Maritime Cybersecurity in the Western Hemisphere Guidelines
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
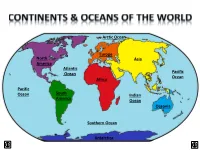
North America Other Continents
Arctic Ocean Europe North Asia America Atlantic Ocean Pacific Ocean Africa Pacific Ocean South Indian America Ocean Oceania Southern Ocean Antarctica LAND & WATER • The surface of the Earth is covered by approximately 71% water and 29% land. • It contains 7 continents and 5 oceans. Land Water EARTH’S HEMISPHERES • The planet Earth can be divided into four different sections or hemispheres. The Equator is an imaginary horizontal line (latitude) that divides the earth into the Northern and Southern hemispheres, while the Prime Meridian is the imaginary vertical line (longitude) that divides the earth into the Eastern and Western hemispheres. • North America, Earth’s 3rd largest continent, includes 23 countries. It contains Bermuda, Canada, Mexico, the United States of America, all Caribbean and Central America countries, as well as Greenland, which is the world’s largest island. North West East LOCATION South • The continent of North America is located in both the Northern and Western hemispheres. It is surrounded by the Arctic Ocean in the north, by the Atlantic Ocean in the east, and by the Pacific Ocean in the west. • It measures 24,256,000 sq. km and takes up a little more than 16% of the land on Earth. North America 16% Other Continents 84% • North America has an approximate population of almost 529 million people, which is about 8% of the World’s total population. 92% 8% North America Other Continents • The Atlantic Ocean is the second largest of Earth’s Oceans. It covers about 15% of the Earth’s total surface area and approximately 21% of its water surface area. -

Geography Notes.Pdf
THE GLOBE What is a globe? a small model of the Earth Parts of a globe: equator - the line on the globe halfway between the North Pole and the South Pole poles - the northern-most and southern-most points on the Earth 1. North Pole 2. South Pole hemispheres - half of the earth, divided by the equator (North & South) and the prime meridian (East and West) 1. Northern Hemisphere 2. Southern Hemisphere 3. Eastern Hemisphere 4. Western Hemisphere continents - the largest land areas on Earth 1. North America 2. South America 3. Europe 4. Asia 5. Africa 6. Australia 7. Antarctica oceans - the largest water areas on Earth 1. Atlantic Ocean 2. Pacific Ocean 3. Indian Ocean 4. Arctic Ocean 5. Antarctic Ocean WORLD MAP ** NOTE: Our textbooks call the “Southern Ocean” the “Antarctic Ocean” ** North America The three major countries of North America are: 1. Canada 2. United States 3. Mexico Where Do We Live? We live in the Western & Northern Hemispheres. We live on the continent of North America. The other 2 large countries on this continent are Canada and Mexico. The name of our country is the United States. There are 50 states in it, but when it first became a country, there were only 13 states. The name of our state is New York. Its capital city is Albany. GEOGRAPHY STUDY GUIDE You will need to know: VOCABULARY: equator globe hemisphere continent ocean compass WORLD MAP - be able to label 7 continents and 5 oceans 3 Large Countries of North America 1. United States 2. Canada 3. -

Indigenous Peoples in Latin America: Statistical Information
Indigenous Peoples in Latin America: Statistical Information Updated August 5, 2021 Congressional Research Service https://crsreports.congress.gov R46225 SUMMARY R46225 Indigenous Peoples in Latin America: Statistical August 5, 2021 Information Carla Y. Davis-Castro This report provides statistical information on Indigenous peoples in Latin America. Data and Research Librarian findings vary, sometimes greatly, on all topics covered in this report, including populations and languages, socioeconomic data, land and natural resources, human rights and international legal conventions. For example the figure below shows four estimates for the Indigenous population of Latin America ranging from 41.8 million to 53.4 million. The statistics vary depending on the source methodology, changes in national censuses, the number of countries covered, and the years examined. Indigenous Population and Percentage of General Population of Latin America Sources: Graphic created by CRS using the World Bank’s LAC Equity Lab with webpage last updated in July 2021; ECLAC and FILAC’s 2020 Los pueblos indígenas de América Latina - Abya Yala y la Agenda 2030 para el Desarrollo Sostenible: tensiones y desafíos desde una perspectiva territorial; the International Bank for Reconstruction and Development and World Bank’s (WB) 2015 Indigenous Latin America in the twenty-first century: the first decade; and ECLAC’s 2014 Guaranteeing Indigenous people’s rights in Latin America: Progress in the past decade and remaining challenges. Notes: The World Bank’s LAC Equity Lab -

The New Strategic Framework of the United States for the Western Hemisphere Visit the WEBSITE Receive the E-NEWSLETTER
Analysis Paper 33/2020 21 October 2020 Andrés González Martín The New Strategic Framework of the United States for the Western Hemisphere Visit the WEBSITE Receive the E-NEWSLETTER The New Strategic Framework of the United States for the Western Hemisphere Abstract: Three months before the North American presidential elections, the president of the National Security Council (NSC), Robert O'Brien, presented the new strategic framework for the Western Hemisphere in Florida. Interestingly, the region is the only one that has concerned NSC public diplomacy so much to publish an area development document of the 2017 National Security Strategy. In principle, this special treatment of Latin America is surprising. Especially when the great novelty of 2017 was the express recognition of China and Russia as powers that challenge the power, influence and interest of the United States. However, when it is discovered what is new about the document with respect to the positions of previous administrations, everything ends up falling into place. In Latin America external everything is complicated because there are "adversary countries that exert an evil influence". Keywords: Western Hemisphere, Chinese Communist Party, predatory practices, debt trap, “Growth in the Americas”, "Back to the Americas", Inter-American Development Bank (IDB). *NOTE: The ideas contained in the Analysis Papers are the responsibility of their authors. They do not necessarily reflect the thinking of the IEEE or the Ministry of Defense. Analysis Paper 33/2020 1 The New Strategic Framework of the United States for the Western Hemisphere Andrés González Martín El nuevo marco estratégico de los Estados Unidos para el hemisferio occidental Resumen: Tres meses antes de las elecciones presidenciales norteamericanas, el presidente del Consejo de Seguridad Nacional (NSC), Robert O’Brien, presento en Florida el nuevo marco estratégico del hemisferio occidental. -

Central America-United States Free United States
Administration of George W. Bush, 2005 / June 23 1061 CAFTA would continue the current trade ing about. That’s why they’re standing up benefits. That means good jobs and higher here and saying with common voice to the labor standards for their workers. And be- United States Congress, ‘‘Let’s get this bill cause of reduced tariffs on U.S. goods, con- passed.’’ See, CAFTA is more than a trade sumers in these countries would have access agreement; it is a signal of our Nation’s com- to better goods at lower prices. And that mitment to democracy and prosperity for the brings us a step closer to our goal of an Amer- entire Western Hemisphere. And I urge, and icas where the opportunities in San Jose, we urge, the United States Congress to pass Costa Rica, are as real as they are in San CAFTA. Jose, California. Thanks for coming. People have got to understand that by pro- moting policy that will help generate wealth NOTE: The President spoke at 1:43 p.m. in Room in Central America, we’re promoting policy 450 of the Dwight D. Eisenhower Executive Of- that will mean someone is less—more likely fice Building. The Office of the Press Secretary to stay at home to find a job. If you’re con- also released a Spanish language transcript of cerned about immigration to this country, these remarks. then you must understand that CAFTA and the benefits of CAFTA will help create new opportunity in Central American countries, Message to the Congress which will mean someone will be able to find Transmitting Legislation and good work at home, somebody will be able Supporting Documents To to provide for their family at home, as op- Implement the Dominican Republic- posed to having to make the long trip to the Central America-United States Free United States. -

Preferential Trade Agreements in the Western Hemisphere
Apuntes 51 Preferential Trade Agreements in the Western Hemisphere Fernando González-Vigil* Resumen En este trabajo se analiza la proliferación de acuerdos comerciales preferenciales en el continente americano, las principales razones económicas y políticas que motivan la suscripción de estos acuerdos, y los cambios ocurridos desde la década de los sesenta en los modelos de integración y países que han liderado el proceso de regionalismo en el continente. El artículo detalla los principales logros de este proceso durante la década de los noventa, tanto en el plano comercial y de inversiones como en términos de convergencia hacia compromi- sos de apertura y liberalización amplios y estables. En tal contexto se examina la evolución de las negociaciones para el ALCA y se hacen planteamientos de mucha actualidad sobre las implicancias de esas negociaciones y las de los acuerdos bilaterales o plurilaterales con Estados Unidos, respecto a la construc- ción de la zona de libre comercio continental y a la coexistencia de esta con acuerdos subregionales de integración más profunda, con acuerdos comerciales regionales en otras partes del mundo y con el sistema multilateral de comercio. Abstract This article analyzes the proliferation of preferential trade agreements in the Western Hemisphere, the main economic and political motivations behind them and the changes that have occurred since the sixties in integration models and countries leading the regionalism process in the hemisphere. The article scrutinizes the main achievements of this process both at the level of trade and investment flows and patterns as in terms of a convergence towards wide and stable commitments to openness and liberalization. -

A NEW ENERGY STRATEGY for the WESTERN HEMISPHERE by David L
A NEW ENERGY STRATEGY FOR THE WESTERN HEMISPHERE by David L. Goldwyn Atlantic Council ADRIENNE ARSHT LATIN AMERICA CENTER The Adrienne Arsht Latin America Center broadens understanding of regional transformations through high-impact work that shapes the conversation among policymakers, the business community, and civil society. The Center focuses on Latin America’s strategic role in a global context with a priority on pressing political, economic, and social issues that will define the trajectory of the region now and in the years ahead. Select lines of programming include: Venezuela’s crisis; Mexico-US and global ties; China in Latin America; Colombia’s future; a changing Brazil; Central America’s trajectory; combating disinformation; shifting trade patterns; and leveraging energy resources. Atlantic Council GLOBAL ENERGY CENTER The Global Energy Center promotes energy security by working alongside government, industry, civil society, and public stakeholders to devise pragmatic solutions to the geopolitical, sustainability, and economic challenges of the changing global energy landscape. Cover: The Western Hemisphere at night in 2016, compiled using the Suomi National Polar-orbiting Partnership’s (Suomi-NPP) Visible Infrared Imaging Radiometer Suite (VIIRS) data from NASA Goddard Space Flight Center’s Miguel Román. NASA Earth Observatory/ Joshua Stevens This report is written and published in accordance with the Atlantic Council Policy on Intellectual Independence. The authors are solely responsible for its analysis and recommendations. The Atlantic Council and its donors do not determine, nor do they necessarily endorse or advocate for, any of this report’s conclusions. Atlantic Council 1030 15th Street NW, 12th Floor Washington, DC 20005 For more information, please visit www.AtlanticCouncil.org. -

Factors Contributing to the European Discovery of Lands in the Western Hemisphere
Factors contributing to the European discovery of lands in the Western Hemisphere 1. Demand for gold, spices, and natural resources in Europe 2. Support for the diffusion of Christianity 3. Political and economic competition between European empires 4. Innovations of European and Islamic origins in navigational arts 5. Pioneering role of Prince Henry the Navigator Factors contributing to the European discovery of lands in the Western Hemisphere 1. Demand for gold, spices, and natural resources in Europe Introduced to luxury items during Crusades (1096-1270) 1st Spices from the east (Asia): nutmeg, ginger, cinnamon & pepper 2nd Gold and Silver from the west (Americas) Natural resources from both Factors contributing to the European discovery of lands in the Western Hemisphere 2. Support for the diffusion of Christianity European hostility from Crusades Conversion of non-Christians in Asia and later Native Americans (forced when Europeans go west) Factors contributing to the European discovery of lands in the Western Hemisphere 3. Political and economic competition between European empires Portugal 1st led Europe in trade to Asia; Vasco da Gama to Calicut, India Spain 1st led Europe in trade to Americas; Columbus to the Caribbean Islands (Hispaniola); thought in Asia Treaty of Tordesillas: signed in 1494, divided the new world between Portugal (Brazil) & Spain (rest of Americas) Factors contributing to the European discovery of lands in the Western Hemisphere 4. Innovations of European and Islamic origins in navigational arts. Caravel (ship) had lateen (triangular) sails to sail into wind (tacking) Mariner’s Astrolabe (Muslim): uses the sun, planets, and stars to figure out latitude (north & south) Magnetic Compass (Chinese) Factors contributing to the European discovery of lands in the Western Hemisphere 5. -

CHAPTER 4 EARLY SOCIETIES in the AMERICAS and OCEANIA 69 G 11/ F of M C \I C O ' C Hi Ch~N B A
n early September of the year 683 C. E., a Maya man named Chan Bahlum grasped a sharp obsidian knife and cut three deep slits into the skin of his penis. He insert ed into each slit a strip of paper made from beaten tree bark so as to encourage a continuing flow of blood. His younger brother Kan Xu I performed a similar rite, and other members of his family also drew blood from their own bodies. The bloodletting observances of September 683 c.E. were political and religious rituals, acts of deep piety performed as Chan Bahlum presided over funeral services for his recently deceased father, Pacal, king of the Maya city of Palenque in the Yu catan peninsula. The Maya believed that the shedding of royal blood was essential to the world's survival. Thus, as Chan Bahlum prepared to succeed his father as king of Palenque, he let his blood flow copiously. Throughout Mesoamerica, Maya and other peoples performed similar rituals for a millennium and more. Maya rulers and their family members regularly spilled their own blood. Men commonly drew blood from the penis, like Chan Bahlum, and women often drew from the tongue. Both sexes occasionally drew blood also from the earlobes, lips, or cheeks, and they sometimes increased the flow by pulling long, thick cords through their wounds. According to Maya priests, the gods had shed their own blood to water the earth and nourish crops of maize, and they expected human beings to honor them by imitating their sacrifice. By spilling human blood the Maya hoped to please the gods and ensure that life-giving waters would bring bountiful harvests to their fields. -

Ring of Fire Proposed RMP and Final EIS- Volume 1 Cover Page
U.S. Department of the Interior Bureau of Land Management N T OF M E TH T E R A IN P T E E D R . I O S R . U M 9 AR 8 4 C H 3, 1 Ring of Fire FINAL Proposed Resource Management Plan and Final Environmental Impact Statement and Final Environmental Impact Statement and Final Environmental Management Plan Resource Proposed Ring of Fire Volume 1: Chapters 1-3 July 2006 Anchorage Field Office, Alaska July 200 U.S. DEPARTMENT OF THE INTERIOR BUREAU OF LAND MANAGEMMENT 6 Volume 1 The Bureau of Land Management Today Our Vision To enhance the quality of life for all citizens through the balanced stewardship of America’s public lands and resources. Our Mission To sustain the health, diversity, and productivity of the public lands for the use and enjoyment of present and future generations. BLM/AK/PL-06/022+1610+040 BLM File Photos: 1. Aerial view of the Chilligan River north of Chakachamna Lake in the northern portion of Neacola Block 2. OHV users on Knik River gravel bar 3. Mountain goat 1 4. Helicopter and raft at Tsirku River 2 3 4 U.S. Department of the Interior Bureau of Land Management Ring of Fire Proposed Resource Management Plan and Final Environmental Impact Statement Prepared By: Anchorage Field Office July 2006 United States Department of the Interior BUREAU OF LAND MANAGEMENT Alaska State Office 222 West Seventh Avenue, #13 Anchorage, Alaska 995 13-7599 http://www.ak.blm.gov Dear Reader: Enclosed for your review is the Proposed Resource Management Plan and Final Environmental Impact Statement (Proposed RMPIFinal EIS) for the lands administered in the Ring of Fire by the Bureau of Land Management's (BLM's) Anchorage Field Office (AFO). -

Overview of US Interests in the Western Hemisphere: Opportunities and Challenges"
OVERVIEW OF U.S. INTERESTS IN THE WESTERN HEMISPHERE: OPPORTUNITIES AND CHALLENGES HEARING BEFORE THE SUBCOMMITTEE ON THE WESTERN HEMISPHERE OF THE COMMITTEE ON FOREIGN AFFAIRS HOUSE OF REPRESENTATIVES ONE HUNDRED THIRTEENTH CONGRESS FIRST SESSION FEBRUARY 28, 2013 Serial No. 113–13 Printed for the use of the Committee on Foreign Affairs ( Available via the World Wide Web: http://www.foreignaffairs.house.gov/ or http://www.gpo.gov/fdsys/ U.S. GOVERNMENT PRINTING OFFICE 79–582PDF WASHINGTON : 2013 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate 0ct 09 2002 16:57 May 09, 2013 Jkt 000000 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 F:\WORK\_WH\022813\79582 HFA PsN: SHIRL COMMITTEE ON FOREIGN AFFAIRS EDWARD R. ROYCE, California, Chairman CHRISTOPHER H. SMITH, New Jersey ELIOT L. ENGEL, New York ILEANA ROS-LEHTINEN, Florida ENI F.H. FALEOMAVAEGA, American DANA ROHRABACHER, California Samoa STEVE CHABOT, Ohio BRAD SHERMAN, California JOE WILSON, South Carolina GREGORY W. MEEKS, New York MICHAEL T. MCCAUL, Texas ALBIO SIRES, New Jersey TED POE, Texas GERALD E. CONNOLLY, Virginia MATT SALMON, Arizona THEODORE E. DEUTCH, Florida TOM MARINO, Pennsylvania BRIAN HIGGINS, New York JEFF DUNCAN, South Carolina KAREN BASS, California ADAM KINZINGER, Illinois WILLIAM KEATING, Massachusetts MO BROOKS, Alabama DAVID CICILLINE, Rhode Island TOM COTTON, Arkansas ALAN GRAYSON, Florida PAUL COOK, California JUAN VARGAS, California GEORGE HOLDING, North Carolina BRADLEY S. SCHNEIDER, Illinois RANDY K. -

Trafficking in Persons to Europe for Sexual Exploitation
Vienna International Centre, PO Box 500, 1400 Vienna, Austria Tel.: (+43-1) 26060-0, Fax: (+43-1) 26060-5866, www.unodc.org Traffi cking in Persons to Europe for sexual exploitation Chapter extracted from “The Globalization of Crime — A Transnational Organized Crime Threat Assessment” Report. This report has not been formally edited. The contents of this report do not necessarily reflect the views or policies of UNODC or contributory organiza- tions and neither do they imply any endorsement. The designations employed and the presentation of material in this report do not imply the expression of any opinion whatsoever on the part of UNODC concerning the legal status of any country, territory or city or its authorities, or concerning the delimitation of its frontiers and boundaries. Cover poto: A. Scotti for UN.GIFT/UNODC To Europe1 for sexual exploitation Route Source: World (main origin: the Balkans and former Soviet Union) Vector to destination: Mainly by land, also sea and air Destination: West and Central Europe Dimensions Annual flow of new victims: About 70,000 victims (based on two-year turnover) Volume of market (stock): About 140,000 victims Value of market (stock): US$3 billion per year Traffickers Groups involved: Western European, Balkan, Eastern European, North African, Turkish, Nigerian and Chinese groups Residence of traffickers: Origin and destination countries Threat Estimated trend: Stable Potential effects: Human rights violations Likelihood of effects being realized: Very high 1 T RAFFICKING IN PERSONS What is the nature of the market? Portugal, France, the Netherlands, Germany, Aus- tria and Switzerland.2 Almost all of this trafficking A greater variety of nationalities has been found is for the purpose of sexual exploitation and it among human trafficking victims in West and Cen- includes transgender victims.3 Among South Amer- tral Europe than in any other part of the world, and icans, Brazilian victims have been increasingly most of these victims (84%) were trafficked for the detected in Europe.