Ipv4 Address Exhaustion, Mitigation Strategies and Implications for the U.S
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Accelerating Adoption of Ipv6
Accelerating Adoption of IPv6 LUDVIG AHLINDER and ANDERS ERIKSSON KTH Information and Communication Technology Degree project in Communication Systems First level, 15.0 HEC Stockholm, Sweden Accelerating Adoption of IPv6 Ludvig Ahlinder and Anders Eriksson 2011.05.17 Mentor and Examiner: Prof. Gerald Q. Maguire Jr School of Information and Communications Technology Royal Institute of Technology (KTH) Stockholm, Sweden Abstract It has long been known that the number of unique IPv4-addresses would be exhausted because of the rapid expansion of the Internet and because countries such as China and India are becoming more and more connected to the rest of the world. IPv6 is a new version of the Internet Protocol which is supposed to succeed the old version, IPv4, in providing more addresses and new services. The biggest challenge of information and communication technology (ICT) today is to transition from IPv4 to IPv6. The purpose of this thesis is to accelerate the adoption of IPv6 by highlighting the benefits of it compared to IPv4. Although the need for more IP-addresses is the most urgent incentive for the transition to IPv6, other factors also exist. IPv6 offers many improvements to IPv4 which are necessary for the continued expansion of Internet-based applications and services. Some argue that we do not need to transition to IPv6 as the problems with IPv4, mainly the address- shortage, can be solved in other ways. One of the methods of doing this is by extending the use of Network Address Translators (NATs), but the majority of experts and specialists believe that NATs should not be seen as a long-term solution. -

INTERNET ADDRESSING: MEASURING DEPLOYMENT of Ipv6
INTERNET ADDRESSING: MEASURING DEPLOYMENT OF IPv6 APRIL 2010 2 FOREWORD FOREWORD This report provides an overview of several indicators and data sets for measuring IPv6 deployment. This report was prepared by Ms. Karine Perset of the OECD‟s Directorate for Science, Technology and Industry. The Working Party on Communication Infrastructures and Services Policy (CISP) recommended, at its meeting in December 2009, forwarding the document to the Committee for Information, Computer and Communications Policy (ICCP) for declassification. The ICCP Committee agreed to make the document publicly available in March 2010. Experts from the Internet Technical Advisory Committee to the ICCP Committee (ITAC) and the Business and Industry Advisory Committee to the OECD (BIAC) have provided comments, suggestions, and contributed significantly to the data in this report. Special thanks are to be given to Geoff Huston from APNIC and Leo Vegoda from ICANN on behalf of ITAC/the NRO, Patrick Grossetete from ArchRock, Martin Levy from Hurricane Electric, Google and the IPv6 Forum for providing data, analysis and comments for this report. This report was originally issued under the code DSTI/ICCP/CISP(2009)17/FINAL. Issued under the responsibility of the Secretary-General of the OECD. The opinions expressed and arguments employed herein do not necessarily reflect the official views of the OECD member countries. ORGANISATION FOR ECONOMIC CO-OPERATION AND DEVELOPMENT The OECD is a unique forum where the governments of 30 democracies work together to address the economic, social and environmental challenges of globalisation. The OECD is also at the forefront of efforts to understand and to help governments respond to new developments and concerns, such as corporate governance, the information economy and the challenges of an ageing population. -

The Internet in Transition: the State of the Transition to Ipv6 in Today's
Please cite this paper as: OECD (2014-04-03), “The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4”, OECD Digital Economy Papers, No. 234, OECD Publishing, Paris. http://dx.doi.org/10.1787/5jz5sq5d7cq2-en OECD Digital Economy Papers No. 234 The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4 OECD FOREWORD This report was presented to the OECD Working Party on Communication, Infrastructures and Services Policy (CISP) in June 2013. The Committee for Information, Computer and Communications Policy (ICCP) approved this report in December 2013 and recommended that it be made available to the general public. It was prepared by Geoff Huston, Chief Scientist at the Asia Pacific Network Information Centre (APNIC). The report is published on the responsibility of the Secretary-General of the OECD. Note to Delegations: This document is also available on OLIS under reference code: DSTI/ICCP/CISP(2012)8/FINAL © OECD 2014 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 TABLE OF CONTENTS FOREWORD ................................................................................................................................................... 2 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 .......................... 4 -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Ipv6 in Mobile Networks APRICOT 2016 – February 2016
IPv6 in Mobile Networks APRICOT 2016 – February 2016 Telstra Unrestricted Introduction Sunny Yeung - Senior Technology Specialist, Telstra Wireless Network Engineering Technical Lead for Wireless IPv6 deployment Wireless Mobile IP Edge/Core Architect Telstra Unrestricted | IPv6 in Mobile Networks | Sunny Yeung | 02/2016 | 2 Agenda 1. Why IPv6 in Mobile Networks? 2. IPv6 – it’s here. Really. 3. Wireless Network Architectures 4. 464XLAT – Saviour? Or the devil in disguise? 5. Solution Testing and Results 6. Conclusion 7. Q&A Telstra Unrestricted | IPv6 in Mobile Networks | Sunny Yeung | 02/2016 | 3 Why IPv6 in Mobile Networks? Why IPv6 in Mobile Networks? • Exponential Growth in mobile data traffic and user equipment • Network readiness for Internet-of-Things • IPv4 public address depletion • IPv4 private address depletion • Offload the NAT44 architecture • VoLTE/IMS Remember – IPv6 should be invisible to the end-user Telstra Unrestricted | IPv6 in Mobile Networks | Sunny Yeung | 02/2016 | 5 IPv6 It’s Here. Really. IPv6 Global Traffic The world according to Google Source - https://www.google.com/intl/en/ipv6/statistics.html Telstra Unrestricted | IPv6 in Mobile Networks | Sunny Yeung | 02/2016 | 7 Carrier Examples SP1 SP2 / SP3 SP4 Dual-Stack SS+NAT64+DNS64+CLAT SS/DS+NAT64+DNS-HD +CLAT 1. Every carrier will have a unique set of circumstances that dictates which transition method they will use. There is no standard way of doing this. 2. You must determine which is the best method for your network. In any method, remember to ensure you have a long-term strategy for the eventual deployment of native Single Stack IPv6! Telstra Unrestricted | IPv6 in Mobile Networks | Sunny Yeung | 02/2016 | 8 IPv4 reality – from a business perspective 1. -

Evolution of Mobile Networks and Ipv6
Evolution of Mobile Networks and IPv6 Miwa Fujii <[email protected]> APNIC, Senior Advisor Internet Development 25th April 2014 APEC TEL49 Yangzhou, China Issue Date: [25/04/2014] Revision: [3] Overview • Growth path of the Internet – Asia Pacific region • Evolution of mobile networks • IPv6 deployment in mobile networks: Case study • IPv6 deployment status update • IPv6 in mobile networks: way forward 2 Growth path of the Internet The next wave of Internet growth • The Internet has experienced phenomenal growth in the last 20 years – 16 million users in 1995 and 2.8 billion users in 2013 • And the Internet is still growing: Research indicates that by 2017, there will be about 3.6 billion Internet users – Over 40% of the world’s projected population (7.6 billion) • The next wave of Internet growth will have a much larger impact on the fundamental nature of the Internet – It is coming from mobile networks http://www.allaboutmarketresearch.com/internet.htm 4 Internet development in AP region: Internet users 100.00 Internet Users (per 100 inhabitants) New Zealand, 89.51 90.00 Canada, 86.77 Korea, 84.10 Australia, 82.35 80.00 United States, 81.03 Japan, 79.05 Chinese Taipei, 75.99 Singapore, 74.18 70.00 Hong Kong, China, 72.80 Malaysia, 65.80 Chile, 61.42 60.00 Brunei Darussalam, 60.27 Russia, 53.27 50.00 China, 42.30 Viet Nam, 39.49 40.00 Mexico, 38.42 Peru, 38.20 The Philippines, 36.24 30.00 Thailand, 26.50 20.00 Indonesia, 15.36 10.00 Papua New Guinea, 2.30 0.00 2005 2006 2007 2008 2009 2010 2011 2012 http://statistics.apec.org/ 5 Internet -
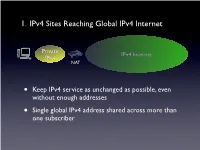
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

Aerohive Configuration Guide: RADIUS Authentication | 2
Aerohive Configuration Guide RADIUS Authentication Aerohive Configuration Guide: RADIUS Authentication | 2 Copyright © 2012 Aerohive Networks, Inc. All rights reserved Aerohive Networks, Inc. 330 Gibraltar Drive Sunnyvale, CA 94089 P/N 330068-03, Rev. A To learn more about Aerohive products visit www.aerohive.com/techdocs Aerohive Networks, Inc. Aerohive Configuration Guide: RADIUS Authentication | 3 Contents Contents ...................................................................................................................................................................................................................... 3 IEEE 802.1X Primer................................................................................................................................................................................................... 4 Example 1: Single Site Authentication .................................................................................................................................................................... 6 Step 1: Configuring the Network Policy ..............................................................................................................................................................7 Step 2: Configuring the Interface and User Access .........................................................................................................................................7 Step 3: Uploading the Configuration and Certificates .................................................................................................................................... -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Domain Name System System Work?
What is the DNS? - how it works Isaac Maposa | Dev Anand Teelucksingh | Beran Gillen Community Onboarding Program | 11 March 2017 Agenda 1 2 3 What is the Domain Structure of the How does the Name System? Domain Name Domain Name System System Work? 4 5 6 Who makes the Stakeholders in the Engage with ICANN Domain Name Domain Name ??? System Work? System. | 2 What is the Domain Name System (DNS)? The Internet, what is it..? ● The Internet is a network of networks that interconnects devices to exchange information. ● In order to “talk” to each other, all of these devices must have a unique numerical address called an Internet Protocol address or IP Address. An example of an IP address is 94.127.53.132 ● When you visit a website from your browser, you are requesting the website from your device’s IP address to the web server’s IP address. ● However, you don’t type in the ip address of the web server, rather the domain name of for example www.google.com ● In so doing, you have queried the DNS. ● So what is this DNS???? | 4 What is the Domain Name System? ● The Domain Name System or DNS overcomes this problem of remembering IP addresses by mapping domain names to IP addresses. ● While this sounds like a phone book, it is not a centralised database. ● The DNS is a distributed database across a hierarchy of networks of servers and provide ways for devices and software (like browsers and email) to query the DNS to get an IP address. ● Domain names must be unique. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S.