Sega V. Accolade and the Right to Reverse Engineer Software William S
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A History of Video Game Consoles Introduction the First Generation
A History of Video Game Consoles By Terry Amick – Gerald Long – James Schell – Gregory Shehan Introduction Today video games are a multibillion dollar industry. They are in practically all American households. They are a major driving force in electronic innovation and development. Though, you would hardly guess this from their modest beginning. The first video games were played on mainframe computers in the 1950s through the 1960s (Winter, n.d.). Arcade games would be the first glimpse for the general public of video games. Magnavox would produce the first home video game console featuring the popular arcade game Pong for the 1972 Christmas Season, released as Tele-Games Pong (Ellis, n.d.). The First Generation Magnavox Odyssey Rushed into production the original game did not even have a microprocessor. Games were selected by using toggle switches. At first sales were poor because people mistakenly believed you needed a Magnavox TV to play the game (GameSpy, n.d., para. 11). By 1975 annual sales had reached 300,000 units (Gamester81, 2012). Other manufacturers copied Pong and began producing their own game consoles, which promptly got them sued for copyright infringement (Barton, & Loguidice, n.d.). The Second Generation Atari 2600 Atari released the 2600 in 1977. Although not the first, the Atari 2600 popularized the use of a microprocessor and game cartridges in video game consoles. The original device had an 8-bit 1.19MHz 6507 microprocessor (“The Atari”, n.d.), two joy sticks, a paddle controller, and two game cartridges. Combat and Pac Man were included with the console. In 2007 the Atari 2600 was inducted into the National Toy Hall of Fame (“National Toy”, n.d.). -

CLONES, BONES and TWILIGHT ZONES: PROTECTING the DIGITAL PERSONA of the QUICK, the DEAD and the IMAGINARY by Josephj
CLONES, BONES AND TWILIGHT ZONES: PROTECTING THE DIGITAL PERSONA OF THE QUICK, THE DEAD AND THE IMAGINARY By JosephJ. Beard' ABSTRACT This article explores a developing technology-the creation of digi- tal replicas of individuals, both living and dead, as well as the creation of totally imaginary humans. The article examines the various laws, includ- ing copyright, sui generis, right of publicity and trademark, that may be employed to prevent the creation, duplication and exploitation of digital replicas of individuals as well as to prevent unauthorized alteration of ex- isting images of a person. With respect to totally imaginary digital hu- mans, the article addresses the issue of whether such virtual humans should be treated like real humans or simply as highly sophisticated forms of animated cartoon characters. TABLE OF CONTENTS I. IN TR O DU C T IO N ................................................................................................ 1166 II. CLONES: DIGITAL REPLICAS OF LIVING INDIVIDUALS ........................ 1171 A. Preventing the Unauthorized Creation or Duplication of a Digital Clone ...1171 1. PhysicalAppearance ............................................................................ 1172 a) The D irect A pproach ...................................................................... 1172 i) The T echnology ....................................................................... 1172 ii) Copyright ................................................................................. 1176 iii) Sui generis Protection -

Trouble in Toyland Table of Contents
Trouble in Toyland Table of Contents 1. Executive Summary..................................................................................2 2. Introduction...............................................................................................5 3. Choking Hazards Regulatory History .............................................................................5 Requirements of the 1994 Child Safety Protection Act ......................6 4. Phthalates in Children’s Toys ...................................................................7 5. Dangerously Loud Toys............................................................................11 6. Other Toy Hazards ...................................................................................12 7. Gaps Remaining in Toy Safety ................................................................14 8. Positive Trends in 2002 ............................................................................17 9. Appendices...............................................................................................18 The 2002 PIRG Potentially Hazardous Toys List Deaths from Toys 1990-2001 Toys Recalled As a Result of PIRG Toy Surveys PIRG’s 2002 Survey of Online Toy Retailers Toy Companies and their Policies Regarding Phthalates PIRG’s Tips for Toy Safety PIRG’s 2002 Trouble in Toyland Report – Page 1 Executive Summary The 2002 Trouble in Toyland report is the seventeenth annual Public Interest Research Group (PIRG) toy safety survey. PIRG uses its survey to educate parents and the general public -

Links to the Past User Research Rage 2
ALL FORMATS LIFTING THE LID ON VIDEO GAMES User Research Links to Game design’s the past best-kept secret? The art of making great Zelda-likes Issue 9 £3 wfmag.cc 09 Rage 2 72000 Playtesting the 16 neon apocalypse 7263 97 Sea Change Rhianna Pratchett rewrites the adventure game in Lost Words Subscribe today 12 weeks for £12* Visit: wfmag.cc/12weeks to order UK Price. 6 issue introductory offer The future of games: subscription-based? ow many subscription services are you upfront, would be devastating for video games. Triple-A shelling out for each month? Spotify and titles still dominate the market in terms of raw sales and Apple Music provide the tunes while we player numbers, so while the largest publishers may H work; perhaps a bit of TV drama on the prosper in a Spotify world, all your favourite indie and lunch break via Now TV or ITV Player; then back home mid-tier developers would no doubt ounder. to watch a movie in the evening, courtesy of etix, MIKE ROSE Put it this way: if Spotify is currently paying artists 1 Amazon Video, Hulu… per 20,000 listens, what sort of terrible deal are game Mike Rose is the The way we consume entertainment has shifted developers working from their bedroom going to get? founder of No More dramatically in the last several years, and it’s becoming Robots, the publishing And before you think to yourself, “This would never increasingly the case that the average person doesn’t label behind titles happen – it already is. -

The Uses of Animation 1
The Uses of Animation 1 1 The Uses of Animation ANIMATION Animation is the process of making the illusion of motion and change by means of the rapid display of a sequence of static images that minimally differ from each other. The illusion—as in motion pictures in general—is thought to rely on the phi phenomenon. Animators are artists who specialize in the creation of animation. Animation can be recorded with either analogue media, a flip book, motion picture film, video tape,digital media, including formats with animated GIF, Flash animation and digital video. To display animation, a digital camera, computer, or projector are used along with new technologies that are produced. Animation creation methods include the traditional animation creation method and those involving stop motion animation of two and three-dimensional objects, paper cutouts, puppets and clay figures. Images are displayed in a rapid succession, usually 24, 25, 30, or 60 frames per second. THE MOST COMMON USES OF ANIMATION Cartoons The most common use of animation, and perhaps the origin of it, is cartoons. Cartoons appear all the time on television and the cinema and can be used for entertainment, advertising, 2 Aspects of Animation: Steps to Learn Animated Cartoons presentations and many more applications that are only limited by the imagination of the designer. The most important factor about making cartoons on a computer is reusability and flexibility. The system that will actually do the animation needs to be such that all the actions that are going to be performed can be repeated easily, without much fuss from the side of the animator. -
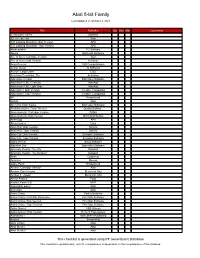
Atari 8-Bit Family
Atari 8-bit Family Last Updated on October 2, 2021 Title Publisher Qty Box Man Comments 221B Baker Street Datasoft 3D Tic-Tac-Toe Atari 747 Landing Simulator: Disk Version APX 747 Landing Simulator: Tape Version APX Abracadabra TG Software Abuse Softsmith Software Ace of Aces: Cartridge Version Atari Ace of Aces: Disk Version Accolade Acey-Deucey L&S Computerware Action Quest JV Software Action!: Large Label OSS Activision Decathlon, The Activision Adventure Creator Spinnaker Software Adventure II XE: Charcoal AtariAge Adventure II XE: Light Gray AtariAge Adventure!: Disk Version Creative Computing Adventure!: Tape Version Creative Computing AE Broderbund Airball Atari Alf in the Color Caves Spinnaker Software Ali Baba and the Forty Thieves Quality Software Alien Ambush: Cartridge Version DANA Alien Ambush: Disk Version Micro Distributors Alien Egg APX Alien Garden Epyx Alien Hell: Disk Version Syncro Alien Hell: Tape Version Syncro Alley Cat: Disk Version Synapse Software Alley Cat: Tape Version Synapse Software Alpha Shield Sirius Software Alphabet Zoo Spinnaker Software Alternate Reality: The City Datasoft Alternate Reality: The Dungeon Datasoft Ankh Datamost Anteater Romox Apple Panic Broderbund Archon: Cartridge Version Atari Archon: Disk Version Electronic Arts Archon II - Adept Electronic Arts Armor Assault Epyx Assault Force 3-D MPP Assembler Editor Atari Asteroids Atari Astro Chase Parker Brothers Astro Chase: First Star Rerelease First Star Software Astro Chase: Disk Version First Star Software Astro Chase: Tape Version First Star Software Astro-Grover CBS Games Astro-Grover: Disk Version Hi-Tech Expressions Astronomy I Main Street Publishing Asylum ScreenPlay Atari LOGO Atari Atari Music I Atari Atari Music II Atari This checklist is generated using RF Generation's Database This checklist is updated daily, and it's completeness is dependent on the completeness of the database. -

Games and Other Uncopyrightable Systems Bruce E
Marquette University Law School Marquette Law Scholarly Commons Faculty Publications Faculty Scholarship 1-1-2011 Games and Other Uncopyrightable Systems Bruce E. Boyden Marquette University Law School, [email protected] Follow this and additional works at: http://scholarship.law.marquette.edu/facpub Part of the Law Commons Publication Information Bruce E. Boyden, Games and Other Uncopyrightable Systems, 18 Geo. Mason L. Rev. 439 (2011) Repository Citation Boyden, Bruce E., "Games and Other Uncopyrightable Systems" (2011). Faculty Publications. Paper 82. http://scholarship.law.marquette.edu/facpub/82 This Article is brought to you for free and open access by the Faculty Scholarship at Marquette Law Scholarly Commons. It has been accepted for inclusion in Faculty Publications by an authorized administrator of Marquette Law Scholarly Commons. For more information, please contact [email protected]. 2011] 439 GAMES AND OTHER UNCOPYRIGHTABLE SYSTEMS Bruce E. Boyden* INTRODUCTION Games are deceptively simple objects of human culture.1 They are familiar, commonplace, and often easy to learn: young children play them at an early age. For most people, games are a pastime, a form of recreation that involves relatively little preparation or time commitment.2 They are thus the very opposite of work, and hardly comparable to such serious pursuits as scholarship or art.3 For all their seeming ingenuousness, however, games are also deeply puzzling. Defining games is a notoriously difficult enterprise.4 Scholars from several different disciplines have struggled to determine what the nature, or essence, of games really is. And the elusiveness of games poses problems for intellectual property law as well. -

Cartoon and the Cult of Reduction
Forced Perspectives: Cartoon and The Cult Of Reduction MARTINE LISA COROMPT Submitted in partial fulfillment of the requirements of the degree of Doctor of Philosophy (by creative work and dissertation) August 2016 School of Art Faculty Of The Victorian College Of The Arts The University of Melbourne 2 FIG 1 Corompt, Martine Torrent – the endless storm 2015 still from the digital animation 3 4 ABSTRACT Summary Commencing with caricature and reductive imaging techniques, this research explores parallel tendencies evident within broader culture. The thesis argues this reductive predisposition became broader and more prominent during Modernism, the digital revolution of the 1990s, and is strongly manifest within various aspects of contemporary art and culture. Theorized as the ‘Cult of Reduction’ this tendency is both a cultural condition, and a studio methodology employed to create two dimensional projected animation and digital prints. Abstract Beginning with pictorial caricature as a historical predecessor to animation, the research attempted to find in caricature a meaningful methodology to provide a framework for two-dimensional animation. Incorporating digital processes with drawing and installation, reduction was understood and examined pictorially, temporally and materially. The thesis project considered caricature as a means of exploring pictorial representation as reduction, but soon recognized reduction had more broad implications, and parallel examples were discovered in areas such as economics, ecology lifestyle ideologies, as well as Fine art and design. While pictorial reduction was most obvious within Modernism, it also was resonant in less obvious ways within the digital art revolution of the 1990’s. It has been prevalent again in contemporary art as a ‘reductivist practice’ recognized by Mike Kelley’s essay ‘Foul Perfection: Thoughts on Caricature’ (1989). -

Pokemon Fans Can Now Choose Yahoo! Auctions to Bid on Hasbro's
Pokemon Fans Can Now Choose Yahoo! Auctions To Bid On Hasbro's "I Choose You Pikachu™" Toys Charity Auction of "Must Have" Toy for Holiday Season to Benefit Hasbro Children's Hospital Pokemon Fans Can Now Choose Yahoo! Auctions To Bid On Hasbro's "I Choose You Pikachu™" Toys Charity Auction of "Must Have" Toy for Holiday Season to Benefit Hasbro Children's Hospital CINCINNATI, OH -- December 2, 1999 -- Consumers can help make a difference in the lives of children this holiday season by heading to Yahoo!® Auctions (http://auctions.yahoo.com). Hasbro, Inc. (NYSE: HAS) today announced that it has teamed with Yahoo! Inc. (NASDAQ: YHOO) to host a series of online auctions of Hasbro's "I Choose You Pikachu," already a hot toy since making its retail debut in November. "I Choose You Pikachu" is the first in a series of electronic plush Pokémon toys to be released by Hasbro, Nintendo's worldwide master toy and board game licensee for Pokémon. "Pokémon, The First Movie " opened to record box office attendance in November. "I Choose You Pikachu" is no ordinary plush toy; it is an electronic plush version of the most popular Pokémon character of all, #25 Pikachu. The adorable eight-inch huggable Pikachu is the ultimate combination of today's hot electronic plush toy and the even hotter Pokémon phenomenon. All proceeds from the Yahoo! charity auction will benefit Hasbro Children's Hospital in Providence, Rhode Island. The more that kids interact with their "I Choose You Pikachu," the more talkative it gets. Squeeze its hand and Pikachu's mouth wiggles while saying its name (at first, "Pi," then "Pi-ka," then "Pikachu!"). -

Un Conjunto De Herramientas Para Unity Orientado Al Desarrollo De Videojuegos De Acción-Aventura Y Estilo Retro Con Gráficos Isométricos 3D
UN CONJUNTO DE HERRAMIENTAS PARA UNITY ORIENTADO AL DESARROLLO DE VIDEOJUEGOS DE ACCIÓN-AVENTURA Y ESTILO RETRO CON GRÁFICOS ISOMÉTRICOS 3D D. Iván José Pérez Colado D. Víctor Manuel Pérez Colado GRADO EN INGENIERÍA DEL SOFTWARE FACULTAD DE INFORMÁTICA UNIVERSIDAD COMPLUTENSE DE MADRID TRABAJO DE FIN DE GRADO DE INGENIERÍA DEL SOFTWARE Madrid, 20 junio de 2014 Director: Prof. Dr. D. Federico Peinado Gil Autorización de difusión y utilización Iván José Pérez Colado y Víctor Manuel Pérez Colado autorizamos a la Universidad Complutense de Madrid a difundir y utilizar con fines académicos, no comerciales y mencionando expresamente a sus autores, tanto la propia memoria, como el código, los contenidos audiovisuales incluso si incluyen imágenes de los autores, la documentación y/o el prototipo desarrollado. Fdo. Iván José Pérez Colado Fdo. Víctor Manuel Pérez Colado Para nuestro nono Quien con su empeño e ilusión, fue un motivo en nuestras vidas para llegar hasta donde hemos llegado y no está hoy con nosotros para verlo Agradecimientos Queremos agradecer, en primer lugar, a nuestro director de proyecto Federico Peinado Gil, por darnos la oportunidad de participar en un proyecto del campo que más nos apasiona, los videojuegos, y por toda la ayuda y dedicación que nos ha prestado durante el curso para completarlo. En segundo lugar, agradecemos a nuestros amigos y familia, su opinión y continua valoración de los resultados que íbamos obteniendo durante la realización del proyecto. Por último, agradecer a la comunidad de usuarios de Unity, y a los usuarios de StackOverflow, la cesión de múltiples fragmentos de código que han servido de referencia para la realización del proyecto. -

Atari IP Catalog 2019 IP List (Highlighted Links Are Included in Deck)
Atari IP Catalog 2019 IP List (Highlighted Links are Included in Deck) 3D Asteroids Basketball Fatal Run Miniature Golf Retro Atari Classics Super Asteroids & Missile 3D Tic-Tac-Toe Basketbrawl Final Legacy Minimum Return to Haunted House Command A Game of Concentration Bionic Breakthrough Fire Truck * Missile Command Roadrunner Super Baseball Adventure Black Belt Firefox * Missile Command 2 * RollerCoaster Tycoon Super Breakout Adventure II Black Jack Flag Capture Missile Command 3D Runaway * Super Bunny Breakout Agent X * Black Widow * Flyball * Monstercise Saboteur Super Football Airborne Ranger Boogie Demo Food Fight (Charley Chuck's) Monte Carlo * Save Mary Superbug * Air-Sea Battle Booty Football Motor Psycho Scrapyard Dog Surround Akka Arrh * Bowling Frisky Tom MotoRodeo Secret Quest Swordquest: Earthworld Alien Brigade Boxing * Frog Pond Night Driver Sentinel Swordquest: Fireworld Alpha 1 * Brain Games Fun With Numbers Ninja Golf Shark Jaws * Swordquest: Waterworld Anti-Aircraft * Breakout Gerry the Germ Goes Body Off the Wall Shooting Arcade Tank * Aquaventure Breakout * Poppin Orbit * Sky Diver Tank II * Asteroids Breakout Boost Goal 4 * Outlaw Sky Raider * Tank III * Asteroids Deluxe * Canyon Bomber Golf Outlaw * Slot Machine Telepathy Asteroids On-line Casino Gotcha * Peek-A-Boo Slot Racers Tempest Asteroids: Gunner Castles and Catapults Gran Trak 10 * Pin Pong * Smokey Joe * Tempest 2000 Asteroids: Gunner+ Caverns of Mars Gran Trak 20 * Planet Smashers Soccer Tempest 4000 Atari 80 Classic Games in One! Centipede Gravitar Pong -

Some Key Toy Manufacturers
45936 MOC Must Toys Book6 12/1/05 7:53 am Page 41 Some key toy manufacturers Britain Abbatt Toys Paul and Marjorie Abbatt were pioneers of innovative educational toys in the 1930s. They set up in business in 1932 selling toys to friends and by mail order from their flat in Tavistock Square, London. Demand was such that in 1936 they opened a child friendly shop at 94 Wimpole Street, designed by their friend the architect Ernö Goldfinger. The Abbatts were his main clients at the time and he designed toys and nursery equipment for them. They were concerned with the play needs of children in general, introducing a range of toys for children with physical disabilities devised by Milan Morgenstern. In 1951 they were instrumental in setting up the Children’s Play Activities Trust Ltd. to promote excellence in toy design and manufacture. After Paul Abbatt died in 1971 the business was bought by the Educational Supply Association. William Britain Ltd. Britains Ltd. was founded by William Britain in London in 1840. At first Britains made tin and clockwork toys and from the 1890s they made model soldiers. It also opened an office in Paris, France in 1905. The company made munitions for both world wars. In 1954 Herald miniatures, makers of unbreakable plastic toys, became a subsidiary of Britains. In 1966 Britains ceased to manufacture its metal soldiers. It was purchased by Ertl Co. in 1997. The Chad Valley Co. Ltd. The Chad Valley trademark was first registered in 1897 when the original company of Johnson Brothers added games to its stationery range.