The Windows Metafile (WMF) Vulnerability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
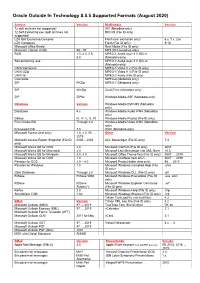
Supported Formats (August 2020)
Oracle Outside In Technology 8.5.5 Supported Formats (August 2020) Archive Version Multimedia Version 7z split archives not supported) AVI (Metadata only) 7z Self Extracting exe (split archives not DICOM (File ID only) supported) LZA Self Extracting Compres Flash (text extraction only) 6.x, 7.x, Lite LZH Compress Flash (File ID only) 9,10 Microsoft Office Binder Real Media (File ID only) Microsoft Cabinet (CAB) 95 – 97 MP3 (ID3 metadata only) RAR 1.5, 2.0, 2.9, MPEG-1 Audio layer 3 V ID3 v1 5.0 (Metadata only) Self-extracting .exe MPEG-1 Audio layer 3 V ID3 v2 (Metadata only) UNIX Compress MPEG-1 Video V 2 (File ID only) UNIX GZip MPEG-1 Video V 3 (File ID only) UNIX tar MPEG-2 Audio (File ID only) Uuencode MPEG-4 (Metadata only) ZIP PKZip MPEG-7 (Metadata only) ZIP WinZip QuickTime (Metadata only) ZIP ZIP64 Windows Media ASF (Metadata only) Database Version Windows Media DVR-MS (Metadata only) DataEase 4.x Windows Media Audio WMA (Metadata only) DBase III, IV, V, X, X1 Windows Media Playlist (File ID only) First Choice DB Through 3.0 Windows Media Video WMV (Metadata only) Framework DB 3.0 WAV (Metadata only) Microsoft Access (text only) 1.0, 2.0, 95 … Other Version 2019 Microsoft Access Report Snapshot (File ID 2000 – 2003 AOL Messenger (File ID only) 7.3 only) Microsoft Works DB for DOS 2.0 Microsoft InfoPath (File ID only) 2007 Microsoft Works DB for Macintosh 2.0 Microsoft Live Messenger (via XML filter) 10.0 Microsoft Works DB for Windows 3.0, 4.0 Microsoft Office Theme files (File ID only) 2007 … 2019 Microsoft Works DB for DOS -

Encapsulated Postscript File Format Specification
® Encapsulated PostScript File Format Specification ®® Adobe Developer Support Version 3.0 1 May 1992 Adobe Systems Incorporated Adobe Developer Technologies 345 Park Avenue San Jose, CA 95110 http://partners.adobe.com/ PN LPS5002 Copyright 1985–1988, 1990, 1992 by Adobe Systems Incorporated. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of the publisher. Any software referred to herein is furnished under license and may only be used or copied in accordance with the terms of such license. PostScript is a registered trademark of Adobe Systems Incorporated. All instances of the name PostScript in the text are references to the PostScript language as defined by Adobe Systems Incorpo- rated unless otherwise stated. The name PostScript also is used as a product trademark for Adobe Sys- tems’ implementation of the PostScript language interpreter. Any references to a “PostScript printer,” a “PostScript file,” or a “PostScript driver” refer to printers, files, and driver programs (respectively) which are written in or support the PostScript language. The sentences in this book that use “PostScript language” as an adjective phrase are so constructed to rein- force that the name refers to the standard language definition as set forth by Adobe Systems Incorpo- rated. PostScript, the PostScript logo, Display PostScript, Adobe, the Adobe logo, Adobe Illustrator, Tran- Script, Carta, and Sonata are trademarks of Adobe Systems Incorporated registered in the U.S.A. and other countries. Adobe Garamond and Lithos are trademarks of Adobe Systems Incorporated. -

Gaussplot 8.0.Pdf
GAUSSplotTM Professional Graphics Aptech Systems, Inc. — Mathematical and Statistical System Information in this document is subject to change without notice and does not represent a commitment on the part of Aptech Systems, Inc. The software described in this document is furnished under a license agreement or nondisclosure agreement. The software may be used or copied only in accordance with the terms of the agreement. The purchaser may make one copy of the software for backup purposes. No part of this manual may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, for any purpose other than the purchaser’s personal use without the written permission of Aptech Systems, Inc. c Copyright 2005-2006 by Aptech Systems, Inc., Maple Valley, WA. All Rights Reserved. ENCSA Hierarchical Data Format (HDF) Software Library and Utilities Copyright (C) 1988-1998 The Board of Trustees of the University of Illinois. All rights reserved. Contributors include National Center for Supercomputing Applications (NCSA) at the University of Illinois, Fortner Software (Windows and Mac), Unidata Program Center (netCDF), The Independent JPEG Group (JPEG), Jean-loup Gailly and Mark Adler (gzip). Bmptopnm, Netpbm Copyright (C) 1992 David W. Sanderson. Dlcompat Copyright (C) 2002 Jorge Acereda, additions and modifications by Peter O’Gorman. Ppmtopict Copyright (C) 1990 Ken Yap. GAUSSplot, GAUSS and GAUSS Engine are trademarks of Aptech Systems, Inc. Tecplot RS, Tecplot, Preplot, Framer and Amtec are registered trademarks or trade- marks of Amtec Engineering, Inc. Encapsulated PostScript, FrameMaker, PageMaker, PostScript, Premier–Adobe Sys- tems, Incorporated. Ghostscript–Aladdin Enterprises. Linotronic, Helvetica, Times– Allied Corporation. -

Data Format Guide
Data Format Guide Tecplot, Inc. Bellevue, WA 2006 COPYRIGHT NOTICE Tecplot 360TMData Format Guide is for use with Tecplot 360TM 2006. Copyright © 1988-2006 Tecplot, Inc. All rights reserved worldwide. Except for personal use, this manual may not be reproduced, trans- mitted, transcribed, stored in a retrieval system, or translated in any form, in whole or in part, without the express written permission of Tecplot, Inc., 3535 Factoria Blvd., Ste 550, Bellevue, Washington, 98006, U.S.A. The software discussed in this documentation and the documentation itself are furnished under license for utilization and duplication only according to the license terms. The copyright for the software is held by Tecplot, Inc. Documentation is provided for information only. It is subject to change without notice. It should not be interpreted as a commitment by Tecplot, Inc. Tecplot, Inc. assumes no liabil- ity or responsibility for documentation errors or inaccuracies. Tecplot, Inc PO Box 52708 Bellevue, WA 98015-2708 U.S.A. Tel: 1.800.763.7005 (within the U.S. or Canada), 00 1 (425)653-1200 (internationally) email: [email protected], [email protected] Questions, comments or concerns regarding this documentation: [email protected] For more information, visit http://www.tecplot.com THIRD PARTY SOFTWARE COPYRIGHT NOTICES ENCSA Hierarchical Data Format (HDF) Software Library and Utilities © 1988-1998 The Board of Trustees of the University of Illi- nois. All rights reserved. Contributors include National Center for Supercomputing Applications (NCSA) at the University of Illinois, Fortner Software (Windows and Mac), Unidata Program Center (netCDF), The Independent JPEG Group (JPEG), Jean-loup Gailly and Mark Adler (gzip). -

FILE FORMATS Darry D
WordPerfect FILE FORMATS Darry D In WordPerfect, when you select File > Open, you are taken to “My Documents.” However, that does not mean that you can open all the files that are stored there. Here are the programs that can open a file, based upon its file extension. A file extension is a string of characters beginning with a period and followed by one to three letters; the optional second part of a PC computer filename; “most applications provide extensions for the files they create”; for example, WordPerfect uses the file extension “wpd”. o .cgm — CGM (Computer Graphics Metafile) was a once-standard for- mat for interchanging graphics images. CGM stores images primarily in vector graphics, but also provides a raster format. Earlier GDM and VDM formats have been merged into CGM. There are many non-standard varieties of CGM in use. Usually found in the “My Pictures” folder of “My Documents” or some other graphics folder (such as “Art”), it can be inserted into WordPerfect 9 using Insert > Graphics > From File (from the MenuBar). o .cvs — comma-delimited file (a database with items separated by commas); this one can be opened only by importing it into the Outlook Express Address Book. o .doc — Created with MS Word; WordPerfect can open it. o .eml — Email created by Outlook Express or Outlook either of which can open it. Http://DarryD.com (5 November 2020) Page 1 of 4 WORDPERFECT 5 NOVEMBER 2020 o .htm —. It is the file extension of HTML, created by programs like Microsoft FrontPage and others, including WordPerfect. -

Windows Metafiles
Windows Metafiles An Analysis of the EMF Attack Surface & Recent Vulnerabilities Mateusz “j00ru” Jurczyk Ruxcon, Melbourne 2016 PS> whoami • Project Zero @ Google • Low-level security researcher with interest in all sorts of vulnerability research and software exploitation • http://j00ru.vexillium.org/ • @j00ru Agenda • Windows Metafile primer, GDI design, attack vectors. • Hacking: • Internet Explorer (GDI) • Windows Kernel (ATMFD.DLL) • Microsoft Office (GDI+) • VMware virtualization (Print Spooling) • Final thoughts. Windows GDI & Metafile primer Windows GDI • GDI stands for Graphics Device Interface. • Enables user-mode applications to use graphics and formatted text on video displays and printers. • Major part of the system API (nearly 300 documented functions). • Present in the OS since the very beginning (Windows 1.0 released in 1985). • One of the oldest subsystems, with most of its original code still running 31 years later. • Concidentally (?) also one of the most buggy components. How to draw 1. Grab a handle to a Device Context (HDC). • Identifies a persistent container of various graphical settings (pens, brushes, palettes etc.). • Can be used to draw to a screen (most typically), a printer, or a metafile. • Most trivial example: HDC hdc = GetDC(NULL); (obtains a HDC for the entire screen) How to draw 2. Use a drawing function. Ellipse(hdc, 100, 100, 500, 300); RoundRect(hdc, 100, 100, 500, 500, 100, 100); Windows GDI – simplified architecture NT OS Kernel Display Drivers Printer Drivers Font Drivers Kernel-mode GDI (win32k.sys) ring-0 ring-3 User-mode GDI (gdi32.dll) GDI+ (gdiplus.dll) app1.exe app2.exe app3.exe app4.exe User to kernel API mappings Most user-mode GDI functions have their direct counterparts in the kernel: GDI32.DLL win32k.sys AbortDoc NtGdiAbortDoc AbortPath NtGdiAbortPath AddFontMemResourceEx NtGdiAddFontMemResourceEx AddFontResourceW NtGdiAddFontResourceW AlphaBlend NtGdiAlphaBlend .. -

About Graphics/Digital Images
About Graphics/Digital Images Digital images are found in lots of file formats (types) that are used for various reasons. I liken the file formats to flavors of ice-cream, which you might or might not choose to consume on any given day. One day chocolate is more important than mint; another day you might use vanilla, and on another day you might decide to combine more than one flavor in the same bowl. Likewise, you might choose one type of graphic file for a particular project, but it might be completely inappropriate for another project. What works well for display purposes (keeping it on the computer, or for publication to the internet) might not print well. Something that prints well might be too big a file to post to the internet, or may make your program run too slowly. Also, some authoring programs (like Boardmaker or Classroom Suite) might be written to only understand certain types of image files. Some file types are more common than others, and are more likely to be recognized by the “parent” program (the one you use to display, edit or print your image). Whatever type you pick ultimately depends on how you plan to use the image. The more technical definitions provided below are taken from the glossary found at http://www.photoshopelementsuser.com/glossary.php?letter=B The additional comments I have added, and hopefully let you know why you would care about any of this, anyway. The two biggest types of images I describe here fall loosely into two categories: vector images and bitmap images. -

EMF2LEO Documentation
EMF2LEO Useful Documentation Contents 2. General Information 2 3. Several functionalities 7 4. Examples 8 5. Question and Error repo rting 18 ADOxx.org Seite 1 2. General Information EMF2LEO is a command-line tool used to convert vector graphics into the Leo-scripting- l anguage. Vector graphics that should be converted have to be stored in the Windows Enhanced Metafile format (EMF). Every modern graphic program is able to save graphics in this format. Nevertheless, vector graphic programs like Corel Draw 9 are more likely to produce good results than e.g. Paint Shop Pro. After all, the emf2leo converter facilitates the work of the ADOxx® customising staff in the way, that simple figures can be drawn outside of the ADOxx® Administration Toolkit and then be easily converted into the Leo-scripting-language. You should be aware that there will still be some work to do after having converted the Enhanced Metafile into Leo. EMF2LEO’s output is a Leo-file whose content must be pasted into in the GraphRep of a class attribute of a ADOxx® standard library. Then the converted graphic elements have to be adapted to the customers’ expectations. Due to the different ways of storing an image in an Enhanced Metafile the usability of the Leo-script can vary a lot. In some cases, very good results are obtained. In other cases, the results only represent a better starting base for the customising staff. In the following passages, it will be shown how to obtain the best possible results while working with EMF2LEO. At first, the structure of an Enhanced Metafile is discussed in detail. -

Vector Graphics Vector Graphics • Graphics That Are Based on Mathematical Formulas That Define Lines, Shapes, and Curves
Vector Graphics Vector Graphics • Graphics that are based on mathematical formulas that define lines, shapes, and curves. • Are comprised of paths connected by anchor points. • Can be 2D or 3D. • Edited in draw programs. Examples Original Image Resized Image Shapes that make up the image. Uses of Vector Graphics • Graphics that will be scaled (or resized) • Architectural drawings, CAD programs, flow charts. • Logos that will be scaled (resized) with loss of quality. • Illustrations and clip art. • Graphics on websites. • Small file size allows for quick load times. • Fonts and specialized text effects Advantages of Vectors • Scalable – able to change size easily • Resolution Independent - Regardless of how much the image is enlarged or reduced, the image definition and quality remain the same. • Editability - since each vector is made up of separate and distinct objects, each can be edited independently at any time. • Small File Sizes - easily transferred over the Internet. Disadvantages of Vectors • Lower color quality than raster images. • They do not support as many colors. • Not good for photographic images. • Limited in the type of effects that can be applied. • Can be time consuming to create. Common Vector File Formats • AI – Adobe Illustrator • Native file format for Adobe Illustrator. • Industry standard used by developers of vector graphics. • Used to create, save, and archive original artwork. Common Vector File Formats • EPS – Encapsulated Postscript • Developed by Adobe but supported by most programs. • Graphics developers generally save a copy of the AI file in EPS format because it can be opened by computers running different operating systems. • Most common interchange format for the print industry due to its portability. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

CS8092-Computer Graphics and Multimedia Notes
UNIT I ILLUMINATION AND COLOUR MODELS Light sources – basic illumination models – halftone patterns and dithering techniques; Properties of light – Standard primaries and chromaticity diagram; Intuitive colour concepts – RGB colour model – YIQ colour model – CMY colour model – HSV colour model – HLS colour model; Colour selection. Color Models Color Model is a method for explaining the properties or behavior of color within some particular context. No single color model can explain all aspects of color, so we make use of different models to help describe the different perceived characteristics of color. Properties of Light Light is a narrow frequency band within the electromagnetic system. Other frequency bands within this spectrum are called radio waves, micro waves, infrared waves and x-rays. The below fig shows the frequency ranges for some of the electromagnetic bands. Each frequency value within the visible band corresponds to a distinct color. 4 At the low frequency end is a red color (4.3*10 Hz) and the highest frequency is a violet color 14 (7.5 *10 Hz) Spectral colors range from the reds through orange and yellow at the low frequency end to greens, blues and violet at the high end. Since light is an electro magnetic wave, the various colors are described in terms of either the frequency for the wave length λ of the wave. The wave length ad frequency of the monochromatic wave are inversely proportional to each other, with the proportionality constants as the speed of light C where C = λ f A light source such as the sun or a light bulb emits all frequencies within the visible range to produce white light. -

Vector Graphic Images • Spline Curves • More About Bézier Curves • Vector Graphic Output Options • Metafile Graphic Images • Metafile Graphic Output Options
Understanding Vector Graphics Contents • Vector Graphic Images • Spline Curves • More About Bézier Curves • Vector Graphic Output Options • Metafile Graphic Images • Metafile Graphic Output Options Vector Graphic Images • Composed of mathematically defined lines and curves called vectors and are device independent, which means they don’t have a fixed resolution. • Figures can be moved, resized or rotated as an independent object as the figure definition is mathematically retained. • Best for type and other shapes that require crisp, clear boundaries. • Typically produced by illustration/drawing/CAD software such as Adobe Illustrator, Adobe Flash, Corel DRAW, AutoCAD, Turbocad etc. or by scanning artwork etc and tracing or vectorising. Return to contents Vector Graphic Images Vector Graphic Example Spline Curves • Spline: A line defined by control points. • Types: • B-Spline: Control points with equal weight that usually are away from curve. • Bézier: Control points always on the curve. Handles on control points for modifying curve. • NURBS (Non Uniform Rational B-Spline): Control points away from curve with weights to control curve. Spline Curves Spline Curves More About Bézier Curves • Developed by Pierre Bézier (a Renault automotive engineer) in 1960s as way to mathematically describe smooth contours on a car surface. • Historically complex lines either required arduous calculations (in mathematical drawings), or were just drawn by hand (in visual arts and design). • In the 20th century this deficiency proved to be a real obstacle, especially in industrial design, where complex curved lines and surfaces must be precisely defined so as to be uniformly reproduced in metal or plastic. More About Bézier Curves • Bezier curves (after their inventor), are now familiar to any user of a vector drawing program.