Oracle VM Virtualbox User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -
SUMURI Macintosh Forensics Best Practices
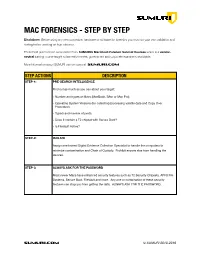
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM). -

Attacker Chatbots for Randomised and Interactive Security Labs, Using Secgen and Ovirt
Hackerbot: Attacker Chatbots for Randomised and Interactive Security Labs, Using SecGen and oVirt Z. Cliffe Schreuders, Thomas Shaw, Aimée Mac Muireadhaigh, Paul Staniforth, Leeds Beckett University Abstract challenges, rewarding correct solutions with flags. We deployed an oVirt infrastructure to host the VMs, and Capture the flag (CTF) has been applied with success in leveraged the SecGen framework [6] to generate lab cybersecurity education, and works particularly well sheets, provision VMs, and provide randomisation when learning offensive techniques. However, between students. defensive security and incident response do not always naturally fit the existing approaches to CTF. We present 2. Related Literature Hackerbot, a unique approach for teaching computer Capture the flag (CTF) is a type of cyber security game security: students interact with a malicious attacker which involves collecting flags by solving security chatbot, who challenges them to complete a variety of challenges. CTF events give professionals, students, security tasks, including defensive and investigatory and enthusiasts an opportunity to test their security challenges. Challenges are randomised using SecGen, skills in competition. CTFs emerged out of the and deployed onto an oVirt infrastructure. DEFCON hacker conference [7] and remain common Evaluation data included system performance, mixed activities at cybersecurity conferences and online [8]. methods questionnaires (including the Instructional Some events target students with the goal of Materials Motivation Survey (IMMS) and the System encouraging interest in the field: for example, PicoCTF Usability Scale (SUS)), and group interviews/focus is an annual high school competition [9], and CSAW groups. Results were encouraging, finding the approach CTF is an annual competition for students in Higher convenient, engaging, fun, and interactive; while Education (HE) [10]. -

Ovirt and Openstack Storage (Present and Future)
oVirt and OpenStack Storage (present and future) Federico Simoncelli Principal Software Engineer, Red Hat January 2014 1 Federico Simoncelli – oVirt and OpenStack Storage (present and future) Agenda ● Introduction ● oVirt and OpenStack Overview ● Present ● oVirt and Glance Integration ● Importing and Exporting Glance Images ● Current Constraints and Limitations ● Future ● Glance Future Integration ● Keystone Authentication in oVirt ● oVirt and Cinder Integration 2 Federico Simoncelli – oVirt and OpenStack Storage (present and future) oVirt Overview ● oVirt is a virtualization management application ● manages hardware nodes, storage and network resources, in order to deploy and monitor virtual machines running in your data center ● Free open source software released under the terms of the Apache License 3 Federico Simoncelli – oVirt and OpenStack Storage (present and future) The oVirt Virtualization Architecture 4 Federico Simoncelli – oVirt and OpenStack Storage (present and future) OpenStack Overview ● Cloud computing project to provide an Infrastructure as a Service (IaaS) ● Controls large pools of compute, storage, and networking resources ● Free open source software released under the terms of the Apache License ● Project is managed by the OpenStack Foundation, a non-profit corporate entity established in September 2012 5 Federico Simoncelli – oVirt and OpenStack Storage (present and future) OpenStack Glance Service ● Provides services for discovering, registering, and retrieving virtual machine images ● RESTful API that allows querying -

Linux Kernal II 9.1 Architecture
Page 1 of 7 Linux Kernal II 9.1 Architecture: The Linux kernel is a Unix-like operating system kernel used by a variety of operating systems based on it, which are usually in the form of Linux distributions. The Linux kernel is a prominent example of free and open source software. Programming language The Linux kernel is written in the version of the C programming language supported by GCC (which has introduced a number of extensions and changes to standard C), together with a number of short sections of code written in the assembly language (in GCC's "AT&T-style" syntax) of the target architecture. Because of the extensions to C it supports, GCC was for a long time the only compiler capable of correctly building the Linux kernel. Compiler compatibility GCC is the default compiler for the Linux kernel source. In 2004, Intel claimed to have modified the kernel so that its C compiler also was capable of compiling it. There was another such reported success in 2009 with a modified 2.6.22 version of the kernel. Since 2010, effort has been underway to build the Linux kernel with Clang, an alternative compiler for the C language; as of 12 April 2014, the official kernel could almost be compiled by Clang. The project dedicated to this effort is named LLVMLinxu after the LLVM compiler infrastructure upon which Clang is built. LLVMLinux does not aim to fork either the Linux kernel or the LLVM, therefore it is a meta-project composed of patches that are eventually submitted to the upstream projects. -

Oracle VM Virtualbox User Manual
Oracle VM VirtualBox R User Manual Version 5.0.16 c 2004-2016 Oracle Corporation http://www.virtualbox.org Contents 1 First steps 11 1.1 Why is virtualization useful?............................. 12 1.2 Some terminology................................... 12 1.3 Features overview................................... 13 1.4 Supported host operating systems.......................... 15 1.5 Installing VirtualBox and extension packs...................... 16 1.6 Starting VirtualBox.................................. 17 1.7 Creating your first virtual machine......................... 18 1.8 Running your virtual machine............................ 21 1.8.1 Starting a new VM for the first time.................... 21 1.8.2 Capturing and releasing keyboard and mouse.............. 22 1.8.3 Typing special characters.......................... 23 1.8.4 Changing removable media......................... 24 1.8.5 Resizing the machine’s window...................... 24 1.8.6 Saving the state of the machine...................... 25 1.9 Using VM groups................................... 26 1.10 Snapshots....................................... 26 1.10.1 Taking, restoring and deleting snapshots................. 27 1.10.2 Snapshot contents.............................. 28 1.11 Virtual machine configuration............................ 29 1.12 Removing virtual machines.............................. 30 1.13 Cloning virtual machines............................... 30 1.14 Importing and exporting virtual machines..................... 31 1.15 Global Settings................................... -

Oracle Virtualbox Installation, Setup, and Ubuntu Introduction
ORACLE VIRTUALBOX INSTALLATION, SETUP, AND UBUNTU INTRODUCTION • VirtualBox is a hardware virtualization program. • Create virtual computers aka virtual machines. • Prototyping, sandboxing, testing. • The computer that VirtualBox is installed on is called the “host”, and each virtual machine is called a “guest”. PREREQUISITES Since virtual machines share resources with the host computer, we need to know what resources we have available on our host. • Click “Type here to search”. • Search for “System Information”. • Note the number of processor cores and the amount of RAM installed in your host. PREREQUISITES • Expand “Components”. • Expand “Storage”. • Select “Drives”. • Note the amount of free space available on your host. Every computer is different, so how we will need to balance these resources between our host and guest systems will differ. DOWNLOADING VIRTUALBOX • VISIT VIRTUALBOX.ORG • SELECT THE CORRECT PACKAGE • CLICK THE DOWNLOAD LINK. FOR YOUR HOST. INSTALLING VIRTUALBOX • Browse to where you downloaded VirtualBox and run the installer. • All default options will be fine. Simply follow the prompts. INSTALLING VIRTUALBOX • CLICK “FINISH”. • VIRTUALBOX INSTALLED! SETTING THINGS UP Before we build our first virtual machine, we need to download an operating system to install as our “guest”. • Visit Ubuntu.com • Click “Download”. • Select the current Ubuntu Desktop “LTS” release. • LTS releases focus on stability rather than cutting edge features. SETTING THINGS UP • IN VIRTUALBOX, CLICK “NEW”. • NAME THE VIRTUAL MACHINE. SETTING THINGS UP Here’s where we will need the system resources information that we looked up earlier. Each virtual machine functions like a separate computer in and of itself and will need to share RAM with the host. -

Vmware Workstation Pro 16.0 Using Vmware Workstation Pro
Using VMware Workstation Pro VMware Workstation Pro 16.0 Using VMware Workstation Pro You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents Using VMware Workstation Pro 14 1 Introduction and System Requirements 15 Host System Requirements for Workstation Pro 15 Processor Requirements for Host Systems 15 Supported Host Operating Systems 16 Memory Requirements for Host Systems 16 Display Requirements for Host Systems 16 Disk Drive Requirements for Host Systems 17 Local Area Networking Requirements for Host Systems 18 ALSA Requirements 18 Virtual Machine Features and Specifications 18 Supported Guest Operating Systems 18 Virtual Machine Processor Support 18 Virtual Machine Chipset and BIOS Support 19 Virtual Machine Memory Allocation 19 Virtual Machine Graphics and Keyboard Support 19 Virtual Machine IDE Drive Support 19 Virtual Machine SCSI Device Support 20 Virtual Machine Floppy Drive Support 20 Virtual Machine Serial and Parallel Port Support 20 Virtual Machine USB Port Support 20 Virtual Machine Mouse and Drawing Tablet Support 21 Virtual Machine Ethernet Card Support 21 Virtual Machine Networking Support 21 Virtual Machine Sound Support 21 2 Installing and Using Workstation Pro 23 Obtaining the Workstation Pro Software and License Key 23 Trial Version Expiration Date Warnings 24 Installing Workstation Pro with Other VMware Products 24 Reinstalling Workstation Pro When Upgrading a Windows Host Operating System 24 Installing the Integrated Virtual Debuggers for Eclipse 25 Installing Workstation Pro 25 Install Workstation Pro on a Windows Host 26 Run an Unattended Workstation Pro Installation on a Windows Host 26 Install Workstation Pro on a Linux Host 28 Upgrading Workstation Pro 31 VMware, Inc. -

Linux Crash HOWTO
Linux Crash HOWTO Norman Patten [email protected] 2002−01−30 Revision History Revision 1.0 2002−01−30 Revised by: NM Initial release. This document describes the installation and usage of the LKCD (Linux Kernel Crash Dump) package. Linux Crash HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 1.1. Copyright and License......................................................................................................................1 2. How LKCD Works.........................................................................................................................................2 2.1. What You Need.................................................................................................................................2 3. Installation of lkcd..........................................................................................................................................3 3.1. Installing From Source Code............................................................................................................3 3.2. Building and Installing LKCD Utilities............................................................................................3 3.3. What Gets Installed...........................................................................................................................3 3.4. Installing LKCD Utilities From RPM..............................................................................................3 -

Oracle VM Virtualbox Data Sheet
ORACLE DATA SHEET ORACLE VM VIRTUALBOX KEY FEATURES Oracle VM VirtualBox is cross-platform virtualization software that allows you • Available for Windows, Mac OS X, Linux to extend your existing computer to run multiple operating systems at the same and Oracle Solaris host operating systems time. Designed for IT professionals, Oracle VM VirtualBox runs on Windows, • Supports a wide-range of guest Mac OS X, Linux and Oracle Solaris systems and is ideal for testing, platforms developing, demonstrating and deploying solutions across multiple platforms on • Easy to use graphical user interface one machine. • Powerful, scriptable command-line interface • Import and export virtual machines using OVF/OVA standards • Shared folders between guest vm and host machine • Seamless, resizable, and full screen window display modes • Video and 3D (OpenGL, DirectX) acceleration • Multiple virtual screen support • Powerful and flexible networking options • USB and serial ports • SAS, SATA, SCSI and IDE storage controllers • Built-in iSCSI initiator • Built-in Remote Display Server • Multi-generational branched snapshots • Linked and Full Clones • Controllable Copy-and-Paste • VM Groups Easy to use, Fast and Powerful, Great Platform coverage KEY BENEFITS Designed for use on systems ranging from ultrabooks to high-end server class hardware, • Run almost any type of application on your existing machine Oracle VM VirtualBox is lightweight and easy to install and use. Yet under the deceptively simple exterior lies an extremely fast and powerful virtualization engine. With a formidable • Quickly and easily try out new platforms reputation for speed and agility, Oracle VM VirtualBox contains innovative features to deliver • Create an optimum test and tangible business benefits: significant performance improvements; a more powerful development environment virtualization system; and a wider range of supported guest operating system platforms. -

Embedded Linux Conference Europe 2019
Embedded Linux Conference Europe 2019 Linux kernel debugging: going beyond printk messages Embedded Labworks By Sergio Prado. São Paulo, October 2019 ® Copyright Embedded Labworks 2004-2019. All rights reserved. Embedded Labworks ABOUT THIS DOCUMENT ✗ This document is available under Creative Commons BY- SA 4.0. https://creativecommons.org/licenses/by-sa/4.0/ ✗ The source code of this document is available at: https://e-labworks.com/talks/elce2019 Embedded Labworks $ WHOAMI ✗ Embedded software developer for more than 20 years. ✗ Principal Engineer of Embedded Labworks, a company specialized in the development of software projects and BSPs for embedded systems. https://e-labworks.com/en/ ✗ Active in the embedded systems community in Brazil, creator of the website Embarcados and blogger (Portuguese language). https://sergioprado.org ✗ Contributor of several open source projects, including Buildroot, Yocto Project and the Linux kernel. Embedded Labworks THIS TALK IS NOT ABOUT... ✗ printk and all related functions and features (pr_ and dev_ family of functions, dynamic debug, etc). ✗ Static analysis tools and fuzzing (sparse, smatch, coccinelle, coverity, trinity, syzkaller, syzbot, etc). ✗ User space debugging. ✗ This is also not a tutorial! We will talk about a lot of tools and techniches and have fun with some demos! Embedded Labworks DEBUGGING STEP-BY-STEP 1. Understand the problem. 2. Reproduce the problem. 3. Identify the source of the problem. 4. Fix the problem. 5. Fixed? If so, celebrate! If not, go back to step 1. Embedded Labworks TYPES OF PROBLEMS ✗ We can consider as the top 5 types of problems in software: ✗ Crash. ✗ Lockup. ✗ Logic/implementation error. ✗ Resource leak. ✗ Performance. -

Linux Kernel Debugging Advanced Operating Systems 2020/2021
Linux Kernel Debugging Advanced Operating Systems 2020/2021 Vlastimil Babka Linux Kernel Developer, SUSE Labs [email protected] Agenda – Debugging Scenarios • Debugging production kernels – Post-mortem analysis: interpreting kernel oops/panic output, creating and analyzing kernel crash dumps – Kernel observability – dynamic debug, tracing, alt-sysrq dumps, live crash session • Debugging during individual kernel development – Debug prints – printk() facilitiy – Debugger (gdb) support • Finding (latent) bugs during collaborative development – Optional runtime checks configurable during build – Testing and fuzzing – Static analysis 2 Enterprise Linux Distro and Bugs (incl. Kernel) • The software installation (e.g. ISO) itself is free (and open source, obviously) • Customers pay for support subscription – Delivery of (tested by QA) package updates – fixing known bugs, CVE’s… but not more! – Getting reported bugs fixed • Bugs specific to customer’s workload, hardware, “luck”, large number of machines… • Upstream will also fix reported bugs, but only with latest kernel and no effort guarantees • Dealing with kernel bugs, e.g. crashes – Find out the root cause (buggy code) with limited possibilities (compared to local development) • Typically no direct access to customer’s system or workload • Long turnarounds for providing a modified debug kernel and reproducing the bug – Write and deliver a fix (upstream first!) or workaround; fix goes to next update • Possibly a livepatch in some cases – Is a lot of fun ;-) 3 Kernel Oops - The Real World Example