The Internet As Ideological Battleground
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Joint Standing Committee on Foreign Affairs, Defence and Trade
PARLIAMENT OF AUSTRALIA Joint Standing Committee on Foreign Affairs, Defence and Trade JSCFADT membership or Senate may also ask the Committee to undertake an inquiry. Information online Introduction The Joint Standing Committee The Committee may initiate its own inquiries into annual The JSCFADT is the largest committee of the Australian reports of relevant Government departments and authorities Joint Standing Committee on Foreign Affairs, Defence and Trade Welcome from the Australian Parliament’s Joint Standing on Foreign Affairs, Defence Parliament with 32 members. Membership comprises: or reports of the Auditor-General. www.aph.gov.au/jfadt Committee on Foreign Affairs, Defence and Trade. and Trade • Five Senators and 12 House of Representatives Members An inquiry is based on the terms of reference – essentially The Parliament of Australia The Committee draws its membership from both the Senate from the governing party. a statement of the topic or issues to be examined. Usually, www.aph.gov.au and House of Representatives, with members sharing a Like many other legislatures, the Australian Parliament • Five Senators and eight House of Representatives inquiries are delegated to the relevant sub-committee to Department of Defence common interest in national security, international affairs and has established a system of committees. Australian Members from the opposition party. complete on behalf of the full Committee. www.defence.gov.au Australia’s role in the world. parliamentary committees each have a defined area of interest, such as the environment or economics. The Joint • Two Senators from a minority party or who are To complete the inquiry process, the Committee (or a Through its public inquiries and reports to Parliament, the Department of Foreign Affairs and Trade Standing Committee on Foreign Affairs, Defence and independents. -

6 April to 15 May 2017 Letter From
Issue 89 6 April to 15 May 2017 Letter from CanberrSaving you time for nine years. a Cold Autumn Edition • 18 C (free speech and similar). • Keating and others on Housing • A not-strong energy system, grid and all • Gas and cattle • Sally McManus In This Issue • More on free speech • Housing. Housing • Hawke Beer Letter From Canberra // Issue 90 Letter from Saving you time for nine years. CanberrA monthly digest of news from around Australia. a Saving you time; now in its ninth year. About Us CONTENTS Media .....................................................10 Affairs of State 43 Richmond Terrace Editorial ....................................................3 IT ............................................................10 Richmond, Melbourne, 3000 Victoria, Australia Governance ..............................................3 Immigration ...........................................10 P +61 408 033 110 [email protected] The Budget ................................................3 Justice .....................................................10 www.affairs.com.au Party Happenings .................................. 4 Housing ..................................................10 Letter From Canberra is a monthly public affairs bulletin, a simple précis, distilling and Industrial Relations and Employment . 5 Welfare ................................................... 11 interpreting public policy and government decisions, which affect business oppor- Business, Economy, Manufacturing and Transport ............................................... -

“Global Terrorism Index: 2015.” Institute for Economics and Peace
MEASURING AND UNDERSTANDING THE IMPACT OF TERRORISM Quantifying Peace and its Benefits The Institute for Economics and Peace (IEP) is an independent, non-partisan, non-profit think tank dedicated to shifting the world’s focus to peace as a positive, achievable, and tangible measure of human well-being and progress. IEP achieves its goals by developing new conceptual frameworks to define peacefulness; providing metrics for measuring peace; and uncovering the relationships between business, peace and prosperity as well as promoting a better understanding of the cultural, economic and political factors that create peace. IEP has offices in Sydney, New York and Mexico City. It works with a wide range of partners internationally and collaborates with intergovernmental organizations on measuring and communicating the economic value of peace. For more information visit www.economicsandpeace.org SPECIAL THANKS to the National Consortium for the Study of Terrorism and Responses to Terrorism (START) headquartered at the University of Maryland for their cooperation on this study and for providing the Institute for Economics and Peace with their Global Terrorism Database (GTD) datasets on terrorism. CONTENTS EXECUTIVE SUMMARY 2 ABOUT THE GLOBAL TERRORISM INDEX 6 1 RESULTS 9 Global Terrorism Index map 10 Terrorist incidents map 12 Ten countries most impacted by terrorism 20 Terrorism compared to other forms of violence 30 2 TRENDS 33 Changes in the patterns and characteristics of terrorist activity 34 Terrorist group trends 38 Foreign fighters in Iraq -

Register of Members' Interests Statement of Registrable Interests 45Th Parliament
RJ•.GISTRY OF 1 6 SEP 2016 MEMBERS' INTERESTS HOUSE OF REPRESENTATIVES REGISTER OF MEMBERS' INTERESTS STATEMENT OF REGISTRABLE INTERESTS 45TH PARLIAMENT Returninr,Members declare at p.2-6. interests as at the date of dissolution of the House in the 4411 Parliament (9 May 2016) AND at p. 7 alteratiolls since the date of dissolution Newly elected Members declare at p.2-6, interests as at the date of election (2 Ju�y 2016) AND at p. 7 alteratio11s since the date of election SURNAME (please print) ALY OTHER NAMES ANNE ELECTORAL DIVISION STATE COWAN WA Notes (I) It is suggested that the accompanying ExplanatoryNotes be read beforethe statement is completed. (2) The information which you are required to provide is contained in resolutions agreed to by the Hou e of Representatives on 9 October 1984 a.m. amended 13 February 1986, 22 October 1986, 30 November 1988, 9 November 1994, 6 November 2003 and 13 Februaiy 2008 a.m. It consists of the Member's registrable interests and the registrable interests of which the Member is aware (a) of the Member's spouse and (b) of any children who are wholly or mainly dependent on the Member for support. For the definition of"dependent children•· see the introduction to the Explanatory Notes. (3) If there is insufficient space on this fonn for the infonnationyou are required to provide, you may attach additional pages for that purpose. Please date and initial each page of any attachment. (4) Forward the·original, signed copy of alJ pages of this statement to the Registrar of Members' Interests, RG.39 Parliament House, Canberra ACT 2600. -
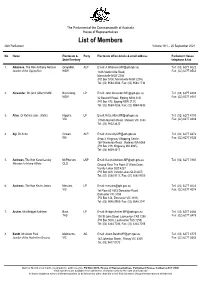
List of Senators
The Parliament of the Commonwealth of Australia House of Representatives List of Members 46th Parliament Volume 19.1 – 20 September 2021 No. Name Electorate & Party Electorate office details & email address Parliament House State/Territory telephone & fax 1. Albanese, The Hon Anthony Norman Grayndler, ALP Email: [email protected] Tel: (02) 6277 4022 Leader of the Opposition NSW 334A Marrickville Road, Fax: (02) 6277 8562 Marrickville NSW 2204 (PO Box 5100, Marrickville NSW 2204) Tel: (02) 9564 3588, Fax: (02) 9564 1734 2. Alexander, Mr John Gilbert OAM Bennelong, LP Email: [email protected] Tel: (02) 6277 4804 NSW 32 Beecroft Road, Epping NSW 2121 Fax: (02) 6277 8581 (PO Box 872, Epping NSW 2121) Tel: (02) 9869 4288, Fax: (02) 9869 4833 3. Allen, Dr Katrina Jane (Katie) Higgins, LP Email: [email protected] Tel: (02) 6277 4100 VIC 1/1343 Malvern Road, Malvern VIC 3144 Fax: (02) 6277 8408 Tel: (03) 9822 4422 4. Aly, Dr Anne Cowan, ALP Email: [email protected] Tel: (02) 6277 4876 WA Shop 3, Kingsway Shopping Centre, Fax: (02) 6277 8526 168 Wanneroo Road, Madeley WA 6065 (PO Box 219, Kingsway WA 6065) Tel: (08) 9409 4517 5. Andrews, The Hon Karen Lesley McPherson, LNP Email: [email protected] Tel: (02) 6277 7860 Minister for Home Affairs QLD Ground Floor The Point 47 Watts Drive, Varsity Lakes QLD 4227 (PO Box 409, Varsity Lakes QLD 4227) Tel: (07) 5580 9111, Fax: (07) 5580 9700 6. Andrews, The Hon Kevin James Menzies, LP Email: [email protected] Tel: (02) 6277 4023 VIC 1st Floor 651-653 Doncaster Road, Fax: (02) 6277 4074 Doncaster VIC 3108 (PO Box 124, Doncaster VIC 3108) Tel: (03) 9848 9900, Fax: (03) 9848 2741 7. -

Deradicalization Programs in Australia and the Foreign Fighter Phenomenon
Deradicalization Programs in Australia and the Foreign Fighter Phenomenon Ido Levy, (Research Assistant, ICT) April 2018 ABSTRACT As increasing numbers of Australians have traveled to Iraq and Syria to fight as “foreign fighters” for Islamist terror groups, the government and civil society have been setting up “deradicalization programs.” These programs seek to prevent or disengage “at-risk” individuals from radical ideologies. This paper surveys Australia’s existing programs and how their efforts relate to the foreign fighter phenomenon. After presenting background on Islamic extremism in Australia and Australian efforts to combat radicalization, it will survey Australian deradicalization programs and analyze how they address radicalization in general and the foreign fighter phenomenon in particular. It concludes that Australian deradicalization programs are currently inadequate in the long-term and recommends closer government cooperation with community leaders. **The views expressed in this publication are solely those of the author(s) and do not necessarily reflect the views of the International Institute for Counter-Terrorism (ICT). 2 Table of Contents Introduction ........................................................................................................................... 4 Islamic Extremism in Australia ........................................................................................... 5 Programs Addressing Deradicalization ............................................................................... 8 Youth -

Re-Imagining Australia: Migration, Culture, Diversity
Re-imagining Australia: Migration, culture, diversity Practical suggestions on the challenges and opportunities ahead Re-imagining Australia: Migration, culture, diversity Practical suggestions on the challenges and opportunities ahead Re-imagining Australia: Migration, culture, diversity Practical suggestions on the challenges and opportunities ahead Essays by Anne Aly, Colin Barnett, Farida Fozdar, Geoff Gallop, Paul J. Maginn, Mike Nahan, Juliet Pietsch, Benjamin Reilly, Shamit Saggar, Samina Yasmeen, Edward Zhang Edited by Shamit Saggar and Anna Zenz Copyright © the authors; used with permission. These works are copyright. Apart from any fair dealing for the purposes of private study, criticism or review, as permitted by the Copyright Act, no part may be reproduced by any process without written permission. Any view or opinion expressed in this publication is that of its author, and does not necessarily represent the position of the author’s affiliate organisations, The University of Western Australia or UWA Public Policy Institute. First published in 2020 by: UWA Public Policy Institute The University of Western Australia M475, 35 Stirling Highway CRAWLEY WA 6009 Design, typesetting and printing: UniPrint, The University of Western Australia. ISBN: 978-1-74052-978-5 Contents Foreword 7 Jane den Hollander, Vice-Chancellor Introduction 9 Shamit Saggar Combatting radicalisation in Australia 13 Anne Aly What middle Australia might think about immigration 21 Colin Barnett Community cohesion choices 25 Farida Fozdar Democracy, human rights -
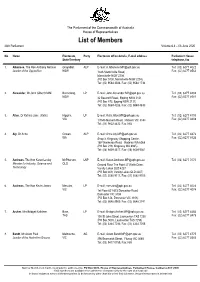
List of Members 46Th Parliament Volume 6.4 – 03 June 2020
The Parliament of the Commonwealth of Australia House of Representatives List of Members 46th Parliament Volume 6.4 – 03 June 2020 No. Name Electorate, Party Electorate office details, E-mail address Parliament House State/Territory telephone, fax 1. Albanese, The Hon Anthony Norman Grayndler, ALP E-mail: [email protected] Tel: (02) 6277 4022 Leader of the Opposition NSW 334A Marrickville Road, Fax: (02) 6277 8562 Marrickville NSW 2204 (PO Box 5100, Marrickville NSW 2204) Tel: (02) 9564 3588, Fax: (02) 9564 1734 2. Alexander, Mr John Gilbert OAM Bennelong, LP E-mail: [email protected] Tel: (02) 6277 4804 NSW 32 Beecroft Road, Epping NSW 2121 Fax: (02) 6277 8581 (PO Box 872, Epping NSW 2121) Tel: (02) 9869 4288, Fax: (02) 9869 4833 3. Allen, Dr Katrina Jane (Katie) Higgins, LP E-mail: [email protected] Tel: (02) 6277 4100 VIC 1/1343 Malvern Road, Malvern VIC 3144 Fax: (02) 6277 8408 Tel: (03) 9822 4422, Fax: N/A 4. Aly, Dr Anne Cowan, ALP E-mail: [email protected] Tel: (02) 6277 4876 WA Shop 3, Kingsway Shopping Centre, Fax: (02) 6277 8526 168 Wanneroo Road, Madeley WA 6065 (PO Box 219, Kingsway WA 6065) Tel: (08) 9409 4517, Fax: (08) 9409 9361 5. Andrews, The Hon Karen Lesley McPherson, LNP E-mail: [email protected] Tel: (02) 6277 7070 Minister for Industry, Science and QLD Ground Floor The Point 47 Watts Drive, Technology Varsity Lakes QLD 4227 (PO Box 409, Varsity Lakes QLD 4227) Tel: (07) 5580 9111, Fax: (07) 5580 9700 6. -

House of Representatives - Western Australia*
House of Representatives - Western Australia* Sitting members in BOLD | *Current 1 June 2016 Labor Liberal Greens National Email Electorate Candidate Email Candidate Email candidate Email Candidate Madeleine [email protected] Craig [email protected] Dawn Jecks [email protected] Brand King g.au Buchanan l.org.au Matt [email protected] Matt Muhammad [email protected] [email protected] Burt Keogh u O'Sullivan Salman Barry Andrew [email protected] Aeron Blundell- [email protected] [email protected] Canning Winmar Hastie ov.au Camden m [email protected] Anne Aly Sheridan Young [email protected] Cowan [email protected] Luke Simpkins v.au curtinco- Melissa [email protected]. Viv Glance [email protected]. Callanan au Curtin [email protected] Julie Bishop au Carol [email protected] Ian James Durack Martin [email protected] Melissa Price v.au [email protected] Lorrae [email protected] Jill Reading [email protected] Forrest Loud [email protected] Nola Marino .au Josh http://www.pierrettekelly. [email protected]. joshforfremantle@walabor. Pierrette Kelly Kate Davis Wilson com.au/contact-pierrette/ au Fremantle org.au Bill [email protected] [email protected] Hasluck Leadbetter [email protected] Ken Wyatt u Patrick Hyslop ens.org.au Ian ian.goodenough.mp@aph. Daniel Lindley Moore Goodenough gov.au [email protected] [email protected] John John.hassell@nation Jon Ford [email protected] O'Connor [email protected] Rick Wilson u Giz Watson Hassell alswa.com Thomas Christian christian.porter.mp@aph. -

The Australian Capital Territory New South Wales
Names and electoral office addresses of Federal Members of Parliament The Australian Capital Territory ......................................................................................................... 1 New South Wales ............................................................................................................................... 1 Northern Territory .............................................................................................................................. 4 Queensland ........................................................................................................................................ 4 South Australia .................................................................................................................................. 6 Tasmania ........................................................................................................................................... 6 Victoria ............................................................................................................................................... 7 Western Australia .............................................................................................................................. 9 How to address Members of Parliament ........................................................................... 10 The Australian Capital Territory Ms Gai Brodtmann, MP Hon Dr Andrew Leigh, MP 205 Anketell St, Unit 8/1 Torrens St, Tuggeranong ACT, 2900 Braddon ACT, 2612 New South Wales Hon Anthony Abbott, -

Social Implications of Fearing Terrorism. a Report on Australian Responses to the Images
Edith Cowan University Research Online "Exploding Media Myths : Misrepresenting Australia?" - Forum Conferences, Symposia and Campus Events 2009 Social Implications of Fearing Terrorism. A report on Australian responses to the images Anne Aly Edith Cowan University Lelia Green Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/cexplodingmyth Part of the Communication Technology and New Media Commons This Report is posted at Research Online. https://ro.ecu.edu.au/cexplodingmyth/1 Social implications of fearing terrorism. A report on Australian responses to the images and discourses of terrorism and the other: Establishing a metric of fear An Australian Research Council Discovery Project Incorporating the recommendations of a community workshop held at UNSW in November 2008 Published by: Edith Cowan University 2 Bradford Street, Mt Lawley, Western Australia, 6050 Editors: Dr Anne Aly Professor Lelia Green Professor Mark Balnaves Copyright © 2009 Anne Aly and Lelia Green All rights reserved ISBN: 978-0-7298-0683-1 A website containing publications arising from this project can be accessed at: www.explodingmediamyths.org.au/publications.html This research was supported under Australian Research Council's Discovery Projects funding scheme (project DP0559707). The views expressed herein are those of the authors and are not necessarily those of the Australian Research Council. Contents FOREWARD EXECUTIVE SUMMARY ................................................................................................................ -

The Rise of Right-Wing Extremism with Doctor Anne Aly MP Recorded Live at 12Pm, 10 February 2021
Webinar Transcript: The Rise of Right-Wing Extremism with Doctor Anne Aly MP Recorded live at 12pm, 10 February 2021 The Rise of Right-Wing Extremism Speakers: Dr Anne Aly MP, International Counter Terrorism Expert, Member for Cowan Dr Richard Denniss, Chief Economist at The Australia Institute Ebony Bennett, Deputy Director at the Australia Institute Ebony Bennett G'day everyone, welcome back. My name is Ebony Bennett. I'm Deputy 00:00 Director at the Australia Institute. And welcome back to our webinar series. We're delighted you can join us again, I can see people I like to say streaming through the doors, but it's certainly virtual a virtual participant can't cropping up there on the right, but we do have more than two and a half 1000 people RSVP for today's webinar. So thank you so much for coming along. I'd like to begin by acknowledging the traditional owners of the land on which I live in work here in Canberra, cameras, none of your country and I acknowledge that sovereignty was never stated, pay my respects to elder's past and present, and also recognise that the 2017 statement from the hot was an invitation for us to participate in creating a voice to Parliament, a treaty making process and a truth telling process and that we all need to be a part of making that happen. And we'll be looking for ways to continue to support that process this year through the webinar series. We have created these webinars in response last year to the pandemic, but they were so popular that we've decided to keep doing them.