-o encrypt chat use Pidgin with the OTR plugin Threat Modeling Decide what your most likely t!reats and plan your defense based on the following questions. 1. What is the most vulnerable/exploitable? 2. What is the most valuable? 3.How can I mitigate my vulnerabilities? 4. What can I o to limit amage i! an attac" is success!ul? Segregation of Identity ● Limit ability of a t!ird party to connect di'erent aspects of your life. 7or e0ample casual we# #rowsing and !ome #anking. ● 8roup activities wit! similar security re5uirements. ● Be self disciplined a#out t!is segregation. -

Hot Topics in Computer Security
Hot Topics in Computer Security Iliano Cervesato http://www.qatar.cmu.edu/iliano Andrew’s Leap June 30, 2010 Outline Let’s play a security game Cryptographic protocols Where did this guy say he’s from? 1 Here is the game Threat “Someone can break into my apartment and steal or destroy my stuff” Attacks and countermeasures I have a basic protection, but worse things can happen, help me to find what and how to mitigate them 2 My apartment’s basic protection Classic wooden door with a 3 points lock On the balcony (2nd floor), PVC windows with a single point lock 3 But … what’s in my apartment? $299 $89 4 What do we learn from the game You never prevent a threat .... you lower the risk! Performing an attack has a cost It's a balance between . the assets that you want to protect . the efforts an attacker will make Deploying a countermeasure has a cost It's a balance between . the cost of recovering from the attack . the cost of a deploying a protection mechanism 5 But keep in mind ... Security should always serves the business and not constrains it, otherwise ... nobody will invest in it or will be disable to be more efficient What is your definition of the risk analysis for computer science? 6 Now you know ... Marketing guy: “My software is totally secure!” You: “Oh really? Against what?” Your boss: “Design my information system and make it secure!” You: “tell me what you want to protect and let's talk together about ... potential threats . -

Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander
Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander 2006 Link to publication Citation for published version (APA): Maximov, A. (2006). Some Words on Cryptanalysis of Stream Ciphers. Department of Information Technology, Lund Univeristy. Total number of authors: 1 General rights Unless other specific re-use rights are stated the following general rights apply: Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal Read more about Creative commons licenses: https://creativecommons.org/licenses/ Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. LUND UNIVERSITY PO Box 117 221 00 Lund +46 46-222 00 00 Some Words on Cryptanalysis of Stream Ciphers Alexander Maximov Ph.D. Thesis, June 16, 2006 Alexander Maximov Department of Information Technology Lund University Box 118 S-221 00 Lund, Sweden e-mail: [email protected] http://www.it.lth.se/ ISBN: 91-7167-039-4 ISRN: LUTEDX/TEIT-06/1035-SE c Alexander Maximov, 2006 Abstract n the world of cryptography, stream ciphers are known as primitives used Ito ensure privacy over a communication channel. -
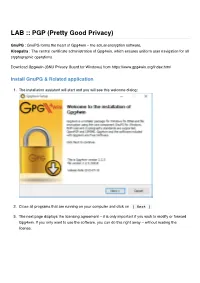
LAB :: PGP (Pretty Good Privacy)
LAB :: PGP (Pretty Good Privacy) GnuPG : GnuPG forms the heart of Gpg4win – the actual encryption software. Kleopatra : The central certificate administration of Gpg4win, which ensures uniform user navigation for all cryptographic operations. Download Gpg4win (GNU Privacy Guard for Windows) from https://www.gpg4win.org/index.html Install GnuPG & Related application 1. The installation assistant will start and you will see this welcome dialog: 2. Close all programs that are running on your computer and click on [ Next ] 3. The next page displays the licensing agreement – it is only important if you wish to modify or forward Gpg4win. If you only want to use the software, you can do this right away – without reading the license. Click on [ Next ] 4. On the page that contains the selection of components you can decide which programs you want to install. A default selection has already been made for you. You can also install individual components at a later time. Moving your mouse cursor over a component will display a brief description. Another useful feature is the display of required hard drive space for all selected components. Bellow are the application and there fucntion: a. GnuPG: Gnu Privacy Guard b. Kleopatra: Keymanager for OpenPGP c. GPA: GNU Privacy Assistant d. GpgOL: GnuPG for Outlook e. GpgEX: GnuPG Shell Extension f. Claws-Mail: Claws Mail user client g. Gpg4win Compedium: The Gpg4Win documentation Click on [ Next ] 5. The system will suggest a folder for the installation, e.g.: C:\Programme Files (x86)\GNU\GnuPG You can accept the suggestion or select a different folder for installing Gpg4win. -

Assessment Tasks 3 Publication Without Notice
ITEC643 Cryptography and Information Security S2 Day 2019 Dept of Computing Contents Disclaimer General Information 2 Macquarie University has taken all reasonable measures to ensure the information in this Learning Outcomes 3 publication is accurate and up-to-date. However, the information may change or become out-dated as a result of change in University policies, General Assessment Information 3 procedures or rules. The University reserves the right to make changes to any information in this Assessment Tasks 3 publication without notice. Users of this publication are advised to check the website Delivery and Resources 6 version of this publication [or the relevant faculty or department] before acting on any information in Unit Schedule 7 this publication. Learning and Teaching Activities 8 Policies and Procedures 8 Graduate Capabilities 10 Changes from Previous Offering 15 Grading Standards 15 Changes since First Published 17 https://unitguides.mq.edu.au/unit_offerings/119161/unit_guide/print 1 Unit guide ITEC643 Cryptography and Information Security General Information Unit convenor and teaching staff Convenor Christophe Doche [email protected] Contact via By email BD building Level 2 TBA Lecturer Les Bell [email protected] TBA Lecturer Alireza Jolfaei [email protected] BD Building Level 3 Tutor Mohamadali Mehrabi [email protected] BD Building Level 2 Credit points 4 Prerequisites Admission to MInfoTech or MEng or MSc or MScInnovation or GradDipIT or MInfoTech(Cyber Sec) Corequisites Co-badged status COMP343 / ITEC643 Unit description This unit provides an introduction to modern cryptography and information security. First, some cryptographic primitives, such as private key and public key ciphers, hash functions and digital signatures, are introduced. -

Sok: Design Tools for Side-Channel-Aware Implementations
SoK: Design Tools for Side-Channel-Aware Implementations Ileana Buhan∗, Lejla Batina∗, Yuval Yarom†, and Patrick Schaumont‡ ∗ Radboud University, Digital Security † University of Adelaide and Data61 ‡ Worcester Polytechnic Institute Abstract—Side-channel attacks that leak sensitive information involve collecting side-channel traces, e.g., power traces, from through a computing device’s interaction with its physical envi- the device and analyzing these traces to demonstrate an attack ronment have proven to be a severe threat to devices’ security, or the existence of leaks. While effective, such methodologies particularly when adversaries have unfettered physical access to the device. Traditional approaches for leakage detection measure require the physical device’s presence for evaluation, and this the physical properties of the device. Hence, they cannot be demand poses significant challenges. used during the design process and fail to provide root cause In the pre-silicon stage of the development, the device does analysis. An alternative approach that is gaining traction is to not yet exist; hence it cannot be adequately assessed. Con- automate leakage detection by modeling the device. The demand versely, in the post-silicone stage, detailed design information to understand the scope, benefits, and limitations of the proposed tools intensifies with the increase in the number of proposals. may not be accessible, for example, when using third-party In this SoK, we classify approaches to automated leakage components. Consequently, it may be challenging to identify detection based on the model’s source of truth. We classify the root cause of leakage. Moreover, detecting, verifying, and the existing tools on two main parameters: whether the model mitigating side-channel leaks require expert knowledge and includes measurements from a concrete device and the abstrac- expensive equipment. -

Centralized Email Encryption with Anubis
SYSADMIN Anubis Centralized email encryption with Anubis xperts acknowledge the danger of transmitting plans, personal Edata, and confidential agree- ments in clear text across the Internet, but end users rarely heed their warnings. EGYPTIAN Users typically don’t turn to tools such as PGP, GnuPG [2], and S/ Mime by choice. CTOs can either bemoan their fate or take proactive steps: so-called PGP servers provide centralized user key ENCRYPTION management and handle the encryption and decryption processes. These services remove the need for time-consuming The Anubis mail manipulation daemon lets you centralize encryption installation and configuration of a PGP client on every user workstation. for outgoing mail. BY DANIEL S. HAISCHT Linux admins have a choice of free en- cryption programs such as GPG-Relay [3] or Kuvert [4], and there are a number of commercial applications (such as [5] and [6]), some of which are also avail- able for Windows. But if you prefer to avoid specialized applications, your best option may be the universal mail manip- ulation program, GNU Anubis [1]. Anubis, which is named after an ancient Egyptian god, is an SMTP pre-processing daemon. The Anubis daemon receives messages from a Mail User Agent (such as the Mutt client shown in Figure 2), then modifies the messages before pass- ing them to the Mail Transfer Agent (such as the Postfix server shown in Fig- ure 2). Anubis can process messages in a number of different ways, but in this case, one of Anubis’ more useful tricks is the ability to encrypt mail using GnuPG.