How to Receive and Process Attachments While Greatly Reducing the Risk of Viruses and Trojans
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Evidence Finder Report
Patrick Leahy Center for Digital Investigation (LCDI) Internet Evidence Finder Report Written and Researched by Nick Murray 175 Lakeside Ave, Room 300A Phone: 802/865-5744 Fax: 802/865-6446 http://www.lcdi.champlin.edu July 2013 IEF Report 6/28/2013 Page 1 of 33 Patrick Leahy Center for Digital Investigation (LCDI) Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................. 5 Prior Work: .......................................................................................................................................................... 7 Purpose and Scope: ............................................................................................................................................ -

Introduction to Online Sexual Exploitation Curriculum 1 Safe Online Outreach Project Learning Objectives
Introduction To Online Sexual Exploitation: Curriculum February 2003 Safe OnLine Outreach Project © M. Horton 2003 Safe OnLine Outreach Project Acknowledgements This document is the result of many hours of hard work and dedication. I'd like to thank Renata Karrys, Jaynne Aster, Nikki O'Halloran, Charlaine Avery, Lisa Ingvallsen and Elizabeth Nethery for their support and assistance in producing this document. Additionally the SOLO Advisory Committee, the Canadian National Crime Prevention - Community Mobilization Program, the Vancouver Foundation, Athabasca University/MediaCan and Parents Against Sexual Abuse have all been instrumental in turning this idea into a Project. Lastly, David and Conor have been silent contributors to this project since it began. Their support is woven into each page. Merlyn Horton SOLO Project Coordinator February 2003 Safe OnLine Outreach Project February 3, 2003 Introduction to the Curriculum Dear Reader, The curriculum you hold in your hands was produced in a former pottery studio in the middle of a coastal rain forest in British Columbia, Canada; the physical launch pad for this examination of a virtual issue. It is the result of three years of research. This introduction is intended to outline a context for the curriculum and to give you an overview of how to use this curriculum, who should present this curriculum and how appropriate audiences might be chosen. Context The philosophical foundation for this curriculum, and indeed for the Safe OnLine Outreach Project, is the United Nations Convention on the Rights of the Child (CRC)1. The CRC is one of four Conventions created by the United Nations to further the goal of recognizing the inherent dignity and rights of all members of the human family2. -

Sample Chapter
5674ch01.qxd_jt 9/24/03 8:44 AM Page 1 11 TheThe OnlineOnline WorldWorld 5674ch01.qxd_jt 9/24/03 8:44 AM Page 2 Today’s online world has changed dramatically in the last decade. Back then, online to the average user meant a telephone connection directly to either another computer or to an online service, such as CompuServe or AOL. The Internet now dominates all online activity. In popular parlance, the Internet is synonymous with the World Wide Web, although it is much more, as we’ll explain in this book. The Internet can be described generally as a “network” of networks. It is a transportation vehicle for applications. In fact, the visual representations of the Net look like a road map. If lines are drawn between each connection, between larger and larger connections, and between smaller and smaller ones, the end result is a web of connections—a virtual road map. This book is divided into four rough sections. The first is for beginners. It is to get anyone up to speed quickly with the information needed about the Web. Each chapter has recommended Web sites (to type the address, or Uniform Resource Locator [URL] into your Web browser) to help direct you. The second section has more detailed information about downloads, email, secu- rity, and information on virus protection. The third part is about how to create a Web site, Web tools, blogging, and what you can add to your Web site (such as streaming media, RSS feeds, and XML, among other things). The fourth part is by far the densest. -

Exinda Applications List
Application List Exinda ExOS Version 6.4 © 2014 Exinda Networks, Inc. 2 Copyright © 2014 Exinda Networks, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Document Built on Tuesday, October 14, 2014 at 5:10 PM Documentation conventions n bold - Interface element such as buttons or menus. For example: Select the Enable checkbox. n italics - Reference to other documents. For example: Refer to the Exinda Application List. n > - Separates navigation elements. For example: Select File > Save. n monospace text - Command line text. n <variable> - Command line arguments. n [x] - An optional CLI keyword or argument. n {x} - A required CLI element. n | - Separates choices within an optional or required element. © 2014 Exinda Networks, Inc. -

DMK BO2K8.Pdf
Black Ops 2008: It’s The End Of The Cache As We Know It Or: “64K Should Be Good Enough For Anyone” Dan Kaminsky Director of Penetration Testing IOActive, Inc. copyright IOActive, Inc. 2006, all rights reserved. Introduction • Hi! I’m Dan Kaminsky – This is my 9th talk here at Black Hat – I look for interesting design elements – new ways to manipulate old systems, old ways to manipulate new systems – Career thus far spent in Fortune 500 • Consulting now – I found a really bad bug a while ago. • You might have heard about it. • There was a rather coordinated patching effort. • I went out on a very shaky limb, to try to keep the details quiet – Asked people not to publicly speculate » Totally unreasonable request » Had to try. – Said they’d be congratulated here Thanks to the community • First finder: Pieter de Boer – Michael Gersten – 51 hours later – Mike Christian • Best Paper • Left the lists – Bernard Mueller, sec- – Paul Schmehl consult.com – Troy XYZ – Five days later, but had full – Others info/repro • Thanks • Interesting thinking (got close, – Jen Grannick (she contacted kept off lists) me) – Andre Ludwig – DNSStuff (they taught me – Nicholas Weaver LDNS, and reimplemented – “Max”/@skst (got really really my code better) close) – Everyone else (people know – Zeev Rabinovich who they are, and know I owe them a beer). Obviously thanks to the Summit Members • Paul Vixie • People have really been • David Dagon incredible with this. – Georgia Tech – thanks for • What did we accomplish? the net/compute nodes • Florian Weimer • Wouter Wijngaards • Andreas Gustaffon • Microsoft • Nominum • OpenDNS • ISC • Neustar • CERT There are numbers and are there are numbers • 120,000,000 – The number of users protected by Nominum’s carrier patching operation – They’re not the Internet’s most popular server! • That’s BIND, and we saw LOTS of BIND patching – They’re not the only server that got lots of updates • Microsoft’s Automatic Updates swept through lots and lots of users • Do not underestimate MSDNS behind the firewall. -

Covert Channels Within IRC Wayne C
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 3-11-2011 Covert Channels Within IRC Wayne C. Henry Follow this and additional works at: https://scholar.afit.edu/etd Part of the Computer and Systems Architecture Commons, and the Digital Communications and Networking Commons Recommended Citation Henry, Wayne C., "Covert Channels Within IRC" (2011). Theses and Dissertations. 1394. https://scholar.afit.edu/etd/1394 This Thesis is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. 88th ABW PUBLIC AFFAIRS SECURITY AND POLICY REVIEW WORKSHEET NOTE: Public release clearance is NOT required for material presented in a closed meeting and which will not be made available to the general public, on the Internet, in print or electronic media. I~;; ;~e;;~~~J JI. 1. SUBMITTER NAME OFFICE SYMBOL IPHONE 2. DATE SUBMITIED [email protected] AFITIENG 53636 3. AUTHOR(S) NAME ORGANIZATION PHONE Wayne C. Henry 53636 4. DOCUMENT TITLE 6. CONFERENCE/EVENT/PUBLICATION NAME 7. DATE NEEDED Covert Channels Within IRC N/A 5. DOCUMENT TYPE N/A D ABSTRACT D TECH REPORT D JOURNAL ARTICLE D VIDEO 8. EVENT lOCATION 9. EVENT DATE D SPEECH D TECH PAPER D BRIEFING CHARTS D PHOTO N/A ~ THESISIDISSERTATION D OTHER N/A 10. RELATED CASES PREVIOUSLY APPROVED 11. OTHER AGENCY COORDINATION REQUIRED 12. OTHER INFORMATION (List contact information) 13. NATIONAL SECURITY STATUTESITECHNOLOGY ISSUES 14. -

Mediawiki Presentation
An Introduction to MediaWiki Niharika Kohli Disambiguation! Table of contents • MediaWiki Architecture Overview • Getting started with MediaWiki Development • Phabricator • Git & Gerrit • Mediawiki - Vagrant • Good to know stuff • IRC • API • Extensions • GSoC and Outreachy MediaWiki Architecture Overview Gadgets Database Core MediaWiki User Scripts MySQL software Skins PostgreSQL PHP SQLite Extensions Database for Wikipedia CC BY SA. Credits to Krinkle (Timo Tijhof) Table of contents • MediaWiki Architecture Overview • Getting started with MediaWiki Development • Phabricator • Git & Gerrit • Mediawiki - Vagrant • Good to know stuff • IRC • API • Extensions • GSoC and Outreachy Where is the code? • All code is hosted on Gerrit (which we will become friends with in a bit) • The code is mirrored over to GitHub: wikimedia/mediawiki Table of contents • MediaWiki Architecture Overview • Getting started with MediaWiki Development • Phabricator • Git & Gerrit • Mediawiki - Vagrant • Good to know stuff • IRC • API • Extensions • GSoC and Outreachy Phabricator • MediaWiki’s bug reporting & tracking system • Replaced Bugzilla last year • Possibly a future Code-review system Table of contents • MediaWiki Architecture Overview • Getting started with MediaWiki Development • Phabricator • Git & Gerrit • Mediawiki - Vagrant • Good to know stuff • IRC • API • Extensions • GSoC and Outreachy What is Git? • Git is, in a nutshell, a Versioning Control System (VCS). • You have probably seen Git at work before - in Google Docs. • Git stores comprehensive revision history. • Git stores who made which changes and when. • Online code repository hosting services like GitHub and BitBucket use Git. What is Gerrit? • Gerrit • Software developers in a team can review each other's modifications on their source code using a Web browser and approve or reject those changes. -

Talk, Type, and Text: Conversation on the Internet
Talk, Type, and Text: Conversation on the Internet Jon Camfield TC660H Plan II Honors Program The University of Texas at Austin April 26, 1999 Joel F. Sherzer Anthropology Supervising Professor Heidi Johnson Linguistics Second Reader i Abstract Author: Jon Camfield Title: Talk, Type, and Text: Conversation on the Internet Supervising Professor: Dr. Joel Sherzer Second Reader: Heidi Johnson On the eve of Y2K, the extent that computers are interwoven with our lives is painfully obvious, yet only relatively recently has the academic eye taken interest in the events going on on-line. Despite this attention, there still remain new frontiers that have not been explored on the Internet. The phenomenon of real-time interaction is the best example of these. Some commentaries have treated the social aspects of MUDs, a special subspecies of real-time interaction, but more pure textual conversations have not been examined closely. This paper seeks to remedy this. I will, by necesity, place my investigations into the frame of the Internet at large, and discuss websites, e-mail and newsgroups. I will focus, however, on data from real-time interactions which use text as their only channel of communication. i Table of Contents ABSTRACT.................................................................................................................................................................. i TABLE OF CONTENTS........................................................................................................................................... -

List Software Pengganti Windows Ke Linux
Tabel Padanan Aplikasi Windows di Linux Untuk Migrasi Selasa, 18-08-2009 Kesulitan besar dalam melakukan migrasi dari Windows ke Linux adalah mencari software pengganti yang berkesesuaian. Berikut ini adalah tabel padanan aplikasi Windows di Linux yang disusun dalam beberapa kategori. Nama Program Windows Linux 1) Networking. 1) Netscape / Mozilla. 2) Galeon. 3) Konqueror. 4) Opera. [Prop] Internet Explorer, 5) Firefox. Web browser Netscape / Mozilla, Opera 6) Nautilus. [Prop], Firefox, ... 7) Epiphany. 8) Links. (with "-g" key). 9) Dillo. 10) Encompass. 1) Links. 1) Links 2) ELinks. Console web browser 2) Lynx 3) Lynx. 3) Xemacs + w3. 4) w3m. 5) Xemacs + w3. 1) Evolution. 2) Netscape / Mozilla/Thunderbird messenger. 3) Sylpheed / Claws Mail. 4) Kmail. Outlook Express, 5) Gnus. Netscape / Mozilla, 6) Balsa. Thunderbird, The Bat, 7) Bynari Insight GroupWare Suite. Email client Eudora, Becky, Datula, [Prop] Sylpheed / Claws Mail, 8) Arrow. Opera 9) Gnumail. 10) Althea. 11) Liamail. 12) Aethera. 13) MailWarrior. 14) Opera. 1) Evolution. Email client / PIM in MS 2) Bynari Insight GroupWare Suite. Outlook Outlook style [Prop] 3) Aethera. 4) Sylpheed. 5) Claws Mail 1) Sylpheed. 2) Claws Mail Email client in The Bat The Bat 3) Kmail. style 4) Gnus. 5) Balsa. 1) Pine. [NF] 2) Mutt. Mutt [de], Pine, Pegasus, Console email client 3) Gnus. Emacs 4) Elm. 5) Emacs. 1) Knode. 2) Pan. 1) Agent [Prop] 3) NewsReader. 2) Free Agent 4) Netscape / Mozilla Thunderbird. 3) Xnews 5) Opera [Prop] 4) Outlook 6) Sylpheed / Claws Mail. 5) Netscape / Mozilla Console: News reader 6) Opera [Prop] 7) Pine. [NF] 7) Sylpheed / Claws Mail 8) Mutt. -
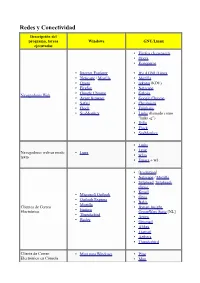
Redes Y Conectividad Descripción Del Programa, Tareas Windows GNU/Linux Ejecutadas • Firefox (Iceweasel) • Opera • Konqueror
Redes y Conectividad Descripción del programa, tareas Windows GNU/Linux ejecutadas • Firefox (Iceweasel) • Opera • Konqueror • Internet Explorer • IEs 4 GNU/Linux • Netscape / Mozilla • Mozilla • Opera • rekonq (KDE) • Firefox • Netscape • Google Chrome • Galeón Navegadores Web • Avant Browser • Google Chrome • Safari • Chromium • Flock • Epiphany • SeaMonkey • Links (llamado como "links -g") • Dillo • Flock • SeaMonkey • Links • • Lynx Navegadores web en modo Lynx • texto w3m • Emacs + w3. • [Evolution] • Netscape / Mozilla • Sylpheed , Sylpheed- claws. • Kmail • Microsoft Outlook • Gnus • Outlook Express • Balsa • Mozilla Clientes de Correo • Bynari Insight • Eudora Electrónico GroupWare Suite [NL] • Thunderbird • Arrow • Becky • Gnumail • Althea • Liamail • Aethera • Thunderbird Cliente de Correo • Mutt para Windows • Pine Electrónico en Cónsola • Mutt • Gnus • de , Pine para Windows • Elm. • Xemacs • Liferea • Knode. • Pan • Xnews , Outlook, • NewsReader Lector de noticias Netscape / Mozilla • Netscape / Mozilla. • Sylpheed / Sylpheed- claws • MultiGet • Orbit Downloader • Downloader para X. • MetaProducts Download • Caitoo (former Kget). Express • Prozilla . • Flashget • wxDownloadFast . • Go!zilla • Kget (KDE). Gestor de Descargas • Reget • Wget (console, standard). • Getright GUI: Kmago, QTget, • Wget para Windows Xget, ... • Download Accelerator Plus • Aria. • Axel. • Httrack. • WWW Offline Explorer. • Wget (consola, estándar). GUI: Kmago, QTget, Extractor de Sitios Web Teleport Pro, Webripper. Xget, ... • Downloader para X. • -

Unsecured Sessions with ICQ - Applying Forensic Computing
Master Thesis Computer Science Thesis no: MCS-2003-04 June 2003 Unsecured sessions with ICQ - applying forensic computing Martin Kling Department of Software Engineering and Computer Science Blekinge Institute of Technology Box 520 SE – 372 25 Ronneby Sweden This thesis is submitted to the Department of Software Engineering and Computer Science at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of Master of Science in Computer Science. The thesis is equivalent to 20 weeks of full time studies. Contact Information: Author: Martin Kling Address: Fältv 17 SE-291 39 Kristianstad E-mail: [email protected] Phone: +46733691999 External advisor: Tony Möörk Swedish National Criminal Investigation Department Information Technology Crime Squad P.O Box 12256 SE-102 26 Stockholm Sweden Phone: +46 8 401 48 41 University advisor: Ph.D. Bengt Carlsson Department of Software Engineering and Computer Science Department of Software Engineering and Computer Science Internet: www.bth.se/ipd Blekinge Institute of Technology Phone: +46 457 38 50 00 Box 520 Fax: + 46 457 271 25 SE – 372 25 Ronneby Sw eden ii Abstract Digital evidence is becoming more and more frequent and important in investigations carried out by the police. To make the correct judgements, the police force needs to know what one can do with ICQ and in what ways it can be exploited. This thesis aims to point out weaknesses in ICQ that can aid the police in their work. But these weaknesses can not only be used by the police, also crackers can perform malicious acts with them. Therefore, I investigated if the use of ICQ resulted in non-secure sessions. -

2600: the Hacker Quarterly
WHA Rf;.QLLY IJI.Q "Hac(.cing can get you in a who(e (0+ �ore +rout>(e than you +hink and if a co�p(ete(y creepy +hing +0 do." - lXlJ wet> page ai�ed a+ kidf +0 difcourage hacking (www.u5doj.!Jov/k.jd5pa!Je/do ..do nt/reck.(e55.ht�) s'rll If If 2600(lSSN 0749-3851) is published Editor-In-Chief quarterly by 2600 Enterprises Inc. Emmanuel Goldstein 7 Strong's Lane, Setauket, NY 11733. Second class postage permit paid at lavoUI and Design shapeSHIFTER Setauket, New York. Cover Design snc. The Chopping Block Inc. POSTMASTER: Send address changes to OfficeManager P.O. Box 752, Middle Island. NY Tamprut 2600, 11953-0752. Wrilers:Bernie S .. Billst. Blue Whale. Copyright (c) 1999 2600 Enterprises. Inc. Noam Chomski. Eric Corlev. Dr. Delam. Yearly subscription: U.S. and Canada - Derneval. Nathan Dortman. John Drake. $18 individual, $50 corporate (U.S. funds). Paul Estev. Mr. French. Thomas Icom. Joe630. Kingpin. Mm. Kevin Mitnick. The Overseas - $26 individual. $65 corporate. Prophet. David Ruderman. Seraf. Silent Back issues available for 1984-1998 at $20 Switchman. Scott Skinner. Mr. Upsetter per year. $25 per year overseas. Individual issues available from 1988 on Webmaslers:Kerrv. Macki at $5 each. S6.25 each overseas. Nelwork Ooeralions:CSS.lzaac Broadcasl Coordinalors: Juintz. ADDRESS ALL Shihlock. AbsoluteO. silicon. cnote. Anakin SUBSCRIPTION CORRESPONDENCE TO: IRC Admins:autojack. ross 2600 Subscription Dept., P.O. Box 752. Insoiralional Music: Joe Strummer. Middle Island. NY 11953-0752 Svd Barrett. real earlv Flovd. Ron Geesin ([email protected]). ShoUI OUIS: Hippies From Hell.