Relational Learning Analysis of Social Politics Using Knowledge Graph Embedding
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Book 9 24, 25 and 26 June 2014
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE COUNCIL FIFTY-SEVENTH PARLIAMENT FIRST SESSION Book 9 24, 25 and 26 June 2014 Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor The Honourable ALEX CHERNOV, AC, QC The Lieutenant-Governor The Honourable Justice MARILYN WARREN, AC The ministry (from 17 March 2014) Premier, Minister for Regional Cities and Minister for Racing .......... The Hon. D. V. Napthine, MP Deputy Premier, Minister for State Development, and Minister for Regional and Rural Development ................................ The Hon. P. J. Ryan, MP Treasurer ....................................................... The Hon. M. A. O’Brien, MP Minister for Innovation, Minister for Tourism and Major Events, and Minister for Employment and Trade .............................. The Hon. Louise Asher, MP Minister for Local Government and Minister for Aboriginal Affairs ...... The Hon. T. O. Bull, MP Attorney-General, Minister for Finance and Minister for Industrial Relations ..................................................... The Hon. R. W. Clark, MP Minister for Health and Minister for Ageing .......................... The Hon. D. M. Davis, MLC Minister for Education ............................................ The Hon. M. F. Dixon, MP Minister for Sport and Recreation, and Minister for Veterans’ Affairs .... The Hon. D. K. Drum, MLC Minister for Planning, and Minister for Multicultural Affairs and Citizenship ................................................... The Hon. M. J. Guy, MLC Minister for Ports, Minister for Major Projects and Minister for Manufacturing ................................................ The Hon. D. J. Hodgett, MP Minister for Housing, and Minister for Children and Early Childhood Development ................................................. The Hon. W. A. Lovell, MLC Minister for Public Transport and Minister for Roads .................. The Hon. T. W. Mulder, MP Minister for Energy and Resources, and Minister for Small Business .... -

Gender & Politics 2020: the Path Towards Real Diversity
Gender & Politics 2020: The path towards real diversity 2020 Update Nick Cater and Nicolle Flint Gender & Politics 2020: The path towards real diversity A Menzies Research Centre Policy Brief Authors: Nick Cater & Nicolle Flint Additonal Research: Holly McDonald Introduction: Nick Cater with Scott Morrison Published by: The Menzies Research Centre Limited RG Menzies House Cnr Blackall and Macquarie Streets BARTON ACT 2600 PO Box 6091 KINGSTON ACT 2604 Executive Director: Nick Cater Phone: 02 6273 5608 Email: [email protected] Designed by: Branded Graphics The Menzies Research Centre Limited is a company limited by guarantee © 2020 THE MENZIES RESEARCH CENTRE DONATIONS TO THE MENZIES RESEARCH CENTRE FUNDS ARE TAX DEDUCTIBLE To donate go to menziesrc.org/donate ‘There is no reason why a qualified woman should not sit in Parliament or on the Bench or in a professorial Chair or preach from the pulpit, or if you like, command an army in the field.’ Robert Menzies, 19431 1 R G Menzies, ‘Women for Canberra’, Radio Broadcast, 29 January 1943. This paper updates the report first released in 2015 and revised in 2017. It attempts to provide empirical evidence of the extent and nature of the gender imbalance in politics, particularly within the Liberal Party, discuss its consequences and construct an intellectual and philosophical framework to address the disparity based on Liberal principles. The 2015 paper drew from the Menzies Research Centre’s Gender and Politics Forum held in Melbourne on 26 June 2015. It was presented to the federal Women’s Committee Conference in Adelaide on 15-16 August 2015, convened to celebrate the 70th Anniversary of the establishment of the Committee. -

4 March 2020
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE COUNCIL FIFTY-NINTH PARLIAMENT FIRST SESSION WEDNESDAY, 4 MARCH 2020 Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor The Honourable LINDA DESSAU, AC The Lieutenant-Governor The Honourable KEN LAY, AO, APM The ministry Premier........................................................ The Hon. DM Andrews, MP Deputy Premier, Minister for Education and Minister for the Coordination of Education and Training: COVID-19 .............. The Hon. JA Merlino, MP Minister for Regional Development, Minister for Agriculture and Minister for Resources ........................................ The Hon. J Symes, MLC Treasurer, Minister for Economic Development, Minister for Industrial Relations and Minister for the Coordination of Treasury and Finance: COVID-19 .......................................... The Hon. TH Pallas, MP Minister for Transport Infrastructure, Minister for the Suburban Rail Loop and Minister for the Coordination of Transport: COVID-19 ... The Hon. JM Allan, MP Minister for Health, Minister for Ambulance Services and Minister for the Coordination of Health and Human Services: COVID-19 ....... The Hon. J Mikakos, MLC Minister for Public Transport and Minister for Roads and Road Safety . The Hon. BA Carroll, MP Minister for Energy, Environment and Climate Change and Minister for Solar Homes ................................................ The Hon. L D’Ambrosio, MP Minister for Child Protection and Minister -

Stubbornly Opposed: Influence of Personal Ideology in Politician's
Stubbornly Opposed: Influence of personal ideology in politician's speeches on Same Sex Marriage Preliminary and incomplete 2020-09-17 Current Version: http://eamonmcginn.com/papers/Same_Sex_Marriage.pdf. By Eamon McGinn∗ There is an emerging consensus in the empirical literature that politicians' personal ideology play an important role in determin- ing their voting behavior (called `partial convergence'). This is in contrast to Downs' theory of political behavior which suggests con- vergence on the position of the median voter. In this paper I extend recent empirical findings on partial convergence by applying a text- as-data approach to analyse politicians' speech behavior. I analyse the debate in parliament following a recent politically charged mo- ment in Australia | a national vote on same sex marriage (SSM). I use a LASSO model to estimate the degree of support or opposi- tion to SSM in parliamentary speeches. I then measure how speech changed following the SSM vote. I find that Opposers of SSM be- came stronger in their opposition once the results of the SSM na- tional survey were released, regardless of how their electorate voted. The average Opposer increased their opposition by 0.15-0.2 on a scale of 0-1. No consistent and statistically significant change is seen in the behavior of Supporters of SSM. This result indicates that personal ideology played a more significant role in determining changes in speech than did the position of the electorate. JEL: C55, D72, D78, J12, H11 Keywords: same sex marriage, marriage equality, voting, political behavior, polarization, text-as-data ∗ McGinn: Univeristy of Technology Sydney, UTS Business School PO Box 123, Broadway, NSW 2007, Australia, [email protected]). -

ALP Federal Caucus by Factional Alignment February 2021 National NSW VIC QLD SA WA TAS NT ACT
ALP federal caucus by factional alignment February 2021 National NSW VIC QLD SA WA TAS NT ACT House of Reps Right Chris Bowen Richard Marles Jim Chalmers Nick Champion Matt Keogh Luke Gosling David Smith Tony Burke Bill Shorten Shayne Neumann Steve Georganas Madeleine King Jason Clare Mark Dreyfus Milton Dick Amanda Rishworth Joel Fitzgibbon Peter Khalil Anika Wells Ed Husic Anthony Byrne Michelle Rowland Rob Mitchell Sharon Bird Clare O'Neil Justine Elliot Josh Burns Mike Freelander Daniel Mulino Chris Hayes Joanne Ryan Kristy McBain Tim Watts Emma McBride Meryl Swanson Matt Thistlethwaite House of Reps Independent Andrew Leigh Alicia Payne House of Reps Left Anthony Albanese Andrew Giles Terri Butler Mark Butler Josh Wilson Julie Collins Warren Snowdon Pat Conroy Julian Hill Graham Perrett Tony Zappia Anne Aly Brian Mitchell Tanya Plibersek Catherine King Pat Gorman Stephen Jones Libby Coker Susan Templeman Ged Kearney Linda Burney Peta Murphy Anne Stanley Brendan O'Connor Julie Owens Lisa Chesters Fiona Phillips Maria Vamvakinou Sharon Claydon Kate Thwaites Senate Right Kristina Keneally Raffaele Ciccone Anthony ChisholmDon Farrell Pat Dodson Catryna Bilyk Tony Sheldon Kimberley Kitching Alex Gallacher Glenn Sterle Helen Polley Deb O'Neill Marielle Smith Senate Left faction Tim Ayres Kim Carr Murray Watt Penny Wong Sue Lines Carol Brown Malarndirri McCarthy Katy Gallagher Jenny McAllister Jess Walsh Nita Green Louise Pratt Anne Urquhart Total House Reps Right 14 11 4 3 2 0 1 1 36 Total House Reps Left 10 10 2 3 2 2 1 0 30 Total House Reps Indi 0 0 0 0 0 0 0 2 2 SuB-total 24 21 6 6 4 2 2 3 68 Total Senate Right 3 2 1 3 2 2 0 0 13 Total Senate Left 2 2 2 1 2 2 1 1 13 SuB-total 5 4 3 4 4 4 1 1 26 ALP Caucus Indi total 2 Left total 43 Right total 49 Total 94. -
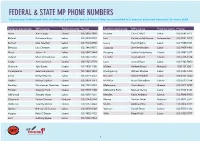
Federal & State Mp Phone Numbers
FEDERAL & STATE MP PHONE NUMBERS Contact your federal and state members of parliament and ask them if they are committed to 2 years of preschool education for every child. Federal electorate MP’s name Political party Phone Federal electorate MP’s name Political party Phone Aston Alan Tudge Liberal (03) 9887 3890 Hotham Clare O’Neil Labor (03) 9545 6211 Ballarat Catherine King Labor (03) 5338 8123 Indi Catherine McGowan Independent (03) 5721 7077 Batman Ged Kearney Labor (03) 9416 8690 Isaacs Mark Dreyfus Labor (03) 9580 4651 Bendigo Lisa Chesters Labor (03) 5443 9055 Jagajaga Jennifer Macklin Labor (03) 9459 1411 Bruce Julian Hill Labor (03) 9547 1444 Kooyong Joshua Frydenberg Liberal (03) 9882 3677 Calwell Maria Vamvakinou Labor (03) 9367 5216 La Trobe Jason Wood Liberal (03) 9768 9164 Casey Anthony Smith Liberal (03) 9727 0799 Lalor Joanne Ryan Labor (03) 9742 5800 Chisholm Julia Banks Liberal (03) 9808 3188 Mallee Andrew Broad National 1300 131 620 Corangamite Sarah Henderson Liberal (03) 5243 1444 Maribyrnong William Shorten Labor (03) 9326 1300 Corio Richard Marles Labor (03) 5221 3033 McEwen Robert Mitchell Labor (03) 9333 0440 Deakin Michael Sukkar Liberal (03) 9874 1711 McMillan Russell Broadbent Liberal (03) 5623 2064 Dunkley Christopher Crewther Liberal (03) 9781 2333 Melbourne Adam Bandt Greens (03) 9417 0759 Flinders Gregory Hunt Liberal (03) 5979 3188 Melbourne Ports Michael Danby Labor (03) 9534 8126 Gellibrand Timothy Watts Labor (03) 9687 7661 Menzies Kevin Andrews Liberal (03) 9848 9900 Gippsland Darren Chester National -

Advocacy Annual Report 2019-2020
ANNUAL ADVOCACY REPORT 2019/20 CONTENTS INTRODUCTION Wyndham City has a diverse and friendly During this term of Council, Wyndham City community, a relaxing lifestyle and endless has yielded significantly positive results for the business opportunities. It is the link between community. Some of the key achievements Melbourne and Geelong, Victoria’s two largest include: cities, making it an area of great economic • Significant levels of investment from the significance that extends beyond its own region, State and Federal Government towards impacting the rest of the state. infrastructure projects including level crossing Wyndham City is one of Australia’s fastest removals, new and updated train station car growing municipalities, with our population parks, and major road upgrades. expected to surpass 500,000 by 2040. A • Working with the private sector in the rapid population growth has created new planning and construction of major opportunities for the 270,000 people who infrastructure projects, including the Western already call Wyndham home. United Football Club’s Wyndham City As a community, we have always supported Stadium. one another in times of need. During this • State Government funding for new and coronavirus pandemic, there has been locally- upgraded primary and secondary schools. led initiatives aimed at supporting vulnerable members of our community, including the • Implementation of social and employment supply of food parcels and vouchers, and our programs that assist members of the Check in and Chat services. Council has also community who have experienced difficulty been responding rapidly to the social and in finding employment or opportunities to economic shock brought on by this pandemic upskill. -

Submission to the Commonwealth Arts
By Email : [email protected] Senate Legal and Constitutional Affairs Committee PO Box 6100 Parliament House Canberra ACT 2600 17 July 2015 Dear Sir/Madam, Re: Impact of the 2014 and 2015 Commonwealth Budget decisions on the Arts Western Melbourne Tourism Inc (WMT) is an association incorporated for the purposes of promoting and developing the tourism sector within the western metropolitan region, embracing the municipal boundaries of Brimbank, Hobsons Bay, Maribyrnong, Melton, Moonee Valley and Wyndham councils. WMT is overseen by an independent board comprising representation from five of the above six western metropolitan partner councils (excl Maribyrnong) as well as the local arts sector, Parks Victoria, Victoria University and other sector representation from the tourism industry in the region. Currently approximately 4 million people visit Melbourne’s west annually and the outlook for future growth of the visitor sector for the region is very positive. WMT has a strong strategic interest in the profile and supporting the development of a stronger visitor economy for Melbourne’s west, including its arts and cultural attractions. The WMT board is committed to working together with its key stakeholders to enable an increase in recognition and greater contribution of such attractions to the region’s economy. It is also seeking to ensure potential visitors are aware of the unique aspects of the region that make Melbourne’s west a compelling place to visit, and this interest converts to visitation growth. The emergence of the vibrant arts sector and other associated creative industries in the west is one of the beacons of opportunity for this part of Melbourne. -

The Australian Capital Territory New South Wales
Names and electoral office addresses of Federal Members of Parliament The Australian Capital Territory ......................................................................................................... 1 New South Wales ............................................................................................................................... 1 Northern Territory .............................................................................................................................. 4 Queensland ........................................................................................................................................ 4 South Australia .................................................................................................................................. 6 Tasmania ........................................................................................................................................... 6 Victoria ............................................................................................................................................... 7 Western Australia .............................................................................................................................. 9 How to address Members of Parliament ........................................................................... 10 The Australian Capital Territory Ms Gai Brodtmann, MP Hon Dr Andrew Leigh, MP 205 Anketell St, Unit 8/1 Torrens St, Tuggeranong ACT, 2900 Braddon ACT, 2612 New South Wales Hon Anthony Abbott, -

Morrison's Miracle the 2019 Australian Federal Election
MORRISON'S MIRACLE THE 2019 AUSTRALIAN FEDERAL ELECTION MORRISON'S MIRACLE THE 2019 AUSTRALIAN FEDERAL ELECTION EDITED BY ANIKA GAUJA, MARIAN SAWER AND MARIAN SIMMS In memory of Dr John Beaton FASSA, Executive Director of the Academy of the Social Sciences in Australia from 2001 to 2018 and an avid supporter of this series of election analyses Published by ANU Press The Australian National University Acton ACT 2601, Australia Email: [email protected] Available to download for free at press.anu.edu.au ISBN (print): 9781760463618 ISBN (online): 9781760463625 WorldCat (print): 1157333181 WorldCat (online): 1157332115 DOI: 10.22459/MM.2020 This title is published under a Creative Commons Attribution-NonCommercial- NoDerivatives 4.0 International (CC BY-NC-ND 4.0). The full licence terms are available at creativecommons.org/licenses/by-nc-nd/4.0/legalcode Cover design and layout by ANU Press Cover photograph: Scott Morrison Campaign Day 11. Photo by Mick Tsikas, AAP. This edition © 2020 ANU Press CONTENTS Figures . ix Plates . xiii Tables . .. xv Abbreviations . xix Acknowledgements . xxiii Contributors . xxv Foreword . xxxiii 1 . Morrison’s miracle: Analysing the 2019 Australian federal election . 1 Anika Gauja, Marian Sawer and Marian Simms Part 1. Campaign and context 2 . Election campaign overview . 21 Marian Simms 3 . The rules of the game . 47 Marian Sawer and Michael Maley 4 . Candidates and pre‑selection . .. 71 Anika Gauja and Marija Taflaga 5 . Ideology and populism . 91 Carol Johnson 6 . The personalisation of the campaign . 107 Paul Strangio and James Walter 7 . National polling and other disasters . 125 Luke Mansillo and Simon Jackman 8 . -
Parliamentary Debates (Hansard)
PARLIAMENT OF VICTORIA PARLIAMENTARY DEBATES (HANSARD) LEGISLATIVE ASSEMBLY FIFTY-EIGHTH PARLIAMENT FIRST SESSION Thursday, 20 September 2018 (Extract from book 13) Internet: www.parliament.vic.gov.au/downloadhansard By authority of the Victorian Government Printer The Governor The Honourable LINDA DESSAU, AC The Lieutenant-Governor The Honourable KEN LAY, AO, APM The ministry (from 16 October 2017) Premier ........................................................ The Hon. D. M. Andrews, MP Deputy Premier, Minister for Education and Minister for Emergency Services...................................................... The Hon. J. A. Merlino, MP Treasurer and Minister for Resources .............................. The Hon. T. H. Pallas, MP Minister for Public Transport and Minister for Major Projects .......... The Hon. J. Allan, MP Minister for Industry and Employment ............................. The Hon. B. A. Carroll, MP Minister for Trade and Investment, Minister for Innovation and the Digital Economy, and Minister for Small Business ................ The Hon. P. Dalidakis, MLC Minister for Energy, Environment and Climate Change, and Minister for Suburban Development ....................................... The Hon. L. D’Ambrosio, MP Minister for Roads and Road Safety, and Minister for Ports ............ The Hon. L. A. Donnellan, MP Minister for Tourism and Major Events, Minister for Sport and Minister for Veterans ................................................. The Hon. J. H. Eren, MP Minister for Housing, Disability and Ageing, Minister for Mental Health, Minister for Equality and Minister for Creative Industries .......... The Hon. M. P. Foley, MP Minister for Health and Minister for Ambulance Services ............. The Hon. J. Hennessy, MP Minister for Aboriginal Affairs, Minister for Industrial Relations, Minister for Women and Minister for the Prevention of Family Violence ............................................. The Hon. N. M. Hutchins, MP Special Minister of State ......................................... The Hon. G. -

TASMANIAN MEMBERS of FEDERAL PARLIAMENT As at June 2019
TASMANIAN MEMBERS OF FEDERAL PARLIAMENT As at June 2019 SENATE (12) The Honourable Eric ABETZ (LIB) Senator Nick McKIM (AG) Highbury House 136 Davey Street 149B Macquarie Street HOBART TAS 7000 GPO Box 1675, HOBART TAS 7001 GPO Box 896 HOBART TAS 7001 PHONE: (03) 6224 3707 (02) 6277 3019 PHONE: (03) 6224 8899 (02) 6277 3601 FAX: (03) 622 43709 (02) 6277 5872 FAX: (03) 6224 7599 (02) 6277 5797 Toll Free: 1300 132 493 Toll Free: 1300 131 720 EMAIL: [email protected] EMAIL: [email protected] Senator Wendy ASKEW (LIB) Senator Helen POLLEY (ALP) Suite 1 71 Paterson Street “The Charles” Suite 101 LAUNCESTON TAS 7250 287 Charles Street LAUNCESTON TAS 7250 PO Box 97 LAUNCESTON TAS 7250 PO BOX 1223 LAUNCESTON TAS 7250 PHONE (03) 6331 8501 (02) 6277 3204 PHONE: (03) 6331 2599 (02) 6277 3129 Toll Free: 1300 134 468 FAX: (03) 6331 2588 (02) 6277 5753 EMAIL: [email protected] EMAIL: [email protected] Senator Catryna BILYK (ALP) Senator Anne URQUHART (ALP) Shop 3 Kingston Plaza Ground Floor 69 Best Street 20 Channel Highway KINGSTON TAS 7050 DEVONPORT TAS 7310 PO Box 320 KINGSTON TAS 7051 PO Box 360, DEVONPORT TAS 7310 PHONE: (03) 6229 4444 (02) 6277 3349 PHONE: (03) 6423 1933 (02) 6277 3434 FAX: (03) 6229 4100 (02) 6277 5799 FAX: (03) 6423 3544 Toll Free: 1300 855 225 EMAIL: [email protected] EMAIL: [email protected] Senator Peter WHISH-WILSON (AG) Senator Carol BROWN (ALP) 37 George Street, AMP Building Ground Floor PO Box 5194 LAUNCESTON TAS 7250 27 Elizabeth Street HOBART TAS 7000 PHONE: (03) 6331 0033