The MUX (Multiplexer) Protocol Wittawat Tantisiriroj, J
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
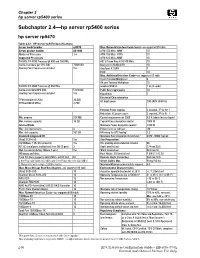
Subchapter 2.4–Hp Server Rp5400 Series
Chapter 2 hp server rp5400 series Subchapter 2.4—hp server rp5400 series hp server rp5470 Table 2.4.1 HP Server rp5470 Specifications Server model number rp5470 Max. Network Interface Cards (cont.)–see supported I/O table Server product number A6144B ATM 155 Mb/s–MMF 10 Number of Processors 1-4 ATM 155 Mb/s–UTP5 10 Supported Processors ATM 622 Mb/s–MMF 10 PA-RISC PA-8700 Processor @ 650 and 750 MHz 802.5 Token Ring 4/16/100 Mb/s 10 Cache–Instr/data per CPU (KB) 750/1500 Dual port X.25/SDLC/FR 10 Floating Point Coprocessor included Yes Quad port X.25/FR 7 FDDI 10 Max. Additional Interface Cards–see supported I/O table 8 port Terminal Multiplexer 4 64 port Terminal Multiplexer 10 PA-RISC PA-8600 Processor @ 550 MHz Graphics/USB kit 1 kit (2 cards) Cache–Instr/data/CPU (KB) 512/1024 Public Key Cryptography 10 Floating Point Coprocessor included Yes HyperFabric 7 Electrical Characteristics TPM estimate (4 CPUs) 34,500 AC Input power 100-240V 50/60 Hz SPECweb99 (4 CPUs) 3,750 Hotswap Power supplies 2 included, 3rd for N+1 Redundant AC power inputs 2 required, 3rd for N+1 Min. memory 256 MB Current requirements at 200V 6.5 A (shared across inputs) Max. memory capacity 16 GB Typical Power dissipation (watts) 1008 W Internal Disks Maximum Power dissipation (watts) 1 1360 W Max. disk mechanisms 4 Power factor at full load .98 Max. disk capacity 292 GB kW rating for UPS loading1 1.3 Standard Integrated I/O Maximum Heat dissipation (BTUs/hour) 1 4380 - (3000 typical) Ultra2 SCSI–LVD Yes Site Preparation 10/100Base-T (RJ-45 connector) Yes Site planning and installation included No RS-232 serial ports (multiplexed from DB-25 port) 3 Depth (mm/inches) 774 mm/30.5 Web Console (including 10Base-T port) Yes Width (mm/inches) 482 mm/19 I/O buses and slots Rack Height (EIA/mm/inches) 7 EIA/311/12.25 Total PCI Slots (supports 66/33 MHz×64/32 bits) 10 Deskside Height (mm/inches) 368 mm/14.5 2 Hot-Plug Twin-Turbo (500 MB/s) and 6 Hot-Plug Turbo slots (250 MB/s) Weight (kg/lbs) Max. -

Analysis of GPGPU Programs for Data-Race and Barrier Divergence
Analysis of GPGPU Programs for Data-race and Barrier Divergence Santonu Sarkar1, Prateek Kandelwal2, Soumyadip Bandyopadhyay3 and Holger Giese3 1ABB Corporate Research, India 2MathWorks, India 3Hasso Plattner Institute fur¨ Digital Engineering gGmbH, Germany Keywords: Verification, SMT Solver, CUDA, GPGPU, Data Races, Barrier Divergence. Abstract: Todays business and scientific applications have a high computing demand due to the increasing data size and the demand for responsiveness. Many such applications have a high degree of parallelism and GPGPUs emerge as a fit candidate for the demand. GPGPUs can offer an extremely high degree of data parallelism owing to its architecture that has many computing cores. However, unless the programs written to exploit the architecture are correct, the potential gain in performance cannot be achieved. In this paper, we focus on the two important properties of the programs written for GPGPUs, namely i) the data-race conditions and ii) the barrier divergence. We present a technique to identify the existence of these properties in a CUDA program using a static property verification method. The proposed approach can be utilized in tandem with normal application development process to help the programmer to remove the bugs that can have an impact on the performance and improve the safety of a CUDA program. 1 INTRODUCTION ans that the program will never end-up in an errone- ous state, or will never stop functioning in an arbitrary With the order of magnitude increase in computing manner, is a well-known and critical property that an demand in the business and scientific applications, de- operational system should exhibit (Lamport, 1977). -

Evolving GPU Machine Code
Journal of Machine Learning Research 16 (2015) 673-712 Submitted 11/12; Revised 7/14; Published 4/15 Evolving GPU Machine Code Cleomar Pereira da Silva [email protected] Department of Electrical Engineering Pontifical Catholic University of Rio de Janeiro (PUC-Rio) Rio de Janeiro, RJ 22451-900, Brazil Department of Education Development Federal Institute of Education, Science and Technology - Catarinense (IFC) Videira, SC 89560-000, Brazil Douglas Mota Dias [email protected] Department of Electrical Engineering Pontifical Catholic University of Rio de Janeiro (PUC-Rio) Rio de Janeiro, RJ 22451-900, Brazil Cristiana Bentes [email protected] Department of Systems Engineering State University of Rio de Janeiro (UERJ) Rio de Janeiro, RJ 20550-013, Brazil Marco Aur´elioCavalcanti Pacheco [email protected] Department of Electrical Engineering Pontifical Catholic University of Rio de Janeiro (PUC-Rio) Rio de Janeiro, RJ 22451-900, Brazil Leandro Fontoura Cupertino [email protected] Toulouse Institute of Computer Science Research (IRIT) University of Toulouse 118 Route de Narbonne F-31062 Toulouse Cedex 9, France Editor: Una-May O'Reilly Abstract Parallel Graphics Processing Unit (GPU) implementations of GP have appeared in the lit- erature using three main methodologies: (i) compilation, which generates the individuals in GPU code and requires compilation; (ii) pseudo-assembly, which generates the individuals in an intermediary assembly code and also requires compilation; and (iii) interpretation, which interprets the codes. This paper proposes a new methodology that uses the concepts of quantum computing and directly handles the GPU machine code instructions. Our methodology utilizes a probabilistic representation of an individual to improve the global search capability. -

Readingsample
Embedded Robotics Mobile Robot Design and Applications with Embedded Systems Bearbeitet von Thomas Bräunl Neuausgabe 2008. Taschenbuch. xiv, 546 S. Paperback ISBN 978 3 540 70533 8 Format (B x L): 17 x 24,4 cm Gewicht: 1940 g Weitere Fachgebiete > Technik > Elektronik > Robotik Zu Inhaltsverzeichnis schnell und portofrei erhältlich bei Die Online-Fachbuchhandlung beck-shop.de ist spezialisiert auf Fachbücher, insbesondere Recht, Steuern und Wirtschaft. Im Sortiment finden Sie alle Medien (Bücher, Zeitschriften, CDs, eBooks, etc.) aller Verlage. Ergänzt wird das Programm durch Services wie Neuerscheinungsdienst oder Zusammenstellungen von Büchern zu Sonderpreisen. Der Shop führt mehr als 8 Millionen Produkte. CENTRAL PROCESSING UNIT . he CPU (central processing unit) is the heart of every embedded system and every personal computer. It comprises the ALU (arithmetic logic unit), responsible for the number crunching, and the CU (control unit), responsible for instruction sequencing and branching. Modern microprocessors and microcontrollers provide on a single chip the CPU and a varying degree of additional components, such as counters, timing coprocessors, watchdogs, SRAM (static RAM), and Flash-ROM (electrically erasable ROM). Hardware can be described on several different levels, from low-level tran- sistor-level to high-level hardware description languages (HDLs). The so- called register-transfer level is somewhat in-between, describing CPU compo- nents and their interaction on a relatively high level. We will use this level in this chapter to introduce gradually more complex components, which we will then use to construct a complete CPU. With the simulation system Retro [Chansavat Bräunl 1999], [Bräunl 2000], we will be able to actually program, run, and test our CPUs. -

MT-088: Analog Switches and Multiplexers Basics
MT-088 TUTORIAL Analog Switches and Multiplexers Basics INTRODUCTION Solid-state analog switches and multiplexers have become an essential component in the design of electronic systems which require the ability to control and select a specified transmission path for an analog signal. These devices are used in a wide variety of applications including multi- channel data acquisition systems, process control, instrumentation, video systems, etc. Switches and multiplexers of the late 1960s were designed with discrete MOSFET devices and were manufactured in small PC boards or modules. With the development of CMOS processes (yielding good PMOS and NMOS transistors on the same substrate), switches and multiplexers rapidly gravitated to integrated circuit form in the mid-1970s, with product introductions such as the Analog Devices' popular AD7500-series (introduced in 1973). A dielectrically-isolated family of these parts introduced in 1976 allowed input overvoltages of ± 25 V (beyond the supply rails) and was insensitive to latch-up. These early CMOS switches and multiplexers were typically designed to handle signal levels up to ±10 V while operating on ±15-V supplies. In 1979, Analog Devices introduced the popular ADG200-series of switches and multiplexers, and in 1988 the ADG201-series was introduced which was fabricated on a proprietary linear-compatible CMOS process (LC2MOS). These devices allowed input signals to ±15 V when operating on ±15-V supplies. A large number of switches and multiplexers were introduced in the 1980s and 1990s, with the trend toward lower on-resistance, faster switching, lower supply voltages, lower cost, lower power, and smaller surface-mount packages. Today, analog switches and multiplexers are available in a wide variety of configurations, options, etc., to suit nearly all applications. -
Processor-103
US005634119A United States Patent 19 11 Patent Number: 5,634,119 Emma et al. 45 Date of Patent: May 27, 1997 54) COMPUTER PROCESSING UNIT 4,691.277 9/1987 Kronstadt et al. ................. 395/421.03 EMPLOYING ASEPARATE MDLLCODE 4,763,245 8/1988 Emma et al. ........................... 395/375 BRANCH HISTORY TABLE 4,901.233 2/1990 Liptay ...... ... 395/375 5,185,869 2/1993 Suzuki ................................... 395/375 75) Inventors: Philip G. Emma, Danbury, Conn.; 5,226,164 7/1993 Nadas et al. ............................ 395/800 Joshua W. Knight, III, Mohegan Lake, Primary Examiner-Kenneth S. Kim N.Y.; Thomas R. Puzak. Ridgefield, Attorney, Agent, or Firm-Jay P. Sbrollini Conn.; James R. Robinson, Essex Junction, Vt.; A. James Wan 57 ABSTRACT Norstrand, Jr., Round Rock, Tex. A computer processing system includes a first memory that 73 Assignee: International Business Machines stores instructions belonging to a first instruction set archi Corporation, Armonk, N.Y. tecture and a second memory that stores instructions belong ing to a second instruction set architecture. An instruction (21) Appl. No.: 369,441 buffer is coupled to the first and second memories, for storing instructions that are executed by a processor unit. 22 Fied: Jan. 6, 1995 The system operates in one of two modes. In a first mode, instructions are fetched from the first memory into the 51 Int, C. m. G06F 9/32 instruction buffer according to data stored in a first branch 52 U.S. Cl. ....................... 395/587; 395/376; 395/586; history table. In the second mode, instructions are fetched 395/595; 395/597 from the second memory into the instruction buffer accord 58 Field of Search ........................... -

A Remotely Accessible Network Processor-Based Router for Network Experimentation
A Remotely Accessible Network Processor-Based Router for Network Experimentation Charlie Wiseman, Jonathan Turner, Michela Becchi, Patrick Crowley, John DeHart, Mart Haitjema, Shakir James, Fred Kuhns, Jing Lu, Jyoti Parwatikar, Ritun Patney, Michael Wilson, Ken Wong, David Zar Department of Computer Science and Engineering Washington University in St. Louis fcgw1,jst,mbecchi,crowley,jdd,mah5,scj1,fredk,jl1,jp,ritun,mlw2,kenw,[email protected] ABSTRACT Keywords Over the last decade, programmable Network Processors Programmable routers, network testbeds, network proces- (NPs) have become widely used in Internet routers and other sors network components. NPs enable rapid development of com- plex packet processing functions as well as rapid response to 1. INTRODUCTION changing requirements. In the network research community, the use of NPs has been limited by the challenges associ- Multi-core Network Processors (NPs) have emerged as a ated with learning to program these devices and with using core technology for modern network components. This has them for substantial research projects. This paper reports been driven primarily by the industry's need for more flexi- on an extension to the Open Network Laboratory testbed ble implementation technologies that are capable of support- that seeks to reduce these \barriers to entry" by providing ing complex packet processing functions such as packet clas- a complete and highly configurable NP-based router that sification, deep packet inspection, virtual networking and users can access remotely and use for network experiments. traffic engineering. Equally important is the need for sys- The base router includes support for IP route lookup and tems that can be extended during their deployment cycle to general packet filtering, as well as a flexible queueing sub- meet new service requirements. -

Abatement of Area and Power in Multiplexer Based on Cordic Using
INTERNATIONAL JOURNAL OF SCIENTIFIC PROGRESS AND RESEARCH (IJSPR) ISSN: 2349-4689 Volume-10, Number - 02, 2015 Abatement of Area and Power In Multiplexer Based on Cordic Using Cadence Tool Uma P.1, AnuVidhya G.2 VLSI Design, Karpaga Vinayaga College of Engineering and Technolog, G.S.T Road,Chinna Kolambakkam-603308 Abstract – CORDIC is an iterative Algorithm to perform a wide The CORDIC Algorithm is a unified computational scheme range of functions including vector rotations, certain to perform trigonometric, hyperbolic, linear and logarithmic functions. Both non pipelined and 2 level pipelined CORDIC with 8 stages, using 1. Computations of the trigonometric functions: sin, two schemes was performed. First scheme was original unrolled cos and arctan. CORDIC and second scheme was MUX based pipelined unrolled CORDIC. Compared to first scheme, the second scheme is more 2. Computations of the hyperbolic trigonometric reliable, since the second scheme uses multiplexer and registers. functions: sinh, cosh and arctanh. By adding multiplexer the area is reduced comparatively to the 3. It also compute the exponential function, the first architecture, since the first scheme uses only addition, natural logarithm and the square root. subtraction and shifting operation in all the 8 stages.8 iterations 4. Multiplication and division. are performed and it is implemented on QUARTUS II software. For future work, the number of iterations can be increased and CORDIC revolves around the idea of "rotating" the phase of also increase the bit size. This can be implemented in (digital) a complex number, by multiplying it by a succession of CADENCE software. constant values. Keywords: CORDIC, rotation mode, multiplexer, pipelining, QUARTUS. -

Graphical Microcode Simulator with a Reconfigurable Datapath
Rochester Institute of Technology RIT Scholar Works Theses 12-11-2006 Graphical microcode simulator with a reconfigurable datapath Brian VanBuren Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation VanBuren, Brian, "Graphical microcode simulator with a reconfigurable datapath" (2006). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Graphical Microcode Simulator with a Reconfigurable Datapath by Brian G VanBuren A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science in Computer Engineering Supervised by Associate Professor Dr. Muhammad Shaaban Department of Computer Engineering Kate Gleason College of Engineering Rochester Institute of Technology Rochester, New York August 2006 Approved By: Dr. Muhammad Shaaban Associate Professor Primary Adviser Dr. Roy Czernikowski Professor, Department of Computer Engineering Dr. Roy Melton Visiting Assistant Professor, Department of Computer Engineering Thesis Release Permission Form Rochester Institute of Technology Kate Gleason College of Engineering Title: Graphical Microcode Simulator with a Reconfigurable Datapath I, Brian G VanBuren, hereby grant permission to the Wallace Memorial Library repor- duce my thesis in whole or part. Brian G VanBuren Date Dedication To my son. iii Acknowledgments I would like to thank Dr. Shaaban for all his input and desire to have an update microcode simulator. I would like to thank Dr. Czernikowski for his support and methodical approach to everything. I would like to thank Dr. -
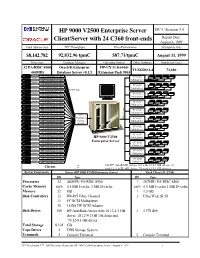
HP 9000 V2500 Enterprise Server Client/Server with 24 C360 Front-Ends
HP 9000 V2500 Enterprise Server TPC-C Revision 3.4 Client/Server with 24 C360 front-ends Report Date: August 6, 1999 Total System Cost TPC Throughput Price/Performance Availability Date $8,142,782 92,832.96 tpmC $87.71/tpmC August 31, 1999 ProcessorsDatabase Manager Operating SystemOther Software Number of Users 32 PA-RISC 8500 Oracle8i Enterprise HP-UX 11.0 64-bit TUXEDO 6.4 74,880 440MHz Database Server v8.1.5 Extension Pack 9903 HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer 1000T Base HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer HP 9000 Model C360 HP 9000 Model C360 FC SCSI Multiplexer HP 9000 Model C360 HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer HP HP 9000 Model C360 ProCurve Fibre Channel FC SCSI HP 9000 Model C360 Switch Multiplexer 4000M HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer HP 9000 Model C360 FC SCSI HP 9000 Model C360 HP 9000 V2500 Multiplexer HP 9000 Model C360 Enterprise Server HP 9000 Model C360 FC SCSI Multiplexer HP 9000 Model C360 HP 9000 Model C360 FC SCSI Multiplexer HP 9000 Model C360 HP 9000 Model C360 FC SCSI HP 9000 Model C360 Multiplexer Clients 106 HP AutoRAID Arrays (18 with 12 4.3 GB drives, 18 with 12 9.1GB 10K drives, 70 with 12 9.1 GB drives) System Components Server (HP 9000 V2500 Enterprise Server) Each Client (24 C360) Qty Type Qty Type Processors 32440MHz PA-RISC 8500 1 367MHz PA-RISC 8500 Cache Memory each0.5 MB I-cache, 1 MB D-cache each 0.5 MB I-cache/1 MB D-cache Memory 32GB 1 1.5 GB Disk Controllers 11HP-PCI Fibre Channel 1 Ultra Wide SCSI 11 FC SCSI Multiplexer 36 16 Bit FW SCSI Adapter Disk Drives 106HP AutoRaid Arrays with 18 12-4.3 GB 1 4 GB disk drives, 18 12-9.1 GB 10k disks and 70 12-9.1 GB drives Total Storage 8,102 GB Tape Drives 1 DDS Storage System Terminals 11Console Terminal Console Terminal TPC Benchmark C™ Full Disclosure Report for HP 9000 V2500 Enterprise Server - August 6, 1999 i HP 9000 V2500 TPC-C Rev 3.4 Enterprise Server Report Date: August 6, 1999 Price Unit Qty 5 Year Maint. -

Unit 2 : Combinational Circuit
Unit 2 : Combinational Circuit Lesson 1 : Half and Full Adder Circuit 1.1. Learning Objectives On completion of this lesson you will be able to : ♦ design half and full adder circuit ♦ understand basic operation of adder circuitry. Digital computers and calculators perform various arithmetic operations on numbers that are represented in binary form. These operations are all performed in the arithmetic logic unit of a computer. Logic gates and flip-flops are combined in the arithmetic logic unit so that they can add, subtract, multiply and divide numbers. These circuits perform arithmetic operations at speeds that are not humanly possible. We shall now study the addition operation circuit which is an important arithmetic operation in digital systems. 1.2. Binary Addition 1.2.1. The Half Adder When two digits are added together, the result consists of two parts, known as the SUM and the CARRY. Since there are only four possible combinations of two binary digits, one combination produces a carry. This can be shown as 0 1 0 1 +0 +0 +1 +1 Carry Sum Carry Sum Carry Sum Carry Sum 0 0 0 1 0 1 1 0 The Half Adder The truth table for the addition of two binary variables A and B can be shown below. A B Sum Carry 0 0 0 0 0 1 1 0 1 0 1 0 1 1 0 1 Table 2.1 : Half adder truth table. From the truth table it is clear that the SUM is only produced when A is at 1 and B is 0 or when A is 0 and B is 1. -

16-Channel Analog Multiplexer/Demultiplexer Rev
74HC4067; 74HCT4067 16-channel analog multiplexer/demultiplexer Rev. 8 — 9 September 2021 Product data sheet 1. General description The 74HC4067; 74HCT4067 is a single-pole 16-throw analog switch (SP16T) suitable for use in analog or digital 16:1 multiplexer/demultiplexer applications. The switch features four digital select inputs (S0, S1, S2 and S3), sixteen independent inputs/outputs (Yn), a common input/output (Z) and a digital enable input (E). When E is HIGH, the switches are turned off. Inputs include clamp diodes. This enables the use of current limiting resistors to interface inputs to voltages in excess of VCC. 2. Features and benefits • Wide supply voltage range from 2.0 V to 10.0 V • Input levels S0, S1, S2, S3 and E inputs: • For 74HC4067: CMOS level • For 74HCT4067: TTL level • CMOS low power dissipation • High noise immunity • Low ON resistance: • 80 Ω (typical) at VCC = 4.5 V • 70 Ω (typical) at VCC = 6.0 V • 60 Ω (typical) at VCC = 9.0 V • Complies with JEDEC standards: • JESD8C (2.7 V to 3.6 V) • JESD7A (2.0 V to 6.0 V) • Latch-up performance exceeds 100 mA per JESD 78 Class II Level B • ESD protection: • HBM JESD22-A114F exceeds 2000 V • MM JESD22-A115-A exceeds 200 V • CDM JESD22-C101E exceeds 1000 V • Multiple package options • Specified from -40 °C to +85 °C and -40 °C to +125 °C • Typical ‘break before make’ built-in 3. Applications • Analog multiplexing and demultiplexing • Digital multiplexing and demultiplexing • Signal gating Nexperia 74HC4067; 74HCT4067 16-channel analog multiplexer/demultiplexer 4.