Connected Security for a Connected World
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dell Local Government Solutions
Dell local government solutions The Dell difference Delivering an agile, efficient and scalable architecture which is enabling local authorities to transform their services and drive down costs. Dell local government solutions - meet the other Dell Mobilising the workforce As a professional working in local government you will be aware of the role of technology in the Empowering a more mobile and agile workforce with anytime, anywhere, successful delivery of services to users, efficient processes, cost-saving opportunities and the any device access. transformation of services and working practices. What you may not know is that Dell has partnered with councils and local government organisations across the UK for over 25 years to deliver solutions and services that empower local government staff and citizens, connect communities and improve service delivery. With a dedicated team of local government specialists, our solutions have tackled just about every IT operational issue faced in local government, from the modernisation of data centres to the setting-up of shared infrastructure services, such as the one recently deployed for the Scottish Fire and Rescue Service. Government cloud computing With dedicated local government account teams and specialists across the country, we Helping organisations understand if, and how, they can take advantage understand both the challenges facing leadership teams within local government and the of cloud technologies. technology needed to overcome them. In recent years, Dell has undertaken an extensive strategic acquisition programme designed to help customers to: • Reduce CapEx through the commoditisation and standardisation of everything in their infrastructures. • Reduce OpEx by driving automation and manageability across not only Dell solutions but those of other vendors too. -

Dell Wyse Configuration Manager
Dell Wyse Configuration Manager Simply select the desired configuration, and WCM does With WCM, IT departments no longer need to create the rest, automatically, with no imaging or re-booting and deploy a new image each and every time a change required, across the entire installation. WCM supports SMB is required to the device settings. IT departments can Everything you need from a to Enterprise environments, stationary or mobile thin define a single‘ Gold’ image for the entire organization clients, in or out of the office, and supports Microsoft to dramatically simplify and reduce costs of managing desktop, without the headaches Active Directory, when present. and maintaining Dell Wyse thin clients with Windows Embedded Standard. Dell Wyse Configuration Manager (WCM) Simple and flexible auto-configuration provides an innovative self-configuring client WCM 1.2 has been expanded to add support for WCM greatly simplifies and automates the configuration technology for Windows Embedded virtual desktop ‘appliance mode,’ wherein any Windows Embedded thin and management of Windows Embedded devices. With environments in a stand-alone application and client can be configured to function as a single-purpose WCM, deploying a new Windows Embedded thin client is service. IT administrators can specify global or user appliance and nothing else (e.g. as a read-only kiosk). as simple as taking it out of the box, plugging it into the configurations using a simple standalone GUI or New features in WCM 1.2 also include display configuration network, turning it on and, within less than 2 minutes the capture them from an already configured Dell Wyse settings for up to two displays, timeserver settings, Internet device is specifically configured for either general or Windows Embedded Standard device, and deploy Explorer proxy settings, and greater security and credential user-specific settings. -
Offering-Specific Terms
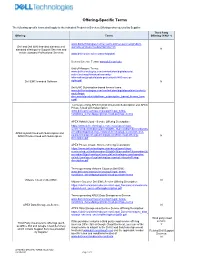
Offering-Specific Terms The following specific terms shall apply to the indicated Product or Services Offerings when quoted by Supplier: Third Party Offering Terms Offering (Y/N)? *) www.delltechnologies.com/en-us/customer-services/product- Dell and Dell EMC branded warranty and warranty-and-service-descriptions.htm N standard offerings for Support Services and certain standard Professional Services www.dell.com/servicecontracts/global General License Terms: www.dell.com/eula Unit of Measure Terms: www.delltechnologies.com/content/dam/digitalassets/ active/en/unauth/manual-warranty- informations/products/data-protection/h2483-sw-use- Dell EMC branded Software rights.pdf N Dell EMC Subscription-based license terms: www.delltechnologies.com/content/dam/digitalassets/active/en/u nauth/legal- documents/products/dellemc_subscription_based_license_term s.pdf Terms governing APEX Hybrid Cloud with Subscription and APEX Private Cloud with Subscription: www.dell.com/learn/us/en/uscorp1/legal_terms- conditions_dellwebpage/global-cloud-purchase-terms APEX Hybrid Cloud - Service Offering Description: https://www.delltechnologies.com/en-us/apex/cloud- services/index.htm#accordion0&tab0=3&accordion1&accordion2& accordion3&pdf-overlay=//www.delltechnologies.com/asset/en- APEX Hybrid Cloud with Subscription and us/solutions/apex/legal-pricing/apex-hybrid-cloud-offering- APEX Private Cloud with Subscription N description.pdf APEX Private Cloud - Service Offering Description: https://www.delltechnologies.com/en-us/apex/cloud- services/index.htm#accordion0&tab0=3&accordion1&accordion2& -

Wyse Cloud Client Device Management
Wyse cloud client device management Learn more. Here: Wyse device management products Meet the Wyse device management product portfolio from Dell The Wyse portfolio of intelligent management software provides the broadest range of client management capabilities. Designed to free IT professionals from unnecessary support tasks, Wyse device management products are invisible, self-configuring, automated client management tools for meeting day-to-day configuration needs, and scalable enterprise-grade management software for hands-on control when and where you need it most. Take a tour or select your preference below: Microsoft Wyse Device Wyse Configuration Wyse Cloud Windows Embedded Manager Manager Client Manager Device Manager Wyse management software from Dell Intro Dell.com Introducing Wyse Device Manager Minimize your desktop support costs. At a glance features: Maximize desktop productivity Security • HTTPS based imaging / updates Wyse Device Manager (WDM) manages all Wyse thin and zero clients from Dell, and • Fully encrypted network traffic addresses key management requirements for deploying powerful thin clients. With its • Delegated admin access (MS AD) support. centralized management and administration, WDM helps IT departments deliver more effective remote cloud client support while minimizing end user downtime. Security No-hassle deployment is assured with HTTPS based imaging, updates and downloads. • Complete device imaging / patching / updates • Bandwidth throttling for efficiency / reliability WDM delivers organization-wide benefits: • Software updates and add-ons. Device administration and monitoring Operations Service and support • Device health status / reporting Centralized management. Easier, more effective remote support. • Remote shadowing / control Collect and organize asset information. Create custom scripts and packages. • Default device configuration. Administration End point device management Scalability Health status reports. -

Oem Terms of Sale General Terms 1. Definitions A. B. C. D. E
OEM TERMS OF SALE These OEM Terms of Sale, including all applicable terms referenced herein, (“Agreement” or “OTS”) only applies to you, if you are an OEM as defined below: “OEM” means you in your capacity as an original equipment manufacturer that is purchasing Standard Products (as defined below) from Supplier for an OEM project. In general, an OEM (a) combines Product with OEM’s proprietary hardware, software or other intellectual property, resulting in a specialized system or solution with industry or task-specific functionality and (b) resells the Standard Product as part of, in conjunction with, or for use with the OEM Product under OEM Customer’s own brand. This Agreement governs your (“you” or “OEM”) purchase and use of products and services ordered by you directly from one of the entities below (“Supplier”) (Supplier and OEM also referred to as “Party”), as applicable for your country of purchase (collectively “Offerings”): Austria: Dell GesmbH or EMC ComputerSystems Austria GmbH, Wienerbergstrasse 41-43, EuroPlaza, 4. Stock, 1120 Vienna, or Belgium: Dell NV, Dell N.V., Koningin Astridlaan 164, 1780 Wemmel, or Denmark: Dell A/S, Arne Jacobsens Allé 17, 2300 Copenhagen, or Finland: Oy Dell Ab, Keilaranta 13 A, Espoo 02150, or France: EMC Computer Systems France SAS, River Ouest, 80 Quai Voltaire, 95870 Bezons, or Dell SA, 1 Rond-Point Benjamin Franklin, 34000 Montpellier, or Germany: Dell GmbH, Unterschweinstiege 10, Frankfurt am Main, 60549, or Ireland: EMC Information Systems International, Ovens, Co Cork, or Dell Products, 70 Sir John Rogerson’s Quay, Dublin 2, or Italy: EMC Computer Systems Italia S.p.A. -

It's That Time
December 2014 / January 2015 | Vol. 8 No. 1 VirtualizationReview.com 2015 READERS CHOICE AWARDS WINNER IT’S THAT TIME OFYEAR! Eggnog, presents and the products you like best. PLUS > VIRTUAL PREDICTIONS > DELL’S VDI STRATEGY > UNTANGLING VMWARE DRS VISIT VIRTUALIZATIONREVIEW.COM contents The objective is helping organizations accomplish their 6 goals; not to push any specifi c type of technology. By Dan Kusnetzky 2015Readers Choice Awards “Chromebook desktop ÌÌÌÌ Winner ÌÌÌÌ access looks especially promising, especially in the education market.” Garret Grajek, dinCloud 18 6 December 2014 / January 2015 | VIRTUALIZATION REVIEW | VOL. 7, NO. 2 FEATURES 11 Best Cloud Storage Product 15 Best Network 4 The 2015 Reader’s Choice 12 Best Cloud Security Product Virtualization Product Awards and Buyer’s Guide 12 Best Cloud Software Product 16 Best Virtualization Security Product You, the readers, have spoken. 13 Best Business Continuity Product Here are the virtualization and Best Converged 14 Best Virtualization 17 cloud computing products that Automation Product Infrastructure Product rock your world. Best Virtualization Training 15 Best Storage 17 6 Best Application Virtualization Product Virtualization Product 6 Best Server Virtualization Product Best Desktop Virtualization/ 7 18 2015 Virtualization Predictions COLUMNS Virtual Desktop Infrastructure Product What can you expect to happen 2 Editor’s Note: KEITH WARD in the virtualization and cloud 3 Expectations for 2015 8 Best Mobile Virtualization/ BYOD Product industries in the coming year? -

Auction List As of 09-18-2020 Final
HIDALGO CO. PURCHASING DEPT. AUCTION LIST (EXHIBIT A) OCTOBER 30, 2020 Lot Asset No. Description Serial No. Fund TF No. No. 1 19-0448 MONITOR W/STAND CN0C0646-46633-53V-113L 1100 2019-188 1 2 19-0449 MONITOR W/STAND CN-0C0646-46633-53V-16WL 1100 2019-188 1 3 19-0312 DELL MONITOR W/STAND CN-09TVYF-72872-19K-AJC1 1100 2019-085 1 4 19-0313 DELL MONITOR W/STAND CN-0YG613-71618-688-AF7C 1100 2019-085 1 5 19-0314 DELL MONITOR W/STAND CN-DHC317-71618-578-A331 1100 2019-085 1 6 19-0319 DELL MONITOR W/STAND CN-09TVYF-72872-19K-AJRI 1100 2019-085 1 7 19-0320 DELL MONITOR W/STAND CN-09TVYF-72872-AK-AJ9I 1100 2019-085 1 8 19-0321 DELL MONITOR W/STAND CN-0PN59G-74261-190-1TLU 1100 2019-085 1 9 19-0315 DELL MONITOR W/STAND CN-09TVYF-72872-19K-AJEI 1100 2019-085 1 10 19-0316 DELL MONITOR W/STAND CN-0PN59G-74261-190-OELU 1100 2019-085 1 11 19-0317 DELL MONITOR W/STAND CN-09TVYF-72872-19K-ALUI 1100 2019-085 1 12 19-0318 DELL MONITOR W/STAND CN-OPN59G-74261-190-ITFU 1100 2019-085 1 13 51979 DELL 4210X DLP PROJECTOR 539X4M1 1100 2019-209 1 14 52025 EPSON 83V & DC06 DOC CAMERA MSFF033190L 1100 2019-209 1 15 19-0282 DELL MONITOR CN0M1609-46633-43V0-3U4S 1100 2019-166 1 16 19-0306 DELL MONITOR W/STAND CN-0RY97974261-7CH-0MRL 1100 2019-087 1 17 19-0305 DELL MONITOR W/STAND CN-0M1609-46633-414-1W1S 1100 2019-087 1 18 20-0015 HP MONITOR CN43260KDT 1100 2019-263 2 19 20-0017 HP MONITOR STAND 130415L0103357 1100 2019-261 2 20 20-0018 HP MONITOR (AWARD) C-0348-05 CNN4491DJZ 1100 2019-264 2 21 20-0019 LG MONITOR 212NDRFFE334 1100 2019-264 2 22 20-0020 HP MONITOR 3CQ140NNJW 1100 2019-264 2 23 20-0021 HP MONITOR 3CQ1250M20 1100 2019-264 2 Page 1 of 89 HIDALGO CO. -

Wyse 3040 Thin Client Spec Sheet
WYSE 3040 Security and performance in a compact design PERFORMANCE TO POWER SECURITY BUILT-IN YOUR WORKDAY End to end security starts at the endpoint. Get the most 3 Featuring Intel® quad core processors, this power-efficient secure thin client with Dell-exclusive Wyse ThinOS . thin client+ delivers business class performance, native support for dual-display setup and robust connectivity for confident connectivity and collaboration. DEPLOY WITH EASE EFFICIENT PRODUCTIVITY Deploy in about a minute1 and autoconfigure in less than 102. The smallest and lightest thin client from Dell+ is ideal for With unified end-to-end deployment and management space-constrained environments. Several custom designed from Wyse Management Suite manage from the cloud mounting solutions help maximize work space set up and or the datacenter. deliver an all-in-one experience. Accelerate your cloud strategy with Wyse cloud clients designed to enhance your virtual workspaces with ultimate security and intelligent unified management. Learn More at Delltechnologies.com/Wyse Recommended Accessories WYSE 3040 AT-THE-DESK / REMOTE DELL 24 MONITOR P2419H WITH DELL P-SERIES MONITOR MOUNT DELL DUAL MONITOR STAND | MDS19 Completely open your workspace with a Optimize your dual monitor setup to improve behind-the-monitor mounting solution. productivity and reduce desktop clutter. WYSE 3040 WALL MOUNT AND DELL PRO STEREO HEADSET | UC350 E-SERIES MONITORS Hear every word clearly on your next Allows the Wyse 3040 to be mounted to select call with the Dell Pro Stereo Headset, Dell E-Series displays. optimized to provide in-person call quality and certified for Microsoft® Skype® for Business. DELL WIRELESS KEYBOARD DELL SMART CARD KEYBOARD | KB813 AND MOUSE | KM636 Access secured endpoints or networks With a compact mouse and full-sized directly from your keyboard with an keyboard for accurate typing, this integrated smart card reader for easy keyboard mouse combo offers the authentication at your fingertips. -

Get the Highest Level of Performance and Security out of Your Workstation Level Applications with Dell's Cloud Client Computing Portfolio
Get the highest level of performance and security out of your workstation level applications with Dell's cloud client computing portfolio Marek Bartyzel Product Specialist Dell Cloud Client-computing [email protected] The way work is being done is fundamentally changing The workforce is evolving Work happens anytime, anywhere Users demand access to data from a variety of endpoints Desktops and Laptops and Tablets & Thin and Tower Mobile Smart Phones Mobile Workstations Workstations Clients 2 Traditional computing limits user collaboration 3 Security and data integrity is challenged as data sets grow 4 How do you enable access to data and apps without compromising on security? 5 Centralizing and virtualizing data and apps makes sense Data is safely secured in the data center, not at endpoints Enable as-needed access to data and apps from a variety of endpoints Manage user workspaces and data centrally, freeing up IT resources Gain business agility by scaling up or down as business demands 6 Enable your workforce to work and collaborate from anywhere 7 Is it possible to do this without compromising the user experience? 8 Graphics and Compression capabilities have evolved More efficient than ever Virtualized to deliver graphics Graphics resources to users 22% reduction Compression Better user experiences Protocols as a result of lower latency and higher fps 9 How Dell makes it possible Market leading Proven expertise in workstation and desktop virtualization, and deep technology partnerships with leading technology providers Leverages -

Enhance Your Virtual Workspaces with Wyse
WYSE THIN CLIENTS Enhance your virtual workspaces with Wyse INTRODUCING THE WYSE FAMILY Accelerate your cloud strategy with Wyse cloud clients and software designed to enhance your virtual workspaces with ultimate security and intelligent unified management. The new generation of Wyse cloud clients powers your organization with a more efficient and effective digital experience. Learn More at DellTechnologies.com/Wyse Why Choose Wyse BUILT TO FIT YOUR CLOUD CLIENT COMPUTING ENVIRONMENT Experience smarter productivity with a portfolio optimized to access traditional VDI, cloud-hosted virtual desktops and apps and cloud services with unprecedented simplicity and flexibility. Capable to meet the needs from collaborative knowledge workers up to graphics-intensive power users, SMARTER, FASTER Wyse thin clients deliver a high-quality computing experience to take fully advantage of the growing number of apps and content whether they are on- END-USER premises or on the cloud. Strong security features, high-speed connectivity EXPERIENCES to attach a broad range of peripherals and support for multiple displays and most popular collaboration tools deliver a productive user experience day after day. Ideal for space-constrained environments, Wyse cloud clients adapt to the way people work with versatile form factors and a large choice of mounting options. Certified with leading VDI brokers, including VMware, Citrix & Microsoft, Wyse thin clients and software are optimized to deliver a faster time- to-value and fully leverage the incredible flexibility and scalability of your cloud computing environment. Installation takes about one minute per endpoint1 with a simple out-of-the-box automatic setup, configuration and INTELLIGENT, management and Wyse Easy Setup provides a shorter time to productivity UNIFIED for Wyse ThinLinux and Windows 10 IoT Enterprise. -

Dell Wyse Management Suite Version 1.4 Administrator's Guide
Dell Wyse Management Suite Version 1.4 Administrator’s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2019 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 2019 - 04 Rev. A00 Contents 1 Introduction to Wyse Management Suite........................................................................................................9 Editions................................................................................................................................................................................9 What is new in this release?............................................................................................................................................. 9 2 Getting started with Wyse Management Suite..............................................................................................11 Logging in to Wyse Management Suite on public cloud...............................................................................................11 Changing your password........................................................................................................................................... -

Dell Wyse T Class IA Thin Clients Datasheet
Wyse Dell Wyse T class The new standard for powerful, economical thin clients. Dell Wyse T class: All you need to know. Here: Introducing the Dell Wyse T class The new standard for entry level. Great to use. Great to manage Dell Wyse T class thin clients deliver an exceptional Citrix, Microsoft, and VMware VDI user experience with unparalleled security, ease of use, and ease of management – on a budget. Two products are available: the Dell Wyse T10 with Dell Wyse ThinOS, and the Dell Wyse T50 with Dell Wyse enhanced Ubuntu™ Linux. Users will find them easy to live with too; enjoying vibrant multimedia and Flash that plays in VDI, the power of their Marvell ARMADA™ PXA 510 v7 1.0 GHz System-on-Chip (SoC) processors and the hands-off support provided by Dell Wyse Automated Management capability. Dell Wyse T10 Dell Wyse T50 Features ThinOS for fast performance Features a fast and simple user interface, with instant-on start up, easy centralized a Chromium web browser and the strong configuration, total security and an exceptional security of Dell Wyse enhanced Linux, entry-level client for Citrix XenDesktop, as well as browser-based connectivity VMware View, and Microsoft Remote to SaaS-based apps, and local Desktop Services (RDS). execution via a VPN. Start Models Features Technical Contact Print dellwyse.com Features Dell Wyse T class The best user experience. On a budget. Dell Wyse T class thin clients are compact, affordable and flexible entry level desktop devices. They deliver the best Web, Citrix, Microsoft and VMware VDI user experience and performance to IT executives needing to equip their task workers with an enterprise-standard client on a budget.