Exploiting C-Closure in Kernelization Algorithms for Graph Problems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fixed-Parameter Tractability Marko Samer and Stefan Szeider
Handbook of Satisfiability 363 Armin Biere, Marijn Heule, Hans van Maaren and Toby Walsch IOS Press, 2008 c 2008 Marko Samer and Stefan Szeider. All rights reserved. Chapter 13 Fixed-Parameter Tractability Marko Samer and Stefan Szeider 13.1. Introduction The propositional satisfiability problem (SAT) is famous for being the first prob- lem shown to be NP-complete—we cannot expect to find a polynomial-time al- gorithm for SAT. However, over the last decade, SAT-solvers have become amaz- ingly successful in solving formulas with thousands of variables that encode prob- lems arising from various application areas. Theoretical performance guarantees, however, are far from explaining this empirically observed efficiency. Actually, theorists believe that the trivial 2n time bound for solving SAT instances with n variables cannot be significantly improved, say to 2o(n) (see the end of Sec- tion 13.2). This enormous discrepancy between theoretical performance guaran- tees and the empirically observed performance of SAT solvers can be explained by the presence of a certain “hidden structure” in instances that come from applica- tions. This hidden structure greatly facilitates the propagation and simplification mechanisms of SAT solvers. Thus, for deriving theoretical performance guaran- tees that are closer to the actual performance of solvers one needs to take this hidden structure of instances into account. The literature contains several sug- gestions for making the vague term of a hidden structure explicit. For example, the hidden structure can be considered as the “tree-likeness” or “Horn-likeness” of the instance (below we will discuss how these notions can be made precise). -

Introduction to Parameterized Complexity
Introduction to Parameterized Complexity Ignasi Sau CNRS, LIRMM, Montpellier, France UFMG Belo Horizonte, February 2018 1/37 Outline of the talk 1 Why parameterized complexity? 2 Basic definitions 3 Kernelization 4 Some techniques 2/37 Next section is... 1 Why parameterized complexity? 2 Basic definitions 3 Kernelization 4 Some techniques 3/37 Karp (1972): list of 21 important NP-complete problems. Nowadays, literally thousands of problems are known to be NP-hard: unlessP = NP, they cannot be solved in polynomial time. But what does it mean for a problem to be NP-hard? No algorithm solves all instances optimally in polynomial time. Some history of complexity: NP-completeness Cook-Levin Theorem (1971): the SAT problem is NP-complete. 4/37 Nowadays, literally thousands of problems are known to be NP-hard: unlessP = NP, they cannot be solved in polynomial time. But what does it mean for a problem to be NP-hard? No algorithm solves all instances optimally in polynomial time. Some history of complexity: NP-completeness Cook-Levin Theorem (1971): the SAT problem is NP-complete. Karp (1972): list of 21 important NP-complete problems. 4/37 But what does it mean for a problem to be NP-hard? No algorithm solves all instances optimally in polynomial time. Some history of complexity: NP-completeness Cook-Levin Theorem (1971): the SAT problem is NP-complete. Karp (1972): list of 21 important NP-complete problems. Nowadays, literally thousands of problems are known to be NP-hard: unlessP = NP, they cannot be solved in polynomial time. 4/37 Some history of complexity: NP-completeness Cook-Levin Theorem (1971): the SAT problem is NP-complete. -

Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data
Eurographics Conference on Visualization (EuroVis) 2014 Volume 33 (2014), Number 3 H. Carr, P. Rheingans, and H. Schumann (Guest Editors) Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data Himangshu Saikia, Hans-Peter Seidel, Tino Weinkauf Max Planck Institute for Informatics, Saarbrücken, Germany Abstract We present a method to find repeating topological structures in scalar data sets. More precisely, we compare all subtrees of two merge trees against each other – in an efficient manner exploiting redundancy. This provides pair-wise distances between the topological structures defined by sub/superlevel sets, which can be exploited in several applications such as finding similar structures in the same data set, assessing periodic behavior in time-dependent data, and comparing the topology of two different data sets. To do so, we introduce a novel data structure called the extended branch decomposition graph, which is composed of the branch decompositions of all subtrees of the merge tree. Based on dynamic programming, we provide two highly efficient algorithms for computing and comparing extended branch decomposition graphs. Several applications attest to the utility of our method and its robustness against noise. 1. Introduction • We introduce the extended branch decomposition graph: a novel data structure that describes the hierarchical decom- Structures repeat in both nature and engineering. An example position of all subtrees of a join/split tree. We abbreviate it is the symmetric arrangement of the atoms in molecules such with ‘eBDG’. as Benzene. A prime example for a periodic process is the • We provide a fast algorithm for computing an eBDG. Typ- combustion in a car engine where the gas concentration in a ical runtimes are in the order of milliseconds. -

3.1 Matchings and Factors: Matchings and Covers
1 3.1 Matchings and Factors: Matchings and Covers This copyrighted material is taken from Introduction to Graph Theory, 2nd Ed., by Doug West; and is not for further distribution beyond this course. These slides will be stored in a limited-access location on an IIT server and are not for distribution or use beyond Math 454/553. 2 Matchings 3.1.1 Definition A matching in a graph G is a set of non-loop edges with no shared endpoints. The vertices incident to the edges of a matching M are saturated by M (M-saturated); the others are unsaturated (M-unsaturated). A perfect matching in a graph is a matching that saturates every vertex. perfect matching M-unsaturated M-saturated M Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 3 Perfect Matchings in Complete Bipartite Graphs a 1 The perfect matchings in a complete b 2 X,Y-bigraph with |X|=|Y| exactly c 3 correspond to the bijections d 4 f: X -> Y e 5 Therefore Kn,n has n! perfect f 6 matchings. g 7 Kn,n The complete graph Kn has a perfect matching iff… Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 4 Perfect Matchings in Complete Graphs The complete graph Kn has a perfect matching iff n is even. So instead of Kn consider K2n. We count the perfect matchings in K2n by: (1) Selecting a vertex v (e.g., with the highest label) one choice u v (2) Selecting a vertex u to match to v K2n-2 2n-1 choices (3) Selecting a perfect matching on the rest of the vertices. -

Approximation Algorithms
Lecture 21 Approximation Algorithms 21.1 Overview Suppose we are given an NP-complete problem to solve. Even though (assuming P = NP) we 6 can’t hope for a polynomial-time algorithm that always gets the best solution, can we develop polynomial-time algorithms that always produce a “pretty good” solution? In this lecture we consider such approximation algorithms, for several important problems. Specific topics in this lecture include: 2-approximation for vertex cover via greedy matchings. • 2-approximation for vertex cover via LP rounding. • Greedy O(log n) approximation for set-cover. • Approximation algorithms for MAX-SAT. • 21.2 Introduction Suppose we are given a problem for which (perhaps because it is NP-complete) we can’t hope for a fast algorithm that always gets the best solution. Can we hope for a fast algorithm that guarantees to get at least a “pretty good” solution? E.g., can we guarantee to find a solution that’s within 10% of optimal? If not that, then how about within a factor of 2 of optimal? Or, anything non-trivial? As seen in the last two lectures, the class of NP-complete problems are all equivalent in the sense that a polynomial-time algorithm to solve any one of them would imply a polynomial-time algorithm to solve all of them (and, moreover, to solve any problem in NP). However, the difficulty of getting a good approximation to these problems varies quite a bit. In this lecture we will examine several important NP-complete problems and look at to what extent we can guarantee to get approximately optimal solutions, and by what algorithms. -

Lower Bounds Based on the Exponential Time Hypothesis
Lower bounds based on the Exponential Time Hypothesis Daniel Lokshtanov∗ Dániel Marxy Saket Saurabhz Abstract In this article we survey algorithmic lower bound results that have been obtained in the field of exact exponential time algorithms and pa- rameterized complexity under certain assumptions on the running time of algorithms solving CNF-Sat, namely Exponential time hypothesis (ETH) and Strong Exponential time hypothesis (SETH). 1 Introduction The theory of NP-hardness gives us strong evidence that certain fundamen- tal combinatorial problems, such as 3SAT or 3-Coloring, are unlikely to be polynomial-time solvable. However, NP-hardness does not give us any information on what kind of super-polynomial running time is possible for NP-hard problems. For example, according to our current knowledge, the complexity assumption P 6= NP does not rule out the possibility of having an nO(log n) time algorithm for 3SAT or an nO(log log k) time algorithm for k- Clique, but such incredibly efficient super-polynomial algorithms would be still highly surprising. Therefore, in order to obtain qualitative lower bounds that rule out such algorithms, we need a complexity assumption stronger than P 6= NP. Impagliazzo, Paturi, and Zane [38, 37] introduced the Exponential Time Hypothesis (ETH) and the stronger variant, the Strong Exponential Time Hypothesis (SETH). These complexity assumptions state lower bounds on how fast satisfiability problems can be solved. These assumptions can be used as a basis for qualitative lower bounds for other concrete computational problems. ∗Dept. of Comp. Sc. and Engineering, University of California, USA. [email protected] yInstitut für Informatik, Humboldt-Universiät , Berlin, Germany. -

Multi-Budgeted Matchings and Matroid Intersection Via Dependent Rounding
Multi-budgeted Matchings and Matroid Intersection via Dependent Rounding Chandra Chekuri∗ Jan Vondrak´ y Rico Zenklusenz Abstract ing: given a fractional point x in a polytope P ⊂ Rn, ran- Motivated by multi-budgeted optimization and other applications, domly round x to a solution R corresponding to a vertex we consider the problem of randomly rounding a fractional solution of P . Here P captures the deterministic constraints that we x in the (non-bipartite graph) matching and matroid intersection wish the rounding to satisfy, and it is natural to assume that polytopes. We show that for any fixed δ > 0, a given point P is an integer polytope (typically a f0; 1g polytope). Of course the important issue is what properties we need R to x can be rounded to a random solution R such that E[1R] = (1 − δ)x and any linear function of x satisfies dimension-free satisfy, and this is dictated by the application at hand. A Chernoff-Hoeffding concentration bounds (the bounds depend on property that is useful in several applications is that R sat- δ and the expectation µ). We build on and adapt the swap isfies concentration properties for linear functions of x: that n rounding scheme in our recent work [9] to achieve this result. is, for any vector a 2 [0; 1] , we want the linear function P 1 Our main contribution is a non-trivial martingale based analysis a(R) = i2R ai to be concentrated around its expectation . framework to prove the desired concentration bounds. In this Ideally, we would like to have E[1R] = x, which would P paper we describe two applications. -

12. Exponential Time Hypothesis COMP6741: Parameterized and Exact Computation
12. Exponential Time Hypothesis COMP6741: Parameterized and Exact Computation Serge Gaspers Semester 2, 2017 Contents 1 SAT and k-SAT 1 2 Subexponential time algorithms 2 3 ETH and SETH 2 4 Algorithmic lower bounds based on ETH 2 5 Algorithmic lower bounds based on SETH 3 6 Further Reading 4 1 SAT and k-SAT SAT SAT Input: A propositional formula F in conjunctive normal form (CNF) Parameter: n = jvar(F )j, the number of variables in F Question: Is there an assignment to var(F ) satisfying all clauses of F ? k-SAT Input: A CNF formula F where each clause has length at most k Parameter: n = jvar(F )j, the number of variables in F Question: Is there an assignment to var(F ) satisfying all clauses of F ? Example: (x1 _ x2) ^ (:x2 _ x3 _:x4) ^ (x1 _ x4) ^ (:x1 _:x3 _:x4) Algorithms for SAT • Brute-force: O∗(2n) • ... after > 50 years of SAT solving (SAT association, SAT conference, JSAT journal, annual SAT competitions, ...) • fastest known algorithm for SAT: O∗(2n·(1−1=O(log m=n))), where m is the number of clauses [Calabro, Impagli- azzo, Paturi, 2006] [Dantsin, Hirsch, 2009] • However: no O∗(1:9999n) time algorithm is known 1 • fastest known algorithms for 3-SAT: O∗(1:3303n) deterministic [Makino, Tamaki, Yamamoto, 2013] and O∗(1:3071n) randomized [Hertli, 2014] • Could it be that 3-SAT cannot be solved in 2o(n) time? • Could it be that SAT cannot be solved in O∗((2 − )n) time for any > 0? 2 Subexponential time algorithms NP-hard problems in subexponential time? • Are there any NP-hard problems that can be solved in 2o(n) time? • Yes. -

On Miniaturized Problems in Parameterized Complexity Theory
On miniaturized problems in parameterized complexity theory Yijia Chen Institut fur¨ Informatik, Humboldt-Universitat¨ zu Berlin, Unter den Linden 6, 10099 Berlin, Germany. [email protected] Jorg¨ Flum Abteilung fur¨ Mathematische Logik, Universitat¨ Freiburg, Eckerstr. 1, 79104 Freiburg, Germany. [email protected] Abstract We introduce a general notion of miniaturization of a problem that comprises the different miniaturizations of concrete problems considered so far. We develop parts of the basic theory of miniaturizations. Using the appropriate logical formalism, we show that the miniaturization of a definable problem in W[t] lies in W[t], too. In particular, the miniaturization of the dominating set problem is in W[2]. Furthermore we investigate the relation between f(k) · no(k) time and subexponential time algorithms for the dominating set problem and for the clique problem. 1. Introduction Parameterized complexity theory provides a framework for a refined complexity analysis of algorithmic problems that are intractable in general. Central to the theory is the notion of fixed-parameter tractability, which relaxes the classical notion of tractability, polynomial time computability, by admitting algorithms whose runtime is exponential, but only in terms of some parameter that is usually expected to be small. Let FPT denote the class of all fixed-parameter tractable problems. A well-known example of a problem in FPT is the vertex cover problem, the parameter being the size of the vertex cover we ask for. As a complexity theoretic counterpart, a theory of parameterized intractability has been developed. In classical complex- ity, the notion of NP-completeness is central to a nice and simple theory for intractable problems. -

FPT Algorithms and Kernelization?
Noname manuscript No. (will be inserted by the editor) Structural Parameterizations of Undirected Feedback Vertex Set: FPT Algorithms and Kernelization? Diptapriyo Majumdar · Venkatesh Raman Received: date / Accepted: date Abstract A feedback vertex set in an undirected graph is a subset of vertices whose removal results in an acyclic graph. We consider the parameterized and kernelization complexity of feedback vertex set where the parameter is the size of some structure in the input. In particular, we consider parameterizations where the parameter is (instead of the solution size), the distance to a class of graphs where the problem is polynomial time solvable, and sometimes smaller than the solution size. Here, by distance to a class of graphs, we mean the minimum number of vertices whose removal results in a graph in the class. Such a set of vertices is also called the `deletion set'. In this paper, we show that k (1) { FVS is fixed-parameter tractable by an O(2 nO ) time algorithm, but is unlikely to have polynomial kernel when parameterized by the number of vertices of the graph whose degree is at least 4. This answersp a question asked in an earlier paper. We also show that an algorithm with k (1) running time O(( 2 − ) nO ) is not possible unless SETH fails. { When parameterized by k, the number of vertices, whose deletion results in a split graph, we give k (1) an O(3:148 nO ) time algorithm. { When parameterized by k, the number of vertices whose deletion results in a cluster graph (a k (1) disjoint union of cliques), we give an O(5 nO ) algorithm. -

The Complexity of Multivariate Matching Polynomials
The Complexity of Multivariate Matching Polynomials Ilia Averbouch∗ and J.A.Makowskyy Faculty of Computer Science Israel Institute of Technology Haifa, Israel failia,[email protected] February 28, 2007 Abstract We study various versions of the univariate and multivariate matching and rook polynomials. We show that there is most general multivariate matching polynomial, which is, up the some simple substitutions and multiplication with a prefactor, the original multivariate matching polynomial introduced by C. Heilmann and E. Lieb. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte, B. Bollobas and O. Riordan, and A. Sokal in studying the chromatic and the Tutte polynomial. We show here that evaluating these polynomials over the reals is ]P-hard for all points in Rk but possibly for an exception set which is semi-algebraic and of dimension strictly less than k. This result is analoguous to the characterization due to F. Jaeger, D. Vertigan and D. Welsh (1990) of the points where the Tutte polynomial is hard to evaluate. Our proof, however, builds mainly on the work by M. Dyer and C. Greenhill (2000). 1 Introduction In this paper we study generalizations of the matching and rook polynomials and their complexity. The matching polynomial was originally introduced in [5] as a multivariate polynomial. Some of its general properties, in particular the so called half-plane property, were studied recently in [2]. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte [15], B. -
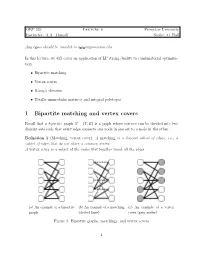
1 Bipartite Matching and Vertex Covers
ORF 523 Lecture 6 Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Any typos should be emailed to a a [email protected]. In this lecture, we will cover an application of LP strong duality to combinatorial optimiza- tion: • Bipartite matching • Vertex covers • K¨onig'stheorem • Totally unimodular matrices and integral polytopes. 1 Bipartite matching and vertex covers Recall that a bipartite graph G = (V; E) is a graph whose vertices can be divided into two disjoint sets such that every edge connects one node in one set to a node in the other. Definition 1 (Matching, vertex cover). A matching is a disjoint subset of edges, i.e., a subset of edges that do not share a common vertex. A vertex cover is a subset of the nodes that together touch all the edges. (a) An example of a bipartite (b) An example of a matching (c) An example of a vertex graph (dotted lines) cover (grey nodes) Figure 1: Bipartite graphs, matchings, and vertex covers 1 Lemma 1. The cardinality of any matching is less than or equal to the cardinality of any vertex cover. This is easy to see: consider any matching. Any vertex cover must have nodes that at least touch the edges in the matching. Moreover, a single node can at most cover one edge in the matching because the edges are disjoint. As it will become clear shortly, this property can also be seen as an immediate consequence of weak duality in linear programming. Theorem 1 (K¨onig). If G is bipartite, the cardinality of the maximum matching is equal to the cardinality of the minimum vertex cover.