The Multi-Principal OS Construction of the Gazelle Web Browser
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

On the Uniqueness of Browser Extensions and Web Logins
To Extend or not to Extend: on the Uniqueness of Browser Extensions and Web Logins Gábor György Gulyás Dolière Francis Somé INRIA INRIA [email protected] [email protected] Nataliia Bielova Claude Castelluccia INRIA INRIA [email protected] [email protected] ABSTRACT shown that a user’s browser has a number of “physical” charac- Recent works showed that websites can detect browser extensions teristics that can be used to uniquely identify her browser and that users install and websites they are logged into. This poses sig- hence to track it across the Web. Fingerprinting of users’ devices is nificant privacy risks, since extensions and Web logins that reflect similar to physical biometric traits of people, where only physical user’s behavior, can be used to uniquely identify users on the Web. characteristics are studied. This paper reports on the first large-scale behavioral uniqueness Similar to previous demonstrations of user uniqueness based on study based on 16,393 users who visited our website. We test and their behavior [23, 50], behavioral characteristics, such as browser detect the presence of 16,743 Chrome extensions, covering 28% settings and the way people use their browsers can also help to of all free Chrome extensions. We also detect whether the user is uniquely identify Web users. For example, a user installs web connected to 60 different websites. browser extensions she prefers, such as AdBlock [1], LastPass [14] We analyze how unique users are based on their behavior, and find or Ghostery [8] to enrich her Web experience. Also, while brows- out that 54.86% of users that have installed at least one detectable ing the Web, she logs into her favorite social networks, such as extension are unique; 19.53% of users are unique among those who Gmail [13], Facebook [7] or LinkedIn [15]. -

Blogger.Com User Guide
Blogger.com User Guide Version 4 Written by: Todd W. Jorns [email protected] Table of Contents Introduction ............................................................................................................................. 1 Create a Google Account ........................................................................................................ 2 Name Your Blog ....................................................................................................................... 3 Choose a Starter Template ..................................................................................................... 4 Posting Tab New Post ............................................................................................................................ 6 Edit Post ............................................................................................................................. 7 Published Successfully ....................................................................................................... 9 Settings Tab Basics ............................................................................................................................. 10 Publishing ........................................................................................................................ 11 Formatting ........................................................................................................................ 12 Design Tab Page Elements ............................................................................................................... -

Picasa.Google.Com
in the classroom Get the tool: http://picasa.google.com What is it? Picasa is a free application that helps you instantly organize, edit, publish, and share all the pictures on your PC or Mac. With Picasa you can even create a collage or movie with an album or series of photos. Picasa also makes powerful photo editing simple. Picasa Web Albums allows photos from Picasa (or iPhoto via a plug-in, on a Mac) to be uploaded to the web quickly and easily. Why use it? Students can use Picasa to: ● Store, edit, and publish their photographic work. ● Create slideshows from a series of images. ● Create collages around a general or specific topic. ● Collaborate with other students on a photo album based upon a topic/theme. Teachers can use Picasa to: ● Create a repository of images for curricular use. ● Set up an album of school buildings so that students can use the photos for image textures in Google Sketchup. ● Make sure every student gets their face in the yearbook using Picasa’s face recognition feature to match names with faces. ● Post instructional videos. Expert Tip You can take full advantage of Picasa’s mobile integration. Photos can be posted to an album from a mobile device via email or your Android device. Instructional Ideas Elementary. Students can create a collage to represent a theme or concept, such as a collage of nouns. For Specially Designed Academic Instruction in English (SDAIE) students can tag images uploaded by the teacher and/or classmates. Middle School. Students can create a movie to digitally tell a story such as a Photo Five in which five sequential images are put together to tell a visual story. -

What Is Dart?
1 Dart in Action By Chris Buckett As a language on its own, Dart might be just another language, but when you take into account the whole Dart ecosystem, Dart represents an exciting prospect in the world of web development. In this green paper based on Dart in Action, author Chris Buckett explains how Dart, with its ability to either run natively or be converted to JavaScript and coupled with HTML5 is an ideal solution for building web applications that do not need external plugins to provide all the features. You may also be interested in… What is Dart? The quick answer to the question of what Dart is that it is an open-source structured programming language for creating complex browser based web applications. You can run applications created in Dart by either using a browser that directly supports Dart code, or by converting your Dart code to JavaScript (which happens seamlessly). It is class based, optionally typed, and single threaded (but supports multiple threads through a mechanism called isolates) and has a familiar syntax. In addition to running in browsers, you can also run Dart code on the server, hosted in the Dart virtual machine. The language itself is very similar to Java, C#, and JavaScript. One of the primary goals of the Dart developers is that the language seems familiar. This is a tiny dart script: main() { #A var d = “Dart”; #B String w = “World”; #C print(“Hello ${d} ${w}”); #D } #A Single entry point function main() executes when the script is fully loaded #B Optional typing (no type specified) #C Static typing (String type specified) #D Outputs “Hello Dart World” to the browser console or stdout This script can be embedded within <script type=“application/dart”> tags and run in the Dartium experimental browser, converted to JavaScript using the Frog tool and run in all modern browsers, or saved to a .dart file and run directly on the server using the dart virtual machine executable. -

Using Replicated Execution for a More Secure and Reliable Web Browser
Using Replicated Execution for a More Secure and Reliable Web Browser Hui Xue Nathan Dautenhahn Samuel T. King University of Illinois at Urbana Champaign huixue2, dautenh1, kingst @uiuc.edu { } Abstract Unfortunately, hackers actively exploit these vulnerabil- ities as indicated in reports from the University of Wash- Modern web browsers are complex. They provide a ington [46], Microsoft [61], and Google [49, 48]. high-performance and rich computational environment Both industry and academia have improved the se- for web-based applications, but they are prone to nu- curity and reliability of web browsers. Current com- merous types of security vulnerabilities that attackers modity browsers make large strides towards improving actively exploit. However, because major browser plat- the security and reliability of plugins by using sandbox- forms differ in their implementations they rarely exhibit ing techniques to isolate plugins from the rest of the the same vulnerabilities. browser [62, 33]. However, these browsers still scatter In this paper we present Cocktail, a system that uses security logic throughout millions of lines of code, leav- three different off-the-shelf web browsers in parallel to ing these systems susceptible to browser-based attacks. provide replicated execution for withstanding browser- Current research efforts, like Tahoma [32], the OP web based attacks and improving browser reliability. Cock- browser [36], the Gazelle web browser [59], and the Illi- tail mirrors inputs to each replica and votes on browser nois Browser Operating System [58] all propose build- states and outputs to detect potential attacks, while con- ing new web browsers to improve security. Although tinuing to run. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Lime Rock Gazette
L 1M E R 0 C K GAZETTE. DEVOTED TO COMMERCE, AGRICULTURE, ART, SCIENCE, MORALITY AND GENERAL INTELLIGENCE. PUBLISHED WEEKLY, BY RICHARDSON & PORTER. Tpiihs, $1,50 in Advance, $1.75 in six monllis $2.00 afleiv-Adverliseinenls inserted al Hie ciisloniarv prices VOL J- LAST—TIIOIIASTOV, TlllltSO AV 1IOILVIA«L O< TOK I it 15. 1840 AO. »». i.j_ - xi u f c i . b.w rjw vjwcyxayztt i TIlC Relllllied Pastor. *,o,n v*cw> nn,l 0,1 *Gc morning of the 'themselves together for family worship.— from nine o’clock in the morning to three 'Aint I a man now. Miss Tabitha, I ’d only, however, who knew the former level- twenty-second of the same month he look- Ho was told that twenty missionaries might I in the nOcrnoon; and from live to nine in like to know ,’ said Jotliam , rising with ness o f the spot. Ct will be recollected By many ol otn renders, that (,d ,|p0„ ,bc s|,((1.es of England—on the find employment there. the eveninu. There were twelve hundred spirit and putting his hat on his head, ‘ I f The Lieutenant, who had c ritic a lly the Kcv. Mr. Vomroy, Tastor ot the livst ( j following day ho landed. He wished to; Mr. l’omroy enumerated the places of | persons composing the convention, about I aint a man now. and a whole hog o f a watched the manoeuvring of the men, grognltonnl Church ol Bangor, lelt his people see ns much of the land of our fathers as interest ho visited in the Holy Land.— nine hundred of whom were clergymen, one too, I think it darned strange.’ congratulated the Orderly on the perfec- sonic sixteen months Since, for an European possible— a land that should lie dear to ! Sidon, Sarepta, Tyre. -

Creating a Website Using Google Blogger
Creating a Website Using Google Blogger 1. Getting Ready to Use Blogger a. Create a Google email address and account by clicking on https://www.google.com/ then Sign In, then Create Account b. Fill in a few items in your Google + profile c. Study the section at the end of this document that defines a few terms we will use 2. Getting Ready to Create a Website a. Think about what you want your website to do b. What will be the titles of the pages you will have? c. What will go on the pages? 1. Create a folder for images that you will use – add some images (use Google Photos?) 2. Create a folder for text or articles you will use – add an article (use Google Drive?) d. Think about what your web address (URL) will be – like example.blogspot.com 3. Creating a Website a. Sign in to Google b. Enter Blogger (type Blogger in the address bar of your browser or click on the Google Apps icon in the upper right of a Google search page) – sign in c. Click on New Blog 1. Enter a Title for your blog – this text will be at the top of your web pages 2. Choose a blog address, or URL. This will be used by readers to view your blog. 3. Choose Picture Window template for now (see below for more on templates) 4. Click Create blog a. Choose Google + profile b. Click No Thanks to finding a domain name – we'll use the free one on blogspot c. -

Introduction to Web 2.0 Technologies
Introduction to Web 2.0 Joshua Stern, Ph.D. Introduction to Web 2.0 Technologies What is Web 2.0? Æ A simple explanation of Web 2.0 (3 minute video): http://www.youtube.com/watch?v=0LzQIUANnHc&feature=related Æ A complex explanation of Web 2.0 (5 minute video): http://www.youtube.com/watch?v=nsa5ZTRJQ5w&feature=related Æ An interesting, fast-paced video about Web.2.0 (4:30 minute video): http://www.youtube.com/watch?v=NLlGopyXT_g Web 2.0 is a term that describes the changing trends in the use of World Wide Web technology and Web design that aim to enhance creativity, secure information sharing, increase collaboration, and improve the functionality of the Web as we know it (Web 1.0). These have led to the development and evolution of Web-based communities and hosted services, such as social-networking sites (i.e. Facebook, MySpace), video sharing sites (i.e. YouTube), wikis, blogs, etc. Although the term suggests a new version of the World Wide Web, it does not refer to any actual change in technical specifications, but rather to changes in the ways software developers and end- users utilize the Web. Web 2.0 is a catch-all term used to describe a variety of developments on the Web and a perceived shift in the way it is used. This shift can be characterized as the evolution of Web use from passive consumption of content to more active participation, creation and sharing. Web 2.0 Websites allow users to do more than just retrieve information. -

The Multi-Principal OS Construction of the Gazelle Web Browser
The Multi-Principal OS Construction of the Gazelle Web Browser Helen J. Wang, Chris Grier, Alex Moshchuk, Sam King, Piali Choudhury, Herman Venter Browser as an application platform • Single stop for many computing needs – banking, shopping, office tasks, social networks, entertainment • Static document browsing rich programs – obtained from mutually distrusting origins – same-origin policy: a browser is a multi-principal platform where web sites are principals • Browser = prime target of today’s attackers Your valuables are online! • Existing browser security mentality: – valuables on local machine – protect local machine from the web Browser OS • This work’s mentality: – valuables online – must also protect web site principals from one another Browser OS Browser design requires OS thinking • Cross-principal protection is an essential function of an operating system • Fundamental flaw with existing browser designs: – OS logic is intermingled with application-specific content processing – consequences: HTML • unreliable cross-principal protection JS engine parsing • many vulnerabilities DOM same-origin rendering protection Persistent network state access browser Gazelle • An OS exclusively manages: HTML JS engine – protection across principals parsing DOM – resource allocation same-origin – resource access control rendering protection Persistent network state access • Our approach for designing Gazelle: Browser kernel – take all OS functionality out of content processing logic – put it into a small, simple browser kernel Gazelle • Build -
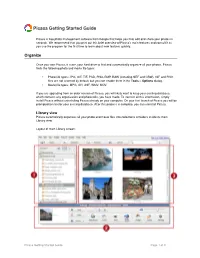
Picasa Getting Started Guide
Picasa Getting Started Guide Picasa is free photo management software from Google that helps you find, edit and share your photos in seconds. We recommend that you print out this brief overview of Picasa's main features and consult it as you use the program for the first time to learn about new features quickly. Organize Once you start Picasa, it scans your hard drive to find and automatically organize all your photos. Picasa finds the following photo and movie file types: • Photo file types: JPG, GIF, TIF, PSD, PNG, BMP, RAW (including NEF and CRW). GIF and PNG files are not scanned by default, but you can enable them in the Tools > Options dialog. • Movie file types: MPG, AVI, ASF, WMV, MOV. If you are upgrading from an older version of Picasa, you will likely want to keep your existing database, which contains any organization and photo edits you have made. To transfer all this information, simply install Picasa without uninstalling Picasa already on your computer. On your first launch of Picasa you will be prompted to transfer your existing database. After this process is complete, you can uninstall Picasa. Library view Picasa automatically organizes all your photo and movie files into collections of folders inside its main Library view. Layout of main Library screen: Picasa Getting Started Guide Page 1 of 9 Folder list The left-hand list in Picasa's Library view shows all the folders containing photos on your computer and all the albums you've created in Picasa. These folders and albums are grouped into collections that are described in the next section.