Map-Matching Using Shortest Paths
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data
Eurographics Conference on Visualization (EuroVis) 2014 Volume 33 (2014), Number 3 H. Carr, P. Rheingans, and H. Schumann (Guest Editors) Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data Himangshu Saikia, Hans-Peter Seidel, Tino Weinkauf Max Planck Institute for Informatics, Saarbrücken, Germany Abstract We present a method to find repeating topological structures in scalar data sets. More precisely, we compare all subtrees of two merge trees against each other – in an efficient manner exploiting redundancy. This provides pair-wise distances between the topological structures defined by sub/superlevel sets, which can be exploited in several applications such as finding similar structures in the same data set, assessing periodic behavior in time-dependent data, and comparing the topology of two different data sets. To do so, we introduce a novel data structure called the extended branch decomposition graph, which is composed of the branch decompositions of all subtrees of the merge tree. Based on dynamic programming, we provide two highly efficient algorithms for computing and comparing extended branch decomposition graphs. Several applications attest to the utility of our method and its robustness against noise. 1. Introduction • We introduce the extended branch decomposition graph: a novel data structure that describes the hierarchical decom- Structures repeat in both nature and engineering. An example position of all subtrees of a join/split tree. We abbreviate it is the symmetric arrangement of the atoms in molecules such with ‘eBDG’. as Benzene. A prime example for a periodic process is the • We provide a fast algorithm for computing an eBDG. Typ- combustion in a car engine where the gas concentration in a ical runtimes are in the order of milliseconds. -

Exploiting C-Closure in Kernelization Algorithms for Graph Problems
Exploiting c-Closure in Kernelization Algorithms for Graph Problems Tomohiro Koana Technische Universität Berlin, Algorithmics and Computational Complexity, Germany [email protected] Christian Komusiewicz Philipps-Universität Marburg, Fachbereich Mathematik und Informatik, Marburg, Germany [email protected] Frank Sommer Philipps-Universität Marburg, Fachbereich Mathematik und Informatik, Marburg, Germany [email protected] Abstract A graph is c-closed if every pair of vertices with at least c common neighbors is adjacent. The c-closure of a graph G is the smallest number such that G is c-closed. Fox et al. [ICALP ’18] defined c-closure and investigated it in the context of clique enumeration. We show that c-closure can be applied in kernelization algorithms for several classic graph problems. We show that Dominating Set admits a kernel of size kO(c), that Induced Matching admits a kernel with O(c7k8) vertices, and that Irredundant Set admits a kernel with O(c5/2k3) vertices. Our kernelization exploits the fact that c-closed graphs have polynomially-bounded Ramsey numbers, as we show. 2012 ACM Subject Classification Theory of computation → Parameterized complexity and exact algorithms; Theory of computation → Graph algorithms analysis Keywords and phrases Fixed-parameter tractability, kernelization, c-closure, Dominating Set, In- duced Matching, Irredundant Set, Ramsey numbers Funding Frank Sommer: Supported by the Deutsche Forschungsgemeinschaft (DFG), project MAGZ, KO 3669/4-1. 1 Introduction Parameterized complexity [9, 14] aims at understanding which properties of input data can be used in the design of efficient algorithms for problems that are hard in general. The properties of input data are encapsulated in the notion of a parameter, a numerical value that can be attributed to each input instance I. -

3.1 Matchings and Factors: Matchings and Covers
1 3.1 Matchings and Factors: Matchings and Covers This copyrighted material is taken from Introduction to Graph Theory, 2nd Ed., by Doug West; and is not for further distribution beyond this course. These slides will be stored in a limited-access location on an IIT server and are not for distribution or use beyond Math 454/553. 2 Matchings 3.1.1 Definition A matching in a graph G is a set of non-loop edges with no shared endpoints. The vertices incident to the edges of a matching M are saturated by M (M-saturated); the others are unsaturated (M-unsaturated). A perfect matching in a graph is a matching that saturates every vertex. perfect matching M-unsaturated M-saturated M Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 3 Perfect Matchings in Complete Bipartite Graphs a 1 The perfect matchings in a complete b 2 X,Y-bigraph with |X|=|Y| exactly c 3 correspond to the bijections d 4 f: X -> Y e 5 Therefore Kn,n has n! perfect f 6 matchings. g 7 Kn,n The complete graph Kn has a perfect matching iff… Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 4 Perfect Matchings in Complete Graphs The complete graph Kn has a perfect matching iff n is even. So instead of Kn consider K2n. We count the perfect matchings in K2n by: (1) Selecting a vertex v (e.g., with the highest label) one choice u v (2) Selecting a vertex u to match to v K2n-2 2n-1 choices (3) Selecting a perfect matching on the rest of the vertices. -

Approximation Algorithms
Lecture 21 Approximation Algorithms 21.1 Overview Suppose we are given an NP-complete problem to solve. Even though (assuming P = NP) we 6 can’t hope for a polynomial-time algorithm that always gets the best solution, can we develop polynomial-time algorithms that always produce a “pretty good” solution? In this lecture we consider such approximation algorithms, for several important problems. Specific topics in this lecture include: 2-approximation for vertex cover via greedy matchings. • 2-approximation for vertex cover via LP rounding. • Greedy O(log n) approximation for set-cover. • Approximation algorithms for MAX-SAT. • 21.2 Introduction Suppose we are given a problem for which (perhaps because it is NP-complete) we can’t hope for a fast algorithm that always gets the best solution. Can we hope for a fast algorithm that guarantees to get at least a “pretty good” solution? E.g., can we guarantee to find a solution that’s within 10% of optimal? If not that, then how about within a factor of 2 of optimal? Or, anything non-trivial? As seen in the last two lectures, the class of NP-complete problems are all equivalent in the sense that a polynomial-time algorithm to solve any one of them would imply a polynomial-time algorithm to solve all of them (and, moreover, to solve any problem in NP). However, the difficulty of getting a good approximation to these problems varies quite a bit. In this lecture we will examine several important NP-complete problems and look at to what extent we can guarantee to get approximately optimal solutions, and by what algorithms. -

Quantum Algorithms for Matching Problems
Quantum Algorithms for Matching Problems Sebastian D¨orn Institut f¨urTheoretische Informatik, Universit¨atUlm, 89069 Ulm, Germany [email protected] Abstract. We present quantum algorithms for the following matching problems in unweighted and weighted graphs with n vertices and m edges: √ – Finding a maximal matching in general graphs in time O( nm log2 n). √ – Finding a maximum matching in general graphs in time O(n m log2 n). – Finding a maximum weight matching in bipartite graphs in time √ O(n mN log2 n), where N is the largest edge weight. – Finding a minimum weight perfect matching in bipartite graphs in √ time O(n nm log3 n). These results improve the best classical complexity bounds for the corre- sponding problems. In particular, the second result solves an open ques- tion stated in a paper by Ambainis and Spalekˇ [AS06]. 1 Introduction A matching in a graph is a set of edges such that for every vertex at most one edge of the matching is incident on the vertex. The task is to find a matching of maximum cardinality. The matching problem has many important applications in graph theory and computer science. In this paper we study the complexity of algorithms for the matching prob- lems on quantum computers and compare these to the best known classical algo- rithms. We will consider different versions of the matching problems, depending on whether the graph is bipartite or not and whether the graph is unweighted or weighted. For unweighted graphs, the best classical algorithm for finding a match- ing of maximum√ cardinality is based on augmenting paths and has running time O( nm) (see Micali and Vazirani [MV80]). -

Multi-Budgeted Matchings and Matroid Intersection Via Dependent Rounding
Multi-budgeted Matchings and Matroid Intersection via Dependent Rounding Chandra Chekuri∗ Jan Vondrak´ y Rico Zenklusenz Abstract ing: given a fractional point x in a polytope P ⊂ Rn, ran- Motivated by multi-budgeted optimization and other applications, domly round x to a solution R corresponding to a vertex we consider the problem of randomly rounding a fractional solution of P . Here P captures the deterministic constraints that we x in the (non-bipartite graph) matching and matroid intersection wish the rounding to satisfy, and it is natural to assume that polytopes. We show that for any fixed δ > 0, a given point P is an integer polytope (typically a f0; 1g polytope). Of course the important issue is what properties we need R to x can be rounded to a random solution R such that E[1R] = (1 − δ)x and any linear function of x satisfies dimension-free satisfy, and this is dictated by the application at hand. A Chernoff-Hoeffding concentration bounds (the bounds depend on property that is useful in several applications is that R sat- δ and the expectation µ). We build on and adapt the swap isfies concentration properties for linear functions of x: that n rounding scheme in our recent work [9] to achieve this result. is, for any vector a 2 [0; 1] , we want the linear function P 1 Our main contribution is a non-trivial martingale based analysis a(R) = i2R ai to be concentrated around its expectation . framework to prove the desired concentration bounds. In this Ideally, we would like to have E[1R] = x, which would P paper we describe two applications. -

Lecture 18 Solving Shortest Path Problem: Dijkstra's Algorithm
Lecture 18 Solving Shortest Path Problem: Dijkstra’s Algorithm October 23, 2009 Lecture 18 Outline • Focus on Dijkstra’s Algorithm • Importance: Where it has been used? • Algorithm’s general description • Algorithm steps in detail • Example Operations Research Methods 1 Lecture 18 One-To-All Shortest Path Problem We are given a weighted network (V, E, C) with node set V , edge set E, and the weight set C specifying weights cij for the edges (i, j) ∈ E. We are also given a starting node s ∈ V . The one-to-all shortest path problem is the problem of determining the shortest path from node s to all the other nodes in the network. The weights on the links are also referred as costs. Operations Research Methods 2 Lecture 18 Algorithms Solving the Problem • Dijkstra’s algorithm • Solves only the problems with nonnegative costs, i.e., cij ≥ 0 for all (i, j) ∈ E • Bellman-Ford algorithm • Applicable to problems with arbitrary costs • Floyd-Warshall algorithm • Applicable to problems with arbitrary costs • Solves a more general all-to-all shortest path problem Floyd-Warshall and Bellman-Ford algorithm solve the problems on graphs that do not have a cycle with negative cost. Operations Research Methods 3 Lecture 18 Importance of Dijkstra’s algorithm Many more problems than you might at first think can be cast as shortest path problems, making Dijkstra’s algorithm a powerful and general tool. For example: • Dijkstra’s algorithm is applied to automatically find directions between physical locations, such as driving directions on websites like Mapquest or Google Maps. -

Faster Shortest-Path Algorithms for Planar Graphs
Journal of Computer and System SciencesSS1493 journal of computer and system sciences 55, 323 (1997) article no. SS971493 Faster Shortest-Path Algorithms for Planar Graphs Monika R. Henzinger* Department of Computer Science, Cornell University, Ithaca, New York 14853 Philip Klein- Department of Computer Science, Brown Univrsity, Providence, Rhode Island 02912 Satish Rao NEC Research Institute and Sairam Subramanian Bell Northern Research Received April 18, 1995; revised August 13, 1996 and matching). In this paper we improved algorithms for We give a linear-time algorithm for single-source shortest paths in single-source shortest paths in planar networks. planar graphs with nonnegative edge-lengths. Our algorithm also The first algorithm handles the important special case of yields a linear-time algorithm for maximum flow in a planar graph nonnegative edge-lengths. For this case, we obtain a linear- with the source and sink on the same face. For the case where time algorithm. Thus our algorithm is optimal, up to con- negative edge-lengths are allowed, we give an algorithm requiring O(n4Â3 log(nL)) time, where L is the absolute value of the most stant factors. No linear-time algorithm for shortest paths in negative length. This algorithm can be used to obtain similar bounds for planar graphs was previously known. For general graphs computing a feasible flow in a planar network, for finding a perfect the best bounds known in the standard model, which for- matching in a planar bipartite graph, and for finding a maximum flow in bids bit-manipulation of the lengths, is O(m+n log n) time, a planar graph when the source and sink are not on the same face. -

The Complexity of Multivariate Matching Polynomials
The Complexity of Multivariate Matching Polynomials Ilia Averbouch∗ and J.A.Makowskyy Faculty of Computer Science Israel Institute of Technology Haifa, Israel failia,[email protected] February 28, 2007 Abstract We study various versions of the univariate and multivariate matching and rook polynomials. We show that there is most general multivariate matching polynomial, which is, up the some simple substitutions and multiplication with a prefactor, the original multivariate matching polynomial introduced by C. Heilmann and E. Lieb. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte, B. Bollobas and O. Riordan, and A. Sokal in studying the chromatic and the Tutte polynomial. We show here that evaluating these polynomials over the reals is ]P-hard for all points in Rk but possibly for an exception set which is semi-algebraic and of dimension strictly less than k. This result is analoguous to the characterization due to F. Jaeger, D. Vertigan and D. Welsh (1990) of the points where the Tutte polynomial is hard to evaluate. Our proof, however, builds mainly on the work by M. Dyer and C. Greenhill (2000). 1 Introduction In this paper we study generalizations of the matching and rook polynomials and their complexity. The matching polynomial was originally introduced in [5] as a multivariate polynomial. Some of its general properties, in particular the so called half-plane property, were studied recently in [2]. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte [15], B. -
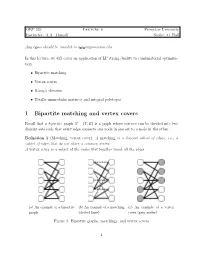
1 Bipartite Matching and Vertex Covers
ORF 523 Lecture 6 Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Any typos should be emailed to a a [email protected]. In this lecture, we will cover an application of LP strong duality to combinatorial optimiza- tion: • Bipartite matching • Vertex covers • K¨onig'stheorem • Totally unimodular matrices and integral polytopes. 1 Bipartite matching and vertex covers Recall that a bipartite graph G = (V; E) is a graph whose vertices can be divided into two disjoint sets such that every edge connects one node in one set to a node in the other. Definition 1 (Matching, vertex cover). A matching is a disjoint subset of edges, i.e., a subset of edges that do not share a common vertex. A vertex cover is a subset of the nodes that together touch all the edges. (a) An example of a bipartite (b) An example of a matching (c) An example of a vertex graph (dotted lines) cover (grey nodes) Figure 1: Bipartite graphs, matchings, and vertex covers 1 Lemma 1. The cardinality of any matching is less than or equal to the cardinality of any vertex cover. This is easy to see: consider any matching. Any vertex cover must have nodes that at least touch the edges in the matching. Moreover, a single node can at most cover one edge in the matching because the edges are disjoint. As it will become clear shortly, this property can also be seen as an immediate consequence of weak duality in linear programming. Theorem 1 (K¨onig). If G is bipartite, the cardinality of the maximum matching is equal to the cardinality of the minimum vertex cover. -

Shortest Path Problems and Algorithms
Shortest path problems and algorithms 1. Shortest path problems . Shortest path problem . Single-source shortest path problem . Single-destination shortest path problem . All-pairs shortest path problem 2. Algorithms . Dijkstra’s algorithm for single source shortest path problem (positive weight) . Bellman–Ford algorithm for single source shortest path problem (allow negative weight) . Floyd–Warshall algorithm for all pairs shortest paths . Johnson's algorithm for all pairs shortest paths CP412 ADAII 1. Shortest path problems Shortest path problem: Input: weight graph G = (V, E, W), source vertex s and destination vertex t. Output: a shortest path of G from s to t. Single-source shortest path problem: Output: shortest paths from source vertex s to all other vertices of G. Single-destination shortest path problem: Output: shortest paths from all vertices of G to a single destination t. All-pairs shortest path problem: Output: shortest paths between every pair of vertices u, v in the graph. CP412 ADAII History of SPP and algorithms Shimbel (1955). Information networks. Ford (1956). RAND, economics of transportation. Leyzorek, Gray, Johnson, Ladew, Meaker, Petry, Seitz (1957). Combat Development Dept. of the Army Electronic Proving Ground. Dantzig (1958). Simplex method for linear programming. Bellman (1958). Dynamic programming. Moore (1959). Routing long-distance telephone calls for Bell Labs. Dijkstra (1959). Simpler and faster version of Ford's algorithm. CP412 ADAII Dijkstra’s algorithms Edger W. Dijkstra’s quotes . The question of whether computers can think is like the question of whether submarines can swim. In their capacity as a tool, computers will be but a ripple on the surface of our culture. -

The On-Line Shortest Path Problem Under Partial Monitoring
Journal of Machine Learning Research 8 (2007) 2369-2403 Submitted 4/07; Revised 8/07; Published 10/07 The On-Line Shortest Path Problem Under Partial Monitoring Andras´ Gyor¨ gy [email protected] Machine Learning Research Group Computer and Automation Research Institute Hungarian Academy of Sciences Kende u. 13-17, Budapest, Hungary, H-1111 Tamas´ Linder [email protected] Department of Mathematics and Statistics Queen’s University, Kingston, Ontario Canada K7L 3N6 Gabor´ Lugosi [email protected] ICREA and Department of Economics Universitat Pompeu Fabra Ramon Trias Fargas 25-27 08005 Barcelona, Spain Gyor¨ gy Ottucsak´ [email protected] Department of Computer Science and Information Theory Budapest University of Technology and Economics Magyar Tudosok´ Kor¨ utja´ 2. Budapest, Hungary, H-1117 Editor: Leslie Pack Kaelbling Abstract The on-line shortest path problem is considered under various models of partial monitoring. Given a weighted directed acyclic graph whose edge weights can change in an arbitrary (adversarial) way, a decision maker has to choose in each round of a game a path between two distinguished vertices such that the loss of the chosen path (defined as the sum of the weights of its composing edges) be as small as possible. In a setting generalizing the multi-armed bandit problem, after choosing a path, the decision maker learns only the weights of those edges that belong to the chosen path. For this problem, an algorithm is given whose average cumulative loss in n rounds exceeds that of the best path, matched off-line to the entire sequence of the edge weights, by a quantity that is proportional to 1=pn and depends only polynomially on the number of edges of the graph.