Online Appendix – NOT for PUBLICATION
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Disfigured History: How the College Board Demolishes the Past
Disfigured History How the College Board Demolishes the Past A report by the Cover design by Beck & Stone; Interior design by Chance Layton 420 Madison Avenue, 7th Floor Published November, 2020. New York, NY 10017 © 2020 National Association of Scholars Disfigured History How the College Board Demolishes the Past Report by David Randall Director of Research, National Assocation of Scholars Introduction by Peter W. Wood President, National Association of Scholars Cover design by Beck & Stone; Interior design by Chance Layton Published November, 2020. © 2020 National Association of Scholars About the National Association of Scholars Mission The National Association of Scholars is an independent membership association of academics and others working to sustain the tradition of reasoned scholarship and civil debate in America’s colleges and universities. We uphold the standards of a liberal arts education that fosters intellectual freedom, searches for the truth, and promotes virtuous citizenship. What We Do We publish a quarterly journal, Academic Questions, which examines the intellectual controversies and the institutional challenges of contemporary higher education. We publish studies of current higher education policy and practice with the aim of drawing attention to weaknesses and stimulating improvements. Our website presents educated opinion and commentary on higher education, and archives our research reports for public access. NAS engages in public advocacy to pass legislation to advance the cause of higher education reform. We file friend-of-the-court briefs in legal cases defending freedom of speech and conscience and the civil rights of educators and students. We give testimony before congressional and legislative committees and engage public support for worthy reforms. -

Fear, Appeasement, and the Effectiveness of Deterrence1
Fear, Appeasement, and the Effectiveness of Deterrence1 Ron Gurantz2 and Alexander V. Hirsch3 June 26, 2015 1We thank Robert Trager, Barry O'Neill, Tiberiu Dragu, Kristopher Ramsay, Robert Powell, Doug Arnold, Mattias Polborn, participants of the UCLA International Relations Reading Group, Princeton Q-APS Interna- tional Relations Conference, and Cowbell working group, and two anonymous reviewers for helpful comments and advice. 2Corresponding Author. University of California, Los Angeles. Department of Political Science, 4289 Bunche Hall, Los Angeles, CA 90095-1472. Phone: (310) 825-4331. Email: [email protected]. 3Associate Professor of Political Science, Division of the Humanities and Social Sciences, California Insti- tute of Technology, MC 228-77, Pasadena, CA 91125. Email: [email protected]. Abstract Governments often fear the future intentions of their adversaries. In this paper we show how this fear can make deterrent threats credible under seemingly incredible circumstances. We consider a model in which a defender seeks to deter a transgression with both intrinsic and military value. We examine how the defender's fear of the challenger's future belligerence affects his willingness to respond to the transgression with war. We derive conditions under which even a very minor transgression effectively \tests" for the challenger's future belligerence, which makes the defender's deterrent threat credible even when the transgression is objectively minor and the challenger is ex- ante unlikely to be belligerent. We also show that fear can actually benefit the defender by allowing her to credibly deter. We show the robustness of our results to a variety of extensions, and apply the model to analyze the Turkish Straits Crisis of 1946. -

Canada in the Cold War
CANADA IN THE COLD WAR Countries in the Cold War Soviet Union/USSR/CCCP/The Motherland/Russia The USSR flag is one of the most iconic flags during the 20th century. Adopted during 1924, this flag would go over a few changes, and would no longer be in use in 1991, when the Soviet Union fell. The Flag has a red backround with a hammer and sickle in the top left corner, with a yellow and red star on top of the hammer and sickle. The hammer and sickle represent workers, peasents, and the victorious revolutionary alliance, while the star represents the Communist Party of the Soviet Union. 1 CANADA IN THE COLD WAR America/US/USA/Merica/The Union The iconic American flag was the capitalist superpower in the Cold War. It was adopted in 1959 by a high schooler who wanted a higher grade. The 50 stars represent the 50 states that are in the Union. The 13 stripes represent the first 13 colonies that took over British lands in North America. 2 CANADA IN THE COLD WAR Canada/CAN/Maple Syrup/The True North/The Dominion of Canada Canada was a key ally of the United States, and was one of the founders of NATO. After no longer being a Dominion of Britain, Canada changes its flag and removes its old one. The flag includes red and white stripes, with a maple leaf in the center. 3 CANADA IN THE COLD WAR UK/United Kingdom/Britain/Great Britain/British Empire The UK was the largest empire in human history, bigger than the Mongol Empire, bigger then the French, and bigger than Russia. -

Remembering George Kennan Does Not Mean Idolizing Him
UNITED STATES InsTITUTE OF PEACE www.usip.org SPECIAL REPORT 1200 17th Street NW • Washington, DC 20036 • 202.457.1700 • fax 202.429.6063 ABOUT THE REPORT Melvyn P. Leffler This report originated while Melvyn P. Leffler was a Jennings Randolph Fellow at the United States Institute of Peace. He was writing his book on what appeared to be the most intractable and ominous conflict of the post–World War II era—the Cold War. He was addressing the questions of why the Cold War lasted as long as it did and why it ended when Remembering it did. As part of the ongoing dialogue at the United States Institute of Peace, he was repeatedly asked about the lessons of the Cold War for our contemporary problems. George Kennan His attention was drawn to the career of George F. Kennan, the father of containment. Kennan was a rather obscure and frustrated foreign service officer at the U.S. embassy in Lessons for Today? Moscow when his “Long Telegram” of February 1946 gained the attention of policymakers in Washington and transformed his career. Leffler reviews Kennan’s legacy and ponders the implications of his thinking for the contemporary era. Is it Summary possible, Leffler wonders, to reconcile Kennan’s legacy with the newfound emphasis on a “democratic peace”? • Kennan’s thinking and policy prescriptions evolved quickly from the time he wrote the Melvyn P. Leffler, a former senior fellow at the United States “Long Telegram” in February 1946 until the time he delivered the Walgreen Lectures Institute of Peace, won the Bancroft Prize for his book at the University of Chicago in 1950. -

The Rise and Fall of Australian Maoism
The Rise and Fall of Australian Maoism By Xiaoxiao Xie Thesis submitted for the degree of Doctor of Philosophy in Asian Studies School of Social Science Faculty of Arts University of Adelaide October 2016 Table of Contents Declaration II Abstract III Acknowledgments V Glossary XV Chapter One Introduction 01 Chapter Two Powell’s Flowing ‘Rivers of Blood’ and the Rise of the ‘Dark Nations’ 22 Chapter Three The ‘Wind from the East’ and the Birth of the ‘First’ Australian Maoists 66 Chapter Four ‘Revolution Is Not a Dinner Party’ 130 Chapter Five ‘Things Are Beginning to Change’: Struggles Against the turning Tide in Australia 178 Chapter Six ‘Continuous Revolution’ in the name of ‘Mango Mao’ and the ‘death’ of the last Australian Maoist 220 Conclusion 260 Bibliography 265 I Declaration I certify that this work contains no material which has been accepted for the award of any other degree or diploma in my name, in any university or other tertiary institution and, to the best of my knowledge and belief, contains no material previously published or written by another person, except where due reference has been made in the text. In addition, I certify that no part of this work will, in the future, be used in a submission in my name, for any other degree or diploma in any university or other tertiary institution without the prior approval of the University of Adelaide and where applicable, any partner institution responsible for the joint-award of this degree. I give consent to this copy of my thesis, when deposited in the University Library, being made available for loan and photocopying, subject to the provisions of the Copyright Act 1968. -

Fear, Appeasement, and the Effectiveness of Deterrence
Fear, Appeasement, and the Effectiveness of Deterrence1 Ron Gurantz2 and Alexander V. Hirsch3 April 1, 2015 1We thank Robert Trager, Barry O'Neill, Tiberiu Dragu, Kristopher Ramsay, Robert Powell, Doug Arnold, Mattias Polborn, participants of the UCLA International Relations Reading Group, Princeton Q-APS International Relations Conference, and Cowbell working group, and two anony- mous reviewers for helpful comments and advice. 2Corresponding Author. University of California, Los Angeles. Department of Political Sci- ence, 4289 Bunche Hall, Los Angeles, CA 90095-1472. Phone: (310) 825-4331. Email: rongu- [email protected]. 3Associate Professor of Political Science, Division of the Humanities and Social Sciences, Cali- fornia Institute of Technology, MC 228-77, Pasadena, CA 91125. Email: [email protected]. Abstract Governments often fear the future intentions of their adversaries. In this paper we explore how this fear affects their willingness to fight, and thus ability to credibly deter, and show that it can make deterrent threats credible under seemingly incredible circumstances. We consider a model in which a defender seeks to deter a transgression that has both intrinsic and military value, and examine how the defender's fear that the challenger will exploit her gains in a future military confrontation affects the credibility of his deterrent threat. We derive conditions under which even a very minor transgression can effectively become a \test" of the challenger's future belligerence. As a result, the defender's deterrent threat of war becomes credible in equilibrium, even when the transgression does not immediately appear to be worth fighting over, and the ex-ante likelihood that the challenger is belligerent is infinitesimally small. -

Turkey As a Nato Ally in the Post-Cold War Period
TALLINN UNIVERISTY OF TECHNOLOGY School of Business and Governance Department of Law Ayberk Bozkurt TURKEY AS A NATO ALLY IN THE POST-COLD WAR PERIOD Master’s thesis Programme of International Relations and European-Asian Studies Supervisor: Peeter Müürsepp, PhD Tallinn 2018 I declare that the I have compiled the paper independently and all works, important standpoints and data by other authors have been properly referenced and the same paper has not been previously been presented for grading. The document length is 11002 words from the introduction to the end of summary. Ayberk Bozkurt …………………………… (signature, date) Student code: 156457TASM Student e-mail address: [email protected] Supervisor: Peeter Müürsepp, PhD: The paper conforms to requirements in force …………………………………………… (signature, date) Chairman of the Defence Committee: /to be added only for graduation theses/ Permitted to the defence ………………………………… (name, signature, date) TABLE OF CONTENTS ABSTRACT.....................................................................................................................................1 INTRODUCTION...........................................................................................................................2 1.THEORETICAL FRAMEWORK AND METHODOLOGY......................................................5 2. WHAT INTERLINKS A NEW TURKEY WITH NATO..........................................................8 2.1. A Historical Brief........................................................................................................10 -

British Foreign Office Perspectives on the Admission of Turkey and Greece to NATO, 1947-1952
1 British Foreign Office Perspectives on the Admission of Turkey and Greece to NATO, 1947-1952 Norasmahani Hussain Submitted in accordance with the requirements for the degree of Doctor of Philosophy The University of Leeds School of History October 2018 2 The candidate confirms that the work submitted is her own and that appropriate credit has been given where reference has been made to the work of others. This copy has been supplied on the understanding that it is copyright material and that no quotation from the thesis may be published without proper acknowledgement. © 2018 The University of Leeds and Norasmahani Hussain The right of Norasmahani Hussain to be identified as Author of this work has been asserted by her in accordance with the Copyright, Designs and Patents Act 1988. 3 ACKNOWLEDGEMENTS I owe a greatest debt of gratitude to my new supervisors Dr Peter Anderson, Dr William Jackson and Dr Elisabeth Leake, also my retired supervisor, Dr Martin Thornton for their immense practical help that enabled me to complete this research. Their invaluable advice, guidance, patience, excellent ideas, constructive comments, kindness, and thoughtfulness, made me feel really grateful for having them as my supervisors. Massive thanks go to my advisor Dr Laura King for her continuing support and encouragement over the years. I would also like to give my thanks to Kementerian Pengajian Tinggi Malaysia and Universiti Sains Malaysia for funding my study in Leeds, United Kingdom. I extend my next gratitude to Professor Simon Ball and Dr James Ellison for their constructive comments during the viva. I express deep sense of gratitude to the School of History, University of Leeds, and its friendly and helpful staffs such as Emma Chippendale, Alice Potter and Maria Di Stefano. -

H-Diplo Roundtable on Acheson: a Life in the Cold
Dean Acheson: A Life in the Cold War Roundtable Review Review by Deborah Larson Reviewed Work: Robert Beisner. Dean Acheson: A Life in the Cold War. Oxford and New York: Oxford University Press, 2006. Roundtable Editor: Thomas Maddux Reviewers: John Earl Haynes, Matthew Jacobs, Deborah Larson, Douglas J. Macdonald, James Matray Stable URL: http://www.h-net.org/~diplo/roundtables/PDF/Beisner-Acheson-Larson.pdf Your use of this H-Diplo roundtable review indicates your acceptance of the H-Diplo and H-Net copyright policies, and terms of condition and use. The following is a plain language summary of these policies: You may redistribute and reprint this work under the following conditions: Attribution: You must include full and accurate attribution to the author(s), web location, date of publication, H-Diplo, and H-Net: Humanities and Social Sciences Online. Nonprofit and education purposes only. You may not use this work for commercial purposes. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions may be waived if you obtain permission from the copyright holder. For such queries, contact the H-Diplo editorial staff at [email protected]. H-Diplo is an international discussion network dedicated to the study of diplomatic and international history (including the history of foreign relations). For more information regarding H-Diplo, please visit http://www.h-net.org/~diplo/. For further information about our parent organization, H-Net: Humanities & Social Sciences Online, please visit http://www.h-net.org/. Copyright © 2007 by H-Diplo, a part of H-Net. -

Russia, NATO, and Black Sea Security for More Information on This Publication, Visit
Russia, NATO, and Black Sea Security Russia, NATO, C O R P O R A T I O N STEPHEN J. FLANAGAN, ANIKA BINNENDIJK, IRINA A. CHINDEA, KATHERINE COSTELLO, GEOFFREY KIRKWOOD, DARA MASSICOT, CLINT REACH Russia, NATO, and Black Sea Security For more information on this publication, visit www.rand.org/t/RRA357-1 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-1-9774-0568-5 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2020 RAND Corporation R® is a registered trademark. Cover: Cover graphic by Dori Walker, adapted from a photo by Petty Officer 3rd Class Weston Jones. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface The Black Sea region is a central locus of the competition between Russia and the West for the future of Europe. -
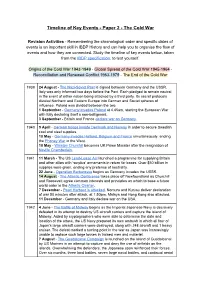
Timeline of Key Events - Paper 2 - the Cold War
Timeline of Key Events - Paper 2 - The Cold War Revision Activities - Remembering the chronological order and specific dates of events is an important skill in IBDP History and can help you to organise the flow of events and how they are connected. Study the timeline of key events below, taken from the IBDP specification, to test yourself. Origins of the Cold War 1943-1949 - Global Spread of the Cold War 1945-1964 - Reconciliation and Renewed Conflict 1963-1979 - The End of the Cold War 1939 24 August - The Nazi-Soviet Pact is signed between Germany and the USSR. Italy was only informed two days before the Pact. Each pledged to remain neutral in the event of either nation being attacked by a third party. Its secret protocols divided Northern and Eastern Europe into German and Soviet spheres of influence. Poland was divided between the two. 1 September - Germany invades Poland at 4.45am, starting the European War with Italy declaring itself a non-belligerent. 3 September - Britain and France declare war on Germany. 1940 9 April - German troops invade Denmark and Norway in order to secure Swedish coal and steel supplies. 10 May - Germany invades Holland, Belgium and France simultaneously, ending the Phoney War in the West. 10 May - Winston Churchill becomes UK Prime Minister after the resignation of Neville Chamberlain. 1941 11 March - The US Lend-Lease Act launched a programme for supplying Britain and other allies with ‘surplus’ armaments in return for bases. Over $50 billion in supplies were given, ending any pretense of neutrality. 22 June - Operation Barbarossa begins as Germany invades the USSR. -

On the Ships That Passed Through the Bosphorus, Moving House Shahzad Chowdhary M, Phil Scholar
Pratidhwani the Echo A Peer-Reviewed International Journal of Humanities & Social Science ISSN: 2278-5264 (Online) 2321-9319 (Print) Impact Factor: 6.28 (Index Copernicus International) Volume-VI, Issue-II, October 2017, Page No. 262-267 Published by Dept. of Bengali, Karimganj College, Karimganj, Assam, India Website: http://www.thecho.in On the Ships that Passed Through the Bosphorus, Moving House Shahzad Chowdhary M, Phil Scholar. Department of Political Science, Central University of Haryana Liyaquit Ali Ph. D Scholar, Dept. of English Literature, Barkatullah University, Bhopal, Madhya Pradesh Abstract The Bosporus: Factors contributing to Marine causalities. Ships trade in a complex and high risk operating environment, hence very many shipping casualties still occur at sea as well as waters connected therewith any accident, whatever in nature, are very seafarers nightmare and comes under the fierce scrutiny of the public. It may take different shapes i.e. from a single operational mishap to a possible major regional catastrophe. Where the shipping traffic is dense, the sea room is relatively insufficient and depth of water is rather restricted, serious risk are likely to be faced several came may give rise to shipping casualty. Inter alia, natural conditions, technical failures, route conditions, ship-related factors and human errors. The strait of Istanbul, the Bosporus, is roughly an s- shaped narrow channel and links the Black sea to the Sea of Marmara. It is thus the integrated part of the Turkish straits, namely the Dardanelles, the Sea of Marmara and the Bosporus, the whole area being known as the Turkish straits region, which constitute one of the major and busiest seaways.