Self-Adaptive Cybersecurity System.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Research Activity Publication 82
RESEARCH ACTIVITY Grid-Internet Platform Development Prediction System Development Software for Design of System on Services for Improved Understanding Based Cropping Period Calendar Chip (SoC) Auto-Based Hardware of Islam (2016) Android Based Results for Weather / Software Codesign Forecasting Harm Reduction investigation by Prediction (Case Study: Soreang, System Based on Results Calendar the Coastal Mangroves through Bandung District) Period Planting Weather Forecasting Numerical Modeling (2016) Detection of PCOS on Medical Image Using Evolutionary Neural Network Stain-based Optimal Algorithm Ultra Sonography (USG) to Identify (2013) for Solving Scheduling Problem Female Fertility (2014) Weather Forecasting Application f on Structure Any Graf Follicles Social Network Analysis for Social System Based on Open Source Automatic Detection Application Media Marketing in Helping SMEs (2012) Development to Support Detection (Small and Medium) System Application Owners and Based PCOS Ultrasound Image Graf Characterization Results Detection To Ensure Authenticity Pronunciation Letter Recognition of Operations Based on Index of Digital Medical Images Using System Hijaiyah Marked Read Optimization f- Kromatiknya to Multiple Watermarking Techniques (2015) Support Time Computing (2014) (2011) PUBLICATION Graph Coloring Based on Evolutionary Markov Model - The 2016 International Embedding on Greyscale Image Algorithms to Support Data Hiding Conference on Data, Internet & Colorization - The Second International Scheme on Medical Images - Procedia -

International Journal of Multicultural and Multireligious Understanding (IJMMU) Vol
Comparative Study of Post-Marriage Nationality Of Women in Legal Systems of Different Countries http://ijmmu.com [email protected] International Journal of Multicultural ISSN 2364-5369 Volume 4, Issue 1 and Multireligious Understanding February, 2017 Pages: 15-24 Traditional Leadership Model of Pluralistic Society in Ciamis District Akhmad Satori*; Subhan Agung Department of Political Science, Siliwangi University Tasikmalaya, Indonesia Email: [email protected] http://dx.doi.org/10.18415/ijmmu.v4i1.62 Abstract This study provides an analysis of traditional leadership model in managing plural society. This study sees the whole pattern formed in a very pluralistic society susuru. Although very pluralistic, the society is able to create the harmony conditions in social life. A qualitative ethnography is applied as the method of analysis. The research approach uses contructivism which develop the idea through data to produce a complete picture of the reasearch focus. The result indicates that the leadership style applies a model of charismatic and traditional authority in Susuru. Power and popularity are obtained through leadership ability in leading the religious rituals. The role of the leader is not only for religious issue, but also for a social escalation. The respect for diversity is more influenced by leader’s ability to manage potential conflict. A local model, duduluran, appear in the effort to establish peace among these differences. Keywords: Traditional leadership; pluralistic society; authority; popularity; power Introduction The dynamics of pluralism of Indonesian society has experienced ups and downs, some phenomenon of violence and conflicts of Indonesian society would undermine the integrity and unity of the nation of Indonesia. -
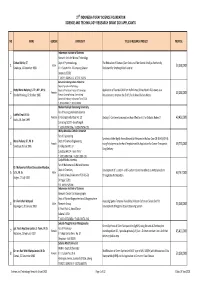
2020 App to Be Published.Xlsx
27 th INDONESIA TORAY SCIENCE FOUNDATION SCIENCE AND TECHNOLOGY RESEARCH GRANT 2020 APPLICANTS NO NAME GENDER UNIVERSITY TITLE OF RESEARCH PROJECT PROPOSE Indonesian Institute of Sciences Research Unit for Mineral Technology Fathan Bahfie, ST Dept of Pyrometallurgy The Utilization of Biomass (Corn Cobs and Palm Kernell Shell) as Ecofriendly 1 Male 50,000,000 Surabaya, 18 December 1990 Jl. Ir. Sutami Km. 15 Lampung Selatan Reductant for Smelting Nickel Laterite Lampung 35361 T. (0721) 350054 / F. (0721) 350056 Samarinda State Agriculture Polytechnic Dept of Agricultural Technology Netty Maria Naibaho, S. TP., MP., M. Sc Majors of Plantation Product of Technology Application of Essential Oils from Kaffir Limes (Citrus Hystrix DC) Leaves as a 2 Female 50,000,000 Bandar Hinalang, 02 October 1985 Kampus Gunung Panjang, Samratulangi Preservative to Improve the Shelf Life of aRaw Chicken Meats Samarinda Sebrang - Kalimantan Timur 75131 T. (0541) 260421 / F. (0541) 260680 Muhammadiyah Semarang University Fac of Nursing and Health Science Luthfia Dewi, M. Gz 3 Female Jl. Kedungmundu Raya No. 18 Dietary b -Carotene Consumption: How Effective is It for Diabetic Rodent? 49,430,000 Kudus, 04 April 1993 Semarang 50273 - Jawa Tengah T. (024) 7674-0296 / F. (024) 7674-0291 Widya Mandala Catholic University Fac of Engineering Synthesis of the Highly Accessible and pH-Responsive Hollow-Core ZIF-8 (HC@ZIF-8) Maria Yuliana, ST., Ph. D Dept of Chemical Engineering 4 Female using Polystyrene as the Hard Template and Its Application for Cancer Therapeutic 49,776,000 Surabaya, 06 July 1986 Jl. Kalijudan NO. 37 Drug Delivery Surabaya 60114 - Jawa Timur T. -

Proposed Designing Maintenance
WELCOME MESSAGE It is our privilege to welcome all presenters, participants, delegates, experts and scholars to the 1st International Conference on Industrial, Enterprise, and System Engineering (ICoIESE-2017). The support of enterprise application software (EAS) for day to day activities within one organization becomes crucial to the success of an organization. Enterprise Application Software (EAS) is computer software used to satisfy the needs of an organization rather than individual users. Such organizations would include industries, services, interest-based user groups, charities, or governments. New application developments have allowed organizations to not only improve the processes effectiveness and efficiencies for greater productivity, but have also provided businesses in order to cut costs, plan for the future, and maintain competitive advantage in the information era. The 1st International Conference on Industrial, Enterprise, and System Engineering (ICoIESE-2017) aims to bring together researchers, engineers and practitioners interested in the advances and business applications of information systems. Eight simultaneous tracks will be held, covering different aspects of Soft Computing and Data Mining, Information System, Software Engineering, Enterprise Architecture, Manufacturing System, Industrial and Supply Chain Management, Ergonomics and Human Factors, and Engineering Management. The tracks covered in ICoIESE-2017 are expected to facilitate and drive innovative ideas for attaining better quality as well as solving real- world problems in enterprise. This ICoIESE-2017 is an activity organized by School of Industrial Engineering, Telkom University, Bandung, Indonesia. The conference co-technical sponsored by IEEE Indonesia Chapter. ICoIESE-2017 held in conjunction with The IEEE Asia Pacific Conference on Wireless and Mobile 2017 (APWiMob-2017), organized and sponsored by the IEEE Communications Society Chapter Indonesia. -

List of English and Native Language Names
LIST OF ENGLISH AND NATIVE LANGUAGE NAMES ALBANIA ALGERIA (continued) Name in English Native language name Name in English Native language name University of Arts Universiteti i Arteve Abdelhamid Mehri University Université Abdelhamid Mehri University of New York at Universiteti i New York-ut në of Constantine 2 Constantine 2 Tirana Tiranë Abdellah Arbaoui National Ecole nationale supérieure Aldent University Universiteti Aldent School of Hydraulic d’Hydraulique Abdellah Arbaoui Aleksandër Moisiu University Universiteti Aleksandër Moisiu i Engineering of Durres Durrësit Abderahmane Mira University Université Abderrahmane Mira de Aleksandër Xhuvani University Universiteti i Elbasanit of Béjaïa Béjaïa of Elbasan Aleksandër Xhuvani Abou Elkacem Sa^adallah Université Abou Elkacem ^ ’ Agricultural University of Universiteti Bujqësor i Tiranës University of Algiers 2 Saadallah d Alger 2 Tirana Advanced School of Commerce Ecole supérieure de Commerce Epoka University Universiteti Epoka Ahmed Ben Bella University of Université Ahmed Ben Bella ’ European University in Tirana Universiteti Europian i Tiranës Oran 1 d Oran 1 “Luigj Gurakuqi” University of Universiteti i Shkodrës ‘Luigj Ahmed Ben Yahia El Centre Universitaire Ahmed Ben Shkodra Gurakuqi’ Wancharissi University Centre Yahia El Wancharissi de of Tissemsilt Tissemsilt Tirana University of Sport Universiteti i Sporteve të Tiranës Ahmed Draya University of Université Ahmed Draïa d’Adrar University of Tirana Universiteti i Tiranës Adrar University of Vlora ‘Ismail Universiteti i Vlorës ‘Ismail -

Book of Abstract AES 2020(1).Pdf
The Chair’s Speech Om Swastiastu, Assalamualaikum Warahmatullahi Wabarakatuh, Namo Buddhaya, Shalom. May peace be with us. The honourable Rector of Universitas Pendidikan Ganesha The honourable keynote speakers, distinguished guests, delegates, presenters, committee, and participants of the conference. First of all, let us begin by expressing our sincere gratitude to the Almighty God for all His graces bestowed upon us, so we are able to assemble here in this precious occasion. The 5th Asian Education Symposium (AES 2020) is an international refereed conference dedicated to the advancement of theories and practices in education. AES 2020 was organized by Universitas Pendidikan Indonesia (UPI) in collaboration with Universitas Pendidikan Ganesha, Universitas Negeri Manado, Universitas Islam Negeri Sunan Gunung Djati Bandung, Universitas Mataram, Universitas Pakuan, Universitas Negeri Surabaya, Universitas Negeri Semarang, Universitas Bengkulu, Universitas Kanjuruhan Malang, Universitas Islam Negeri Sulthan Thaha Syaifuddin Jambi and Universitas Islam Negeri Raden Fatah Palembang. Our theme for AES 2020 is Enhancing the Quality of Transdisciplinary Education of Sustainable Development Goals. The aim of AES 2020 is to provide an opportunity for academicians and professionals from various educational fields with cross-disciplinary interests to bridge the knowledge gap, promote research esteem and the evolution of pedagogy Through this conferences, we expect that the researchers all over the world are able to culminate reflection on how educational field answers the challenge of where new trends and technologies might lead. Distinguished Guests, Ladies and Gentlemen, The conference is attended by approximately by 157 attendees coming from different countries: Indonesia, Australia, and Japan. We are very proud to have outstanding keynote speakers who come from Indonesia, Australia, and Japan. -

Optimization Design of Irrigation Water Management to Reduce Field Failure Risk
IOP Conference Series: Materials Science and Engineering PAPER • OPEN ACCESS Optimization design of irrigation water management to reduce field failure risk To cite this article: A K Hidayat et al 2019 IOP Conf. Ser.: Mater. Sci. Eng. 550 012021 View the article online for updates and enhancements. This content was downloaded from IP address 103.123.236.253 on 18/03/2020 at 06:07 SICIR IOP Publishing IOP Conf. Series: Materials Science and Engineering 550 (2019) 012021 doi:10.1088/1757-899X/550/1/012021 Optimization design of irrigation water management to reduce field failure risk A K Hidayat1, I N Norken2, M I Yekti 3, P Irawan4 and A S Kosnayani5 1, 4Civil Engineering Department, Faculty of Engineering, Siliwangi University, Jl. Siliwangi No. 24, Tasikmalaya, West Java, Indonesia 2, 3Civil Engineering Department, Faculty of Engineering, Udayana University Jl.P.B. Sudirman, Denpasar, Kota Denpasar, Bali, Indonesia 5Nutrition Department, Faculty of Health Science, Siliwangi University Jl. Siliwangi No. 24, Tasikmalaya, West Java, Indonesia Email: [email protected] Abstract. The existing condition of the irrigation area after construction or the irrigation area in operation needs to be evaluated because in the planning of water availability and irrigation water needs many parameters-parameters which is the result of the analysis approach or indeed the data - the data that then changed. The changing conditions of the data will cause many impacts. The risk of field failure is one of impact if water availability is less than the initial estimate. This paper reports the analysis of the availability of water and irrigation water requirements is dynamic, in this study the availability of water is analyzed with 80% reliability. -

Preface International E-Conference on Sustainable Agriculture and Farming System (Icosafs 2020)
IOP Conference Series: Earth and Environmental Science PAPER • OPEN ACCESS Preface International e-Conference on Sustainable Agriculture and Farming System (ICoSAFS 2020) To cite this article: S Sudarsono et al 2021 IOP Conf. Ser.: Earth Environ. Sci. 694 011001 View the article online for updates and enhancements. This content was downloaded from IP address 170.106.35.93 on 25/09/2021 at 07:20 International e-Conference on Sustainable Agriculture and Farming System IOP Publishing IOP Conf. Series: Earth and Environmental Science 694 (2021) 011001 doi:10.1088/1755-1315/694/1/011001 Preface International e-Conference on Sustainable Agriculture and Farming System (ICoSAFS 2020) S Sudarsono1*, S Suwardi2 and A Junaedi1 1 Department of Agronomy and Horticulture, and 2 Department of Soil Science and Land Resources, Faculty of Agriculture, IPB University, Jl. Meranti, Darmaga Campus, Bogor 16680, West Java, Indonesia *Contact email address: [email protected] Abstract. The International e-Conference on Sustainable Agriculture and Farming System (ICoSAFS 2020) was organized by the Faculty of Agriculture, IPB University, Bogor, Indonesia. The ICoSAFS 2020 was conducted to facilitate exchanges among researchers about the advanced progress in sustainable agriculture and farming system research. The e-conference successfully attracted as many as 271 attendants, 80 presentations and scientists from 10 countries including Croatia, Indonesia, Japan, Malaysia, and the USA. The major scientific presentation topics discussed in the ICoSAFS 2020 include agricultural economics, farming system, landscape, plant production, plant protection, soil science, sustainable agriculture, and other miscellaneous topics associated with sustainable agriculture and farming system. 1. Introduction Sustainable agriculture systems are among the focus subjects of researchers, farmers, and policymakers in various parts of the world. -

2Nd ICSMTR 2017
nd 2 ICSMTR 2017 INTERNATIONAL CONFERENCE ON STATISTICS, MATHEMATICS, TEACHING, AND RESEARCH Department of Statistics & Department of Mathematics Faculty of Mathematics and Natural Sciences, Universitas Negeri Makassar Jalan Daeng Tata, Kampus UNM Parangtambung Makassar, Indonesia Phone : +6285255436981 email: [email protected] Nomor : 05/ICSMTR17/X/2017 2 Oktober 2017 Lampiran : 1 berkas Perihal : Undangan Menghadiri dan Presentasi di ICSMTR 2017 Yth. (Daftar Pemakalah Terlampir) Pemakalah pada ICSMTR 2017 di Tempat Assalamu Alaikum Wr. Wb. Dengan hormat, Menindaklanjuti pengumuman pemakalah yang dinyatakan ACCEPTED pada ICSMTR 2017 yang dilaksanakan oleh Program Studi Statistika dan Jurusan Matematika Fakultas Matematika dan Ilmu Pengetahuan Alam Universitas Negeri Makassar, selanjutnya kami mengundang Bapak/Ibu untuk menghadiri konferensi dan mempresentasikan makalah Anda pada: Hari : Senin - Selasa Tanggal : 9 – 10 Oktober 2017 Tempat : Grand Clarion Hotel, Makassar, Indonesia Susunan acara konferensi dan jadwal Bapak/Ibu presentasi dapat dilihat dalam lampiran surat ini. Demikian informasi ini, atas perhatian, partisipasi, dan kehadiran Bapak/Ibu, kami mengucapkan terima kasih. Hormat kami, Chairman of Committe, Dr. Syafruddin Side, M.Si. Book of Abstracts | Book of Abstracts International Conference on Statistics, Mathematics, Teaching, and Research nd 2 ICSMTR 2017 Makassar, South Sulawesi, Indonesia October 9 – 10, 2017 Faculty of Mathematics and Natural Sciences Universitas Negeri Makassar Indonesia 2nd International Conference -

Student Perception of Upn "Veteran" Yogyakarta Brand Image As a New State University
Volume 11 Dec No. 2 2018 STUDENT PERCEPTION OF UPN "VETERAN" YOGYAKARTA BRAND IMAGE AS A NEW STATE UNIVERSITY Swastika Ajeng Dewanti, Siti Fatonah, Subhan Afifi Department of Communication Science Faculty of Social and Political Sciences, UPN “Veteran” Yogyakarta [email protected] Abstract This study aims to identify how the perception of UPN "Veteran" Yogyakarta students about the brand image owned by UPN "Veteran" Yogyakarta, to know what are the obstacles and developments that happened after UPN "Veteran" Yogyakarta became the country. Type of research used in this research is descriptive research type with qualitative method. The theory used is the theory of perception and brand image. Data collection techniques in this study were obtained through interviews, direct observation and documentation. The results showed that the brand image owned UPN "Veteran" Yogyakarta post to State College of New State is a state defense that should be realized not only in the country but also on the international scene. Student perception on brand image UPN "Veteran" Yogyakarta in its application is good enough, because it has applied discipline to the students, lecturers, and employees of UPN "Veteran" Yogyakarta, and the state defend has been attached not only to the students but also to the wider community. However, in the implementation and understanding of the state defense has not been maximal, so there are still UPN "Veteran" Yogyakarta students who do not know how the brand image owned UPN "Veteran" Yogyakarta. Keywords: brand image, defend country, perception INTRODUCTION Higher Education is one of the To improve the quality of universities important pillars in the development of a there are 14 private universities that nation. -

USAID MITRA KUNCI INITIATIVE QUARTERLY REPORT OCTOBER – DECEMBER 2020 Task Order No
USAID MITRA KUNCI INITIATIVE QUARTERLY REPORT OCTOBER – DECEMBER 2020 Task Order No. AID-497-TO-17-00001 This publication was produced by the USAID MITRA KUNCI INITIATIVE under Youth Power: Implementation IDIQ Contract AID-OAA-I-15-00014 at the request of the United States Agency for International Development. This document is made possible by the support of the American people through the United States Agency for International Development. Its contents are the sole responsibility of the author or authors and do not necessarily reflect the views of USAID or the U.S. Government. USAID MITRA KUNCI INITIATIVE QUARTERLY REPORT OCTOBER - DECEMBER 2020 Task Order No. AID-497-TO-17-00001 Program Title: USAID Mitra Kunci Initiative Sponsoring USAID Office: USAID/Indonesia Task Order Number: AID-497-TO-17-00001, under Youth Power IDIQ Contract AID-OAA- I-15-00014 COR: Ester Manurung Contractor: DAI Global, LLC Status: First submission Date of Publication: January 30, 2021 Cover picture (Top Left – Right Bottom): Mitra Kunci’s Deputy Chief of Party Muhammad Hudallah (left) delivering his presentation on community-led BLKs during the coordination meeting hosted by the Ministry of Manpower in Padang, West Sumatra, December 4. Accor Hotels Indonesia Director of Talent and Culture Faris Setiabudi delivering his presentation during the online event to promote the Guide to Equality and Inclusivity at the Workplace with Accor Hotels Indonesia on Thursday, December 3 Deputy Director of Human Capacity and Partnership USAID/Indonesia Peter Novak delivering his opening remark, at the online event with Accor Hotels Indonesia, December 3 Hamzah shared his experience of working at BCA as an employee with a physical disability during the presentation and discussion session on the Guide to Equality and Inclusivity in the Workplace for BCA employees on November 24. -

TENTATIVE Schedule of CONAPLIN 10
TIMELINE FOR THE TENTH CONFERENCE ON APPLIED LINGUISTICS AND THE SECOND ENGLISH LANGUAGE TEACHING AND TECHNOLOGY CONFERENCE November 22 - 23, 2017 Banana Inn Bandung DAY 1 WAKTU/ RUANG/ROOM- NAMA/NAME JUDUL/TITLE INSTITUSI/INSTITUTION TIME GEDUNG/BUILDING 07.00- 08.00 Registration Ballroom 08.00 - 08.30 Opening Ballroom KEYNOTE SPEECH 1 08.30 - 09.30 Technology Enhanced Language Learning: From Corpus Tools The Japan Association for Language Ballroom Robert Chartrand to CALL Applications Teaching 09.30 - 09.45 Coffee Break Plaza of B'Leaf Café 09.45 - 10.30 Poster Presentation* PARALLEL SESSION 1 Achmad Yudi The Impact of Online Peer Feedback on EFL Students’ Writing at Universitas Teknokrat Indonesia Wahyudin Tertiary Level Annisa Astrid Using Couched Peer Feedback Through Online Interaction: A UIN RADEN FATAH PALEMBANG case at a Writing Class of UIN Raden Fatah Palembang Ballroom Nur Laili Indasari; Using Toondoo.Com as Digital Literacy Practice to Enhance Getari Adyagarini Learners' Autonomy in Writing Skill Universitas Negeri Surabaya Asri Purnamasari A Classroom-Based Assessment of EFL Academic Essay Edulight English, Indonesia Teaches Writing Class - Who gets the benefits? Movement, UoE, USD Fauzul Aufa Exploring L2 Learner Interaction in Blended Collaborative Writing BINUS Jakarta Mangosteen Activities Gilang Mustika Building Students’ Creativity in Narrative Writing through Project Universitas Suryakancana 10.35-11.35 Based Learning by using Big Book Irwandi Athaya IMPROVING STUDENTS’ WRITING SKILL THROUGH Faculty of Teacher Training